Jural Quorate
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Syllabus of Arts Education
SYLLABUS OF ARTS EDUCATION 2008 National Council of Educational Research and Training Sri Aurobindo Marg, New Delhi - 110016 Contents Introduction Primary • Objectives • Content and Methods • Assessment Visual arts • Upper Primary • Secondary • Higher Secondary Theatre • Upper Primary • Secondary • Higher Secondary Music • Upper Primary • Secondary • Higher Secondary Dance • Upper Primary • Secondary • Higher Secondary Heritage Crafts • Higher Secondary Graphic Design • Higher Secondary Introduction The need to integrate art s education in the formal schooling of our students now requires urgent attention if we are to retain our unique cultural identity in all its diversity and richness. For decades now, the need to integrate arts in the education system has been repeatedly debated, discussed and recommended and yet, today we stand at a point in time when we face the danger of lo osing our unique cultural identity. One of the reasons for this is the growing distance between the arts and the people at large. Far from encouraging the pursuit of arts, our education system has steadily discouraged young students and creative minds from taking to the arts or at best, permits them to consider the arts to be ‘useful hobbies’ and ‘leisure activities’. Arts are therefore, tools for enhancing the prestige of the school on occasions like Independence Day, Founder’s Day, Annual Day or during an inspection of the school’s progress and working etc. Before or after that, the arts are abandoned for the better part of a child’s school life and the student is herded towards subjects that are perceived as being more worthy of attention. General awareness of the arts is also ebbing steadily among not just students, but their guardians, teachers and even among policy makers and educationalists. -

20Years of Sahmat.Pdf
SAHMAT – 20 Years 1 SAHMAT 20 YEARS 1989-2009 A Document of Activities and Statements 2 PUBLICATIONS SAHMAT – 20 YEARS, 1989-2009 A Document of Activities and Statements © SAHMAT, 2009 ISBN: 978-81-86219-90-4 Rs. 250 Cover design: Ram Rahman Printed by: Creative Advertisers & Printers New Delhi Ph: 98110 04852 Safdar Hashmi Memorial Trust 29 Ferozeshah Road New Delhi 110 001 Tel: (011) 2307 0787, 2338 1276 E-mail: [email protected] www.sahmat.org SAHMAT – 20 Years 3 4 PUBLICATIONS SAHMAT – 20 Years 5 Safdar Hashmi 1954–1989 Twenty years ago, on 1 January 1989, Safdar Hashmi was fatally attacked in broad daylight while performing a street play in Sahibabad, a working-class area just outside Delhi. Political activist, actor, playwright and poet, Safdar had been deeply committed, like so many young men and women of his generation, to the anti-imperialist, secular and egalitarian values that were woven into the rich fabric of the nation’s liberation struggle. Safdar moved closer to the Left, eventually joining the CPI(M), to pursue his goal of being part of a social order worthy of a free people. Tragically, it would be of the manner of his death at the hands of a politically patronised mafia that would single him out. The spontaneous, nationwide wave of revulsion, grief and resistance aroused by his brutal murder transformed him into a powerful symbol of the very values that had been sought to be crushed by his death. Such a death belongs to the revolutionary martyr. 6 PUBLICATIONS Safdar was thirty-four years old when he died. -

Price List 2015.Indd
