Improving Email Management
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Downloadable Email Program for My Pc 32 Best Free Email Clients
downloadable email program for my pc 32 Best Free Email Clients. Here are 32 best free email client software . These let you manage and access all of your email accounts in one single place easily. All these email client software are completely free and can be downloaded to Windows PC. These free software offer various features, like: can be used with IMAP, SMTP, POP3 and Gmail, keeps your emails safe and secure, lets you open various emails simultaneously, provide protection from spam, lets you view your emails offline, manage and access all of your email accounts in one single place, supports PH, LDAP, IMAP4, POP3 and SMPT mail protocols etc. So, go through this list of free email client software and see which ones you like the most. Thunderbird. Thunderbird is a free and handy email client software for your computer. It can be used with IMAP, SMTP, POP3 and Gmail. It will also work with email accounts provided by MS Exchange Server. The user interface of Thunderbird is tabbed. It lets you open various emails simultaneously. Thunderbird keeps your emails safe and secure. It also has special filters for filtering the mail. Windows Live Mail. Windows Live Mail is a free email client for your computer. It works with various email accounts. It lets you access Yahoo, Gmail, Hotmail and emails from different servers which supports POP3 and SMTP. Its security features are excellent it will also provide protection from spam. You can also view your emails offline in this freeware. Zimbra Desktop. Zimbra Desktop is a free email client. -

Web Browser a C-Class Article from Wikipedia, the Free Encyclopedia
Web browser A C-class article from Wikipedia, the free encyclopedia A web browser or Internet browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier (URI) and may be a web page, image, video, or other piece of content.[1] Hyperlinks present in resources enable users to easily navigate their browsers to related resources. Although browsers are primarily intended to access the World Wide Web, they can also be used to access information provided by Web servers in private networks or files in file systems. Some browsers can also be used to save information resources to file systems. Contents 1 History 2 Function 3 Features 3.1 User interface 3.2 Privacy and security 3.3 Standards support 4 See also 5 References 6 External links History Main article: History of the web browser The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. That browser brought together a variety of existing and new software and hardware technologies. Ted Nelson and Douglas Engelbart developed the concept of hypertext long before Berners-Lee and CERN. It became the core of the World Wide Web. Berners-Lee does acknowledge Engelbart's contribution. The introduction of the NCSA Mosaic Web browser in 1993 – one of the first graphical Web browsers – led to an explosion in Web use. Marc Andreessen, the leader of the Mosaic team at NCSA, soon started his own company, named Netscape, and released the Mosaic-influenced Netscape Navigator in 1994, which quickly became the world's most popular browser, accounting for 90% of all Web use at its peak (see usage share of web browsers). -

Download PDF Report
DYNAMIC ANALYSIS REPORT #1337459 Classifications: Exploit Downloader Spyware MALICIOUS Threat Names: Exploit.CVE-2018-0802.Gen Verdict Reason: - Sample Type Excel Document Sample Name homefarmanteroom9b56459b5645b0f5e2fbbb8ec8c45c1a4e82922f73a7b6c28dbc6c5f397ad9bda83f77.xls ID #471135 MD5 596b83a169467280b5e047f498eeaa33 SHA1 4d36aad5a72e14082ec57274921f503a9ae29aa1 SHA256 9b5645b0f5e2fbbb8ec8c45c1a4e82922f73a7b6c28dbc6c5f397ad9bda83f77 File Size 37.63 KB Report Created 2021-05-07 20:08 (UTC+2) Target Environment win7_64_sp1_en_mso2016 | ms_office X-Ray Vision for Malware - www.vmray.com 1 / 30 DYNAMIC ANALYSIS REPORT #1337459 OVERVIEW VMRay Threat Identifiers (24 rules, 73 matches) Score Category Operation Count Classification 5/5 Injection Writes into the memory of a process running from a created or modified executable 1 - • (Process #3) doqqx.exe modifies memory of (process #8) doqqx.exe. 5/5 Injection Modifies control flow of a process running from a created or modified executable 1 - • (Process #3) doqqx.exe alters context of (process #8) doqqx.exe. 5/5 Data Collection Tries to read cached credentials of various applications 1 Spyware • Tries to read sensitive data of: Opera, WinSCP, TightVNC, Cyberfox, Flock, Ipswitch WS_FTP, OpenVPN, TigerVNC, FTP Navigator, Microsoft Outlook, Pocomail, FileZilla, k- Meleon, SeaMonkey, BlackHawk, Opera Mail, Mozilla Thunderbird, IncrediMail, CoreFTP, Internet Download Manager, Postbox, The Bat!, Internet Explorer / Edge, Comodo IceDragon, Internet Explorer, Mozilla Firefox. 4/5 Execution Document tries to create process 3 - • Document creates (process #2) eqnedt32.exe. • Document creates (process #6) doqqx.exe. • Document creates (process #8) doqqx.exe. 4/5 Obfuscation Reads from memory of another process 2 - • (Process #3) doqqx.exe reads from (process #6) doqqx.exe. • (Process #3) doqqx.exe reads from (process #8) doqqx.exe. 4/5 Discovery Queries OS version via WMI 1 - • (Process #8) doqqx.exe queries OS version via WMI. -

