Deep Fritz Benchmark Top Ten World Chess E
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Videos Bearbeiten Im Überblick: Sieben Aktuelle VIDEOSCHNITT Werkzeuge Für Den Videoschnitt
Miller: Texttool-Allrounder Wego: Schicke Wetter-COMMUNITY-EDITIONManjaro i3: Arch-Derivat mit bereitet CSVs optimal auf S. 54 App für die Konsole S. 44 Tiling-Window-Manager S. 48 Frei kopieren und beliebig weiter verteilen ! 03.2016 03.2016 Guter Schnitt für Bild und Ton, eindrucksvolle Effekte, perfektes Mastering VIDEOSCHNITT Videos bearbeiten Im Überblick: Sieben aktuelle VIDEOSCHNITT Werkzeuge für den Videoschnitt unter Linux im Direktvergleich S. 10 • Veracrypt • Wego • Wego • Veracrypt • Pitivi & OpenShot: Einfach wie noch nie – die neue Generation der Videoschnitt-Werkzeuge S. 20 Lightworks: So kitzeln Sie optimale Ergebnisse aus der kostenlosen Free-Version heraus S. 26 Verschlüsselte Daten sicher verstecken S. 64 Glaubhafte Abstreitbarkeit: Wie Sie mit dem Truecrypt-Nachfolger • SQLiteStudio Stellarium Synology RT1900ac Veracrypt wichtige Daten unauffindbar in Hidden Volumes verbergen Stellarium erweitern S. 32 Workshop SQLiteStudio S. 78 Eigene Objekte und Landschaften Die komfortable Datenbankoberfläche ins virtuelle Planetarium einbinden für Alltagsprogramme auf dem Desktop Top-Distris • Anydesk • Miller PyChess • auf zwei Heft-DVDs ANYDESK • MILLER • PYCHESS • STELLARIUM • VERACRYPT • WEGO • • WEGO • VERACRYPT • STELLARIUM • PYCHESS • MILLER • ANYDESK EUR 8,50 EUR 9,35 sfr 17,00 EUR 10,85 EUR 11,05 EUR 11,05 2 DVD-10 03 www.linux-user.de Deutschland Österreich Schweiz Benelux Spanien Italien 4 196067 008502 03 Editorial Old and busted? Jörg Luther Chefredakteur Sehr geehrte Leserinnen und Leser, viele kleinere, innovative Distributionen seit einem Jahrzehnt kommen Desktop- Immer öfter stellen wir uns aber die haben damit erst gar nicht angefangen und Notebook-Systeme nur noch mit Frage, ob es wirklich noch Sinn ergibt, oder sparen es sich schon lange. Open- 64-Bit-CPUs, sodass sich die Zahl der moderne Distributionen überhaupt Suse verzichtet seit Leap 42.1 darauf; das 32-Bit-Systeme in freier Wildbahn lang- noch als 32-Bit-Images beizulegen. -
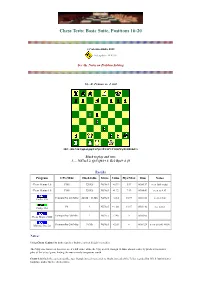
Chess Tests: Basic Suite, Positions 16-20
Chess Tests: Basic Suite, Positions 16-20 (c) Valentin Albillo, 2020 Last update: 14/01/98 See the Notes on Problem Solving 16.- Z. Franco vs. J. Gil FEN: rbb1N1k1/pp1n1ppp/8/2Pp4/3P4/4P3/P1Q2PPq/R1BR1K2/ b Black to play and win: 1. ... Nd7xc5 2. Qc5 Qh1+ 3. Ke2 Bg4+ 4. f3 Results Program CPU/Mhz Hash table Move Value Plys/Max Time Notes Chess Genius 1.0 P100 320 Kb Nd7xc5 +0.39 5/17 00:00:17 sees little value Chess Genius 1.0 P100 320 Kb Nd7xc5 +1.72 7/19 00:04:49 sees to 4. f3 Pentium Pro 200 MHz 24 Mb + 16 Mb Nd7xc5 +2.14 10/19 00:01:20 seen at 14s Crafty 12.6 P6 ? Nd7xc5 +1.181 11/17 00:01:46 see notes Crafty 13.3 Pentium Pro 200 Mhz ? Nd7xc5 +2.46 9 00:03:05 Chess Master 5500 Pentium Pro 200 Mhz 10 Mb Nd7xc5 +2.65 6 00:01:24 seen at 0:00, +0.00 MChess Pro 5.0 Notes: Using Chess Genius 1.0, both searches find the correct Knight's sacrifice. The 5-ply one, however, does not see it's full value, while the 7-ply search, though 16 times slower, correctly predicts the next 6 plies of the actual game, finding the move nearly two pawns worth. Crafty 12.6 finds the correct sacrifice too, though it needs to search to 10 ply, instead of the 7 plies required by CG1.0, but its better hardware makes for the shortest time. -
Draft – Not for Circulation
A Gross Miscarriage of Justice in Computer Chess by Dr. Søren Riis Introduction In June 2011 it was widely reported in the global media that the International Computer Games Association (ICGA) had found chess programmer International Master Vasik Rajlich in breach of the ICGA‟s annual World Computer Chess Championship (WCCC) tournament rule related to program originality. In the ICGA‟s accompanying report it was asserted that Rajlich‟s chess program Rybka contained “plagiarized” code from Fruit, a program authored by Fabien Letouzey of France. Some of the headlines reporting the charges and ruling in the media were “Computer Chess Champion Caught Injecting Performance-Enhancing Code”, “Computer Chess Reels from Biggest Sporting Scandal Since Ben Johnson” and “Czech Mate, Mr. Cheat”, accompanied by a photo of Rajlich and his wife at their wedding. In response, Rajlich claimed complete innocence and made it clear that he found the ICGA‟s investigatory process and conclusions to be biased and unprofessional, and the charges baseless and unworthy. He refused to be drawn into a protracted dispute with his accusers or mount a comprehensive defense. This article re-examines the case. With the support of an extensive technical report by Ed Schröder, author of chess program Rebel (World Computer Chess champion in 1991 and 1992) as well as support in the form of unpublished notes from chess programmer Sven Schüle, I argue that the ICGA‟s findings were misleading and its ruling lacked any sense of proportion. The purpose of this paper is to defend the reputation of Vasik Rajlich, whose innovative and influential program Rybka was in the vanguard of a mid-decade paradigm change within the computer chess community. -

