Crafty Command Documentation (Version 18) ------Crafty Is Nothing More Than a Long-Time Hobby of Mine, Dating Back to Blitz and Later Cray Blitz
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Videos Bearbeiten Im Überblick: Sieben Aktuelle VIDEOSCHNITT Werkzeuge Für Den Videoschnitt
Miller: Texttool-Allrounder Wego: Schicke Wetter-COMMUNITY-EDITIONManjaro i3: Arch-Derivat mit bereitet CSVs optimal auf S. 54 App für die Konsole S. 44 Tiling-Window-Manager S. 48 Frei kopieren und beliebig weiter verteilen ! 03.2016 03.2016 Guter Schnitt für Bild und Ton, eindrucksvolle Effekte, perfektes Mastering VIDEOSCHNITT Videos bearbeiten Im Überblick: Sieben aktuelle VIDEOSCHNITT Werkzeuge für den Videoschnitt unter Linux im Direktvergleich S. 10 • Veracrypt • Wego • Wego • Veracrypt • Pitivi & OpenShot: Einfach wie noch nie – die neue Generation der Videoschnitt-Werkzeuge S. 20 Lightworks: So kitzeln Sie optimale Ergebnisse aus der kostenlosen Free-Version heraus S. 26 Verschlüsselte Daten sicher verstecken S. 64 Glaubhafte Abstreitbarkeit: Wie Sie mit dem Truecrypt-Nachfolger • SQLiteStudio Stellarium Synology RT1900ac Veracrypt wichtige Daten unauffindbar in Hidden Volumes verbergen Stellarium erweitern S. 32 Workshop SQLiteStudio S. 78 Eigene Objekte und Landschaften Die komfortable Datenbankoberfläche ins virtuelle Planetarium einbinden für Alltagsprogramme auf dem Desktop Top-Distris • Anydesk • Miller PyChess • auf zwei Heft-DVDs ANYDESK • MILLER • PYCHESS • STELLARIUM • VERACRYPT • WEGO • • WEGO • VERACRYPT • STELLARIUM • PYCHESS • MILLER • ANYDESK EUR 8,50 EUR 9,35 sfr 17,00 EUR 10,85 EUR 11,05 EUR 11,05 2 DVD-10 03 www.linux-user.de Deutschland Österreich Schweiz Benelux Spanien Italien 4 196067 008502 03 Editorial Old and busted? Jörg Luther Chefredakteur Sehr geehrte Leserinnen und Leser, viele kleinere, innovative Distributionen seit einem Jahrzehnt kommen Desktop- Immer öfter stellen wir uns aber die haben damit erst gar nicht angefangen und Notebook-Systeme nur noch mit Frage, ob es wirklich noch Sinn ergibt, oder sparen es sich schon lange. Open- 64-Bit-CPUs, sodass sich die Zahl der moderne Distributionen überhaupt Suse verzichtet seit Leap 42.1 darauf; das 32-Bit-Systeme in freier Wildbahn lang- noch als 32-Bit-Images beizulegen. -

