INSIDE! Double-Sided DVD Double-Sided
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux and Electronics
Linux and Electronics Urs Lindegger Linux and Electronics Urs Lindegger Copyright © 2019-11-25 Urs Lindegger Table of Contents 1. Introduction .......................................................................................................... 1 Note ................................................................................................................ 1 2. Printed Circuits ...................................................................................................... 2 Printed Circuit Board design ................................................................................ 2 Kicad ....................................................................................................... 2 Eagle ..................................................................................................... 13 Simulation ...................................................................................................... 13 Spice ..................................................................................................... 13 Digital simulation .................................................................................... 18 Wings 3D ....................................................................................................... 18 User interface .......................................................................................... 19 Modeling ................................................................................................ 19 Making holes in Wings 3D ....................................................................... -

One of the Biggest Aims of Limux Was to Make the City More Independent.”
FEATURE MUNICH Munich city council has migrated 15,000 workers from Windows to Linux. Mike Saunders and Graham Morrison visited the city and learned just how upset Steve Ballmer was… “One of the biggest aims of LiMux was to make the city more independent.” irschgarten, in the west of the last decade. Migrating workers of Munich, is one of Europe’s biggest Germany’s third-largest city was no easy Hbeer gardens, with over 8,000 task and there were plenty of hurdles along places to sit. It’s a spectacular sight in the way, but by and large the project has summer: hundreds of benches as far as been a storming success. the eye can see, trees providing some We’ve been following the progress of shelter from the heat, and a vast number LiMux (Linux in Munich) for years, and now of people relaxing and enjoying the city’s that the project is effectively complete, we famous beers. decided to visit the city and talk to the man But while 8,000 is an impressive number, in charge of it. Read on to discover how it it’s not as impressive as 15,000. That’s all started, how Microsoft tried to torpedo how many people the Munich city council it, and whether other cities in the world can has switched from Windows to Linux over follow Munich’s lead… 52 www.linuxvoice.com MUNICH FEATURE Humble beginnings Cast your mind back to 2001, and the state of Linux at the time. It was well established as a server OS and fairly well known among computing hobbyists, but still a small fish in the desktop pond. -

Limux - the IT-Evolution Status of Migration Strategy: Limux Is a Core Item for a Sustainable IT-Strategy Facing Munichs Independance
LiMux - the IT-evolution Status of migration Strategy: LiMux is a core item for a sustainable IT-strategy facing Munichs independance Munich is on its way to an open, modern and citizen centered administration „Munich focuses on free software and open standards. They are indispensable elements of our information technology.“ Lord mayor Christian Ude Currently, there are 22 different IT departments, supporting 15.000 PC- workstations The IT of the city of Munich is going to be reorganized. This includes centralization of plan, build and run, installation of new processes according to ITIL®, standardization of applications and modernization of the IT architecture LiMux is Germanys biggest Linux project in the public sector The six main mandates of the city council of Munich Consistent linux based operating system (LiMux client) Vendor independent Office solution Migration of business applications to platform-open solutions Consolidation of PC-standard applications Consolidation and migration of MS-Office macros, templates and forms Implementation of system management solutions (standardization) IT-reorganization: Currently, the IT of the Munich administration is on its way to a rebuilding-process Facts ~ 33.000 employees (~ 1.000 located in the IT) ~ 15.000 PC-workstations 51 locations 22 independent IT-departments ~ 140 mio Euro IT-expenses Reorganization of Munichs IT (centralization of Plan, Build and Run, standardization of business applications) Project goals: Open Source until 2013 Purpose until 2011... Current status (June 2012) is Open source application programs for ~10.500 PC-workstations are migra- office communication are implemen- ted ted for each user Since 2009, all PC-workstations have Document templates are systematical- been provided with OpenOffice.org, ly based in the open source document Firefox and Thunderbird template tool „WollMux“ Since 2009, WollMux has been esta- blished as a standard document tem- Purpose until 2013.. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -

Extron SMP 111 User Guide
User Guide Streaming AV Product SMP 111 Streaming Media Processor 68-2850-01 Rev. C 11 17 Safety Instructions Safety Instructions • English Istruzioni di sicurezza • Italiano WARNING: This symbol, , when used on the product, is intended to AVVERTENZA: Il simbolo, , se usato sul prodotto, serve ad alert the user of the presence of uninsulated dangerous voltage within avvertire l’utente della presenza di tensione non isolata pericolosa the product’s enclosure that may present a risk of electric shock. all’interno del contenitore del prodotto che può costituire un rischio di scosse elettriche. ATTENTION: This symbol, , when used on the product, is intended to alert the user of important operating and maintenance (servicing) ATTENTZIONE: Il simbolo, , se usato sul prodotto, serve ad instructions in the literature provided with the equipment. avvertire l’utente della presenza di importanti istruzioni di funzionamento e manutenzione nella documentazione fornita con l’apparecchio. For information on safety guidelines, regulatory compliances, EMI/EMF compatibility, accessibility, and related topics, see the Extron Safety and Per informazioni su parametri di sicurezza, conformità alle normative, Regulatory Compliance Guide, part number 68-290-01, on the Extron compatibilità EMI/EMF, accessibilità e argomenti simili, fare riferimento website, www.extron.com. alla Guida alla conformità normativa e di sicurezza di Extron, cod. articolo 68-290-01, sul sito web di Extron, www.extron.com. Sicherheitsanweisungen • Deutsch Instrukcje bezpieczeństwa • Polska WARNUNG: Dieses Symbol auf dem Produkt soll den Benutzer darauf aufmerksam machen, dass im Inneren des Gehäuses dieses OSTRZEŻENIE: Ten symbol, , gdy używany na produkt, ma na celu Produktes gefährliche Spannungen herrschen, die nicht isoliert sind und poinformować użytkownika o obecności izolowanego i niebezpiecznego die einen elektrischen Schlag verursachen können. -

Open Source Software and Goverment Policy in South
OPEN SOURCE SOFTWARE AND GOVERNMENT POLICY IN SOUTH AFRICA Minnaar Pieters Thesis submitted in fulfilment of the requirements for the degree of Magister Artium (Socio‐Informatics) © Stellenbosch University 2008 Supervisor: Prof Johann Kinghorn March 2008 Stellenbosch University http://scholar.sun.ac.za Declaration I, the undersigned, hereby declare that the work contained in this thesis is my own original work and that I have not previously in its entirety, or in part, at any university for a degree. Signature: ………………………………. Date: ………………………………. ii Stellenbosch University http://scholar.sun.ac.za Summary Open-source software is not something new; however, it has come into the spotlight in the last few years, mostly due to hyped initial cost savings of the Linux operating system. Consumers and businesses were made aware of shortcomings in the traditional proprietary software model and this has in turn created a surge in popularity of open-source. The migration to open-source requires efficient research of options available and thorough analysis of the migratory process through all levels of the organization. Initial independent cost analysis has not been conclusive, with unreliable, skewed results and below average performance due to poor implementation. The focus of this study is whether open-source software is a suitable alternative to current proprietary software packages utilized by the government sector. The government sector offers unique challenges to which open-source software can be ideally suited. These include high initial costs of hardware and proprietary software, vendor lock-in, file format “future proofing” and the need for high security. Open-source software has addressed most of these issues admirably, but requires proper implementation. -