The SSDF Chess Engine Rating List, 2019-02
The SSDF Chess Engine Rating List, 2019-02 Article Accepted Version The SSDF report Sandin, L. and Haworth, G. (2019) The SSDF Chess Engine Rating List, 2019-02. ICGA Journal, 41 (2). 113. ISSN 1389- 6911 doi: https://doi.org/10.3233/ICG-190107 Available at http://centaur.reading.ac.uk/82675/ It is advisable to refer to the publisher’s version if you intend to cite from the work. See Guidance on citing . Published version at: https://doi.org/10.3233/ICG-190085 To link to this article DOI: http://dx.doi.org/10.3233/ICG-190107 Publisher: The International Computer Games Association All outputs in CentAUR are protected by Intellectual Property Rights law, including copyright law. Copyright and IPR is retained by the creators or other copyright holders. Terms and conditions for use of this material are defined in the End User Agreement . www.reading.ac.uk/centaur CentAUR Central Archive at the University of Reading Reading’s research outputs online THE SSDF RATING LIST 2019-02-28 148673 games played by 377 computers Rating + - Games Won Oppo ------ --- --- ----- --- ---- 1 Stockfish 9 x64 1800X 3.6 GHz 3494 32 -30 642 74% 3308 2 Komodo 12.3 x64 1800X 3.6 GHz 3456 30 -28 640 68% 3321 3 Stockfish 9 x64 Q6600 2.4 GHz 3446 50 -48 200 57% 3396 4 Stockfish 8 x64 1800X 3.6 GHz 3432 26 -24 1059 77% 3217 5 Stockfish 8 x64 Q6600 2.4 GHz 3418 38 -35 440 72% 3251 6 Komodo 11.01 x64 1800X 3.6 GHz 3397 23 -22 1134 72% 3229 7 Deep Shredder 13 x64 1800X 3.6 GHz 3360 25 -24 830 66% 3246 8 Booot 6.3.1 x64 1800X 3.6 GHz 3352 29 -29 560 54% 3319 9 Komodo 9.1 -