Lalit Kala Publications 2015 Lalit Kala Akademi Rabindra Bhavan, New Delhi-110001 MONOGRAPHS The monographs in the Lalit Kala Series of Contemporary Indian Art have been undertaken by the Lalit Kala Akademi with the intention of popularising the works of India’s leading painters, sculptors and printmakers. Effort is made to present a bird’s eye view of the development of their artistic career. Each monograph is in the format 17.5 x 12 cms. on foreign art paper. It contains a brief introduction of the artist along with colour plates and b/w illustrations. Monographs Available Rs. 1. Dhanraj Bhagat 50 2. Prodosh Das Gupta 50 3. Biren De 50 4. L. Munuswamy 50 5. K. S. Kulkarni 50 6. Ram Gopal Vijaiwargiya 50 7. S. H. Raza 50 8. Y. K. Shukla 50 9. Ranvir Singh Bisht 50 10. V. P. Karmarkar 50 11. Bimal Das Gupta 50 12. Radhamohan 50 13. Sarat Chandra Debo 50 14. Goverdhan Lal Joshi 50 15. P. T. Reddy 50 16. K. Madhava Menon 50 17. Nicholas Roerich 50 18. Amarnath Sehgal 50 19. Chittaprosad 50 20. Kanwal Krishna & Devyani Krishna 50 21. J. Swaminathan 50 22. Gurcharan Singh 50 23. Piraji Sagara 50 24. M. Reddappa Naidu 50 25. Devki Nandan Sharma 75 26. A. P. Santhanaraj 75 27. R. K. Rao 75 28. Balbir Singh Katt 75 29. Sakti Burman 75 30. Kripal Singh Shekhawat 75 Monographs Large Format (Hard Bound 9”x9”) 31. J. Sultan Ali 100 32. Pilloo Pochkhanawala 100 33. Somnath Hore 100 34. V. S. Gaitonde 100 35. -

List of Officers Who Attended Courses at NCRB
List of officers who attened courses at NCRB Sr.No State/Organisation Name Rank YEAR 2000 SQL & RDBMS (INGRES) From 03/04/2000 to 20/04/2000 1 Andhra Pradesh Shri P. GOPALAKRISHNAMURTHY SI 2 Andhra Pradesh Shri P. MURALI KRISHNA INSPECTOR 3 Assam Shri AMULYA KUMAR DEKA SI 4 Delhi Shri SANDEEP KUMAR ASI 5 Gujarat Shri KALPESH DHIRAJLAL BHATT PWSI 6 Gujarat Shri SHRIDHAR NATVARRAO THAKARE PWSI 7 Jammu & Kashmir Shri TAHIR AHMED SI 8 Jammu & Kashmir Shri VIJAY KUMAR SI 9 Maharashtra Shri ABHIMAN SARKAR HEAD CONSTABLE 10 Maharashtra Shri MODAK YASHWANT MOHANIRAJ INSPECTOR 11 Mizoram Shri C. LALCHHUANKIMA ASI 12 Mizoram Shri F. RAMNGHAKLIANA ASI 13 Mizoram Shri MS. LALNUNTHARI HMAR ASI 14 Mizoram Shri R. ROTLUANGA ASI 15 Punjab Shri GURDEV SINGH INSPECTOR 16 Punjab Shri SUKHCHAIN SINGH SI 17 Tamil Nadu Shri JERALD ALEXANDER SI 18 Tamil Nadu Shri S. CHARLES SI 19 Tamil Nadu Shri SMT. C. KALAVATHEY INSPECTOR 20 Uttar Pradesh Shri INDU BHUSHAN NAUTIYAL SI 21 Uttar Pradesh Shri OM PRAKASH ARYA INSPECTOR 22 West Bengal Shri PARTHA PRATIM GUHA ASI 23 West Bengal Shri PURNA CHANDRA DUTTA ASI PC OPERATION & OFFICE AUTOMATION From 01/05/2000 to 12/05/2000 1 Andhra Pradesh Shri LALSAHEB BANDANAPUDI DY.SP 2 Andhra Pradesh Shri V. RUDRA KUMAR DY.SP 3 Border Security Force Shri ASHOK ARJUN PATIL DY.COMDT. 4 Border Security Force Shri DANIEL ADHIKARI DY.COMDT. 5 Border Security Force Shri DR. VINAYA BHARATI CMO 6 CISF Shri JISHNU PRASANNA MUKHERJEE ASST.COMDT. 7 CISF Shri K.K. SHARMA ASST.COMDT. -

Chandigarh – the Pioneer
( ) > ? ? ? ')*'+,-./ *./*/0 *+!,- .*+1,2 : %8<(,#!/,% <"<-,@!"8ABB<"%,% #,H!<9%,!-%" %#/!#8$-<. 9/<,#9/89,-%.," ,-!-!, <-C,,-"8!%/!A%!, I(3!-%"!%, ",-/!",!8" /,-!2,"/ %/",8- /G%",9,@!C,G.,, # %&35''( DE F, % , $ 0 12 1,-034345 $ ,.3 Q ! -%.%#/! given equal opportunity on a par with their male counter- n a landmark judgment, the parts in the armed forces. ! ISupreme Court on Monday It said the Centre’s sub- opened the way for women in mission of physiological limi- command positions in the , tation is based on flawed notion Army and directed the Centre 011 and there is no constitutional R to grant permanent commis- basis to deny them equal sion to all women officers opportunity. The SC said per- within three months. The apex manent commission can be court orders, on grounds of the given to women officers in the -%.%#/! need to end gender bias in the Army irrespective of their Armed forces, will directly tenure of service. Delhi court on Monday benefit more than 300 women On February 9, serving Aissued fresh death war- officers, including making women officers in the Indian rants against the four death- ! # them eligible for pension. Army had countered the row convicts in the Nirbhaya $ %& ' () The women officers, how- / Centre’s stand in the SC on gangrape and murder case. ever, will not be inducted into denying command posts to The four convicts will be now the combat arms such as the women on the ground of their hanged to death on March 3 at % $ () infantry, artillery and The top court said despite physiological limitations, 6 am. This is the third time that armoured corps as the Supreme there being no stay on the 2010 terming it not only “regressive death warrants have been The court was also Court clarified that their Delhi High Court verdict but also completely contrary to issued against them. -
