Worked World Page 18
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Blühender Baum Beim Oberbühlchnubel Bei Wynigen
Rondo-Kurier Jahrgang: 20 Juni 2016 Blühender Baum beim Oberbühlchnubel bei Wynigen Das ist das Informationsorgan des Alters- und Pflegezentrums Rondo Safenwil für seine Bewohnerinnen und Bewohner sowie deren Angehörige. 1 Inhaltsverzeichnis Inhaltsverzeichnis 2 Worte der Zentrumsleiterin 3 Geburtstage im Mai 4 Personelles 5 Portrait Nicola Eichholzer / Veranstaltungen 6 Seniorennachmittag 7 Ja, wir kommen gerne! 8 Safenwil im Laufe der Zeit 10 Menüplan Spezialitätenwoche 13 Ausflug mit der Jassgruppe der ref. Kirchgemeinde 15 Impressionen aus der Aktivierung 17 Muttertag 20 Zofingen etwas anders gesehen 22 Rüeblimuffins 23 Impressum 24 2 Die Farben unserer Handlungen hängen von der Farbe unserer Stimmung ab wie die Farben einer Landschaft vom jeweiligen Licht Francis Bacon Liebe Leserinnen und Leser Was kommt Ihnen zuerst in den Sinn, wenn Sie an den Sommer denken? Grillieren am See? Familienferien am Meer? Egal, welche Bilder Ihnen gerade durch den Kopf gehen: Die einzigartige Stim- mung lebt neben den Gerüchen und Geräuschen vor allem von der Farbe. Wenn sich im Frühsommer die zunehmend stärkere Sonne mit ge- legentlichen Regengüssen und ersten Gewittern abwechselt, ge- deiht die Natur prächtig und strotzt geradezu vor Lebenskraft. Zwit- schernde Vögel und summende Bienen verbreiten ein Gefühl von Entspannung und Gemütlichkeit, das von dem allgegenwärtigen Grün noch zusätzlich unterstützt wird. Geniessen Sie dieses ange- nehme Gefühl und gehen Sie mit offenen Augen durch die Land- schaft. Marlis Businger, Zentrumsleiterin 3 Geburtstage im Juni Herr Hans Burgener Frau Margrit Thommen 2. Juni 1928 3. Juni 1927 Frau Elsy Zimmerli Frau Margrit Dietrich 4. Juni 1930 25. Juni 1938 4 Personelles Austritte im Mai Felder Stefanie Pflegehelferin SRK Oehler Elisabeth Mitarbeiterin Lingerie Rittgasser Krisztina Mitarbeiterin Hauswirtschaft Lieb Bruno Pflegefachmann HF Jubiläum 5 Jahre / 15 Jahre Rondo Am 1. -

Karl Barth's Contribution to the German Church Struggle Against National
Karl Barth’s contribution to the German Church struggle against National Socialism Ramathate Dolamo Department of Philosophy and Systematic Theology, University of South Africa, Pretoria, South Africa Abstract Germany was under a totalitarian regime led by Adolf Hitler from 1933 to 1945. This article looks at the responses of the churches in Germany during that period. In particular, Karl Barth’s theology on church and state is examined to determine to what extent it did assist Germany in fighting National Socialism and in rebuilding Germany after the war. The author is of the view that most of Barth’s insights could be relevant and would be applicable today especially in those countries that are still being ruled by autocrats and dictators. Introduction Not only do theologians differ as to whether the (divine) com- mand should be grounded in the Christology or in the “orders of creation”, but also some theologians appear unwilling to recognise that the command is the ground and the instrument of God’s creative will of love both in originating and in sustaining creation in its historical development (Maimela 1984:158). Karl Barth’s views on sociopolitical matters especially those on church and state relations that he started to formulate during his Safenwil pastorate in 1911 were put to the harshest and rigorous test during the reign of Adolf Hitler from 1933 to the end of World War II in 1945. This article is an appre- ciation of the insights of Barth as a theologian and as an activist during the church struggle in Germany against National Socialism. -

Kreisspieltag STV Staffelbach