Distributional Differences Between Human and Computer Play at Chess
Multidisciplinary Workshop on Advances in Preference Handling: Papers from the AAAI-14 Workshop Human and Computer Preferences at Chess Kenneth W. Regan Tamal Biswas Jason Zhou Department of CSE Department of CSE The Nichols School University at Buffalo University at Buffalo Buffalo, NY 14216 USA Amherst, NY 14260 USA Amherst, NY 14260 USA [email protected] [email protected] Abstract In our case the third parties are computer chess programs Distributional analysis of large data-sets of chess games analyzing the position and the played move, and the error played by humans and those played by computers shows the is the difference in analyzed value from its preferred move following differences in preferences and performance: when the two differ. We have run the computer analysis (1) The average error per move scales uniformly higher the to sufficient depth estimated to have strength at least equal more advantage is enjoyed by either side, with the effect to the top human players in our samples, depth significantly much sharper for humans than computers; greater than used in previous studies. We have replicated our (2) For almost any degree of advantage or disadvantage, a main human data set of 726,120 positions from tournaments human player has a significant 2–3% lower scoring expecta- played in 2010–2012 on each of four different programs: tion if it is his/her turn to move, than when the opponent is to Komodo 6, Stockfish DD (or 5), Houdini 4, and Rybka 3. move; the effect is nearly absent for computers. The first three finished 1-2-3 in the most recent Thoresen (3) Humans prefer to drive games into positions with fewer Chess Engine Competition, while Rybka 3 (to version 4.1) reasonable options and earlier resolutions, even when playing was the top program from 2008 to 2011. -

Extended Null-Move Reductions
Extended Null-Move Reductions Omid David-Tabibi1 and Nathan S. Netanyahu1,2 1 Department of Computer Science, Bar-Ilan University, Ramat-Gan 52900, Israel [email protected], [email protected] 2 Center for Automation Research, University of Maryland, College Park, MD 20742, USA [email protected] Abstract. In this paper we review the conventional versions of null- move pruning, and present our enhancements which allow for a deeper search with greater accuracy. While the conventional versions of null- move pruning use reduction values of R ≤ 3, we use an aggressive re- duction value of R = 4 within a verified adaptive configuration which maximizes the benefit from the more aggressive pruning, while limiting its tactical liabilities. Our experimental results using our grandmaster- level chess program, Falcon, show that our null-move reductions (NMR) outperform the conventional methods, with the tactical benefits of the deeper search dominating the deficiencies. Moreover, unlike standard null-move pruning, which fails badly in zugzwang positions, NMR is impervious to zugzwangs. Finally, the implementation of NMR in any program already using null-move pruning requires a modification of only a few lines of code. 1 Introduction Chess programs trying to search the same way humans think by generating “plausible” moves dominated until the mid-1970s. By using extensive chess knowledge at each node, these programs selected a few moves which they consid- ered plausible, and thus pruned large parts of the search tree. However, plausible- move generating programs had serious tactical shortcomings, and as soon as brute-force search programs such as Tech [17] and Chess 4.x [29] managed to reach depths of 5 plies and more, plausible-move generating programs fre- quently lost to brute-force searchers due to their tactical weaknesses. -