Ada Lovelace Articles S
ADA Volume 36 USER Number 1 March 2015 JOURNAL Contents Page Editorial Policy for Ada User Journal 2 Editorial 3 Quarterly News Digest 4 Conference Calendar 24 Forthcoming Events 32 Bicentennial Ada Lovelace Articles S. Charman-Anderson “Ada Lovelace: Victorian Computing Visionary” 35 Articles from the Advances on Methods Special Session of Ada-Europe 2015 J. Sparre Andersen "Persistent Containers with Ada 2012" 43 F. Sánchez-Ledesma, J. Pastor, D. Alonso and B. Álvarez "A Task-Based Concurrency Scheme for Executing Component-Based Applications" 49 Ada-Europe Associate Members (National Ada Organizations) 56 Ada-Europe Sponsors Inside Back Cover Ada User Journal Volume 36, Number 1, March 2015 2 Editorial Policy for Ada User Journal Publication Original Papers a wider audience. This includes papers Ada User Journal — The Journal for Manuscripts should be submitted in published in North America that are the international Ada Community — is accordance with the submission not easily available in Europe. published by Ada-Europe. It appears guidelines (below). We have a reciprocal approach in four times a year, on the last days of granting permission for other March, June, September and All original technical contributions are submitted to refereeing by at least two publications to reprint papers originally December. Copy date is the last day of published in Ada User Journal. the month of publication. people. Names of referees will be kept confidential, but their comments will Commentaries Aims be relayed to the authors at the discretion of the Editor. We publish commentaries on Ada and Ada User Journal aims to inform software engineering topics. -
Draft – Not for Circulation
A Gross Miscarriage of Justice in Computer Chess by Dr. Søren Riis Introduction In June 2011 it was widely reported in the global media that the International Computer Games Association (ICGA) had found chess programmer International Master Vasik Rajlich in breach of the ICGA‟s annual World Computer Chess Championship (WCCC) tournament rule related to program originality. In the ICGA‟s accompanying report it was asserted that Rajlich‟s chess program Rybka contained “plagiarized” code from Fruit, a program authored by Fabien Letouzey of France. Some of the headlines reporting the charges and ruling in the media were “Computer Chess Champion Caught Injecting Performance-Enhancing Code”, “Computer Chess Reels from Biggest Sporting Scandal Since Ben Johnson” and “Czech Mate, Mr. Cheat”, accompanied by a photo of Rajlich and his wife at their wedding. In response, Rajlich claimed complete innocence and made it clear that he found the ICGA‟s investigatory process and conclusions to be biased and unprofessional, and the charges baseless and unworthy. He refused to be drawn into a protracted dispute with his accusers or mount a comprehensive defense. This article re-examines the case. With the support of an extensive technical report by Ed Schröder, author of chess program Rebel (World Computer Chess champion in 1991 and 1992) as well as support in the form of unpublished notes from chess programmer Sven Schüle, I argue that the ICGA‟s findings were misleading and its ruling lacked any sense of proportion. The purpose of this paper is to defend the reputation of Vasik Rajlich, whose innovative and influential program Rybka was in the vanguard of a mid-decade paradigm change within the computer chess community. -

The SSDF Chess Engine Rating List, 2019-02
The SSDF Chess Engine Rating List, 2019-02 Article Accepted Version The SSDF report Sandin, L. and Haworth, G. (2019) The SSDF Chess Engine Rating List, 2019-02. ICGA Journal, 41 (2). 113. ISSN 1389- 6911 doi: https://doi.org/10.3233/ICG-190107 Available at http://centaur.reading.ac.uk/82675/ It is advisable to refer to the publisher’s version if you intend to cite from the work. See Guidance on citing . Published version at: https://doi.org/10.3233/ICG-190085 To link to this article DOI: http://dx.doi.org/10.3233/ICG-190107 Publisher: The International Computer Games Association All outputs in CentAUR are protected by Intellectual Property Rights law, including copyright law. Copyright and IPR is retained by the creators or other copyright holders. Terms and conditions for use of this material are defined in the End User Agreement . www.reading.ac.uk/centaur CentAUR Central Archive at the University of Reading Reading’s research outputs online THE SSDF RATING LIST 2019-02-28 148673 games played by 377 computers Rating + - Games Won Oppo ------ --- --- ----- --- ---- 1 Stockfish 9 x64 1800X 3.6 GHz 3494 32 -30 642 74% 3308 2 Komodo 12.3 x64 1800X 3.6 GHz 3456 30 -28 640 68% 3321 3 Stockfish 9 x64 Q6600 2.4 GHz 3446 50 -48 200 57% 3396 4 Stockfish 8 x64 1800X 3.6 GHz 3432 26 -24 1059 77% 3217 5 Stockfish 8 x64 Q6600 2.4 GHz 3418 38 -35 440 72% 3251 6 Komodo 11.01 x64 1800X 3.6 GHz 3397 23 -22 1134 72% 3229 7 Deep Shredder 13 x64 1800X 3.6 GHz 3360 25 -24 830 66% 3246 8 Booot 6.3.1 x64 1800X 3.6 GHz 3352 29 -29 560 54% 3319 9 Komodo 9.1 -

