Internet Explorer 6 and 7 Users How and Why to Clear Your Cache
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Answering the Diagnostic Questions
Answering This Incident Report Guide is to help users answer the questions found on the Incident Report Form. the Diagnostic Questions The user may wish to provide the Incident Report form to the IT or CIO at their location to gather this information. In the case where they are not available, or the user is using a private laptop, we have provided this guide as means to help the user find the answers needed to best diagnose the issue at hand. If the user doesn’t already know how to take a screen shot of the issue, they can learn how here. CTRL+Click the Questions you wish to learn about: 1. How often does the issue occur? 2. What is your current operating system? 3. What internet browser were you using? 4. Is “compatibility mode” enabled in your internet browser? 5. What was your location when the issue occurred? 6. What type of internet connection were you using? 7. Are you not able to submit the review because of this issue? 8. What is the name of your antivirus software? 1. HowOnce often: The doesissue only the occurred issue occur? once. If this is the case, please try closing the portal and internet explorer completely and try again. Sporadic: The issue happens at random times. If this is the case, we will ask you to notice when it happens vs. when it doesn’t. Common patterns to look for are: “The issue only happens when I am on-site” or “I only get an error when I click “Store closed” Many: Issue reoccurs continually under certain circumstances. -

Questfields EXTRACT
QuestFields EXTRACT: Full-Page Web Applications and the MO Framework (Section 3 of the QuestFields Client Administration Guide) Legal Notices Copyright © 2009 by MasterObjects, Inc. All rights reserved. U.S. and international patents pending. MasterObjects, QuestObjects, QuestField, Questlet, QOP, and the Q Arrow logo are trademarks or registered trademarks of MasterObjects, Inc. (http://www.masterobjects.com) in the United States and other countries. Other trademarks used in this document are the property of their respective owners. Screen shots were used to the benefit of their respective copyright owners, for informational purposes only. Use of trademarks or screen shots is not intended to convey endorsement or other affiliation with MasterObjects. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher or copyright owner. MasterObjects has tried to make the information contained in this publication as accurate and reliable as possible, but assumes no responsibility for errors or omissions. MasterObjects disclaims any warranty of any kind, whether express or implied, as to any matter whatsoever relating to this publication, including without limitation the merchantability or fitness for any particular purpose. In no event shall MasterObjects be liable for any indirect, special, incidental, or consequential damages arising out of purchase or use of this -

Internet Explorer 11 Settings for Web Client
Internet Explorer 11 Settings for Web Client. Summary of Changes being performed: Change Compatibility View 1. Click on Tools, then Compatibility View Settings a. 2. Click Add and the web address will move down to the Websites box 3. Click Close 4. If the page does not refresh, close the tab and then reopen. Internet Explorer 11 Settings 1. Adding the site to the Trusted sites zone 2. Change the Security settings for the Trusted Sites. 1. To add the site to the Trusted Sites list. a. Click on Tools then Internet Options. Explorer 11 Settings Page 1 of 12 Joe Arcara b. c. Click on the Security tab. Explorer 11 Settings Page 2 of 12 Joe Arcara d. e. Select (click on) the Trusted Sites Zone f. Click on the Sites box. Explorer 11 Settings Page 3 of 12 Joe Arcara g. h. If the website https://direct.imagedepositgateway.com is not already in the Websites box, click on Add button to put the site on the list. If it is already in the Websites box, you do not need to do anything, just click Close. i. Explorer 11 Settings Page 4 of 12 Joe Arcara j. Click Close to return to the Security Tab. Explorer 11 Settings Page 5 of 12 Joe Arcara 2. Set Security for the Trusted Sites Zone. a. b. Click on Custom Level c. Set the Reset To: drop down list to Medium-low Explorer 11 Settings Page 6 of 12 Joe Arcara d. e. Click on Reset to set the level. f. g. -