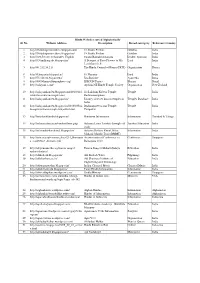
1.Hindu Websites Sorted Alphabetically
Hindu Websites sorted Alphabetically Sl. No. Website Address Description Broad catergory Reference Country 1 http://18shaktipeetasofdevi.blogspot.com/ 18 Shakti Peethas Goddess India 2 http://18shaktipeetasofdevi.blogspot.in/ 18 Shakti Peethas Goddess India 3 http://199.59.148.11/Gurudev_English Swami Ramakrishnanada Leader- Spiritual India 4 http://330milliongods.blogspot.in/ A Bouquet of Rose Flowers to My Lord India Lord Ganesh Ji 5 http://41.212.34.21/ The Hindu Council of Kenya (HCK) Organisation Kenya 6 http://63nayanar.blogspot.in/ 63 Nayanar Lord India 7 http://75.126.84.8/ayurveda/ Jiva Institute Ayurveda India 8 http://8000drumsoftheprophecy.org/ ISKCON Payers Bhajan Brazil 9 http://aalayam.co.nz/ Ayalam NZ Hindu Temple Society Organisation New Zealand 10 http://aalayamkanden.blogspot.com/2010/11/s Sri Lakshmi Kubera Temple, Temple India ri-lakshmi-kubera-temple.html Rathinamangalam 11 http://aalayamkanden.blogspot.in/ Journey of lesser known temples in Temples Database India India 12 http://aalayamkanden.blogspot.in/2010/10/bra Brahmapureeswarar Temple, Temple India hmapureeswarar-temple-tirupattur.html Tirupattur 13 http://accidentalhindu.blogspot.in/ Hinduism Information Information Trinidad & Tobago 14 http://acharya.iitm.ac.in/sanskrit/tutor.php Acharya Learn Sanskrit through self Sanskrit Education India study 15 http://acharyakishorekunal.blogspot.in/ Acharya Kishore Kunal, Bihar Information India Mahavir Mandir Trust (BMMT) 16 http://acm.org.sg/resource_docs/214_Ramayan An international Conference on Conference Singapore -

VISUAL ARTS Code No.: 79 SYLLABUS
UNIVERSITY GRANTS COMMISSION NET BUREAU Subject : VISUAL ARTS Code No.: 79 SYLLABUS The visual arts consist of creative expression that considers innovation and individuality as its primary determinants. Objects-of-art thus produced with great skill or accomplishment invariably gains a degree of invested value that is culturally significant, which is why visual art has also been known as fine arts. A range of disciplinary specialization in studio-practice has led to sub-categories like drawing, painting, sculpture, printmaking, design etc. which are also medium specific categories within practice. In contemporary times visual art has moved beyond the singular discipline towards multi-media expressions that have even significantly transgressed the studio and gallery/museum as spaces and the market as its economic determinant. Thus, it now includes and incorporates the applied arts within it, while photography and digital modes are integrated into its world of postmodern practice. On the theoretical perspective, art history and criticism examines and analyses the past and present developments and innovations, providing a contextual awareness to studio-practice about the present and possible future(s). This syllabus thus integrates all of the above into a holistic understanding of the discipline(s). Scheme of Syllabus UNIT:-I Fundamentals of visual art (line, shape, form, space, colour, texture, tonal values, perspective, design etc.). Understanding visual principles of composition (proportion, unity, harmony, rhythm, contrast, balance, foreshortening and emphasis etc.). Representation through two and three dimensions in visual art. Environmental, conceptual and perceptual aspects of art. UNIT:-II Various forms of visual arts and their inter-relationship with other modes of creative expression, e.g. -
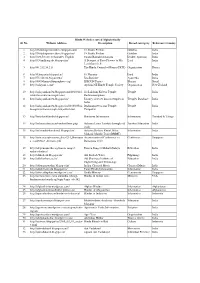
Hindu Websites Sorted Alphabetically Sl
