List of Applications Updated in ARL #2576
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Effective Virtual CPU Configuration with QEMU and Libvirt
Effective Virtual CPU Configuration with QEMU and libvirt Kashyap Chamarthy <[email protected]> Open Source Summit Edinburgh, 2018 1 / 38 Timeline of recent CPU flaws, 2018 (a) Jan 03 • Spectre v1: Bounds Check Bypass Jan 03 • Spectre v2: Branch Target Injection Jan 03 • Meltdown: Rogue Data Cache Load May 21 • Spectre-NG: Speculative Store Bypass Jun 21 • TLBleed: Side-channel attack over shared TLBs 2 / 38 Timeline of recent CPU flaws, 2018 (b) Jun 29 • NetSpectre: Side-channel attack over local network Jul 10 • Spectre-NG: Bounds Check Bypass Store Aug 14 • L1TF: "L1 Terminal Fault" ... • ? 3 / 38 Related talks in the ‘References’ section Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications What this talk is not about 4 / 38 Related talks in the ‘References’ section What this talk is not about Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications 4 / 38 What this talk is not about Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications Related talks in the ‘References’ section 4 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) libvirtd QMP QMP QEMU QEMU VM1 VM2 Custom Disk1 Disk2 Appliance ioctl() KVM-based virtualization components Linux with KVM 5 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) libvirtd QMP QMP Custom Appliance KVM-based virtualization components QEMU QEMU VM1 VM2 Disk1 Disk2 ioctl() Linux with KVM 5 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) Custom Appliance KVM-based virtualization components libvirtd QMP QMP QEMU QEMU VM1 VM2 Disk1 Disk2 ioctl() Linux with KVM 5 / 38 libguestfs (guestfish) Custom Appliance KVM-based virtualization components OpenStack, et al. -

Red Hat Enterprise Linux 7 7.1 Release Notes
Red Hat Enterprise Linux 7 7.1 Release Notes Release Notes for Red Hat Enterprise Linux 7 Red Hat Customer Content Services Red Hat Enterprise Linux 7 7.1 Release Notes Release Notes for Red Hat Enterprise Linux 7 Red Hat Customer Content Services Legal Notice Copyright © 2015 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

