Business E-Mail and Personal Information Management
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Citrix Netscaler Deployment Guide for Microsoft Exchange 2010
Citrix NetScaler Deployment Guide for Microsoft Exchange 2010 Table of Contents Citrix NetScaler Deployment Guide for Microsoft Exchange 2010 ................................................................... 1 Introduction .................................................................................................................................................................. 3 Solution Requirements ................................................................................................................................................ 3 Prerequisites .................................................................................................................................................................. 3 Deployment Overview ................................................................................................................................................ 4 Network Diagram ................................................................................................................................................... 7 NetScaler Deployment ................................................................................................................................................ 7 Client Access Server ............................................................................................................................................... 7 Configuring NetScaler for Outlook Web App (OWA) ................................................................................ 9 Configuring NetScaler for -

Download Windows Live Messenger for Linux Ubuntu
Download windows live messenger for linux ubuntu But installing applications in Ubuntu that were originally made for I found emescene to be the best Msn Messenger for Ubuntu Linux so far. It really gives you the feel as if you are using Windows Live Messenger. Its builds are available for Archlinux, Debian, Ubuntu, Fedora, Mandriva and Windows. At first I found it quite difficult to use Pidgin Internet Messenger on Ubuntu Linux. Even though it allows signing into MSN, Yahoo! Messenger and Google Talk. While finding MSN Messenger for Linux / Ubuntu, I found different emesene is also available and could be downloaded and installed for. At first I found it quite difficult to use Pidgin Internet Messenger on Ubuntu Linux. Even though it allows signing into MSN, Yahoo! Messenger. A simple & beautiful app for Facebook Messenger. OS X, Windows & Linux By downloading Messenger for Desktop, you acknowledge that it is not an. An alternative MSN Messenger chat client for Linux. It allows Linux users to chat with friends who use MSN Messenger in Windows or Mac OS. The strength of. Windows Live Messenger is an instant messenger application that For more information on installing applications, see InstallingSoftware. sudo apt-get install chromium-browser. 2. After the installation is Windows Live Messenger running in LinuxMint / Ubuntu. You can close the. Linux / X LAN Messenger for Debian/Ubuntu LAN Messenger for Fedora/openSUSE Download LAN Messenger for Windows. Windows installer A MSN Messenger / Live Messenger client for Linux, aiming at integration with the KDE desktop Ubuntu: Ubuntu has KMess in its default repositories. -

The Webmail Experience Gmail Versus Share
RADBOUD UNIVERSITY NIJMEGEN The webmail experience Gmail versus Share A Bachelor Thesis in Information Science August 2012 Beau Verdiesen - 0813648 Supervised by: Dr. Louis Vuurpijl Contents 1. Introduction ......................................................................................................................................... 3 2. Theory .................................................................................................................................................. 4 2.1 Nielsen’s Usability Attributes ........................................................................................................ 5 2.1.1 Learnability ............................................................................................................................. 5 2.1.2 Efficiency ................................................................................................................................ 5 2.1.3 Memorability .......................................................................................................................... 5 2.1.4 Errors ...................................................................................................................................... 6 2.1.5 Satisfaction ............................................................................................................................. 6 2.2 User Experience ............................................................................................................................. 6 3. Method ............................................................................................................................................... -

Downloadable Email Program for My Pc 32 Best Free Email Clients
downloadable email program for my pc 32 Best Free Email Clients. Here are 32 best free email client software . These let you manage and access all of your email accounts in one single place easily. All these email client software are completely free and can be downloaded to Windows PC. These free software offer various features, like: can be used with IMAP, SMTP, POP3 and Gmail, keeps your emails safe and secure, lets you open various emails simultaneously, provide protection from spam, lets you view your emails offline, manage and access all of your email accounts in one single place, supports PH, LDAP, IMAP4, POP3 and SMPT mail protocols etc. So, go through this list of free email client software and see which ones you like the most. Thunderbird. Thunderbird is a free and handy email client software for your computer. It can be used with IMAP, SMTP, POP3 and Gmail. It will also work with email accounts provided by MS Exchange Server. The user interface of Thunderbird is tabbed. It lets you open various emails simultaneously. Thunderbird keeps your emails safe and secure. It also has special filters for filtering the mail. Windows Live Mail. Windows Live Mail is a free email client for your computer. It works with various email accounts. It lets you access Yahoo, Gmail, Hotmail and emails from different servers which supports POP3 and SMTP. Its security features are excellent it will also provide protection from spam. You can also view your emails offline in this freeware. Zimbra Desktop. Zimbra Desktop is a free email client. -