Kreisspieltag STV Staffelbach 18. / 19. August 2007 auf dem Höchacker in Safenwil Kreisspieltag STV Staffelbach 2007 2 Kreisspieltag STV Staffelbach 2007 Kreisspieltag Jugend und Aktive 18. / 19. August 2007 auf dem Sportplatz Höchacker in Safenwil Willkommen Geschätzte Kinder, Turnerinnen, Turner, Gäste und Zuschauer Der STV Staffelbach möchte alle herzlich Willkommen heissen am Kreisspieltag des Zofinger Kreisturnverbandes. Da wir in Staffelbach nicht über die nötige Infrastruktur verfügen, dürfen wir Gastrecht in Safenwil geniessen. Welchen Stellenwert hat der Kreisspieltag? Geht es nur um den Wettkampf? Nein, am Kreisspieltag treffen sich die turnenden Vereine aus dem Zofinger Kreisturnverband. Neben dem Kräftemessen in den verschiedenen Disziplinen haben aber auch die Gemütlichkeit und das gemeinsame Erlebnis des Teamsports einen grossen Stellenwert. Am Abend haben alle etwas gewonnen, sei es auch nur die Freude an der sportlichen Betätigung unter freiem Himmel. An dieser Stelle möchten wir uns bei allen Sponsoren, Helfern, Gönnern, Funktionären und OK-Mitgliedern für Ihren unermüdlichen Einsatz bedanken. Ein ganz besonderer Dank gilt der Gemeinde Safenwil, die uns den Sportplatz Höchacker für den Kreisspieltag zur Verfügung stellt. Ohne das grosszügige Entgegenkommen hätten wir vom STV Staffelbach diesen Kreisspieltag nicht durchführen können. Wir möchten es nicht unterlassen Euch viel Glück, Erfolg und vor allem viel Freude bei den Spielen und Wettkämpfen zu wünschen. Mit Turnergrüssen OK Kreisspieltag Turnverein STV Staffelbach 3 Kreisspieltag STV Staffelbach 2007 Kreisspieltag STV Staffelbach auf dem Höchacker in Safenwil 2007 Jugendspieltag Samstag 18. August Spieltagleitung Siegrist Patrik, Bütikofer Hans Speaker Morgenthaler Silvia Rechnungsbüro Röcker Christoph Aktivspieltag Sonntag 19. August Spieltagleitung Röcker Christoph Speaker Morgenthaler Silvia Indiaca / Schnurball Meyer Elisabeth Parkplätze sind signalisiert (Achtung auf Wiese) bzw. -

Herzlichen Dank
Spielerische Experimente Herzlichen Dank Ein grosses Dankeschön an alle unsere Sponsoren, Behörden, Auf der grossen, rund sieben Kilometer langen Route laden Vereine, Institutionen und Gönner, welche das Pionierprojekt zehn Stationen mit kleinen, spielerischen Experimenten zum Atem-Weg unterstützen. ATEM-WEG bewussten Atmen ein. Barfuss kann man ein speziell herge- Richtig atmen. Besser leben. richtetes Terrain erforschen, bei einem kurzen Aufstieg die Atemfrequenz spüren und den eigenen Rhythmus nden Hauptsponsoren: oder beim Balancieren den eigenen Atem beobachten. Die einfachen Aufgaben werden kurz auf Tafeln erklärt, der Weg ist gut ausgeschildert. Generalagentur Zofingen 160412S07GA_A7_Logo_inkl_GA_Zofingen.indd 1 13.04.16 07:51 Wer nicht so weit gehen mag, kann eine kürzere Route wählen oder auch gezielt einzelne Wegpunkte angehen. Eine Sponsoren: gepegte Feuerstelle zum Abschluss des Lehrpfades bietet Gelegenheit zum Verweilen. Ich bin ein CMYK-Logo und komme bei Vierfarbendruck zum Einsatz. Atem heisst leben, 2 Fussparcours 4 Atem-Kraft Bänkli leben heisst atmen. ATEM-WEG ATEM-WEG Richtig atmen. Besser leben. Richtig atmen. Besser leben. Atem-Reaktion Innere Bewegung – Bleibe einen Moment ruhig stehen. Atempausee Spüre deinen Atem und lese die Anleitung. Bleibe einen Moment ruhig stehen. Spüre deinen Atem und lese die Anleitung. Erkunde Barfuss, in kleinen Schritten diesen Fussparcours. Balanciere durch Gewichtsverlagerung Die Inhalte eines Atemzugs bedeuten im abwechselnd auf einem Bein zum andern. Alltag annehmen, abgeben, ruhen! Der kleine Beachte die Reaktion deines Atems. Rhythmus in die grosse Welt! · Kanton Aargau, Dep. Bau, · Gemeinde Oftringen Gewinn: Füsse werden durch unterschiedliche Boden- Setze dich aufrecht auf die Bank, die Füsse strukturen aktiviert, Blutkreislauf und damit fest auf dem Boden. Lege die Hände auf Verkehr und Umwelt · Gemeinde Uerkheim Füsse und Beine belebt. -