GNAT User's Guide for Native Platforms
GNAT User's Guide for Native Platforms GNAT User's Guide for Native Platforms , January 13, 2017 AdaCore Copyright c 2008-2017, Free Software Foundation i Table of Contents 1 About This Guide :::::::::::::::::::::::::::::: 2 1.1 What This Guide Contains ::::::::::::::::::::::::::::::::::::: 2 1.2 What You Should Know before Reading This Guide :::::::::::: 2 1.3 Related Information :::::::::::::::::::::::::::::::::::::::::::: 3 1.4 A Note to Readers of Previous Versions of the Manual :::::::::: 3 1.5 Conventions:::::::::::::::::::::::::::::::::::::::::::::::::::: 4 2 Getting Started with GNAT ::::::::::::::::::: 5 2.1 Running GNAT :::::::::::::::::::::::::::::::::::::::::::::::: 5 2.2 Running a Simple Ada Program :::::::::::::::::::::::::::::::: 5 2.3 Running a Program with Multiple Units :::::::::::::::::::::::: 6 2.4 Using the gnatmake Utility ::::::::::::::::::::::::::::::::::::: 7 3 The GNAT Compilation Model ::::::::::::::: 9 3.1 Source Representation:::::::::::::::::::::::::::::::::::::::::: 9 3.2 Foreign Language Representation:::::::::::::::::::::::::::::: 10 3.2.1 Latin-1::::::::::::::::::::::::::::::::::::::::::::::::::: 10 3.2.2 Other 8-Bit Codes:::::::::::::::::::::::::::::::::::::::: 10 3.2.3 Wide Character Encodings ::::::::::::::::::::::::::::::: 11 3.2.4 Wide Wide Character Encodings ::::::::::::::::::::::::: 12 3.3 File Naming Topics and Utilities :::::::::::::::::::::::::::::: 13 3.3.1 File Naming Rules ::::::::::::::::::::::::::::::::::::::: 13 3.3.2 Using Other File Names :::::::::::::::::::::::::::::::::: 14 3.3.3 Alternative -
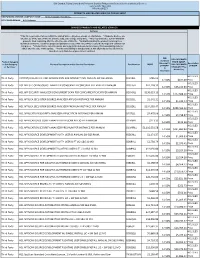
HCL Software's
IBM Branded, Fujistu Branded and Panasonic Branded Products and Related Services and Cloud Services Contract DIR-TSO-3999 PRICING SHEET PRODUCTS AND RELATED SERVICES PRICING SHEET RESPONDING VENDOR COMPANY NAME:____Sirius Computer Solutions_______________ PROPOSED BRAND:__HCL Software__________________________ BRANDED PRODUCTS AND RELATED SERVICES Software * This file is generated for use within the United States. All prices shown are US Dollars. * Products & prices are effective as of the date of this file and are subject to change at any time. * HCL may announce new or withdraw products from marketing after the effective date of this file. * Nothwithstanding the product list and prices identified on this file, customer proposals/quotations issued will reflect HCL's current offerings and commercial list prices. * Product list is not all inclusive and may not include products removed from availability (sale) or added after the date of this update. * Product availability is not guaranteed. Not all products listed below are found on every State/Local government contract. DIR DIR CUSTOMER Customer Product Category PRICE (MSRP- Discount % Description or SubCategory Product Description and/or Service Description Part Number MSRP DIR CUSTOMER off MSRP* of MSRP or Services* DISCOUNT Plus (2 Admin Fee) Decimals) HCL SLED Third Party CNTENT/COLLAB ACC AND WEBSPH PRTL SVR INTRANET PVU ANNUAL SW S&S RNWL E045KLL $786.02 14.50% $677.09 Price HCL SLED Third Party HCL APP SEC OPEN SOURCE ANALYZER CONSCAN PER CONCURRENT EVENT PER ANNUM D20H6LL $41,118.32 -

Computer Virus 16 Views 0 0 RELATED TITLES Virus
16 views 0 0 RELATED TITLES Virus Uploaded by Abu Naser Mohammad Saif Full description Save Embed Share Print Steve Jobs Cryptonomicon The Woman Who Smashed Codes: A True Computer Virus 16 views 0 0 RELATED TITLES Virus Uploaded by Abu Naser Mohammad Saif Full description Save Embed Share Print Steve Jobs Cryptonomicon The Woman Who Smashed Codes: A True Presentation Outline 1. Introduction: 2. VIRUS Definition and Naming: 3. Types of computer virus: 4. Example of Virus 5. To phases of virus 6. Symptom of computer attacked by virus 7. Special focus on: Trojan, & phishing site 8. Combating Viruses 9. Anti viruses & Firewall 16 views 0 0 RELATED TITLES Virus Uploaded by Abu Naser Mohammad Saif Full description Save Embed Share Print Steve Jobs Cryptonomicon The Woman Who Smashed Codes: A True Presentation Outline Symptom of computer attacked by virus Special focus on: Trojan, & phishing site Combating VirusesAnti viruses & Firewall 16 views 0 0 RELATED TITLES Virus Uploaded by Abu Naser Mohammad Saif Full description Save Embed Share Print Steve Jobs Cryptonomicon The Woman Who Smashed Codes: A True Presentation Outline 1. Introduction: 2. VIRUS Definition and Naming: 3. History of Computer Virus: 4. Types of computer virus: 5. Example of Virus 6. To phases of virus: 16 views 0 0 RELATED TITLES Virus Uploaded by Abu Naser Mohammad Saif Full description Save Embed Share Print Steve Jobs Cryptonomicon The Woman Who Smashed Codes: A True Introduction: Computer VIRUS Almost every uses has faced virus attack And loses some sort of computer resources Computer VIRUS is not a biological element rather computer program (s). -