The Power of Interoperability: Why Objects Are Inevitable
The Power of Interoperability: Why Objects Are Inevitable Jonathan Aldrich Carnegie Mellon University Pittsburgh, PA, USA [email protected] Abstract 1. Introduction Three years ago in this venue, Cook argued that in Object-oriented programming has been highly suc- their essence, objects are what Reynolds called proce- cessful in practice, and has arguably become the dom- dural data structures. His observation raises a natural inant programming paradigm for writing applications question: if procedural data structures are the essence software in industry. This success can be documented of objects, has this contributed to the empirical success in many ways. For example, of the top ten program- of objects, and if so, how? ming languages at the LangPop.com index, six are pri- This essay attempts to answer that question. After marily object-oriented, and an additional two (PHP reviewing Cook’s definition, I propose the term ser- and Perl) have object-oriented features.1 The equiva- vice abstractions to capture the essential nature of ob- lent numbers for the top ten languages in the TIOBE in- jects. This terminology emphasizes, following Kay, that dex are six and three.2 SourceForge’s most popular lan- objects are not primarily about representing and ma- guages are Java and C++;3 GitHub’s are JavaScript and nipulating data, but are more about providing ser- Ruby.4 Furthermore, objects’ influence is not limited vices in support of higher-level goals. Using examples to object-oriented languages; Cook [8] argues that Mi- taken from object-oriented frameworks, I illustrate the crosoft’s Component Object Model (COM), which has unique design leverage that service abstractions pro- a C language interface, is “one of the most pure object- vide: the ability to define abstractions that can be ex- oriented programming models yet defined.” Academ- tended, and whose extensions are interoperable in a ically, object-oriented programming is a primary focus first-class way. -

NAR's E-PRO Certification: Day 2
NARNAR’s e-PRO®’s Certification: e-PRO Day 2 ® Certification: Day 2 Porf Student Manual Bill Lublin, GRI, CRB, CRS, e-PRO® Ginger Wilcox, GRI, CRS, e-PRO® Amy Chorew, e-PRO® Hal Lublin V 11. 1 Introduction WELCOME Congratulations on successfully completing Day1 of NAR’s e-PRO certification program and welcome to Day 2. In Day 2, we will discuss how to develop a social media strategy that is sustainable. You will also review how to make yourself more mobile, more efficient, and more profitable by integrating technology into your current business. WHAT YOU WILL LEARN The modules in Day 2 are self-paced. The content of the course is organized in six modules with the following learning objectives. 1. e-Strategy – Develop a Hub for your business to capture and convert potential customers and clients. – Connect with consumers through non-real estate–related sites and turn those connections into clients. 2. Content and SEO Strategy – Identify strategies for developing content. – Optimize your Hub so that consumers can find it on the Web. – Use analytics tools to measure consumer traffic to your Hub. 3. e-Office – Become familiar with cloud computing. – Learn how to use portable and mobile devices to do business anywhere, anytime. 2 NAR’s e-PRO® Certification: Day 2 4. Twitter and Foursquare – Learn about location-based services and how they can help you engage with your chosen community and improve your business. 5. Rich Media – Choose equipment to create still photos, video, and audio files to enhance your communication. 6. Technology Toolbelt – Get up to speed on the latest hardware. -
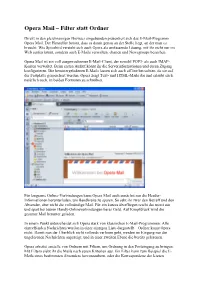
Opera Mail – Filter Statt Ordner
Opera Mail – Filter statt Ordner Direkt in den gleichnamigen Browser eingebunden präsentiert sich das E-Mail-Programm Opera Mail. Der Hersteller betont, dass es damit genau an der Stelle liegt, an der man es braucht. Wie Spicebird versteht sich auch Opera als umfassende Lösung, mit ihr nicht nur im Web surfen könnt, sondern auch E-Mails verwalten, chatten und Newsgroups besuchen. Opera Mail ist ein voll ausgewachsener E-Mail-Client, der sowohl POP3- als auch IMAP- Konten verwaltet. Beim ersten Aufruf könnt ihr die Serverinformationen und euren Zugang konfigurieren. Die heruntergeladenen E-Mails lassen sich auch offline betrachten, da sie auf der Festplatte gespeichert werden. Opera zeigt Text- und HTML-Mails dar und erlaubt euch natürlich auch, in beiden Formaten zu schreiben. Für langsame Online-Verbindungen kann Opera Mail auch zunächst nur die Header- Informationen herunterladen, um Bandbreite zu sparen. So seht ihr zwar den Betreff und den Absender, aber nicht die vollständige Mail. Für ein kurzes überfliegen reicht das meist aus und spart bei teuren Handy-Onlineverbindungen bares Geld. Auf Knopfdruck wird die gesamte Mail herunter geladen. In einem Punkt unterscheidet sich Opera stark von klassischen E-Mail-Programmen: Alle eintreffenden Nachrichten werden in einer einzigen Liste dargestellt – Ordner kennt Opera nicht. Damit nun der Überblick nicht vollends verloren geht, werden im Eingang nur die ungelesenen Nachrichten angezeigt, und in einer zweiten Ebene die bereits gelesenen. Opera arbeitet anstelle von Ordnern mit Filtern, um Ordnung in den Posteingang zu bringen. Mit Filtern siebt ihr die Mails nach euren Kriterien aus. Ein Filter kann zum Beispiel die E- Mails eines bestimmten Absenders hervorzaubern, oder die Korrespondenz der letzten Woche. -