3 Gruppenschiessen Im Suhrental
3 GruppenschiessenSehr kurze Wegstrecken im Suhrental von Platz zu Platz 16. Chnöbeli-Chopf-Schiessen Feldschützengesellschaft Moosleerau Schiessanlage Moosleerau 8. Sodhubelschiessen Schützengesellschaft Safenwil Schiessanlage „im Boden“ Safenwil 2. Wili-Bärger-Schiesse Schützengesellschaft Wiliberg-Hintermoos Schiessanlage „Hargarten“ Reitnau war Schiessplatz Aarg. Kant. Schützenfest 2017 Gewehr 300 m Gruppenwett- Scheibe A 10 kampf 2 Schüsse Probe 6 Schüsse Einzel 4 Schüsse Einzel am Schluss gezeigt, ohne Zeitbeschränkung Auszahlungsstich kombiniert mit Gruppenstich auf allen 3 Schiessplätzen Gruppenwettkampf Gewehr 300 m Sportgeräte: alle Gewehre Trefferfeld Scheibe A 10 Schiessprogramm: 2 Schüsse Probe, obligatorisch 6 Schüsse Einzel 4 Schüsse Einzel, am Schluss gezeigt Stellungen: Freigewehr nicht liegend, Standartgewehr und Karabiner liegend frei, Sturmgewehre ab Zweibeinstütze. Veteranen und Seniorveteranen dürfen mit dem Karabiner liegend aufgelegt oder mit dem Freigewehr liegend frei schiessen. Teilnahmegebühr: Fr. 24.00 (inklusive Munition und Gebühren) Fr. 20.00 für Junioren (U17 / U 21) Teilnahmekosten Gruppe: Keine Auszeichnungen: Honig 500 g (Moosleerau und Reitnau) bzw. Bergkristall (in Safenwil) im Wert von Fr. 12.00, oder Kranzkarte AGSV, Wert Fr. 10.00 E / S V / U21 SV / U17 Kat. A Freigewehre, E / S StandartgewehreV / U21 SV / U17 90 88 87 Kat. A:D Freigewehre,Stgw 57/03 Standartgewehre 90 Pkt. 8688 Pkt. 8784 Pkt. 83 Kat. D: Stgw 57/03 86Pkt. 84 Pkt. 83Kat. Pkt. E Stgw 57/02, Stgw 90, Karabiner 84 82 81 Kat. E: Stgw 57/02, Stgw 90, Karabiner 84 Pkt. 82 Pkt. 81 P Gruppenwettkampf: Je 5 lizenzierte Schützen eines Vereins bilden eine Gruppe. Gruppenwettkampf in 2 Kategorien. Kat. A Sport alle Gewehre, Kat. D alle Ordonanzgewehre Rangordnung: Das Total der 5 Einzelresultate bestimmt den Rang. -

Cultivated Light – People –Space –People Light 25.04.18 14:14 Ribag.Com @Ribaglight Ribaglight
cultivated Light – People – Space 1 – 18 XX_Umschlag culti 01-18_e.indd 1 25.04.18 14:14 ribag.com @ribaglight ribaglight XX_Umschlag culti 01-18_e.indd 2 25.04.18 14:14 EDITORIAL uman Centric Lighting is currently the most with regional partners. For optimal results, user used term in the lighting industry. Each requirements and solution-orientation need to H individual person is central – their needs remain centre stage. Products are tailored to re- are reflected in the lighting. Lighting solutions spective projects and assembled as usual with are as varied as individual requirements. Techno- quality service standards. logical requirements for lighting fixtures, such as Therefore, keeping the individual at the centre, is light distribution, desired lighting colour, intensi- the focus of this issue of "cultivated". It presents ty, absence of glare, and the aspect of biological individualised lighting solutions from the Draft rhythms, not only require external adjustments & Craft Collection, and provides an insight into a to design and lighting style, but also in usability. new floor lamp design with different light presen- tation possibilities and tells us of regional part- With its Draft & Craft Collection, RIBAG is taking a nerships, which focus on craftsmanship. It also groundbreaking step into the future. Tailor-made reports on young talent in the field of design, and lighting solutions perfectly display high-quality displays fascinating examples of architecture in design and solution expertise and subsequent- both the private and public sectors, in which indi- ly meet specific needs to the greatest degree. vidualised lighting solutions optimally accompany First-class craftsmanship is combined with the users through their everyday life. -