Project Management Software March 2019
PROJECT MANAGEMENT SOFTWARE MARCH 2019 Powered by Methodology CONTENTS 3 Introduction 5 Defining Project Management Software 6 FrontRunners (Small Vendors) 8 FrontRunners (Enterprise Vendors) 10 Runners Up 22 Methodology Basics 2 INTRODUCTION his FrontRunners analysis minimum qualifying score of 3.96 Tis a data-driven assessment for Usability and 3.91 for User identifying products in the Project Recommended, while the Small Management software market that Vendor graphic had a minimum offer the best capability and value qualifying score of 4.55 for Usability for small businesses. For a given and 4.38 for User Recommended. market, products are evaluated and given a score for Usability (x-axis) To be considered for the Project and User Recommended (y-axis). Management FrontRunners, a FrontRunners then plots 10-15 product needed a minimum of 20 products each on a Small Vendor user reviews published within 18 and an Enterprise Vendor graphic, months of the evaluation period. based on vendor business size, per Products needed a minimum user category. rating score of 3.0 for both Usability and User Recommended in both In the Project Management the Small and Enterprise graphics. FrontRunners infographic, the Enterprise Vendor graphic had a 3 INTRODUCTION The minimum score cutoff to be included in the FrontRunners graphic varies by category, depending on the range of scores in each category. No product with a score less than 3.0 in either dimension is included in any FrontRunners graphic. For products included, the Usability and User Recommended scores determine their positions on the FrontRunners graphic. 4 DEFINING PROJECT MANAGEMENT SOFTWARE roject management software and document management, as well Phelps organizations manage as at least one of the following: time and deliver projects on time, on tracking, budgeting, and resource budget and within scope. -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

A Model-Driven Development and Verification Approach
A MODEL-DRIVEN DEVELOPMENT AND VERIFICATION APPROACH FOR MEDICAL DEVICES by Jakub Jedryszek B.S., Wroclaw University of Technology, Poland, 2012 B.A., Wroclaw University of Economics, Poland, 2012 A THESIS submitted in partial fulfillment of the requirements for the degree MASTER OF SCIENCE Department of Computing and Information Sciences College of Engineering KANSAS STATE UNIVERSITY Manhattan, Kansas 2014 Approved by: Major Professor John Hatcliff Abstract Medical devices are safety-critical systems whose failure may put human life in danger. They are becoming more advanced and thus more complex. This leads to bigger and more complicated code-bases that are hard to maintain and verify. Model-driven development provides high-level and abstract description of the system in the form of models that omit details, which are not relevant during the design phase. This allows for certain types of verification and hazard analysis to be performed on the models. These models can then be translated into code. However, errors that do not exist in the models may be introduced during the implementation phase. Automated translation from verified models to code may prevent to some extent. This thesis proposes approach for model-driven development and verification of medi- cal devices. Models are created in AADL (Architecture Analysis & Design Language), a language for software and hardware architecture modeling. AADL models are translated to SPARK Ada, contract-based programming language, which is suitable for software veri- fication. Generated code base is further extended by developers to implement internals of specific devices. Created programs can be verified using SPARK tools. A PCA (Patient Controlled Analgesia) pump medical device is used to illustrate the primary artifacts and process steps. -
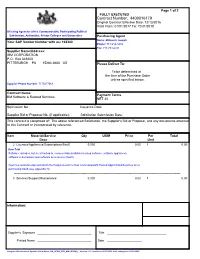
Contract Number: 4400016179
Page 1 of 2 FULLY EXECUTED Contract Number: 4400016179 Original Contract Effective Date: 12/13/2016 Valid From: 01/01/2017 To: 12/31/2018 All using Agencies of the Commonwealth, Participating Political Subdivision, Authorities, Private Colleges and Universities Purchasing Agent Name: Millovich Joseph Your SAP Vendor Number with us: 102380 Phone: 717-214-3434 Fax: 717-783-6241 Supplier Name/Address: IBM CORPORATION P.O. Box 643600 PITTSBURGH PA 15264-3600 US Please Deliver To: To be determined at the time of the Purchase Order unless specified below. Supplier Phone Number: 7175477069 Contract Name: Payment Terms IBM Software & Related Services NET 30 Solicitation No.: Issuance Date: Supplier Bid or Proposal No. (if applicable): Solicitation Submission Date: This contract is comprised of: The above referenced Solicitation, the Supplier's Bid or Proposal, and any documents attached to this Contract or incorporated by reference. Item Material/Service Qty UOM Price Per Total Desc Unit 2 Licenses/Appliances/Subscriptions/SaaS 0.000 0.00 1 0.00 Item Text Software: includes, but is not limited to, commercially available licensed software, software appliances, software subscriptions and software as a service (SaaS). Agencies must develop and attach the Requirements for Non-Commonwealth Hosted Applications/Services when purchasing SaaS (see Appendix H). -------------------------------------------------------------------------------------------------------------------------------------------------------- 3 Services/Support/Maintenance 0.000 0.00 -