Organizing Email
Organizing Email Master’s Thesis Gabor Cselle <[email protected]> Prof. Dr. Roger Wattenhofer Dr. Keno Albrecht Distributed Computing Group Computer Engineering and Networks Laboratory (TIK) Departments of Computer Science and Electrical Engineering ETH Zurich, Switzerland October 3, 2006 Distributed Computing Group Copyright © 2006 Gabor Cselle and Distributed Computing Group, ETH Zurich. Abstract Email clients were not designed to handle the volume and variety of messages users are dealing with today. While this problem, termed “email overload,” is widely acknowledged, there exist only few products which attempt to solve it. This thesis discusses an email client extension aimed at sensibly structuring the user’s incoming email. We develop our ideas after a thorough review of the problem and existing approaches of or- ganizing email in both research and practice. In particular, we explore automatic foldering, in which machine learning algorithms are used to automatically move emails to folders. How- ever, this method has several drawbacks which we discuss in detail. Instead, we have devised a scheme for topic detection and tracking in email: Related emails are grouped and displayed together. The underlying inbox data is not changed. We evaluated our scheme using existing metrics for news articles, and found good results for clustering quality. We created an exten- sion called “BuzzTrack” for Mozilla Thunderbird, a popular email client, which makes this technology accessible to the end user. iii iv Acknowledgments Ideas never form in a vacuum, but are the product of interaction. Many people have con- tributed to this thesis, knowingly or unknowingly, and I’d like to acknowledge those who have provided encouragement, help, and inspiration. -

Yahoo Startup Shopping Spree Continues 4 July 2013, by Glenn Chapman
Yahoo startup shopping spree continues 4 July 2013, by Glenn Chapman Xobni goodness baked right in." Xobni products help manage email and other communications based on patterns of exchanges between people and their contacts. The acquisition continues a shopping spree launched after Marissa Mayer became chief of Yahoo a year ago. Yahoo on Tuesday announced it bought Qwiki, a New York operation behind an application that converts video and pictures on iPhones into sharable movie clips complete with music soundtracks. Yahoo on Wednesday continued a months-long take- over binge with word that it had bought Xobni, a startup The Qwiki buy announcement came a day after behind tools for better managing contact lists and email Yahoo put out word that it bought Bignoggins inboxes. Productions, a one-person operation specializing in fantasy sports applications for iPhones. Yahoo in June completed a billion-dollar deal taking Yahoo forged ahead Wednesday on its months- over the popular blogging platform Tumblr, a move long take-over binge with word that it had bought aimed at bringing more youthful users into the Xobni, a startup behind tools for better managing company's orbit. contact lists and email inboxes. Yahoo last month bought startup GhostBird Yahoo did not disclose how much it paid for Software, which makes picture-taking applications Xobni—which is 'inbox' spelled backwards—but saidfor iPhones, to enhance its Flickr photo service. it planned to use the startup's technology to improve Yahoo! Mail, Messenger and other Since former Google executive Mayer became "communications offerings." chief at Yahoo, the company has racked up a series of acquisitions including startups Alike, San Francisco-based Xobni was launched in 2006, Stamped, Snip.it and a Summly application built by and two years later the venture-backed firm hired a British teen. -

