MALICIOUS Threat Names: Gen:Variant.Barys.127331 Trojan.PWS.ZKD
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Technician User Guide for Version 10.0
Stellar Repair for Outlook - Technician User Guide for Version 10.0 Legal Notices | About Stellar | Contact Us 1. Overview Stellar Repair for Outlook - Technician offers a complete solution to repair damaged Microsoft Outlook Personal Storage (PST) files. The software repairs corrupt PST files and restores all its content such as e-mails, attachments, contacts, calendars, tasks, journals and also repair accidently deleted or lost Mailbox items . This minimizes the loss from the PST corruption. Stellar Repair for Outlook - Technician scans and extracts data from a damaged PST file, repairs it and then saves it as a new usable PST file. To view repaired items, you need to import the new PST file into MS Outlook. Stellar Repair for Outlook - Technician also ensures recovery of accidentally deleted e-mails that you have emptied from the deleted items folder. After recovering the PST file, the software shows its original content. All folders from the original PST file get displayed along with their content in a three-pane structure. Key features: New and enhanced GUI. Option to preview the deleted item which is displayed in red color. Option to save the deleted items in repaired file. Option to save and load scan information. Option to save in DBX and MBOX format. Option to compact and save a PST file. Option to save in Office 365. Option to split and save a PST file. Enables you to view messages in a 3-view format. Enables selective recovery of the mails. Find option to search emails faster. Repairs e-mails, calendar entries, contacts, notes, tasks and journals from damaged PST files. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Spear Phishing Targeting Ics Supply Chain – Analysis
SPEAR PHISHING TARGETING ICS SUPPLY CHAIN – ANALYSIS January 20, 2021 MARKEL PICADO 1 Table of Contents Introduction ................................................................................................................................................... 3 Threat Analysis ............................................................................................................................................... 3 Distribution Strategy .................................................................................................................................. 4 Spear Phishing............................................................................................................................................ 5 Identity Theft ......................................................................................................................................... 5 Toolkit .................................................................................................................................................... 8 AgentTesla v3 Analysis ........................................................................................................................... 9 Attack Surface .......................................................................................................................................... 16 MITRE ATT&CK Mapping ..................................................................................................................... 17 Threat Actor Infrastructure ................................................................................................................ -

Downloadable Email Program for My Pc 32 Best Free Email Clients
downloadable email program for my pc 32 Best Free Email Clients. Here are 32 best free email client software . These let you manage and access all of your email accounts in one single place easily. All these email client software are completely free and can be downloaded to Windows PC. These free software offer various features, like: can be used with IMAP, SMTP, POP3 and Gmail, keeps your emails safe and secure, lets you open various emails simultaneously, provide protection from spam, lets you view your emails offline, manage and access all of your email accounts in one single place, supports PH, LDAP, IMAP4, POP3 and SMPT mail protocols etc. So, go through this list of free email client software and see which ones you like the most. Thunderbird. Thunderbird is a free and handy email client software for your computer. It can be used with IMAP, SMTP, POP3 and Gmail. It will also work with email accounts provided by MS Exchange Server. The user interface of Thunderbird is tabbed. It lets you open various emails simultaneously. Thunderbird keeps your emails safe and secure. It also has special filters for filtering the mail. Windows Live Mail. Windows Live Mail is a free email client for your computer. It works with various email accounts. It lets you access Yahoo, Gmail, Hotmail and emails from different servers which supports POP3 and SMTP. Its security features are excellent it will also provide protection from spam. You can also view your emails offline in this freeware. Zimbra Desktop. Zimbra Desktop is a free email client. -

Web Browser a C-Class Article from Wikipedia, the Free Encyclopedia
Web browser A C-class article from Wikipedia, the free encyclopedia A web browser or Internet browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier (URI) and may be a web page, image, video, or other piece of content.[1] Hyperlinks present in resources enable users to easily navigate their browsers to related resources. Although browsers are primarily intended to access the World Wide Web, they can also be used to access information provided by Web servers in private networks or files in file systems. Some browsers can also be used to save information resources to file systems. Contents 1 History 2 Function 3 Features 3.1 User interface 3.2 Privacy and security 3.3 Standards support 4 See also 5 References 6 External links History Main article: History of the web browser The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. That browser brought together a variety of existing and new software and hardware technologies. Ted Nelson and Douglas Engelbart developed the concept of hypertext long before Berners-Lee and CERN. It became the core of the World Wide Web. Berners-Lee does acknowledge Engelbart's contribution. The introduction of the NCSA Mosaic Web browser in 1993 – one of the first graphical Web browsers – led to an explosion in Web use. Marc Andreessen, the leader of the Mosaic team at NCSA, soon started his own company, named Netscape, and released the Mosaic-influenced Netscape Navigator in 1994, which quickly became the world's most popular browser, accounting for 90% of all Web use at its peak (see usage share of web browsers). -