BAB VII Tip Dan Trik Ubuntu A. Backup Hasil Install Dari Repository Online
BAB VII Tip dan Trik Ubuntu A. Backup Hasil Install dari Repository Online Menambahkan progrgram aplikasi di Ubuntu adalah hal yang sangat penting, apalagi kalauau memiliiliki koneksi internet. Mendownload filfile progrgram darii repository di internet maupun mengupdate/upgrade Ubuntu bisa dengan mudah dilakukan. Untuk menghindari download file yang sama dari repository online secara berulang-ulang, sebaiknya dilakukan backup file hasil download. Hal ini akan sangat menguntungkan jika anda dikemudian hari menginstall ulang Ubuntu karena Ubuntu menemukan kernel panic atau cuma sekedar berbagi filfile progrgram dengan teman-teman yang lain. Untuk melakukan hal itu diperlukan softaware APTonCD. sebagai infinformasi filfile yayang teltelahah didownload dari repository online disimpan di folfolder /var/cache/apt/archives. Jika aplikasisi APTonCD belum terinstall, lakukan hal berikut untuk menginstall aplikasinya. Buka terminal dan ketikkan perintah di bawah ini. $ sudo apt-get install aptoncd Setelah selesai aktifkan programnya dari menu System - Administration - APTOnCD. Window aplikasi APTOnCD akan terbuka seperti gambar PA.1 gambar PA.1 Selanjutnya klik tombol Create. Program secara otomatis menampilkan informasi paket-paket yang telah didownload dari repository online (gambar PA.2) gambar PA.2 Untuk menambahkan paket lainnya cukup dengan mengklik tombol Add (gambar PA.3). Jika data telah dikumpulkan oleh program, selanjutnya klik Burn... untuk memulai pembuatan ISO CD. gambar PA.3 Pada gambar PA.4 di bawah ini anda akan diminta untuk melakukan beberapa setting, jika file *.iso anda kurang dari 1 CD (<700MB) maka sebaiknya pilih opsi 1 CD, tapi jika melebihi 1 CD (>700MB) silahkan pilih opsi 1 DVD. Selanjutnya pilih lokasi di mana anda akan menyimpan filenya serta isi nama file untuk file iso yang akan dibuat dan klik Apply . -

Web-Based Fingerprinting Techniques
Web-based Fingerprinting Techniques V´ıtor Bernardo and Dulce Domingos LaSIGE, Faculdade de Ciencias,ˆ Universidade de Lisboa, Lisboa, Portugal Keywords: Browser Fingerprinting, Cross-browser Fingerprinting, Device Fingerprinting, Privacy, Fingerprint. Abstract: The concept of device fingerprinting is based in the assumption that each electronic device holds a unique set of physical and/or logical features that others can capture and use to differentiate it from the whole. Web-based fingerprinting, a particular case of device fingerprinting, allows website owners to differentiate devices based on the set of information that browsers transmit. Depending on the techniques being used, a website can track a device based on its browser features (browser fingerprinting) or based on system settings (cross-browser fingerprinting). The latter allows identification of the device even when more than one browser is used. Several different works have introduced new techniques over the last years proving that fingerprinting can be done in multiple ways, but there is not a consolidated work gathering all of them. The current work identifies known web-based fingerprinting techniques, categorizing them as which ones are browser and which are cross-browser and showing real examples of the data that can be captured with each technique. The study is synthesized in a taxonomy, which provides a clear separation between techniques, making it easier to identify the threats to security and privacy inherent to each one. 1 INTRODUCTION far more upsetting than simple cookies. In most cases, web-based fingerprinting is used to Device fingerprinting is based on the assumption that track users activity in sites and bind a device finger- no two devices are exactly alike and that profiles can print to a user profile (together with its preferences, be created by capturing the emanation patterns sent tastes and interests). -

Op E N So U R C E Yea R B O O K 2 0
OPEN SOURCE YEARBOOK 2016 ..... ........ .... ... .. .... .. .. ... .. OPENSOURCE.COM Opensource.com publishes stories about creating, adopting, and sharing open source solutions. Visit Opensource.com to learn more about how the open source way is improving technologies, education, business, government, health, law, entertainment, humanitarian efforts, and more. Submit a story idea: https://opensource.com/story Email us: [email protected] Chat with us in Freenode IRC: #opensource.com . OPEN SOURCE YEARBOOK 2016 . OPENSOURCE.COM 3 ...... ........ .. .. .. ... .... AUTOGRAPHS . ... .. .... .. .. ... .. ........ ...... ........ .. .. .. ... .... AUTOGRAPHS . ... .. .... .. .. ... .. ........ OPENSOURCE.COM...... ........ .. .. .. ... .... ........ WRITE FOR US ..... .. .. .. ... .... 7 big reasons to contribute to Opensource.com: Career benefits: “I probably would not have gotten my most recent job if it had not been for my articles on 1 Opensource.com.” Raise awareness: “The platform and publicity that is available through Opensource.com is extremely 2 valuable.” Grow your network: “I met a lot of interesting people after that, boosted my blog stats immediately, and 3 even got some business offers!” Contribute back to open source communities: “Writing for Opensource.com has allowed me to give 4 back to a community of users and developers from whom I have truly benefited for many years.” Receive free, professional editing services: “The team helps me, through feedback, on improving my 5 writing skills.” We’re loveable: “I love the Opensource.com team. I have known some of them for years and they are 6 good people.” 7 Writing for us is easy: “I couldn't have been more pleased with my writing experience.” Email us to learn more or to share your feedback about writing for us: https://opensource.com/story Visit our Participate page to more about joining in the Opensource.com community: https://opensource.com/participate Find our editorial team, moderators, authors, and readers on Freenode IRC at #opensource.com: https://opensource.com/irc . -