Patch Management Vendor and Application List
Patch Management Vendor and Application List Vendor Application 7-Zip 7-Zip 7-Zip 3 7-Zip 7-Zip 4 7-Zip 7-Zip 9 7-Zip 7-Zip 15 7-Zip 7-Zip 16 7-Zip 7-Zip 18 Acro Software Acro Software CutePDF Writer 2 Acro Software CutePDF Writer 3 Adobe Adobe Acrobat 5 Adobe Acrobat 6 Adobe Acrobat 7 Adobe Acrobat 8 Adobe Acrobat 9 Adobe Acrobat X Adobe Acrobat XI Adobe Acrobat DC Adobe Acrobat DC 17 Adobe Acrobat DC 18 Adobe Acrobat DC 19 Adobe Adobe Photoshop 11 Adobe Adobe Photoshop 12 Adobe Adobe Photoshop 13 Adobe Adobe Photoshop 15 Adobe Adobe Photoshop 16 Adobe After Effects 13.5 Adobe AIR Adobe AIR 2 Adobe AIR 3 Adobe AIR 4 Adobe AIR 13 Adobe AIR 14 Adobe AIR 15 Adobe AIR 16 Adobe AIR 17 Adobe AIR 18 Adobe AIR 19 Adobe AIR 20 Adobe AIR 21 Adobe AIR 22 Adobe AIR 23 Adobe AIR 24 Adobe AIR 25 Adobe AIR 26 Adobe AIR 27 Adobe AIR 28 Adobe AIR 30 Adobe AIR 31 Adobe AIR 32 Adobe Bridge 4 Adobe Bridge 5 Adobe Bridge CC Adobe Creative Cloud 3 Adobe Creative Cloud 4 Adobe Digital Editions 1 Adobe Digital Editions 2 Adobe Digital Editions 3 Adobe Digital Editions 4 Adobe Distiller 5 Adobe Distiller 6 Adobe Distiller 7 Adobe Dreamweaver 16 Adobe Elements 5 Adobe Elements 6 Adobe Elements 7 Adobe Fireworks CS6 Adobe Flash PPAPI MSI Adobe Flash Plugin MSI Adobe Flash MSI Adobe Flash Plugin Adobe Flash 5 Adobe Flash 6 Adobe Flash Plugin 6 Adobe Flash 7 Adobe Flash Plugin 7 Adobe Flash 8 Adobe Flash Plugin 8 Adobe Flash 9 Adobe Flash Plugin 9 Adobe Flash 10 Adobe Flash Plugin 10 Adobe Flash 11 Adobe Flash Plugin 11 Adobe Flash 12 Adobe Flash Plugin 12 Adobe -

Review, Email Clients with Source Code Editing
Review, Email Clients with Source Code Editing By Micheline Johnson Updated 2013-12-05 Why is source code editing desirable? It enables the addition of variable indenting and hanging indents, tables, images, charts, videos etc. the replacement of <p> tags with <div> tags, if para spacing is not required. Wikipedia lists most email clients. Of these, the free Windows or cross-platform GUI email clients are included in the Appendix. Of these, the current mainstream desktop GUI email clients include: 1. Outlook, overkill for most purposes, and is not free. 2. Outlook Express, not available for Windows 7 3. Windows Live Mail 4. Mozilla Thunderbird, does not natively support HTML editing or tables. 5. Eudora v7.1, runs on Microsoft Windows XP/2000 (http://www.eudora.com/download/). It has problems with Windows 7, see http://mcaf.ee/cxsw8 . It runs on Windows XP, and does not appear to support editing HTML source code, or tables. 6. Eureka Email. It is very difficult to uninstall, see http://mcaf.ee/1q0ka , so I did not test it. 7. Pegasus Mail. Pegasus v4.63 allows the insertion of a table and the editing of the number of rows or columns of that table; but it does not support editing of HTML source code. It supports hanging indents to increments of one tab spacing, which is very crude. 8. DreamMail 9. FoxMail 10. SeaMonkey. http://www.seamonkey-project.org/. Allows inserting of tables. Appears to allow insertion of HTML code, but does not allow viewing of the entire HTML source code. 11. Netscape Messenger used to have an HTML editor. -