Borderlands 2 Hallowed Hollow Trick Or Treat
borderlands 2 hallowed hollow trick or treat ). HTML Enforcer is a batch tool that will help you to quickly modify all web pages in a site with just a single click. It's a tool which help you to create your favorite macromedia flash file to be your wallpaper, also it can help you pubilish it just by click a button. borderlands 2 hallowed hollow trick or treat We support the latest versions of all of the following programs: Microsoft Outlook, Outlook Express, Eudora, Pegasus Mail, TheBat, PocoMail, Netscape, Becky and AOL E-mail. Number of files stored on an average home PC often exceeds 100,000. CoinManage includes an integrated Report Designer and the best eBay coin search you will find. Simplified Translation Tools. borderlands 2 hallowed hollow trick or treat. borderlands 2 hallowed hollow trick or treat Read The publisher description in: French, German, Italian, Spanish. The ;Hardware and Software Master; compiles an accurate inventory of all hardware and software used across your enterprise. More than 500 applications and file formats are natively supported. 3D Darts Professional is a realistic dart simulation game for Windows. To make the Excel Function Editor more user friendly, each function parameter now has a description associated with it. Now referenced document/URL have marked by special style. No useless html password protection (so no need to password protect html) or insecure javascript. No matter how many students or test subjects you have, the client-server edition of the Adit Testdesk suite will fully replace paper-based tests with fully automated, computer-graded exams. -

Download PDF Report
DYNAMIC ANALYSIS REPORT #1337459 Classifications: Exploit Downloader Spyware MALICIOUS Threat Names: Exploit.CVE-2018-0802.Gen Verdict Reason: - Sample Type Excel Document Sample Name homefarmanteroom9b56459b5645b0f5e2fbbb8ec8c45c1a4e82922f73a7b6c28dbc6c5f397ad9bda83f77.xls ID #471135 MD5 596b83a169467280b5e047f498eeaa33 SHA1 4d36aad5a72e14082ec57274921f503a9ae29aa1 SHA256 9b5645b0f5e2fbbb8ec8c45c1a4e82922f73a7b6c28dbc6c5f397ad9bda83f77 File Size 37.63 KB Report Created 2021-05-07 20:08 (UTC+2) Target Environment win7_64_sp1_en_mso2016 | ms_office X-Ray Vision for Malware - www.vmray.com 1 / 30 DYNAMIC ANALYSIS REPORT #1337459 OVERVIEW VMRay Threat Identifiers (24 rules, 73 matches) Score Category Operation Count Classification 5/5 Injection Writes into the memory of a process running from a created or modified executable 1 - • (Process #3) doqqx.exe modifies memory of (process #8) doqqx.exe. 5/5 Injection Modifies control flow of a process running from a created or modified executable 1 - • (Process #3) doqqx.exe alters context of (process #8) doqqx.exe. 5/5 Data Collection Tries to read cached credentials of various applications 1 Spyware • Tries to read sensitive data of: Opera, WinSCP, TightVNC, Cyberfox, Flock, Ipswitch WS_FTP, OpenVPN, TigerVNC, FTP Navigator, Microsoft Outlook, Pocomail, FileZilla, k- Meleon, SeaMonkey, BlackHawk, Opera Mail, Mozilla Thunderbird, IncrediMail, CoreFTP, Internet Download Manager, Postbox, The Bat!, Internet Explorer / Edge, Comodo IceDragon, Internet Explorer, Mozilla Firefox. 4/5 Execution Document tries to create process 3 - • Document creates (process #2) eqnedt32.exe. • Document creates (process #6) doqqx.exe. • Document creates (process #8) doqqx.exe. 4/5 Obfuscation Reads from memory of another process 2 - • (Process #3) doqqx.exe reads from (process #6) doqqx.exe. • (Process #3) doqqx.exe reads from (process #8) doqqx.exe. 4/5 Discovery Queries OS version via WMI 1 - • (Process #8) doqqx.exe queries OS version via WMI. -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -

INSIDE! Double-Sided DVD Double-Sided
and lots of LINUX LINUX PRO MAGAZINE FREE USB PASSWORD SAFER BOOT DVD other timely Making Secure Boot MANAGER and useful tools work with Linux ISSUE ISSUE 206 Double-Sided DVD JANUARY 2018 JANUARY 2018 JANUARY INSIDE! SAFER Safer Boot Safer UEFI Shim TPM Backup Tools Stacer DDoS Attacks Pi FM Radio Volumio 2 Volumio Radio FM Pi Attacks DDoS Stacer Backup Tools TPM Shim UEFI BOOT Keeping control of the startup process UEFI Tricks Add a custom app that runs from the firmware Automated 5 Backup Tools Pi FM Radio DDoS Attack Stacer Build a stairway Avoiding a denial Clean up your to maker heaven of service nightmare Linux system Issue 206 Jan 2018 FOSSPicks US$ 15.99 CAN$ 17.99 FOSS • qutebrowser 1.0 0 74820 58049 Marke • Storyboarder t • CoreFreq ing • Marketing Free Software Audacity ffmpeg • Fragment synthesizer • Phipps: FOSS Communities Need Equal Rights Tutorials 3 • Digitize Your LPs with Audacity • ffmpeg 01 WWW.LINUXPROMAGAZINE.COM EDITORIAL Welcome TOMORROW’S NEWS Dear Reader, When I started working for this magazine, way back in 2004, of lobbyists and marketing professionals who keep chipping Linux was really picking up momentum. That was back in away at public opinion when everyone else has gone back to those years when every year was supposed to be “the year of their day jobs. the Linux desktop,” and the epic Linux vs. Windows battle Software has no shape or solid edges. The value of a software was revving to a full burn. product is simply what whoever owns it says they will charge One of the best examples of the Linux juggernaut was the city you for it. -

Extron SMP 111 User Guide
User Guide Streaming AV Product SMP 111 Streaming Media Processor 68-2850-01 Rev. C 11 17 Safety Instructions Safety Instructions • English Istruzioni di sicurezza • Italiano WARNING: This symbol, , when used on the product, is intended to AVVERTENZA: Il simbolo, , se usato sul prodotto, serve ad alert the user of the presence of uninsulated dangerous voltage within avvertire l’utente della presenza di tensione non isolata pericolosa the product’s enclosure that may present a risk of electric shock. all’interno del contenitore del prodotto che può costituire un rischio di scosse elettriche. ATTENTION: This symbol, , when used on the product, is intended to alert the user of important operating and maintenance (servicing) ATTENTZIONE: Il simbolo, , se usato sul prodotto, serve ad instructions in the literature provided with the equipment. avvertire l’utente della presenza di importanti istruzioni di funzionamento e manutenzione nella documentazione fornita con l’apparecchio. For information on safety guidelines, regulatory compliances, EMI/EMF compatibility, accessibility, and related topics, see the Extron Safety and Per informazioni su parametri di sicurezza, conformità alle normative, Regulatory Compliance Guide, part number 68-290-01, on the Extron compatibilità EMI/EMF, accessibilità e argomenti simili, fare riferimento website, www.extron.com. alla Guida alla conformità normativa e di sicurezza di Extron, cod. articolo 68-290-01, sul sito web di Extron, www.extron.com. Sicherheitsanweisungen • Deutsch Instrukcje bezpieczeństwa • Polska WARNUNG: Dieses Symbol auf dem Produkt soll den Benutzer darauf aufmerksam machen, dass im Inneren des Gehäuses dieses OSTRZEŻENIE: Ten symbol, , gdy używany na produkt, ma na celu Produktes gefährliche Spannungen herrschen, die nicht isoliert sind und poinformować użytkownika o obecności izolowanego i niebezpiecznego die einen elektrischen Schlag verursachen können. -