FEDRO Roads and Traffic 2012
Schweizerische Eidgenossenschaft Confédération suisse Confederazione Svizzera Confederaziun svizra Swiss Confederation Swiss Federal Roads Office FEDRO FEDRO 2012 Roads and Traffic Facts and figures Contents 3 Editorial 4 – 6 Energy Saving energy – but not at the cost of safety 7 Solar power production on noise-prevention barriers 8 – 9 Pedestrian crossings Accidents on pedestrian crossings during winter 10 – 13 Traffic noise Noise reduction in the interest of our health 14 – 15 CO2 emissions Lower CO2 emissions from cars to protect the climate 16 – 17 Operation and safety Cables are vital motorway components 18 Road signs Useful information on 900 road signs 20 – 21 Archaeology/Palaeontology Neanderthals and dinosaurs beneath the motorways 22 – 23 FEDRO unearths “Jurassic Park” on the A16 24 – 25 Federal network resolution Main roads to be added to the motorway network 26 – 27 Roadworks in 2012 Major roadworks 28 Personnel Changes in FEDRO management Facts and figures 30 Motorway network 1,798.7 kilometres of motorway completed 31 The Swiss motorway network 32 Administrative measures Number of confiscated licences down again 33 Accumulated kilometres 26 billion kilometres on the motorways 34 – 35 Traffic volume Map of traffic volume on the motorway network 36 – 37 Transalpine goods traffic Unchanged volume of goods traffic through the Alps 38 Vehicle statistics Total registered vehicles rose by 121,000 in 2011 39 New registrations of cars in 2011 40 Accident statistics Fewer accident victims on Swiss roads 41 Finance Finance and expenditure 42 Structure of FEDRO Organisational chart of the Federal Roads Office 43 Addresses Addresses of FEDRO and regional units 44 Cantonal police headquarters 45 Road traffic departments Cover photo Every four years, the condition of the surfaces of the motorways is checked with the aid of laser technology. -

Hohe Lebensqualität in Einem Leistungsfähigen Wirtschaftsraum
DIE REGION ZOFINGEN HOHE LEBENSQUALITÄT IN EINEM LEISTUNGSFÄHIGEN WIRTSCHAFTSRAUM Bericht zum regionalen Entwicklungs- konzept der Region Zofingen REK Stand August 2002 1 KURZFASSUNG FÜR DEN EILIGEN LESER WELCHE REGION ZOFINGEN WOLLEN WIR? Wir wollen eine Region Zofingen, die in einem leistungsfähigen Wirt- schaftsraum eine hohe Lebensqualität bietet. Einen Lebensraum, in dem Wirtschaft, Freizeit und das Zusammenleben von Jung und Alt in einer herzlichen Atmosphäre Platz haben. Einen Lebensraum, wo Gäste will- kommen sind. Einen Lebensraum, wo anstehende Aufgaben gemeinde- übergreifend gelöst werden. Die Voraussetzungen dafür sind gegeben, aber die zukünftige Entwicklung darf nicht dem Zufall überlassen wer- den. Der Standortwettbewerb unter den Regionen wird immer härter, und der Entwicklungsdruck auf unsere Region ist unter anderem durch die her- vorragende zentrale Lage spürbar gewachsen. In der Region Zofingen soll die Zukunft aktiv gestaltet werden, denn Passivität führt nicht zum Ziel. Deshalb haben der Verein Vision Region Zofingen und der Regionalverband Wiggertal-Suhrental mit dem regio- nalen Entwicklungskonzept (REK) ein Instrument geschaffen, welches die zukünftige Raumentwicklung nicht sich selbst überlässt, sondern eine räumliche Struktur mit eigenständiger Identität und guter Lebens- qualität schafft. Mit dem Regionsmarketing als Bestandteil des REK kann sich die Region Zofingen im Wettbewerb der Regionen klarer positionie- ren, und die wirtschaftlichen Chancen der Region werden nachhaltig gestärkt. Der Wandel muss von innen kommen. Um die Zukunft der Region aktiv zu gestalten, braucht es den Willen aller Gemeinden mit ihren Behörden. Wir sind überzeugt, dass wir gemeinsam mit dem regionalen Entwick- lungskonzept eine Bewegung auslösen können, die unsere Region Zofingen in eine prosperierende Zukunft führt. URS LOCHER MARTIN BASLER Präsident RVWS Präsident Vision Region Zofingen INHALT I Kurzfassung für den eiligen Leser 5 IV Kurzbericht Konzept Raumentwicklung 16 1. -