Why Websites Can Change Without Warning
Why Websites Can Change Without Warning WHY WOULD MY WEBSITE LOOK DIFFERENT WITHOUT NOTICE? HISTORY: Your website is a series of files & databases. Websites used to be “static” because there were only a few ways to view them. Now we have a complex system, and telling your webmaster what device, operating system and browser is crucial, here’s why: TERMINOLOGY: You have a desktop or mobile “device”. Desktop computers and mobile devices have “operating systems” which are software. To see your website, you’ll pull up a “browser” which is also software, to surf the Internet. Your website is a series of files that needs to be 100% compatible with all devices, operating systems and browsers. Your website is built on WordPress and gets a weekly check up (sometimes more often) to see if any changes have occured. Your site could also be attacked with bad files, links, spam, comments and other annoying internet pests! Or other components will suddenly need updating which is nothing out of the ordinary. WHAT DOES IT LOOK LIKE IF SOMETHING HAS CHANGED? Any update to the following can make your website look differently: There are 85 operating systems (OS) that can update (without warning). And any of the most popular roughly 7 browsers also update regularly which can affect your site visually and other ways. (Lists below) Now, with an OS or browser update, your site’s 18 website components likely will need updating too. Once website updates are implemented, there are currently about 21 mobile devices, and 141 desktop devices that need to be viewed for compatibility. -
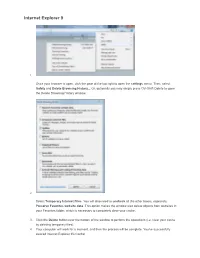
Internet Explorer 9
Internet Explorer 9 1. Once your browser is open, click the gear at the top right to open the settings menu. Then, select Safety and Delete Browsing History... Or, optionally you may simply press Ctrl-Shift-Delete to open the Delete Browsing History window. 2. Select Temporary Internet Files. You will also need to uncheck all the other boxes, especially Preserve Favorites website data. This option makes the window also delete objects from websites in your Favorites folder, which is necessary to completely clear your cache. 3. Click the Delete button near the bottom of the window to perform the operations (i.e. clear your cache by deleting temporary files). 4. Your computer will work for a moment, and then the process will be complete. You've successfully cleared Internet Explorer 9's Cache! Internet Explorer 8 1. Once your browser is open, click the Tools menu. Or, optionally you may simply press Ctrl-Shift-Delete to open the Delete Browsing History window (and skip step 2) 2. Click on Delete Browsing History... 3. Select Temporary Internet Files. 4. Click the Delete button near the bottom of the window to delete your temporary files (i.e. clear your cache). 5. If you want the browser to automatically clear the cache whenever you close it, click the Advanced tab. Click to check the box next to the Empty Temporary Internet Files folder when browser is closed option (in the section labeled Security). Click OK. This will delete everything except cookies. o Note: IE8 has a "feature" which retains some cookies even after you clear your cache if you do not UNCHECK the "Preserve Favorites Website Data." If you truly need to clear your cache, you will want to uncheck this! Internet Explorer 7 1. -

Find out Which Version of Internet Explorer You're Using This Information Applies to Windows Internet Explorer 7 and Windows Internet Explorer 8
The following instructions apply to both Windows 7 and Windows Vista. 1. Click the Start button . ! 2. Type "Programs and Features" in the search box or Click "Control Panel" and Click the icon "Programs !and Features". ! 3. Click "View installed updates" in the left panel. ! 4. Under "Uninstall an update", scroll down to the Microsoft Windows section. ! 5. Right-click "Windows Internet Explorer 9", click Uninstall, and then, when prompted, click Yes. ! 6. Click one of the following: ! o Restart now (to finish the process of uninstalling Internet Explorer 9 and restore the previous version of Internet Explorer). o Restart later Note: After you uninstall Internet Explorer 9, the previously installed version of Internet Explorer will be available on your PC. It isn't necessary to reinstall. Find out which version of Internet Explorer you're using This information applies to Windows Internet Explorer 7 and Windows Internet Explorer 8. To find out which version of Internet Explorer you're using, the cipher strength (SSL) it is using, the product identification number, or to see when the latest update was applied, follow these steps. 1. Open Internet Explorer by clicking the Start button , and then clicking Internet Explorer. ! 2. Press ALT+H, and then click About Internet Explorer. ! This information applies to Windows Internet Explorer 9 1. Open Internet Explorer by clicking the Start button . In the search box, type Internet Explorer, and then, in the list of results, click Internet Explorer. ! 2. Click the Tools button , and then click About Internet Explorer. ! . -