Project: Chess Engine 1 Introduction 2 Peachess
P. Thiemann, A. Bieniusa, P. Heidegger Winter term 2010/11 Lecture: Concurrency Theory and Practise Project: Chess engine http://proglang.informatik.uni-freiburg.de/teaching/concurrency/2010ws/ Project: Chess engine 1 Introduction From the Wikipedia article on Chess: Chess is a two-player board game played on a chessboard, a square-checkered board with 64 squares arranged in an eight-by-eight grid. Each player begins the game with sixteen pieces: one king, one queen, two rooks, two knights, two bishops, and eight pawns. The object of the game is to checkmate the opponent’s king, whereby the king is under immediate attack (in “check”) and there is no way to remove or defend it from attack on the next move. The game’s present form emerged in Europe during the second half of the 15th century, an evolution of an older Indian game, Shatranj. Theoreticians have developed extensive chess strategies and tactics since the game’s inception. Computers have been used for many years to create chess-playing programs, and their abilities and insights have contributed significantly to modern chess theory. One, Deep Blue, was the first machine to beat a reigning World Chess Champion when it defeated Garry Kasparov in 1997. Do not worry if you are not familiar with the rules of chess! You are not asked to change the methods which calculate the moves, nor the internal representation of boards or moves, nor the scoring of boards. 2 Peachess Peachess is a chess engine written in Java. The implementation consists of several components. 2.1 The chess board The chess board representation stores the actual state of the game. -

Python-Chess Release 1.0.0 Unknown
python-chess Release 1.0.0 unknown Sep 24, 2020 CONTENTS 1 Introduction 3 2 Documentation 5 3 Features 7 4 Installing 11 5 Selected use cases 13 6 Acknowledgements 15 7 License 17 8 Contents 19 8.1 Core................................................... 19 8.2 PGN parsing and writing......................................... 35 8.3 Polyglot opening book reading...................................... 42 8.4 Gaviota endgame tablebase probing................................... 44 8.5 Syzygy endgame tablebase probing................................... 45 8.6 UCI/XBoard engine communication................................... 47 8.7 SVG rendering.............................................. 58 8.8 Variants.................................................. 59 8.9 Changelog for python-chess....................................... 61 9 Indices and tables 93 Index 95 i ii python-chess, Release 1.0.0 CONTENTS 1 python-chess, Release 1.0.0 2 CONTENTS CHAPTER ONE INTRODUCTION python-chess is a pure Python chess library with move generation, move validation and support for common formats. This is the Scholar’s mate in python-chess: >>> import chess >>> board= chess.Board() >>> board.legal_moves <LegalMoveGenerator at ... (Nh3, Nf3, Nc3, Na3, h3, g3, f3, e3, d3, c3, ...)> >>> chess.Move.from_uci("a8a1") in board.legal_moves False >>> board.push_san("e4") Move.from_uci('e2e4') >>> board.push_san("e5") Move.from_uci('e7e5') >>> board.push_san("Qh5") Move.from_uci('d1h5') >>> board.push_san("Nc6") Move.from_uci('b8c6') >>> board.push_san("Bc4") Move.from_uci('f1c4') -

Distributional Differences Between Human and Computer Play at Chess
Multidisciplinary Workshop on Advances in Preference Handling: Papers from the AAAI-14 Workshop Human and Computer Preferences at Chess Kenneth W. Regan Tamal Biswas Jason Zhou Department of CSE Department of CSE The Nichols School University at Buffalo University at Buffalo Buffalo, NY 14216 USA Amherst, NY 14260 USA Amherst, NY 14260 USA [email protected] [email protected] Abstract In our case the third parties are computer chess programs Distributional analysis of large data-sets of chess games analyzing the position and the played move, and the error played by humans and those played by computers shows the is the difference in analyzed value from its preferred move following differences in preferences and performance: when the two differ. We have run the computer analysis (1) The average error per move scales uniformly higher the to sufficient depth estimated to have strength at least equal more advantage is enjoyed by either side, with the effect to the top human players in our samples, depth significantly much sharper for humans than computers; greater than used in previous studies. We have replicated our (2) For almost any degree of advantage or disadvantage, a main human data set of 726,120 positions from tournaments human player has a significant 2–3% lower scoring expecta- played in 2010–2012 on each of four different programs: tion if it is his/her turn to move, than when the opponent is to Komodo 6, Stockfish DD (or 5), Houdini 4, and Rybka 3. move; the effect is nearly absent for computers. The first three finished 1-2-3 in the most recent Thoresen (3) Humans prefer to drive games into positions with fewer Chess Engine Competition, while Rybka 3 (to version 4.1) reasonable options and earlier resolutions, even when playing was the top program from 2008 to 2011. -