Ordonnance Sur La Protection En Cas D'urgence Au Voisinage Des
732.33 Ordonnance sur la protection en cas d’urgence au voisinage des installations nucléaires (Ordonnance sur la protection d’urgence, OPU) du 20 octobre 2010 (Etat le 1er janvier 2014) Le Conseil fédéral suisse, vu les art. 5, al. 4, et 101, al. 1, de la loi du 21 mars 2003 sur l’énergie nucléaire (LENu)1, vu l’art. 75, al. 1, de la loi du 4 octobre 2002 sur la protection de la population et sur la protection civile (LPPCi)2, arrête: Section 1 Dispositions générales Art. 1 Champ d’application 1 La présente ordonnance règle la protection d’urgence en cas d’événement surve- nant dans une installation nucléaire suisse au cours duquel le rejet d’une quantité non négligeable de radioactivité ne peut être exclu. 2 Les installations nucléaires soumises à la présente ordonnance sont désignées dans l’annexe 1. Art. 2 But de la protection d’urgence La protection d’urgence vise à: a. protéger la population et son milieu de vie; b. assister temporairement la population touchée et lui assurer l’indispensable; c. limiter les effets d’un événement. RO 2010 5191 1 RS 732.1 2 RS 520.1 1 732.33 Energie nucléaire Section 2 Zones Art. 3 Principe 1 Le territoire au voisinage d’une installation nucléaire est réparti en deux zones: a. la zone 1 couvre l’aire proche de l’installation nucléaire où une défaillance grave peut causer un danger exigeant des mesures immédiates de protection de la population; b. la zone 2 est contiguë à la zone 1 et couvre l’aire où une défaillance grave de l’installation nucléaire peut causer un danger exigeant des mesures de pro- tection de la population. -
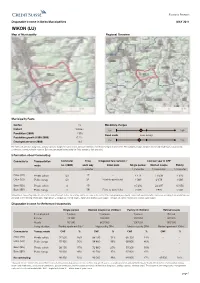
WIKON (LU) Map of Municipality Regional Overview
Economic Research Disposable Income in Swiss Municipalities MAY 2011 WIKON (LU) Map of Municipality Regional Overview Municipality Facts Canton LU Mandatory charges District Willisau low high Population (2009) 1'359 Fixed costs Swiss average Population growth (1999-2009) 0.1% low high Employed persons (2008) 753 The fixed costs comprise: living costs, ancillary expenses, charges for water, sewers and waste collection, cost of commuting to nearest center. The mandatory charges comprise: Income and wealth taxes, social security contributions, mandatory health insurance. Both are standardized figures taking the Swiss average as their zero point. Information about Commuting Commute to Transportation Commuter Time Integrated fare network / Cost per year in CHF mode no. (2000) each way travel pass Single person Married couple Family in minutes 1 commuter 2 commuters 1 commuter Olten (SO) Private vehicle 23 17 - 4'414 11'539 4'576 Olten (SO) Public transp. 23 24 Point-to-point ticket 1'089 2'178 1'089 Basel (BS) Private vehicle 4 49 - 10'492 24'437 10'956 Basel (BS) Public transp. 4 58 Point-to-point ticket 2'286 4'572 2'286 Information on commuting relates to routes to the nearest relevant center. The starting point in each case is the center of the corresponding municipality. Travel costs associated with vehicles vary according to household type and are based on the following vehicle types: Single person = compact car, married couple = higher-price-bracket station wagon + compact car, family: medium-price-bracket station wagon. Disposable Income for Reference Households Single person Married couple (no children) Family (2 children) Retired couple In employment 1 person 2 persons 1 person Retired Income 75'000 250'000 150'000 80'000 Assets 50'000 600'000 300'000 300'000 Living situation Rented apartment 60m2 High-quality SFH Medium-quality SFH Rented apartment 100m2 Commute to Transp. -