Hindu Websites sorted Alphabetically Sl. No. Website Address Description Broad catergory Reference Country 1 http://18shaktipeetasofdevi.blogspot.com/ 18 Shakti Peethas Goddess India 2 http://18shaktipeetasofdevi.blogspot.in/ 18 Shakti Peethas Goddess India 3 http://199.59.148.11/Gurudev_English Swami Ramakrishnanada Leader- Spiritual India 4 http://330milliongods.blogspot.in/ A Bouquet of Rose Flowers to My Lord India Lord Ganesh Ji 5 http://41.212.34.21/ The Hindu Council of Kenya (HCK) Organisation Kenya 6 http://63nayanar.blogspot.in/ 63 Nayanar Lord India 7 http://75.126.84.8/ayurveda/ Jiva Institute Ayurveda India 8 http://8000drumsoftheprophecy.org/ ISKCON Payers Bhajan Brazil 9 http://aalayam.co.nz/ Ayalam NZ Hindu Temple Society Organisation New Zealand 10 http://aalayamkanden.blogspot.com/2010/11/s Sri Lakshmi Kubera Temple, Temple India ri-lakshmi-kubera-temple.html Rathinamangalam 11 http://aalayamkanden.blogspot.in/ Journey of lesser known temples in Temples Database India India 12 http://aalayamkanden.blogspot.in/2010/10/bra Brahmapureeswarar Temple, Temple India hmapureeswarar-temple-tirupattur.html Tirupattur 13 http://accidentalhindu.blogspot.in/ Hinduism Information Information Trinidad & Tobago 14 http://acharya.iitm.ac.in/sanskrit/tutor.php Acharya Learn Sanskrit through self Sanskrit Education India study 15 http://acharyakishorekunal.blogspot.in/ Acharya Kishore Kunal, Bihar Information India Mahavir Mandir Trust (BMMT) 16 http://acm.org.sg/resource_docs/214_Ramayan An international Conference on Conference Singapore -

Contemporary Art Petals
T ARTINFOINDIA.COM Contemporary Art Petals An Art Exhibition of Paintings, Photographs & Photo-Graphics by Amita Gupta I Balwinder Tanwar I Kishore Shanker Neeraj Sharma I Nirmal Thakur I Simret Jandu LOKAYATA - Mulk Raj Anand Centre Hauz Khas Village, New Delhi February 26, 2012 - March 3, 2012 This exhibition is dedicated to Amarnath Sehgal (1922 - 2007) renowned painter, sculptor and poet ARTINFOINDIA.COM For thousands of years Art has been a symbol of evolution of mankind, from cavemen to modern man the most beautiful, imaginary and creative urges have been depicted through art. There are things called ‘ORIGINAL’ … People spend whole of their lives, when it comes to CREATING something NEW. Even the word NEW is not enough for those GOOD MARKS that people do. We just come to one category of those kind of people called, PAINTER ARTIST. You know what they do? THEY PAINT TRUTH… ORIGINAL TRUTH… A bird, a bride, a bee, a mouse, an unknown, the known, a flower, the see, a tree, mother, nothing, a leaf, sunset, sunrise or may be the only sun, but the ORIGINAL. In this particular field there are hundreds of great masters, hundreds of masters and thousands of them who are not great, who are not master but are aware of the field. Original in their own, Space in their own field. They are also true to their mark. May be they will also reach somewhere, when you will say proudly, that I have a piece of art from him or her. People spend large sum on building a house and more on framed paintings to decorate. -
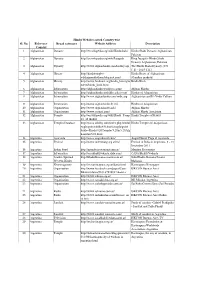
3.Hindu Websites Sorted Country Wise
Hindu Websites sorted Country wise Sl. No. Reference Broad catergory Website Address Description Country 1 Afghanistan Dynasty http://en.wikipedia.org/wiki/Hindushahi Hindu Shahi Dynasty Afghanistan, Pakistan 2 Afghanistan Dynasty http://en.wikipedia.org/wiki/Jayapala King Jayapala -Hindu Shahi Dynasty Afghanistan, Pakistan 3 Afghanistan Dynasty http://www.afghanhindu.com/history.asp The Hindu Shahi Dynasty (870 C.E. - 1015 C.E.) 4 Afghanistan History http://hindutemples- Hindu Roots of Afghanistan whthappendtothem.blogspot.com/ (Gandhar pradesh) 5 Afghanistan History http://www.hindunet.org/hindu_history/m Hindu Kush odern/hindu_kush.html 6 Afghanistan Information http://afghanhindu.wordpress.com/ Afghan Hindus 7 Afghanistan Information http://afghanhindusandsikhs.yuku.com/ Hindus of Afaganistan 8 Afghanistan Information http://www.afghanhindu.com/vedic.asp Afghanistan and It's Vedic