Move Similarity Analysis in Chess Programs
Move similarity analysis in chess programs D. Dailey, A. Hair, M. Watkins Abstract In June 2011, the International Computer Games Association (ICGA) disqual- ified Vasik Rajlich and his Rybka chess program for plagiarism and breaking their rules on originality in their events from 2006-10. One primary basis for this came from a painstaking code comparison, using the source code of Fruit and the object code of Rybka, which found the selection of evaluation features in the programs to be almost the same, much more than expected by chance. In his brief defense, Rajlich indicated his opinion that move similarity testing was a superior method of detecting misappropriated entries. Later commentary by both Rajlich and his defenders reiterated the same, and indeed the ICGA Rules themselves specify move similarity as an example reason for why the tournament director would have warrant to request a source code examination. We report on data obtained from move-similarity testing. The principal dataset here consists of over 8000 positions and nearly 100 independent engines. We comment on such issues as: the robustness of the methods (upon modifying the experimental conditions), whether strong engines tend to play more similarly than weak ones, and the observed Fruit/Rybka move-similarity data. 1. History and background on derivative programs in computer chess Computer chess has seen a number of derivative programs over the years. One of the first was the incident in the 1989 World Microcomputer Chess Cham- pionship (WMCCC), in which Quickstep was disqualified due to the program being \a copy of the program Mephisto Almeria" in all important areas. -
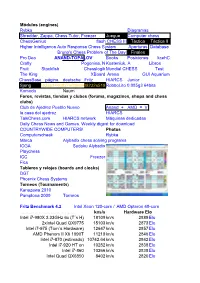
Deep Fritz Benchmark Top Ten World Chess E
Módulos (engines) Deep Fritz Benchmarktop ten WorldColossus: chess download www.colossus.demon.co.uk/chess/colossuschessuci.htmengines pagechecksl.com Rybka Diagramas Shredder, Zappa, Chess Tutor, Freezer Juegue Computer chess ChessGenius flash CHESS III Táctica Táctica II Higher Intelligence Auto Response Chess System Aperturas Database Bruno's Chess Problem of The Day Finales Pro Deo ANAND-TOPALOV Books Posiciones kcehC Crafty Pogonina, N Kosteniuk, A Libros Fruit Stockfish Chesslogik Mundial CHESS Test The King XBoard Arena GUI Aquarium ChessBase página deutsche Fritz HIARCS Junior 0df20896bed45d7d33b1e3d899c64bc9875a0ad9 Sjeng3bbe03a3ae144d827a0d6d909232e519 RobboLito 0.085g3 64bits Komodo Naum _____________ Foros, revistas, tiendas y clubes (forums, magazines, shops and chess clubs) Club de Ajedrez Pueblo Nuevo Anand + AMD = V la casa del ajedrez HIARCS TalkChess.com HIARCS network Máquinas dedicadas Daily Chess News and Games. Weekly digest for download COUNTRYWIDE COMPUTERS! Photos Computerschaak Rybka checksl.com Marca Alybadix chess solving programs ICGA Sudoku Alybadix Playchess ICC Freezer Fics Tableros y relojes (boards and clocks) DGT Phoenix Chess Systems Torneos (Tournaments) Kanazawa 2010 Pamplona 2009 Torneos Fritz Benchmark 4.2 Intel Xeon 120-core / AMD Opteron 48-core chessbase.com/products/deepfritz12/index.asp kns/s Hardware Elo Intel i7-980X 3.33GHz 6x (T´s H) 18109 kn/s 2889 Elo 2xIntel Quad QX9775 15103 kn/s 2873 Elo Intel i7-975 (Tom´s Hardware) 12647 kn/s 2857 Elo AMD Phenom II X6 1090T 11219 kn/s 2846 Elo Intel -

Rybka Investigation and Summary of Findings for the ICGA Mark Lefler, Robert Hyatt, Harvey Williamson and ICGA Panel Members 12 May 2011
Rybka Investigation and Summary of Findings for the ICGA Mark Lefler, Robert Hyatt, Harvey Williamson and ICGA panel members 12 May 2011 1. Background 1.1 Purpose: To investigate claims that the chess playing program Rybka is a derivative of the chess programs Fruit and Crafty and violated International Computer Games Association (ICGA) Tournament rules. Rybka is a program by Vasik Rajlich. Fruit was written by Fabien Letouzey. Crafty was written by Robert Hyatt. 1.2 Allegations. Allegations have surfaced that Rybka 1.0 beta and later versions are derivatives of Fruit 2.1. Fruit 2.1 source code was distributed with a specific license in the copying.txt file. Part of this license reads: "For example, if you distribute copies of such a program, whether gratis or for a fee, you must give the recipients all the rights that you have. You must make sure that they, too, receive or can get the source code. And you must show them these terms so they know their rights." Allegations point out that by distributing Rybka, if it is based on Fruit, this GNU license was violated (http://icga.wikispaces.com/Open+letter+to+the+ICGA+about+the+Rybka- Fruit+issue). If versions of Rybka are derived from Fruit and participated in ICGA tournaments, then Rybka has also violated ICGA Tournament Rules. Specifically, the rules state: "Each program must be the original work of the entering developers. Programming teams whose code is derived from or including game-playing code written by others must name all other authors, or the source of such code, in the details of their submission form. -