Ordonnance Sur La Protection En Cas D'urgence Au
Ordonnance sur la protection en cas d’urgence au voisinage des installations nucléaires (Ordonnance sur la protection d’urgence, OPU) Modification du 20 novembre 2015 L’Inspection fédérale de la sécurité nucléaire, vu l’art. 5, al. 2, de l’ordonnance du 20 octobre 2010 sur la protection d’urgence (OPU)1, arrête: I L’annexe 3 de l’OPU est remplacée par la version ci-jointe. II La présente ordonnance entre en vigueur le 1er janvier 2016. 20 novembre 2015 Inspection fédérale de la sécurité nucléaire: Hans Wanner 1 RS 732.33 2015-3032 4945 O sur la protection d’urgence RO 2015 Annexe 3 (art. 3, al. 2) Communes situées dans les zones 1 et 2, avec leurs secteurs de danger Désignation des centrales nucléaires: B/L – Beznau/Leibstadt G – Gösgen M – Mühleberg Commune District Zone 2 Secteurs de danger 1 2 3 4 5 6 Canton CN Zone 1 Aarau Aarau AG G X X X Aarberg Seeland BE M X X Aarburg Zofingen / Zofingue AG G X X Aegerten Biel/Bienne BE M X X Alterswil Sense FR M XX Altishofen Willisau LU G X X Ammerswil Lenzburg AG G X X Anwil Sissach BL G X X Arboldswil Waldenburg BL G X X Attelwil Zofingen / Zofingue AG G X X Auenstein Brugg AG B/L X X Auenstein Brugg AG G X X Avenches La Broye-Vully VD M X X Bachs Dielsdorf ZH B/L XX Bad Zurzach Zurzach AG B/L X X X Baden Baden AG B/L XX Baldingen Zurzach AG B/L XX X Barberêche See / du Lac FR M X X Bargen (BE) Seeland BE M X X X Belfaux (seul Cutterwil) La Sarine FR M X X Bellmund Biel/Bienne BE M X X Belp Bern-Mittelland BE M X X Bennwil Waldenburg BL G X X Bern/Berne Bern-Mittelland BE M X X Biberstein Aarau -

Schutzengel Über Safenwil Newsletter Feuerwehrwesen Nr. 2/2009
Newsletter F euerwehrwesen Nr. 2/2009 Schutzengel über Safenwil (Text eingereicht von David Bürge, Chef Ausbildung, Feuerwehr Safenwil) Bericht aus Sicht des Einsatzleiters David Bürge Während der Mittagszeit vom Samstag, 28. November 2009, wurde die Bevölkerung durch eine Deto- nation erschreckt. Nach dem zweiten Knall läuteten bereits die Telefone der Angehörigen der Feuer- wehr Safenwil. „12:27 Brand-Gross, in Safenwil, Köllikerstrasse, Gasdepot“ hiess die Alarmmeldung. Während der Fahrt ins Magazin erlebte ich die gewaltigen Explosionen von Gasflaschen bei der Firma Jäggi AG. Die angehaltenen Autos sowie die herumstehenden Menschen erschwerten meine Weiter- fahrt massiv. Meinen Entscheid, die Fahrt ins Magazin vorzunehmen, musste ich vor der Durchfahrt der Liegenschaft Jäggi streichen. Die Situation vor Ort zwang mich sofort zum Handeln. Ich musste Passanten für die erste Strassensperre beiziehen, verschiedene Automobilisten waren mit dieser aus- sergewöhnlichen Situation überfordert. Dank einer Begehung der Autogastankstelle Jäggi im Oktober 2009 durch unsere Kommandogruppe war mir bekannt, dass der 6,4 m³ grosse Propangastank (war zu 76 % gefüllt) mit einer manuell zu bedienenden Berieselungsanlage ausgerüstet ist. Ich stellte fest, dass die Behälterkühlung bereits in Betrieb gesetzt wurde. Als mir das Ausmass des Ereignisses zu diesem Zeitpunkt bereits bewusst war, eilte ich in Richtung des anrückenden Tanklöschfahrzeuges der Feuerwehr Safenwil. Mit genügend sicherer Distanz stellte der Fahrer dieses in Position. Der Beifahrer meldete sich bei mir und wurde über das Ausmass informiert. Die ersten Sofortmassnahmen (Nachalarmierung, SBB stromlos, Aufgebot Stützpunkt Zofingen etc.) wurden durch diesen Offizier ausgelöst. Weitere Offiziere meldeten sich in der Zwischenzeit bei mir. Um den Übergriff auf die Firma RIBAG Licht AG zu verhindern, wurde per Funk der Feuerwehr Kölliken (wird bei Grossalarm automatisch aufgeboten) ein Abschnitt zugeteilt.