Web Browser a C-Class Article from Wikipedia, the Free Encyclopedia
Web browser A C-class article from Wikipedia, the free encyclopedia A web browser or Internet browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier (URI) and may be a web page, image, video, or other piece of content.[1] Hyperlinks present in resources enable users to easily navigate their browsers to related resources. Although browsers are primarily intended to access the World Wide Web, they can also be used to access information provided by Web servers in private networks or files in file systems. Some browsers can also be used to save information resources to file systems. Contents 1 History 2 Function 3 Features 3.1 User interface 3.2 Privacy and security 3.3 Standards support 4 See also 5 References 6 External links History Main article: History of the web browser The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. That browser brought together a variety of existing and new software and hardware technologies. Ted Nelson and Douglas Engelbart developed the concept of hypertext long before Berners-Lee and CERN. It became the core of the World Wide Web. Berners-Lee does acknowledge Engelbart's contribution. The introduction of the NCSA Mosaic Web browser in 1993 – one of the first graphical Web browsers – led to an explosion in Web use. Marc Andreessen, the leader of the Mosaic team at NCSA, soon started his own company, named Netscape, and released the Mosaic-influenced Netscape Navigator in 1994, which quickly became the world's most popular browser, accounting for 90% of all Web use at its peak (see usage share of web browsers). -

Windows Geknackt Die Besten Tools 2013
ttbewerb Mit DVD Preise im Wert We 00001 www.onlinepc.ch Fr. 4.70 von Fr. 7‘154.– 985503 € 4,– Ultrabook, Digicam, WLAN-Bundles, 71422 iPhone-Hüllen und Software S.52 97 System verschlüsseln 51 DVD Zürich So geht‘s: Der wirksamste Schutz gegen Datenklau S.30 Auf 8051 D Nr. 1 – Januar 2013 16 Internet-Tipps Auf DV AZB Das Computer-Magazin Firefox-Befehle, Cloud verschlüsseln, Mails sichern... S.30 D Auf DV Total Mounter Virtuelle CDs und DVDs auf jedem PC brennen – ohne Brenner S.30 ▪ Der Schutz macht Windows unzerstörbar ▪ Nach jedem Neustart ist Windows wie neu ▪ Der Schutz lässt sich ein- und ausschalten S.22 Die besten Tools 2013 Das sind die beliebtesten Open-Source-Programme S.36 D D Auf DV Auf DV Windows geknackt So booten Sie jeden Sicherheit PC mit Windows 7 S.42 am PPaasswortsswort besten Abp Mon 9.0 50 Hammertipps Die Überwacht RAM, CPU, Die besten Tricks für vorbei S.16 Special Netzwerk… S.26 Windows 7 S.14 Mit Sicherheits-Tipps Anzeige EDITORIAL /INHALT INHALT 1/2013 PC am Passwort Schutzmodus für vorbei booten: Windows 7 Ein Trick überlistet Der Schutzmodus den Schutz von macht Windows Windows 16 unzerstörbar 22 Leserumfrage Top-100-Software Virenalarm, was tun? Mitmachen und eine Video-Soft- Aus den monatlichen Top 10 Downloads hat Keine Panik! So ware von Magix die Redaktion für Sie eine Auswahl getrof- werden Sie die gewinnen! 62 fen und die 100 beliebtesten Programme auf Schädlinge los 46 die Heft-DVD gepackt. Die Tools decken ein breites Spektrum ab – vom Browser bis zum E-Mail-Programm, von der Sicherheitssoftware bis zum Videoplayer und vom Backup-Pro- AKTUELL TEST & KAUFBERATUNG gramm bis zum Passwortmanager (Seite 36). -

Windows Live Mail
1. Adding the email settings on Windows Live Mail • Click on ♦ Add an e-mail account: (located on the left, refer image above) ♦ or go to Tools Accounts Add E-mail Account Add an E-mail Account ♦ Enter email address password display name ♦ Check "remember password" box (unless you are concerned about security and want to enter the password every time you access your account) ♦ Hit the "Next" button to continue. Here, you need to select your incoming mail server type POP3 or IMAP pop.bluetie.com Port: 110 or imap.bluetie.com Port: 143 login ID Full Email address (should already be there) Outgoing email server address. smtp.bluetie.com Port: 5125 The Windows Live Mail setup process is now complete. You have a choice of setting the new account as the default by checking the box. When a new email account is added on Windows Live Mail, the program creates 5 new folders - Inbox , Drafts , Sent items , Junk e-mail Deleted items For all you Outlook Express users - The Junk e-mail folder was included in Windows Mail Vista as a part of the automated junk email filter utility and carried forward to Windows Live Mail email client. Step 3 - Modifying the properties of the email account The last step is to modify the properties of the newly set up email account. ♦ Right-click on the account in the left panel ♦ select " Properties ". ♦ Advanced tab. ♦ Check "Leave a copy of messages on server " ♦ "Remove from server when deleted ..." . -

