Identifying Memory Inefficiencies Via Object-Centric Profiling for Java
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
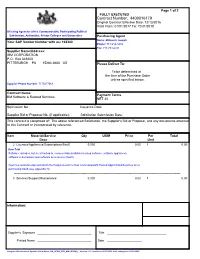
Contract Number: 4400016179
Page 1 of 2 FULLY EXECUTED Contract Number: 4400016179 Original Contract Effective Date: 12/13/2016 Valid From: 01/01/2017 To: 12/31/2018 All using Agencies of the Commonwealth, Participating Political Subdivision, Authorities, Private Colleges and Universities Purchasing Agent Name: Millovich Joseph Your SAP Vendor Number with us: 102380 Phone: 717-214-3434 Fax: 717-783-6241 Supplier Name/Address: IBM CORPORATION P.O. Box 643600 PITTSBURGH PA 15264-3600 US Please Deliver To: To be determined at the time of the Purchase Order unless specified below. Supplier Phone Number: 7175477069 Contract Name: Payment Terms IBM Software & Related Services NET 30 Solicitation No.: Issuance Date: Supplier Bid or Proposal No. (if applicable): Solicitation Submission Date: This contract is comprised of: The above referenced Solicitation, the Supplier's Bid or Proposal, and any documents attached to this Contract or incorporated by reference. Item Material/Service Qty UOM Price Per Total Desc Unit 2 Licenses/Appliances/Subscriptions/SaaS 0.000 0.00 1 0.00 Item Text Software: includes, but is not limited to, commercially available licensed software, software appliances, software subscriptions and software as a service (SaaS). Agencies must develop and attach the Requirements for Non-Commonwealth Hosted Applications/Services when purchasing SaaS (see Appendix H). -------------------------------------------------------------------------------------------------------------------------------------------------------- 3 Services/Support/Maintenance 0.000 0.00 -

Enterprise CRM Suites
Oracle Corporation et al v. SAP AG et al Doc. 844 Att. 14 EXHIBIT N Dockets.Justia.com August 29, 2008 | Updated: September 2, 2008 The Forrester Wave™: Enterprise CRM Suites, Q3 2008 by William Band for Business Process & Applications Professionals Making Leaders Successful Every Day ORCLX-PIN-000006_001 For Business Process & Applications Professionals Includes a Forrester Wave™ August 29, 2008 | Updated: September 2, 2008 The Forrester Wave™: Enterprise CRM Suites, Q3 2008 Buyers Face Difficult Choices In A Crowded Market by William Band with Sharyn C. Leaver, Pete Marston, Natalie L. Petouhoff, Ph.D., Elisse Gaynor, and Andrew Magarie EXECUTIVE SUMMARY Forrester evaluated leading enterprise CRM suite solutions against 516 criteria and found that with the latest releases of their solutions, Oracle’s Siebel and SAP maintain their status as Leaders with comprehensive functionality and much improved usability. Microsoft, salesforce.com, RightNow, and Oracle CRM On Demand have improved their credibility as enterprise-class solutions and have graduated into the Leaders group. The latter vendors all get high marks for ease-of-use and quick time-to-value. The Leaders are challenged by Strong Performers offering a diverse range of benefits. Oracle’s E-Business Suite CRM and PeopleSoft CRM are good options for their respective ERP customers looking for end-to-end integration. Chordiant, ciboodle, and Pegasystems offer business process management (BPM) strengths to help enterprises orchestrate complex customer-facing processes. Infor CRM Epiphany and Onyx CRM are working to regain market momentum through investments in product enhancements being made by their respective new corporate parents, Infor and Consona. -

Emerging Technologies for Academic Libraries in the Digital Age CHANDOS INFORMATION PROFESSIONAL SERIES
Emerging Technologies for Academic Libraries in the Digital Age CHANDOS INFORMATION PROFESSIONAL SERIES Series Editor: Ruth Rikowski (email: [email protected]) Chandos’ new series of books are aimed at the busy information professional. They have been specially commissioned to provide the reader with an authoritative view of current thinking. They are designed to provide easy-to-read and (most importantly) practical coverage of topics that are of interest to librarians and other information professionals. If you would like a full listing of current and forthcoming titles, please visit our web site www.chandospublishing.com or contact Hannah Grace-Williams on email [email protected] or telephone number +44 (0) 1993 848726. New authors: we are always pleased to receive ideas for new titles; if you would like to write a book for Chandos, please contact Dr Glyn Jones on email [email protected] or telephone number +44 (0) 1993 848726. Bulk orders: some organisations buy a number of copies of our books. If you are interested in doing this, we would be pleased to discuss a discount. Please contact Hannah Grace-Williams on email [email protected] or telephone number +44 (0) 1993 848726. Emerging Technologies for Academic Libraries in the Digital Age LILI LI Chandos Publishing Oxford · England Chandos Publishing (Oxford) Limited TBAC Business Centre Avenue 4 Station Lane Witney Oxford OX28 4BN UK Tel: +44 (0) 1993 848726 Fax: +44 (0) 1865 884448 E-mail: [email protected] www.chandospublishing.com First published in Great Britain in 2009 ISBN: 978 1 84334 320 2 (paperback) 978 1 84334 323 3 (hardback) 1 84334 320 7 (paperback) 1 84334 323 1 (hardback) © LiLi Li, 2009 British Library Cataloguing-in-Publication Data. -