Policy Center Requirements Operating Systems: the Following Operating Systems Are Recommended to Access Policy Center
Policy Center Requirements Operating Systems: The following operating systems are recommended to access Policy Center. Operating Systems Supported: Microsoft Windows Vista SP2 Microsoft Windows 7 Microsoft Windows 8 Microsoft Windows 10 * *There are some known issues with these Operating Systems. For more details, see ‘Known Issues’ section below. Internet Browsers: The following browsers are required to access Policy Center. If you currently use an older Microsoft browser than listed, or a non-Microsoft browser, you may receive other errors or experience other unknown issues. Browsers Supported: 32-bit Microsoft Internet Explorer 7+ 32-bit Microsoft Internet Explorer 8+ * 32-bit Microsoft Internet Explorer 9+ * 32-bit Microsoft Internet Explorer 10+ * 32-bit Microsoft Internet Explorer 11+ * *There are some known issues with these browsers. For more details, see ‘Known Issues’ section below. Additional Requirements:** Adobe Reader version 7 or higher (or a similar PDF viewer) Guidewire Document Assistant ActiveX plug-in **Required to view system generated documents. Microsoft Office 2007 or 2010 is suggested to view all other documents. You are responsible for uploading policy documents to Policy Center before and after submission of the application. Upload only what is needed. Most file types are acceptable. All documents will be retained according to TWIA’s document retention policy. Claims Center Requirements Internet Browsers: To provide the best user experience it is recommended to use browsers that support HTML5 & CSS3. Claims Center is a web application accessed through a web browser. There are tiered levels of support for web browsers: Tier 1 includes browsers used in testing environments. Tier 2 includes browsers that can present the core functionality and content, but may not be pixel perfect and may not to perform as well as Tier 1 browsers. -

Internet Explorer and Firefox: Web Browser Features Comparision and Their Future
https://doi.org/10.48009/2_iis_2007_478-483 INTERNET EXPLORER AND FIREFOX: WEB BROWSER FEATURES COMPARISION AND THEIR FUTURE Siwat Saibua, Texas A&M University-Kingsville, [email protected] Joon-Yeoul Oh, Texas A&M University-Kingsville, [email protected] Richard A. Aukerman, Texas A&M University-Kingsville, [email protected] ABSTRACT Next to Netscape, which was introduced to the Internet technology is one of the utmost inventions of market in 1998, Mozilla Firefox was released in 2004 our era and has contributed significantly in to compete with IE. The software codes of Firefox distributing and collecting data and information. are in the open source format, and any software Effectiveness and efficiency of the process depends developers around the world can put their own ideas on the performance of the web browser. Internet into this browser. As a result, Firefox’s performance Explorer is the leader of the competitive browser effectiveness and efficiency improved every day and market with Mozzilla Fox as its strongest rival, which gained popularity rapidly. has been and is gaining a substantial level of popularity among internet users. Choosing the 100.00% superlative web browser is a difficult task due to the considerably large selection of browser programs and lack of tangible comparison data. This paper 90.00% describes and compares vital features of Internet Firefox Explorer and Mozzilla Firefox, which represent over 90% of the browser market. The performance of each 80.00% IE browser is evaluated based on the general features, operating system support, browser features, protocol 70.00% support and language support. -

Browser Tips for Peoplesoft
PeopleSoft User Guide: Browser Tips BROWSER TIPS FOR PEOPLESOFT TABLE OF CONTENTS Overview ............................................................................................................................................. 3 Preferred Browsers for Working in PeopleSoft .................................................................................... 3 Working in Financials and Human Resources Simultaneously ............................................................. 3 Browser Versions ................................................................................................................................ 3 Clearing Browser Cache ....................................................................................................................... 4 Why is it necessary to clear the browser cache?.................................................................................... 4 How to clear browser cache ................................................................................................................... 4 Allowing Pop-Up Windows in PeopleSoft ............................................................................................ 4 How to allow PeopleSoft pop-ups in Mozilla Firefox ............................................................................. 5 How to allow PeopleSoft pop-ups in Microsoft Internet Explorer (versions 9-11) ................................ 6 How to allow PeopleSoft pop-ups in Microsoft Edge ............................................................................ -