Mailstore Server Vs. Office 365 Archiving
MailStore Server vs. Office 365 Archiving The goal of this document is to detail the advantages of using MailStore Server instead of Office 365 archiving for email archiving based on provable facts as opposed to mere assumptions or hearsay. To achieve this goal, only statements about Office 365 archiving that are based on publicly available material published by Microsoft are taken into account. These statements are compared to the capabilities of MailStore Server, based on equally publicly available material published by MailStore Software GmbH. To further enhance the quality of this analysis, all statements (with the exception of those related to pricing) have been extracted from technical specifications and implementation guides to ensure that they are based on current best practice and state of affairs. This document supersedes all previous versions and has been updated to the latest information available in April 2014. Overview No Feature MailStore Server Office 365 Archive 1. Supported versions of All editions of Outlook 2003, Specific editions of Outlook Outlook with access to the 2007, 2010, 2013 1 2007, 2010, 2013 2 archive 2. Supported Office 365 plans All plans that include email 3 Archiving options dependent on plan, with various limits. Additional features can be added to certain plans only 4,5,6 3. Search capabilities Full text search of all Search capabilities readable folders including dependent on the Outlook attachment contents 7 version and edition 8 4. Completeness of the archive Ensured through journaling ° Journaling not available support 9 in all plans 10 ° Office 365 needs external mailbox for journaling 10 The Experts in Email Archiving www.mailstore.com 2 | 7 No Feature MailStore Server Office 365 Archive 5. -

Download PDF Report
DYNAMIC ANALYSIS REPORT #1337459 Classifications: Exploit Downloader Spyware MALICIOUS Threat Names: Exploit.CVE-2018-0802.Gen Verdict Reason: - Sample Type Excel Document Sample Name homefarmanteroom9b56459b5645b0f5e2fbbb8ec8c45c1a4e82922f73a7b6c28dbc6c5f397ad9bda83f77.xls ID #471135 MD5 596b83a169467280b5e047f498eeaa33 SHA1 4d36aad5a72e14082ec57274921f503a9ae29aa1 SHA256 9b5645b0f5e2fbbb8ec8c45c1a4e82922f73a7b6c28dbc6c5f397ad9bda83f77 File Size 37.63 KB Report Created 2021-05-07 20:08 (UTC+2) Target Environment win7_64_sp1_en_mso2016 | ms_office X-Ray Vision for Malware - www.vmray.com 1 / 30 DYNAMIC ANALYSIS REPORT #1337459 OVERVIEW VMRay Threat Identifiers (24 rules, 73 matches) Score Category Operation Count Classification 5/5 Injection Writes into the memory of a process running from a created or modified executable 1 - • (Process #3) doqqx.exe modifies memory of (process #8) doqqx.exe. 5/5 Injection Modifies control flow of a process running from a created or modified executable 1 - • (Process #3) doqqx.exe alters context of (process #8) doqqx.exe. 5/5 Data Collection Tries to read cached credentials of various applications 1 Spyware • Tries to read sensitive data of: Opera, WinSCP, TightVNC, Cyberfox, Flock, Ipswitch WS_FTP, OpenVPN, TigerVNC, FTP Navigator, Microsoft Outlook, Pocomail, FileZilla, k- Meleon, SeaMonkey, BlackHawk, Opera Mail, Mozilla Thunderbird, IncrediMail, CoreFTP, Internet Download Manager, Postbox, The Bat!, Internet Explorer / Edge, Comodo IceDragon, Internet Explorer, Mozilla Firefox. 4/5 Execution Document tries to create process 3 - • Document creates (process #2) eqnedt32.exe. • Document creates (process #6) doqqx.exe. • Document creates (process #8) doqqx.exe. 4/5 Obfuscation Reads from memory of another process 2 - • (Process #3) doqqx.exe reads from (process #6) doqqx.exe. • (Process #3) doqqx.exe reads from (process #8) doqqx.exe. 4/5 Discovery Queries OS version via WMI 1 - • (Process #8) doqqx.exe queries OS version via WMI. -