Download Proceedings Book
International Conference on Artificial Intelligence towards Industry 4.0 (ICAII4.0) Nov 15-17, 2018 Iskenderun, Hatay / TURKEY Conference Proceedings Book ISBN: 978-605-68970-1-6 Editors : Assoc. Prof. Dr. Yakup Kutlu Assoc. Prof. Dr. Sertan Alkan Assist. Prof. Dr. Yaşar Daşdemir Assist. Prof. Dr. İpek Abasıkeleş Turgut Assist. Prof. Dr. Ahmet Gökçen Assist. Prof. Dr. Gökhan Altan Technical Editors: Merve Nilay Aydın Handan Gürsoy Demir Ezgi Zorarpacı Hüseyin Atasoy Kadir Tohma Mehmet Sarıgül Süleyman Serhan Narlı Kerim Melih Çimrin 2 International Conference on Artificial Intelligence towards Industry 4.0 (ICAII4.0) Nov 15-17, 2018 Iskenderun, Hatay / TURKEY International Conference on Artificial Intelligence towards Industry 4.0 (ICAII4.0) has been organized in Iskenderun, Hatay/Turkey on 15-17 November 2018. The main objective of ICAII4.0 is to present the latest research and results of scientists related to Artificial Intelligence, Industry 4.0 and all sub-disciplines of Computer Engineering. This conference provides opportunities for the different areas delegates to exchange new ideas and application experiences face to face, to establish business or research relations and to find global partners for future collaboration. We hope that the conference results provide significant contribution to the knowledge in this scientific field. The organizing committee of conference is pleased to invite prospective authors to submit their original manuscripts to ICAII4.0. All paper submissions will be double-blind and peer-reviewed and evaluated -

Including ACG8, ACG9, Games in AI Research, ACG10 T/M P. 18) Version: 20 June 2007
REFERENCE DATABASE 1 Updated till Vol. 29. No. 2 (including ACG8, ACG9, Games in AI Research, ACG10 t/m p. 18) Version: 20 June 2007 AAAI (1988). Proceedings of the AAAI Spring Symposium: Computer Game Playing. AAAI Press. Abramson, B. (1990). Expected-outcome: a general model of static evaluation. IEEE Transactions on Pattern Analysis and Machine Intelligence, Vol. 12, No.2, pp. 182-193. ACF (1990), American Checkers Federation. http://www.acfcheckers.com/. Adelson-Velskiy, G.M., Arlazarov, V.L., Bitman, A.R., Zhivotovsky, A.A., and Uskov, A.V. (1970). Programming a Computer to Play Chess. Russian Mathematical Surveys, Vol. 25, pp. 221-262. Adelson-Velskiy, M., Arlazarov, V.L., and Donskoy, M.V. (1975). Some Methods of Controlling the Tree Search in Chess Programs. Artificial Ingelligence, Vol. 6, No. 4, pp. 361-371. ISSN 0004-3702. Adelson-Velskiy, G.M., Arlazarov, V. and Donskoy, M. (1977). On the Structure of an Important Class of Exhaustive Problems and Methods of Search Reduction for them. Advances in Computer Chess 1 (ed. M.R.B. Clarke), pp. 1-6. Edinburgh University Press, Edinburgh. ISBN 0-85224-292-1. Adelson-Velskiy, G.M., Arlazarov, V.L. and Donskoy, M.V. (1988). Algorithms for Games. Springer-Verlag, New York, NY. ISBN 3-540-96629-3. Adleman, L. (1994). Molecular Computation of Solutions to Combinatorial Problems. Science, Vol. 266. p. 1021. American Association for the Advancement of Science, Washington. ISSN 0036-8075. Ahlswede, R. and Wegener, I. (1979). Suchprobleme. Teubner-Verlag, Stuttgart. Aichholzer, O., Aurenhammer, F., and Werner, T. (2002). Algorithmic Fun: Abalone. Technical report, Institut for Theoretical Computer Science, Graz University of Technology.