Deep Hiarcs 14 Uci Chess Engine Download
Deep Hiarcs 14 Uci Chess Engine Download Deep Hiarcs 14 Uci Chess Engine Download 1 / 3 14, Arics (WB), Vladimir Fadeev, Belarus, SD, 0,08, no ?? ... 22, Ifrit (UCI), Бренкман Андрей (Brenkman Andrey), Russia, 0,04, no, 2200, B1_6 B1_7 B1_9 ... 1. deep hiarcs 14 uci chess engine download 2. deep hiarcs chess explorer download o Deep HIARCS 14 WCSC (available with the Deep HIARCS Chess Explorer ... Please note you can add other UCI chess engines including third party UCI ... publisher is "Applied Computer Concepts Ltd.", do not trust the download if it is not ... deep hiarcs 14 uci chess engine download deep hiarcs 14 uci chess engine download, deep hiarcs chess explorer, deep hiarcs chess explorer download, deep hiarcs chess explorer for mac Red Giant VFX Suite 1.0.4 With Crack [Latest] Free download deep hiarcs 14 uci engine torrent Files at Software Informer. HIARCS 12 MP UCI - a chess program that can do more than .... See my blog for more information and download instructions. ... UCI parameters When an engine runs through a chess GUI, it communicates all the settings ... HIARCS14 (HIARCS book), TC 15sec; +8 -5 =7 First test with Lc0-v0. inf. exe (only ... AlphaZero; Deep Learning; Deus X; Leela Chess Zero; Forum Posts 2019. call of duty black ops crack indir oyuncehennemi multi.flash.kit.2.10.30 free download deep hiarcs chess explorer download Pinegrow Web Editor Crack 5.91 With keygen Free Download 2020 It connects a UCI chess engine to an xboard interface such as ... the AlphaZero-style Monte Carlo Tree Search and deep neural networks a flexible, .. -

Move Similarity Analysis in Chess Programs
Move similarity analysis in chess programs D. Dailey, A. Hair, M. Watkins Abstract In June 2011, the International Computer Games Association (ICGA) disqual- ified Vasik Rajlich and his Rybka chess program for plagiarism and breaking their rules on originality in their events from 2006-10. One primary basis for this came from a painstaking code comparison, using the source code of Fruit and the object code of Rybka, which found the selection of evaluation features in the programs to be almost the same, much more than expected by chance. In his brief defense, Rajlich indicated his opinion that move similarity testing was a superior method of detecting misappropriated entries. Later commentary by both Rajlich and his defenders reiterated the same, and indeed the ICGA Rules themselves specify move similarity as an example reason for why the tournament director would have warrant to request a source code examination. We report on data obtained from move-similarity testing. The principal dataset here consists of over 8000 positions and nearly 100 independent engines. We comment on such issues as: the robustness of the methods (upon modifying the experimental conditions), whether strong engines tend to play more similarly than weak ones, and the observed Fruit/Rybka move-similarity data. 1. History and background on derivative programs in computer chess Computer chess has seen a number of derivative programs over the years. One of the first was the incident in the 1989 World Microcomputer Chess Cham- pionship (WMCCC), in which Quickstep was disqualified due to the program being \a copy of the program Mephisto Almeria" in all important areas. -

Crafty Command Documentation (Version 18) ------Crafty Is Nothing More Than a Long-Time Hobby of Mine, Dating Back to Blitz and Later Cray Blitz
Crafty Command Documentation (version 18) ----------------------------------------------- Crafty is nothing more than a long-time hobby of mine, dating back to Blitz and later Cray Blitz. People ask me howI keep doing this, and that is the one question that generally leaves me at a loss for words. Perhaps the most common question I’m asked is "is this version of Crafty some dumbed-down version of what you play on ICC or what you use at a computer chess event?" The answer is a resounding *NO*. The current version is *exactly* what is running on ICC under this version number.Note that a newversion can, on occasion, introduce weaknesses or outright bugs that were not present in previous "gold" versions. As aresult, you should be careful to back up your "favorite" before trying the latest and greatest. If you aren’tsatisfied with the newver- sion, you can then go back to what you believe isabetter version. If you are looking for the strongest playing computer chess program available, you should likely look to Fritz, Rebel, Tiger,and the other commercial entries. There you will find strong opponents with polished interfaces that have been tested in a systematic and careful way.If you are looking for a program that plays good chess, has a reasonable set of features for you to use, is available in source form, and one where the author welcomes feedback, code or sugges- tions, then you are at the right place. Iwelcome comments and suggestions, and also feedback from ideas you try yourself that seem to work. Crafty is a state-of-the-art computer chess program, and uses all of the search algorithms you have probably read about, negascout search, killer/history move ordering, SEE (Static Exchange Evaluation) quiescence move ordering and pruning, hash (transposition/refutation) tables as well as evaluation caches, selective extensions, recursive null-move search, futility pruning, late move reductions, and a host of other features that have been used and are still being used in most computer chess programs. -