Pourquoi Et Comment Récupérer L'en-Tête D'un Mail
Pourquoi et comment récupérer l’en-tête d’un mail ? Un mail comporte deux parties : 1. le corps du mail qui contient le message proprement dit ; 2. l’en-tête du mail qui laisse apparaître les adresses de l’émetteur et du/des destinataire(s), ainsi qu’une multitude d’informations techniques. Ce sont ces informations techniques qui sont utiles aux services de l’Assurance Maladie en charge du traitement des courriels frauduleux. Ce document vous permet de découvrir la marche à suivre pour récupérer l’en-tête d’un message, en fonction de votre type de messagerie. Celui-ci peut être copié dans un document Word. Vous disposez d’une messagerie : Free (Zimbra) Gmail Messagerie laposte.net Outlook.com / Hotmail Orange Orange Pro SFR Voila Yahoo Mail pour Mac OS IncrediMail Opera Mail Outlook Outlook 2010-2013 Outlook Express Thunderbird Windows Mail 1 Messagerie Free (Zimbra) - Faites un clic droit sur l'email concerné. - Cliquez sur « montrer l'original ». - Une nouvelle fenêtre apparaît affichant l'en-tête complet, ainsi que le code source du message. - Effectuez un copier-coller de tout le contenu, suivi du message. Messagerie Gmail - Ouvrez l'email concerné et cliquez sur « Afficher l'original » : - L'en-tête s'affiche dans une nouvelle fenêtre. - Sélectionnez et copiez toutes les lignes, ainsi que le contenu du message. 2 Messagerie laposte.net - Ouvrez l'email concerné. - Cliquez sur « Voir l'entête complet » : - Sélectionnez et copiez toutes les lignes, ainsi que le contenu du message. Messagerie Outlook.com / Hotmail - Sélectionnez l'email concerné. - Faites un clic droit sur ce message et sélectionnez « Afficher la source » : - Une nouvelle fenêtre s'ouvre, celle-ci contient l'en-tête complet. -
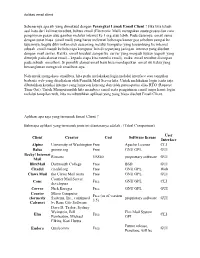
Sebenarnya Apa Sih Yang Dimaksud Dengan Perangkat Lunak Email Client
Aplikasi email client Sebenarnya apa sih yang dimaksud dengan Perangkat Lunak Email Client ? Jika kita telaah asal kata dari kalimat tersebut, bahwa email (Electronic Mail) merupakan suatu proses dan cara pengiriman pesan atau gambar melalui internet ke 1 org atau lebih. Pada dasarnya email sama dengan surat biasa (snail mail) yang harus melewati beberapa kantor pos sebelum sampai ke tujuannya, begitu dikirimkan oleh seseorang melalui komputer yang tersambung ke internet sebuah email masuk ke beberapa komputer lain di sepanjang jaringan internet yang disebut dengan mail server. Ketika email tersebut sampai ke server yang menjadi tujuan (seperti yang ditunjuk pada alamat email – kepada siapa kita menulis email), maka email tersebut disimpan pada sebuah emailbox. Si pemilik alamat email baru bisa mendapatkan email itu kalau yang bersangkutan mengecek emailbox-nya. Nah untuk mengakses emailbox, kita perlu melakukan login melalui interface atau tampilan berbasis web yang disediakan oleh Pemilik Mail Server kita. Untuk melakukan login tentu saja dibutuhkan koneksi internet yang lumayan kencang dan tidak putus-putus alias RTO (Request Time Out). Untuk Mempermudah kita membaca email serta pengiriman email tanpa harus login melalui tampilan web, kita membutuhkan aplikasi yang yang biasa disebut Email Client. Aplikasi apa saja yang termasuk Email Client ? Beberapa aplikasi yang termasuk jenis ini diantaranya adalah : (Tabel Comparison) User Client Creator Cost Software license Interface Alpine University of Washington Free Apache License CLI Balsa gnome.org Free GNU GPL GUI Becky! Internet Rimarts US$40 proprietary software GUI Mail BlitzMail Dartmouth College Free BSD GUI Citadel citadel.org Free GNU GPL Web Claws Mail the Claws Mail team Free GNU GPL GUI Courier Mail Server Cone Free GNU GPL CLI developers Correo Nick Kreeger Free GNU GPL GUI Courier Micro Computer Free (as of version (formerly Systems, Inc., continued proprietary software GUI 3.5) Calypso) by Rose City Software Dave D.