Oracle Corporation (Exact Name of Registrant As Specified in Its Charter)
ORACLE CORP FORM 10-Q (Quarterly Report) Filed 03/23/12 for the Period Ending 02/29/12 Address 500 ORACLE PARKWAY MAIL STOP 5 OP 7 REDWOOD CITY, CA 94065 Telephone 6505067000 CIK 0001341439 Symbol ORCL SIC Code 7372 - Prepackaged Software Industry Software & Programming Sector Technology Fiscal Year 05/31 http://www.edgar-online.com © Copyright 2015, EDGAR Online, Inc. All Rights Reserved. Distribution and use of this document restricted under EDGAR Online, Inc. Terms of Use. Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 10-Q x QUARTERLY REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the quarterly period ended February 29, 2012 or ¨ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission File Number: 000-51788 Oracle Corporation (Exact name of registrant as specified in its charter) Delaware 54-2185193 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification No.) 500 Oracle Parkway Redwood City, California 94065 (Address of principal executive offices) (Zip Code) (650) 506-7000 (Registrant’s telephone number, including area code) Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -

Is Open Source the ERP Cure-All? Page 1 of 5
Is Open Source the ERP Cure-All? Page 1 of 5 Enterprise Resource Planning PRINT THIS PAGE NOW Is Open Source the ERP Cure-All? 5/1/2008 By Joseph C. Panettieri Conventional and hosted applications thrive, but open source ERP is coming on strong. Here's how to choose the best type of solution for your own institution. Campus CIOs John Bielec and Bradley Wheeler are IT experts with strikingly similar missions: They want modern enterprise applications to manage their respective universities' critical information. Ultimately, Bielec and Wheeler took divergent paths to ERP (enterprise resource planning) success. Importantly, each CIO carefully assessed campus need and the most current options available, before committing to an ERP solution or solutions. Wheeler, VP for IT and CIO of Indiana University, has focused his efforts on open source ERP. In contrast, Bielec, Drexel University (PA) CIO, is leveraging closed source ERP software, but in a hosted model. Evolution of Options In many ways, the evolution of the ERP market is littered with ironies. When Oracle began buying up customer relationship management (CRM) and ERP companies, some universities worried that they would be left with fewer choices and higher prices. Yet, the rise of open source-coupled with the advent and growth of software as a service (SaaS)-has created a whole range of new ERP options. In addition to Oracle, today's options include Jenzabar, Campus Management, Datatel, SunGard Higher Education, and numerous others. For instance, 20-plus universities have joined the Kuali Foundation, a nonprofit organization driving open source ERP forward. Bigname Kuali backers include Cornell University (NY), Carnegie Mellon University (PA), the Massachusetts Institute of Technology, and Indiana University. -

Introduction to Cloud Computing
Introduction to Cloud Computing Business & Technology Timothy Chou © 2010 by Active Book Press 2nd Edition All rights reserved. ,6%1 Printed in the United States of America Contents ACKNOWLEDGEMENTS..........................................................................V INTRODUCTION.................................................................................... VIII SEVEN BUSINESS MODELS......................................................................1 MODEL ONE: TRADITIONAL.........................................................................3 MODEL TWO: OPEN SOURCE........................................................................5 MODEL THREE: OUTSOURCING....................................................................7 MODEL FOUR: HYBRID. ...............................................................................9 MODEL FIVE: HYBRID+ .............................................................................14 MODEL SIX: SOFTWARE AS A SERVICE ......................................................15 MODEL SEVEN: INTERNET .........................................................................17 COST OF SOFTWARE...................................................................................18 SUMMARY..................................................................................................22 APPLICATION CLOUD SERVICES .......................................................24 COLLABORATION .......................................................................................25 WEBEX STORY .............................................................................................26 -