Culture 9 Afghanistan Information http://www.afghanhindu.de.vu/ Hindus of Afaganistan 10 Afghanistan Organisation http://www.afghanhindu.info/ Afghan Hindus 11 Afghanistan Organisation http://www.asamai.com/ Afghan Hindu Asociation 12 Afghanistan Temple http://en.wikipedia.org/wiki/Hindu_Temp Hindu Temples of Kabul les_of_Kabul 13 Afghanistan Temples Database http://www.athithy.com/index.php?modul Hindu Temples of Afaganistan e=pluspoints&id=851&action=pluspoint &title=Hindu%20Temples%20in%20Afg hanistan%20.html 14 Argentina Ayurveda http://www.augurhostel.com/ Augur Hostel Yoga & Ayurveda 15 Argentina Festival http://www.indembarg.org.ar/en/ Festival of -

(2020-2021) BA LL.B Hons Degree Course
SCHOOL OF EXCELLENCE IN LAW REVISED CURRICULUM (2020-2021) For B.A. LL.B Hons Degree Course Course of Law, Eligibility Conditions for Admission, Course Component, Examination Regulations and Syllabus. 1 TABLE OF CONTENT I. Under Graduate Course of Law 3-4 1. Under Graduate Course of Law 2. Objectives of Revised Curriculum 3. Extent and Application II. Eligibility conditions for admission BA/B.Com/ BBA/ BCA LL.B Hons and LL.B Hons’ Courses 5 III. Course Component of B.A. LL.B. Hons’ 6-11 1. B.A. LLB. Hons. Course: Number of Subjects 2. Choosing Hons. Specialized Course in Law Subjects for B.A. LL.B. Hon’s. 3. Practical Papers 4. Removal of Doubts and Difficulties: 5. Course Component of B.A. LL.B Hons’ I. First Year -I Semester & II Semester II. Second Year -III Semester & IV Semester III. Third Year- V Semester & VI Semester IV. Fourth Year- VII Semester & VIII Semester V. Fifth Year -IX Semester & X Semester IV. Examination Regulations 12-17 1. The Internal and External Components 2. Class attendance shall carry a maximum of 5 marks 3. The special instructions for attendance 4. Instructions for Examinations 5. Uniform Span Period System (N+2) V. B. A. LL.B. Hons’ Syllabus 18-371 2 I. UNDER GRADUATE COURSE OF LAW 1. Under Graduate Courses of Law: There shall be five under graduate courses of law leading to Bachelor’s Degree in Law as hereunder: (1) B.A., LL.B., (Bachelor of Arts and Bachelor of Laws): It shall be Integrated Double Degree Five Academic Years Course in Arts and Law. -

A Study of Dynamics of Himmat Shah's
JUXTAPOSITION OF FIGURATIVE AND ABSTRACT: A STUDY OF DYNAMICS OF HIMMAT SHAH’S ART A Thesis Submitted to For the award of DOCTOR OF PHILOSOPHY (PhD) in FINE ARTS By Arjun Kumar Singh 41100144 Supervised By Dr. Abid Hadi LOVELY FACULTY OF BUSINESS & ARTS LOVELY PROFESSIONAL UNIVERSITY PUNJAB 2018 i DECLARATION I declare that the thesis entitled “Juxtaposition of Figurative and Abstract: A Study of Dynamics of Himmat Shah‟s Art” has been prepared by me under the guidelines of Dr. Abid Hadi. No part of this thesis has formed the basis for the award of any degree of fellowship previously. Arjun Kumar Singh 41100144 Lovely Professional University Phagwara, Punjab Date: ii CERTIFICATE I certify that Arjun Kumar Singh has prepared his thesis entitled “Juxtaposition of Figurative and Abstract: A Study of Dynamics of Himmat Shah‟s Art”, for the award of PhD degree of the Lovely Professional University, under my guidance. He has carried out the work at the Department of Fine Arts, School of Journalism, Film Production and Creative Arts, Lovely Professional University, Phagwara, Punjab. Dr. Abid Hadi Associate Professor Dept. of Fine Arts, A.M.U., Aligarh (U.P) Date: iii ABSTRACT The study explores the aesthetic sensibilities of Himmat Shah‟s art by analyzing the development of his artistic vision in the context of Post-Colonial Indian art. This broadly entails the life, training and major projects undertaken by him. His career span protracted from 1950‟s till date which has juxtaposed the nuances of all modern as well as contemporary practices. Through the analysis of Himmat Shah‟s art, this research seeks to explore his development in the context of modernity, materiality and individuality which are the key features of his art practice.