Web Design.” I Found Books on Everything from HTML to XML and from Web Graphics to Web Usability
Free ebooks ==> www.ebook777.com Free ebooks ==> www.ebook777.com Web Design: A Beginner’s Guide Second Edition www.ebook777.com Free ebooks ==> www.ebook777.com About the Author Wendy Willard is a designer, consultant, writer, and educator who has been involved in web design for about 15 years. She is the author of HTML: A Beginner’s Guide, Fourth Edition, and other books. Wendy is a graduate of Art Center College of Design in Pasadena, California. About the Technical Editor Kathi McCracken-Dente is a user experience strategist with an expertise in designing for e-commerce, communities, and web applications. Before starting McCracken Design, a web design agency in Oakland, California, she was a designer at frog design, Addwater, and Intuit. Her clients include Yahoo!, Intuit, PowerReviews, and LeapFrog. She is a graduate of Duke University and Art Center College of Design. Free ebooks ==> www.ebook777.com Web Design: A Beginner’s Guide Second Edition Wendy Willard New York Chicago San Francisco Lisbon London Madrid Mexico City Milan New Delhi San Juan Seoul Singapore Sydney Toronto Free ebooks ==> www.ebook777.com Copyright © 2010 by The McGraw-Hill Companies. All rights reserved. Except as permitted under the United States Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any means, or stored in a database or retrieval system, without the prior written permission of the publisher. ISBN: 978-0-07-170135-8 MHID: 0-07-170135-4 The material in this eBook also appears in the print version of this title: ISBN: 978-0-07-170134-1, MHID: 0-07-170134-6. -

Architectural Styles of Extensible REST-Based Applications
Institute for Software Research University of California, Irvine Architectural Styles of Extensible REST-based Applications Justin R. Erenkrantz University of California, Irvine [email protected] August 2006 ISR Technical Report # UCI-ISR-06-12 Institute for Software Research ICS2 110 University of California, Irvine Irvine, CA 92697-3455 www.isr.uci.edu www.isr.uci.edu/tech-reports.html Architectural Styles of Extensible REST-based Applications Justin R. Erenkrantz Institute for Software Research University of California, Irvine Irvine, CA 92697-3425 [email protected] ISR Technical Report # UCI-ISR-06-12 August 2006 Abstract: At the beginning of the World Wide Web (WWW or Web), there was no clear set of principles to guide the decisions being made by developers and architects. In these early days, a cacophony emerged without a clear direction to guide the evolution of the Web. If there was any direction during the inception of the Web, it was a weak focus on how communication might occur between machines on the Web and the content that was to be transferred. Within a matter of a few years, scalability and other design concerns threatened the future of the early Web - this led to the introduction of REpresentation State Transfer architectural style (REST). The REST style imposed constraints on the exchange of communication over the Web and provided guidance for further modifications to the underlying protocols. The introduction of REST, through the HTTP/1.1 protocol, restored order to the Web by articulating the necessary constraints required for participation. In this survey, we will characterize any environment that is governed by REST constraints to be in a RESTful world. -

Kenneth Arnes Ryan Paul Jaca Network Software Applications History
Kenneth Arnes Ryan Paul Jaca Network Software Applications Networks consist of hardware, such as servers, Ethernet cables and wireless routers, and networking software. Networking software differs from software applications in that the software does not perform tasks that end-users can see in the way word processors and spreadsheets do. Instead, networking software operates invisibly in the background, allowing the user to access network resources without the user even knowing the software is operating. History o Computer networks, and the networking software that enabled them, began to appear as early as the 1970s. Early networks consisted of computers connected to each other through telephone modems. As personal computers became more pervasive in homes and in the workplace in the late 1980s and early 1990s, networks to connect them became equally pervasive. Microsoft enabled usable and stable peer-to-peer networking with built-in networking software as early as 1995 in the Windows 95 operating system. Types y Different types of networks require different types of software. Peer-to-peer networks, where computers connect to each other directly, use networking software whose basic function is to enable file sharing and printer sharing. Client-server networks, where multiple end-user computers, the clients, connect to each other indirectly through a central computer, the server, require networking software solutions that have two parts. The server software part, running on the server computer, stores information in a central location that client computers can access and passes information to client software running on the individual computers. Application-server software work much as client-server software does, but allows the end-user client computers to access not just data but also software applications running on the central server.