IBM Lotus Communications CEO Bundle, IBM Messaging and Portal CEO Bundle, and IBM Lotus Working Together CEO Bundle
IBM Europe Announcement ZP07-0217, dated April 10, 2007 IBM Lotus Communications CEO bundle, IBM Messaging and Portal CEO bundle, and IBM Lotus Working Together CEO bundle Reference information ............................... 2 Overview The following three bundles no longer include Lotus® Workplace Messaging™: • IBM Lotus Communications CEO bundle • IBM Messaging and Portal CEO bundle • IBM Lotus Working Together® CEO bundle Lotus Workplace Messaging is withdrawn from marketing. For details, refer to Withdrawal Announcement ZP06-0531, dated December 12, 2006. The affected bundles are otherwise unchanged. Key prerequisites Refer to the Hardware requirements section. Planned availability dates • July 10, 2007: Electronic software delivery • July 10, 2007: Media and documentation See the complete letter for globalization details. IBM Europe Announcement ZP07-0217 IBM is a registered trademark of International Business Machines Corporation 1 Description IBM Lotus Communications CEO bundle The IBM Lotus Communications CEO bundle combines full support for the latest Internet mail standards with the industry-leading messaging, calendar and scheduling, discussion database, and reference database capabilities of IBM Lotus Domino® software, all in one manageable and reliable package. It also includes support for Lotus Domino partitioning (running more than one instance of Lotus Domino on the same machine using one copy of the Lotus Domino code). IBM Lotus Domino server software offers support for custom intranet and Internet applications. The applications may be developed in-house using IBM Lotus Domino Designer® or acquired from an Independent Software Vendor. IBM Lotus Domino server software includes support for IBM Lotus Domino clustering, which allows data to be replicated in real time across a cluster of servers. -

Software Development Process Improvements - Case QPR Software Plc
Software development process improvements - Case QPR Software Plc Lidia Zalevskaya Master’s Thesis Degree Programme in Information Systems Management 2019 Abstract Date: 2019.11.24 Author(s) Lidia Zalevskaya Degree programme Information Systems Management, Master’s Degree Thesis title Number of pages and appendix pages Software development process improvements - 98 + 26 Case QPR Software Plc Initially this study was planned as an effort to improve on a software development process within an existing team using an existing product code and systems. However, the situation changed and a new team (DevApps team) was established and given a new project, which created an opportunity to build a new type of team, product, process, and tools pipeline from scratch utilizing the improvement ideas. An Action Research framework was adopted as the theoretical approach for the study, while the Scrum methodology served as a framework for the development practices. The study began by summarizing previously identified problems in the software development process at QPR Software Plc and formulating improvement ideas focused on the coding workflow and Scrum practices. These were then tested in practice by the new DevApps scrum team. The research analysis centres on the process of choosing and setting up the new team’s development tools, figuring out ways of working, and implementing several iterations to find the best suitable development process. The most valuable empirical outcomes were the creation of a branching strategy and Git workflow for the DevApps team, the team members’ practical experience of working with Git and with the Azure DevOps developer services. A key outcome was the shift in many verification activities to earlier phases.