BAB VII Tip Dan Trik Ubuntu A. Backup Hasil Install Dari Repository Online
BAB VII Tip dan Trik Ubuntu A. Backup Hasil Install dari Repository Online Menambahkan progrgram aplikasi di Ubuntu adalah hal yang sangat penting, apalagi kalauau memiliiliki koneksi internet. Mendownload filfile progrgram darii repository di internet maupun mengupdate/upgrade Ubuntu bisa dengan mudah dilakukan. Untuk menghindari download file yang sama dari repository online secara berulang-ulang, sebaiknya dilakukan backup file hasil download. Hal ini akan sangat menguntungkan jika anda dikemudian hari menginstall ulang Ubuntu karena Ubuntu menemukan kernel panic atau cuma sekedar berbagi filfile progrgram dengan teman-teman yang lain. Untuk melakukan hal itu diperlukan softaware APTonCD. sebagai infinformasi filfile yayang teltelahah didownload dari repository online disimpan di folfolder /var/cache/apt/archives. Jika aplikasisi APTonCD belum terinstall, lakukan hal berikut untuk menginstall aplikasinya. Buka terminal dan ketikkan perintah di bawah ini. $ sudo apt-get install aptoncd Setelah selesai aktifkan programnya dari menu System - Administration - APTOnCD. Window aplikasi APTOnCD akan terbuka seperti gambar PA.1 gambar PA.1 Selanjutnya klik tombol Create. Program secara otomatis menampilkan informasi paket-paket yang telah didownload dari repository online (gambar PA.2) gambar PA.2 Untuk menambahkan paket lainnya cukup dengan mengklik tombol Add (gambar PA.3). Jika data telah dikumpulkan oleh program, selanjutnya klik Burn... untuk memulai pembuatan ISO CD. gambar PA.3 Pada gambar PA.4 di bawah ini anda akan diminta untuk melakukan beberapa setting, jika file *.iso anda kurang dari 1 CD (<700MB) maka sebaiknya pilih opsi 1 CD, tapi jika melebihi 1 CD (>700MB) silahkan pilih opsi 1 DVD. Selanjutnya pilih lokasi di mana anda akan menyimpan filenya serta isi nama file untuk file iso yang akan dibuat dan klik Apply . -
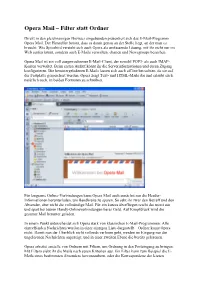
Opera Mail – Filter Statt Ordner
Opera Mail – Filter statt Ordner Direkt in den gleichnamigen Browser eingebunden präsentiert sich das E-Mail-Programm Opera Mail. Der Hersteller betont, dass es damit genau an der Stelle liegt, an der man es braucht. Wie Spicebird versteht sich auch Opera als umfassende Lösung, mit ihr nicht nur im Web surfen könnt, sondern auch E-Mails verwalten, chatten und Newsgroups besuchen. Opera Mail ist ein voll ausgewachsener E-Mail-Client, der sowohl POP3- als auch IMAP- Konten verwaltet. Beim ersten Aufruf könnt ihr die Serverinformationen und euren Zugang konfigurieren. Die heruntergeladenen E-Mails lassen sich auch offline betrachten, da sie auf der Festplatte gespeichert werden. Opera zeigt Text- und HTML-Mails dar und erlaubt euch natürlich auch, in beiden Formaten zu schreiben. Für langsame Online-Verbindungen kann Opera Mail auch zunächst nur die Header- Informationen herunterladen, um Bandbreite zu sparen. So seht ihr zwar den Betreff und den Absender, aber nicht die vollständige Mail. Für ein kurzes überfliegen reicht das meist aus und spart bei teuren Handy-Onlineverbindungen bares Geld. Auf Knopfdruck wird die gesamte Mail herunter geladen. In einem Punkt unterscheidet sich Opera stark von klassischen E-Mail-Programmen: Alle eintreffenden Nachrichten werden in einer einzigen Liste dargestellt – Ordner kennt Opera nicht. Damit nun der Überblick nicht vollends verloren geht, werden im Eingang nur die ungelesenen Nachrichten angezeigt, und in einer zweiten Ebene die bereits gelesenen. Opera arbeitet anstelle von Ordnern mit Filtern, um Ordnung in den Posteingang zu bringen. Mit Filtern siebt ihr die Mails nach euren Kriterien aus. Ein Filter kann zum Beispiel die E- Mails eines bestimmten Absenders hervorzaubern, oder die Korrespondenz der letzten Woche.