The Webmail Experience Gmail Versus Share
RADBOUD UNIVERSITY NIJMEGEN The webmail experience Gmail versus Share A Bachelor Thesis in Information Science August 2012 Beau Verdiesen - 0813648 Supervised by: Dr. Louis Vuurpijl Contents 1. Introduction ......................................................................................................................................... 3 2. Theory .................................................................................................................................................. 4 2.1 Nielsen’s Usability Attributes ........................................................................................................ 5 2.1.1 Learnability ............................................................................................................................. 5 2.1.2 Efficiency ................................................................................................................................ 5 2.1.3 Memorability .......................................................................................................................... 5 2.1.4 Errors ...................................................................................................................................... 6 2.1.5 Satisfaction ............................................................................................................................. 6 2.2 User Experience ............................................................................................................................. 6 3. Method ............................................................................................................................................... -
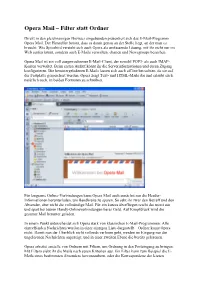
Opera Mail – Filter Statt Ordner
Opera Mail – Filter statt Ordner Direkt in den gleichnamigen Browser eingebunden präsentiert sich das E-Mail-Programm Opera Mail. Der Hersteller betont, dass es damit genau an der Stelle liegt, an der man es braucht. Wie Spicebird versteht sich auch Opera als umfassende Lösung, mit ihr nicht nur im Web surfen könnt, sondern auch E-Mails verwalten, chatten und Newsgroups besuchen. Opera Mail ist ein voll ausgewachsener E-Mail-Client, der sowohl POP3- als auch IMAP- Konten verwaltet. Beim ersten Aufruf könnt ihr die Serverinformationen und euren Zugang konfigurieren. Die heruntergeladenen E-Mails lassen sich auch offline betrachten, da sie auf der Festplatte gespeichert werden. Opera zeigt Text- und HTML-Mails dar und erlaubt euch natürlich auch, in beiden Formaten zu schreiben. Für langsame Online-Verbindungen kann Opera Mail auch zunächst nur die Header- Informationen herunterladen, um Bandbreite zu sparen. So seht ihr zwar den Betreff und den Absender, aber nicht die vollständige Mail. Für ein kurzes überfliegen reicht das meist aus und spart bei teuren Handy-Onlineverbindungen bares Geld. Auf Knopfdruck wird die gesamte Mail herunter geladen. In einem Punkt unterscheidet sich Opera stark von klassischen E-Mail-Programmen: Alle eintreffenden Nachrichten werden in einer einzigen Liste dargestellt – Ordner kennt Opera nicht. Damit nun der Überblick nicht vollends verloren geht, werden im Eingang nur die ungelesenen Nachrichten angezeigt, und in einer zweiten Ebene die bereits gelesenen. Opera arbeitet anstelle von Ordnern mit Filtern, um Ordnung in den Posteingang zu bringen. Mit Filtern siebt ihr die Mails nach euren Kriterien aus. Ein Filter kann zum Beispiel die E- Mails eines bestimmten Absenders hervorzaubern, oder die Korrespondenz der letzten Woche. -

Beginning Computer Skills Level
level one Presented by: Tori Moody - CPU ON-SITE [email protected] 209-296-0660 Is this the right class for you? • Do you have limited experience with computers – for example: job related or email only? • Can you talk to a computer sales person with confidence? • Do you know the correct names for computer parts? • Do you know how and where to properly save your files? • Can you find something even if you forgot the file name? • Do you know the difference between hardware and software? • Are you familiar with the rules of etiquette for email? • Do you know how the Internet works? • Are you able to successfully find what you want on the web? • Do you know the best practices to avoid hacker attacks? CLASS OUTLINE • Terminology: The “Lingo” - 15 minutes • Hardware vs. Software – 10 minutes • How files are stored in your computer – 10 minutes • Email Programs and Rules of Etiquette – 10 minutes Break – 10 minutes • The Web: What is a Browser? Which Browser to Choose? - 20 min • Happy Surfing: How to get the most from Web – 20 min • Internet Safety: – 10 minutes • Questions and Answers – open discussion Will this class be appropriate for YOUR version of Windows? YES! Terminology -The Lingo: How to speak “Geek” Computer terminology can seem confusing. But in reality, it is very logical. Computer hardware is very similar to the human body. Reference material: handout “Hardware Terminology” Hardware terms PARTS OF ALL COMPUTERS MOTHERBOARD Central nervous system All parts are connected to the Mother Board. All electrical current flows through it. HARD DRIVE Hardware terms PARTS OF ALL COMPUTERS HARD DRIVE The “brain” – Long term memory All software programs and data created in the programs is stored here.