Limux Desktop Retrospective “Five Years of Governmental Linux Desktops in München”
LiMux Desktop Retrospective “Five years of governmental Linux desktops in München” Florian Maier (City of Munich, Project LiMux) August 8th, 2011 08.08.2011 LiMux Desktop Retrospective About Munich: 1.3 mio citizens rd 3 biggest town in GER th 12 biggest town in EU Many IT companies © Michael Nagy, Presseamt München © 2011 Landeshauptstadt München Page 2 LiMux Desktop Retrospective LiMux is part of the IT in Munich 33.000 employees are trained using OSS 15.000 PC-workplaces ● Additional 28,000 in schools 1.000 IT-employees 51 service locations 22 independent IT-departments 6,800 workplaces are using the linux client goal for 2012 is 8500 clients © 2011 Landeshauptstadt München Page 3 LiMux Desktop Retrospective LiMux project objectives Increased independence of software vendors, consultants, platforms, timelines → freedom of choice More possibilities to decide about costs → reduction in the mid term Decisions Free software and open standards for the administrations' PCs Plattform-open business applications in the future © 2011 Landeshauptstadt München Page 4 LiMux Desktop Retrospective LiMux desktop components proprietary alien © 2011 Landeshauptstadt München Page 5 LiMux Desktop Retrospective Desktop deployment with GOsa & FAI - Fully Automatic Installation ● Automatic System Installation ● Change Management System http://fai-project.org/ - Gonicus System Administrator ● Web-based administration tool https://oss.gonicus.de/labs/gosa/ Settings are read from LDAP and used to configure KDE with a set of python and bash scripts -
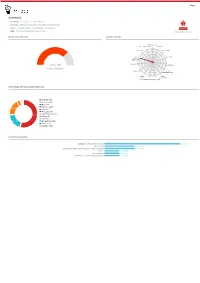
Advanced File Analysis System | Valkyrie
Page 1 Summary File Name: Packing_list_and_Draft_BL.exe File Type: PE32 executable (GUI) Intel 80386, for MS Windows SHA1: 948482095bade1c1d72cda2a08b165a47ca128f3 MALWARE MD5: 7828dd5b474006b86ffe30dce57520bc Valkyrie Final Verdict DETECTION SECTION CLASSIFICATION Backdoor(1.74%) Ransomware(0.00%) Bot(0.60%) 81% Worm(3.46%) Exploit(0.00%) 65% 48% Trojan 32% Pua(5.26%) Password Stealer(75.74%) 16% Rootkit(0.00%) Trojan Severity: High Generic(3.43%) Verdict: Malware Spyware(0.00%) Trojan Downloader(4.23%) Remote Trojan Access Dropper(3.60%) Trojan(0.00%V)irus(0.77%) Rogue(1.17%) HIGH LEVEL BEHAVIOR DISTRIBUTION Network (19) Process (128) Misc (47) System (1493) 18.2% Crypto (12) Threading (7) Synchronization (6) 54.0% Device (2) Windows (1) 19.7% File System (543) Services (3) Registry (502) ACTIVITY OVERVIEW Stealing of Sensitive Information 5 (41.67%) Networking 2 (16.67%) Hooking and other Techniques for Hiding Protection 2 (16.67%) Packer 1 (8.33%) Static Anomaly 1 (8.33%) Persistence and Installation Behavior 1 (8.33%) Page 2 Activity Details NETWORKING HTTP traffic contains suspicious features which may be indicative of malware related traffic Show sources Performs some HTTP requests Show sources PACKER The binary likely contains encrypted or compressed data. Show sources STEALING OF SENSITIVE INFORMATION Collects information to fingerprint the system Show sources Steals private information from local Internet browsers Show sources Harvests information related to installed instant messenger clients Show sources Harvests credentials