Rybka Investigation and Summary of Findings for the ICGA Mark Lefler, Robert Hyatt, Harvey Williamson and ICGA Panel Members 12 May 2011
Rybka Investigation and Summary of Findings for the ICGA Mark Lefler, Robert Hyatt, Harvey Williamson and ICGA panel members 12 May 2011 1. Background 1.1 Purpose: To investigate claims that the chess playing program Rybka is a derivative of the chess programs Fruit and Crafty and violated International Computer Games Association (ICGA) Tournament rules. Rybka is a program by Vasik Rajlich. Fruit was written by Fabien Letouzey. Crafty was written by Robert Hyatt. 1.2 Allegations. Allegations have surfaced that Rybka 1.0 beta and later versions are derivatives of Fruit 2.1. Fruit 2.1 source code was distributed with a specific license in the copying.txt file. Part of this license reads: "For example, if you distribute copies of such a program, whether gratis or for a fee, you must give the recipients all the rights that you have. You must make sure that they, too, receive or can get the source code. And you must show them these terms so they know their rights." Allegations point out that by distributing Rybka, if it is based on Fruit, this GNU license was violated (http://icga.wikispaces.com/Open+letter+to+the+ICGA+about+the+Rybka- Fruit+issue). If versions of Rybka are derived from Fruit and participated in ICGA tournaments, then Rybka has also violated ICGA Tournament Rules. Specifically, the rules state: "Each program must be the original work of the entering developers. Programming teams whose code is derived from or including game-playing code written by others must name all other authors, or the source of such code, in the details of their submission form. -

The Myth Rajlich Copied Fruit Revision 1.1
The myth Rajlich copied Fruit Revision 1.1 Contents 1. The myth Rajlich copied Fruit ................................................................................ 2 2. Mixed Messages ...................................................................................................... 3 3. How much is too much? ......................................................................................... 4 4. About originality ...................................................................................................... 5 5. ICGA Responsibility ................................................................................................ 6 6. The evidence about “TOO MUCH” ......................................................................... 7 7. Technical stuff ......................................................................................................... 8 8. The Fruitification of Rybka ..................................................................................... 8 9. EVAL-COMP comments ........................................................................................ 15 10. FIDE Ethics Committee slams ICGA board as incompetent amateurs ................................................................................................................ 19 11. The denial of a fair appeal .................................................................................... 22 12. Conclusions ........................................................................................................... 22 September -

The First FIDE Man-Machine World Chess Championship
The First FIDE Man-Machine World Chess Championship Jonathan Schaeffer Department of Computing Science University of Alberta Edmonton, Alberta Canada T6G 2E8 [email protected] In 1989, 1996 and 1997, world chess champion Garry Kasparov battled with the strongest computer chess program in the world – Deep Blue and its predecessor Deep Thought. In 1989, man easily defeated machine. In 1996, Kasparov also won, but this time with difficulty, including losing a game to the computer. In 1997, Deep Blue stunned the world by narrowly winning the match. Was Deep Blue the best chess player in the world? Or was the result a fluke? We had no answer, as IBM immediately retired Deep Blue after the match. A frustrated Kasparov wanted another chance to play the computer, but it never happened. I am a professor in computer science, and specifically do research in the area of artificial intelligence – making computers appear to do intelligent things. Most of my research has used games to demonstrate my ideas. In the 1980’s it was with my chess program Phoenix. In the early 1990’s it was with the checkers program Chinook. These days it is with our poker program, Poki. As a scientist, I was dissatisfied with the 1997 result. There was one short chess match which suggested that machine was better than man at chess. But science is all about producing reproducible results. More data was needed before one could objectively decide whether computer chess programs really were as good as (or better) than the best human chess player in the world.