Oracle Corporation
ORACLE CORPORATION The Oracle Corporation is an American global computer technology corporation, headquartered in Redwood City, California. The company primarily specializes in developing and marketing computer hardware systems and enterprise software products – particularly its own brands of database management systems. In 2011 Oracle was the second- largest software maker by revenue, after Microsoft.[3] The company also develops and builds tools for database development and systems of middle-tier software, enterprise resource planning (ERP) software, customer relationship management (CRM) software and supply chain management (SCM) software. Larry Ellison, a co-founder of Oracle, served as Oracle's CEO from founding. On September 18, 2014, it was announced that he would be stepping down (with Mark Hurd and Safra Catz to become CEOs). Ellison became executive chairman and CTO.[4] He also served as the Chairman of the Board until his replacement by Jeffrey O. Henley in 2004. On August 22, 2008, the Associated Press ranked Ellison as the top-paid chief executive in the world.[5] Larry Ellison , Ellison was born in New York City but grew up in Chicago. He studied at the University of Illinois at Urbana–Champaign and the University of Chicago without graduating before moving to California in 1966. While working at Ampex in the early 1970s, he became influenced by Edgar F. Codd's research on relational database design, which led in 1977 to the formation of what became Oracle. Oracle became a successful database vendor to mid- and low- Larry Ellison in October 2009. range systems, competing with Sybase and Microsoft SQL Server, Born August 17, 1944 (age 71) which led to Ellison being listed by Forbes Lower East Side, Manhattan, New York, U.S. -

Routledge Encyclopedia of Translation Technology
THE ROUTLEDGE ENCYCLOPEDIA OF TRANSLATION TECHNOLOGY The Routledge Encyclopedia of Translation Technology provides a state-of-the art survey of the field of computer-assisted translation. It is the first definitive reference to provide a comprehensive overview of the general, regional and topical aspects of this increasingly significant area of study. The Encyclopedia is divided into three parts: • Part One presents general issues in translation technology, such as its history and development, translator training and various aspects of machine translation, including a valuable case study of its teaching at a major university. • Part Two discusses national and regional developments in translation technology, offering contributions covering the crucial territories of China, Canada, France, Hong Kong, Japan, South Africa, Taiwan, the Netherlands and Belgium, the United Kingdom and the United States. • Part Three evaluates specific matters in translation technology, with entries focused on subjects such as alignment, bitext, computational lexicography, corpus, editing, online translation, subtitling and technology and translation management systems. The Routledge Encyclopedia of Translation Technology draws on the expertise of over 50 contributors from around the world and an international panel of consultant editors to provide a selection of articles on the most pertinent topics in the discipline. All the articles are self-contained, extensively cross-referenced, and include useful and up-to-date references and information for further reading. It will be an invaluable reference work for anyone with a professional or academic interest in the subject. Chan Sin-wai is Professor in the Department of Translation at The Chinese University of Hong Kong. His research interests include computer translation, translation studies and lexicography. -

Rightnow Technologies a Montana Success Story
Making Montana the First Best Place How Entrepreneurship is Creating High-Paying Jobs Greg Gianforte, Founder RightNow Technologies © RightNow Technologies, Inc. 2 $80,000 $60,000 $40,000 $20,000 Montana is 49 Montana $0 New York Connecticut Massachusetts New Jersey California Illinois Maryland Delaware Virginia Washington th Texas Colorado Nationally in Wages Alaska Minnesota New Hampshire Pennsylvania Georgia Michigan Arizona Rhode Island Wyoming Tennessee Louisiana Oregon Ohio North Dakota North Carolina Missouri Nevada Florida Wisconsin Kansas Indiana Oklahoma Alabama Utah Hawaii Vermont Kentucky New Mexico West Virginia Iowa South Carolina Nebraska Maine Arkansas Idaho 3 South Dakota Montana Mississippi RightNow At A Glance Started in Bozeman 1997 in an extra bedroom 14 years of continuous revenue growth Self-funded and cash flow positive from day one 1,100 employees worldwide with avg MT wage $86,000 Bozeman’s largest commercial employer Montana’s only public technology company $5 billion of economic value into Montana 5 Montana Quality of Life www.ILoveItHere.com 6 RightNow’s Success is Repeatable RightNow's Bozeman Campus High Tech uniquely is able to raises wages statewide Twenty five more RightNows would create: . 15,000 new high paying jobs in Montana . $120B+ of economic value created over 15 years (5x multiplier) 7 U.S. Earnings per Job, by Industry, 2012 $0 $20,000 $40,000 $60,000 $80,000 $100,000 Natural Resources $96,757 Hi-Tech $94,933 Manufacturing $60,568 Construction $52,050 Transp. & Warehousing $48,609 Arts -

Izbira Informacijske Rešitve Za Management Odnosov S Strankami
UNIVERZA V LJUBLJANI EKONOMSKA FAKULTETA MAGISTRSKO DELO IZBIRA INFORMACIJSKE REŠITVE ZA MANAGEMENT ODNOSOV S STRANKAMI Ljubljana, oktober 2006 ROBERT KUNSTELJ IZJAVA O AVTORSTVU IN MENTORSTVU MAGISTRSKEGA DELA Študent ROBERT KUNSTELJ izjavljam, da sem avtor tega magistrskega dela, ki sem ga napisal pod mentorstvom PROF. DR. MOJCE INDIHAR ŠTEMBERGER in skladno s 1. odstavkom 21. člena Zakona o avtorskih in sorodnih pravicah dovolim objavo magistrskega dela na fakultetnih spletnih straneh. V Ljubljani, dne 25.10.2006. Podpis:____________________ KAZALO 1. UVOD............................................................................................................................... 1 1.1. PROBLEMATIKA MAGISTRSKEGA DELA............................................................................ 1 1.2. NAMEN MAGISTRSKEGA DELA ............................................................................................ 2 1.3. CILJI MAGISTRSKEGA DELA.................................................................................................. 3 1.4. METODA RAZISKOVANJA V MAGISTRSKEM DELU ......................................................... 4 2. MANAGEMENT ODNOSOV S STRANKAMI.......................................................... 5 2.1. DEFINICIJA MANAGEMENTA ODNOSOV S STRANKAMI................................................. 5 2.2. CILJI IN KORISTI MANAGEMENTA ODNOSOV S STRANKAMI ....................................... 7 2.3. UMESTITEV IN VLOGA SISTEMA ZA MANAGEMENT ODNOSOV S STRANKAMI....... 8 3. UVAJANJE KONCEPTA ZA MANAGEMENT -

Vintage Filings, LLC (A PR Newswire Company)
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 10-K ࠚ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the Fiscal Year Ended December 31, 2010 OR □ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the Transition Period from to . Commission File Number 000-30141 LIVEPERSON, INC. (Exact Name of Registrant As Specified in Its Charter) Delaware 13-3861628 (State of Incorporation) (I.R.S. Employer Identification Number) 462 Seventh Avenue, 3rd Floor, New York, New York 10018 (Address of Principal Executive Offices) (Zip Code) (212) 609-4200 (Registrant’s Telephone Number, Including Area Code) Securities registered pursuant to Section 12(b) of the Act: Title of Each Class Name of Each Exchange on Which Registered Common Stock, par value $0.001 per share The Nasdaq Stock Market LLC Securities registered pursuant to Section 12(g) of the Act: None Indicate by check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes Ⅺ No ࠚ Indicate by check mark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes Ⅺ No ࠚ Indicate by check mark whether the registrant: (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -

Nexxphase HCC RFP Solution and Pricing
NexxPhase appreciates the opportunity to become a part of the State of *HRUJLD¶VWHFKQRORJ\ IXWXUHThe Georgia Technology Authority is structuring its supplier contracts and business relationships in a manner that allows each agency to make best-fit infrastructure decisions that derive from sound technical and business guidance from a trusted partner in GTA that harvests technology options that combine foresight, economy, versatility, and, primarily, pinpoint functionality that delivers measurable business outcomes. NexxPhase understands the GTA and partner agency objectives and needs, and we believe that our array of applications coalesces precisely with your stated objectives. <RX¶UH looking for a proven provider with all the latest tools. You want someone dependable, and aggressively-priced. You want a partner that is agile, responsive and scalable, as critical government services are sensitive to events and unforeseeable impacts. :KDW\RX¶UHORRNLQJ IRULVemblematic of what the greater enterprise contact center marketplace something we deal with every day. We welcome you to challenge us. NexxPhase will step forward. GTA and the agencies of government in the State of Georgia are intensively seeking solutions that drive down costs, increase efficiency of operation, and provide constituents immediate and meaningful issue closure through innovations and self-service. $VWKHVWDWHRI*HRUJLD¶VWUXHSDUWQHU1H[[3KDVHZLOOHQWHULQWR DVKDUHGPLVVLRQ WRGHOLYHU top-flight solutions that provide the state continuing opportunities to achieve cost-savings: x NexxPhase pricing versatility aligns fully with your pricing objectives outlined in the SURJUDP¶VVWDWHPHQWRIZRUN -C Solution Document §6.1 x :HZRQ¶WVWRSfine-tuning our solutions to yield additional savings throughout the life of each engagement x AND, we will guarantee our results (see our 2-E RFQ statement of work).