Digital Technical Journal, Number 7, August 1988: CVAX-Based Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Engineering Specification for the KA43 Processor Module Revision 1.0 1–May–1989 COMPANY CONFIDENTIAL RESTRICTED DISTRIBUTION
Engineering Specification for the KA43 Processor Module Revision 1.0 1–May–1989 COMPANY CONFIDENTIAL RESTRICTED DISTRIBUTION COPYRIGHT (c) 1989 by DIGITAL EQUIPMENT CORPORATION This information shall not be disclosed to non-Digital personnel or generally distributed within Digital. Distribution is restricted to persons authorized and designated by the responsible en- gineer or manager. This document shall not be left unattended, and when not in use shall be stored in a locked storage container. The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may occur in this document. The information in this document does not describe any program or product currently available from Digital Equipment Corporation. Nor does Digital Equipment Corporation commit to imple- ment this specification in any program or product. Digital Equipment Corporation makes no commitment that this document accurately describes any product which it might ever make. Digital Equipment Corporation CONTENTS Preface . ........................................................... v Chapter 1 INTRODUCTION .............................................. 1 1.1 Scope of Document ................................................... 1 1.2 General Description .................................................. 1 1.3 Applicable Documents ................................................. 2 Chapter 2 KA43 ROM MEMORY ........................................ -

Digital Technical Journal, Number 7, August 1988: CVAX
Digital Technical Tournal Digital Equipment Corporation Managing Editor Richard W Beam Edltor Jane C. Dlak Pcoductloa St& Production Editor - Helen 1 Partenon Designer - Charlotte Bell Typographers -Jonathan M. Bohy Macgaret Burdine lllusultor - Deborah Kc~lcy Advisoiy Board Samuel H. Fuller, Chairman Robert M. Glorioso John W. McCredle Mahendra R. Patel F. Grant Saviers William D. Srrcckr Victor A. Vyssutsky The Digital Technical Journal is published by Digital Equipment Corporatloa, 77 Reed Road, Hudson, Magsachu~etts0 1749. Changes of address should be sent to Digital Equipment Corporation. attention: List Maintenance. I0 Forbes Road, Northboro, MA 01532 Please indude the address label wlth changes marked. Comments on the content of any paper arc welcomed. Write to the editor at Mall Stop HL02.3/K11 at the published~bpaddress. Comments can ahbe sent on the BNET to RDVAX: :BIAKEor on the ARPANET to B~%RDVAX.DE~DE~. Copyright @ 1988 Digital Equipment Corporation. Copying without fee is permitted provided that such copies are made for use in educational lnstltutions by faculty members and are nor distributed for commercial advantage. Abstncting with credit of Digital Equipment Corporation's authorship is permltted. Requests for other copies for a Pee may br made to Digiul Press of Digital Equipment Corporation. A11 rights reserved. The information in this journal is subject to change without notice and should not bc construed as a com- mltment by Digital Equipment Corporation. Digital Equipment Corpmtion assumes no responslbllity for any errors that may appcss in this document ISSN 0898.901X Documentatlcm Number EY-6742H-DP The following are wademarks of Digital Gquipmcnt Corporation: ALL.IN-I. -

Chapter 1-Introduction to Microprocessors File
Chapter 1 Introduction to Microprocessors Expected Outcomes Explain the role of the CPU, memory and I/O device in a computer Distinguish between the microprocessor and microcontroller Differentiate various form of programming languages Compare between CISC vs RISC and Von Neumann vs Harvard architecture NMKNYFKEEUMP Introduction A microprocessor is an integrated circuit built on a tiny piece of silicon It contains thousands or even millions of transistors which are interconnected via superfine traces of aluminum The transistors work together to store and manipulate data so that the microprocessor can perform a wide variety of useful functions The particular functions a microprocessor perform are dictated by software The first microprocessor was the Intel 4004 (16-pin) introduced in 1971 containing 2300 transistors with 46 instruction sets Power8 processor, by contrast, contains 4.2 billion transistors NMKNYFKEEUMP Introduction Computer is an electronic machine that perform arithmetic operation and logic in response to instructions written Computer requires hardware and software to function Hardware is electronic circuit boards that provide functionality of the system such as power supply, cable, etc CPU – Central Processing Unit/Microprocessor Memory – store all programming and data Input/Output device – the flow of information Software is a programming that control the system operation and facilitate the computer usage Programming is a group of instructions that inform the computer to perform certain task NMKNYFKEEUMP Introduction Computer -

VAX 6000 Series Installation Guide
VAX 6000 Series Installation Guide Order Number EK–600EB–IN.002 This guide is intended for use by Digital customer service engineers and self-maintenance customers installing a VAX 6000 series system. digital equipment corporation maynard, massachusetts First Printing, October 1990 Revised, November 1991 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software, if any, described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software or equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Copyright ©1990, 1991 by Digital Equipment Corporation. All Rights Reserved. Printed in U.S.A. The following are trademarks of Digital Equipment Corporation: DEC PDP VAXcluster DEC LANcontroller ULTRIX VAXELN DECnet UNIBUS VMS DECUS VAX XMI DWMVA VAXBI FCC NOTICE: The equipment described in this manual generates, uses, and may emit radio frequency energy. The equipment has been type tested and found to comply with the limits for a Class A computing device pursuant to Subpart J of Part 15 of FCC Rules, which are designed to provide reasonable protection against such radio frequency interference when operated in a commercial environment. Operation of this equipment in a residential area may cause interference, in which case the user at his own expense may be required to take measures to correct the interference. -

VAX 6000 Platform Technical User's Guide
VAX 6000 Platform Technical User’s Guide Order Number: EK–600EA–TM-001 This manual serves as a reference for field-level repair or programming for systems based on the VAX 6000 platform. The manual describes the platform architecture, the XMI system bus, the DWMBB XMI-to-VAXBI adapter, and the power and cooling systems found in the H9657-CA/CB/CU cabinet. Digital Equipment Corporation First Printing, May 1991 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software, if any, described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software or equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Copyright ©1991 by Digital Equipment Corporation All Rights Reserved. Printed in U.S.A. The postpaid READER’S COMMENTS form on the last page of this document requests the user’s critical evaluation to assist in preparing future documentation. The following are trademarks of Digital Equipment Corporation: DEMNA PDP VAXcluster DEC ULTRIX VAXELN DEC LANcontroller UNIBUS VMS DECnet VAX XMI DECUS VAXBI dt This document was prepared using VAX DOCUMENT, Version 1.2 Contents PREFACE xiii CHAPTER 1 THE VAX 6000 PLATFORM OVERVIEW 1–1 1.1 SPECIFICATIONS 1–2 1.2 SYSTEM FRONT VIEW 1–4 -
VAX-Computer
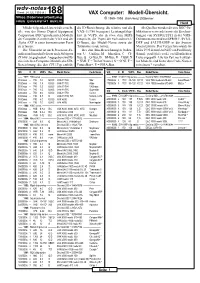
wdv-notes Stand: 24.JUL.1993 (4.) 188 VAX Computer: Modell-Übersicht. Wiss.Datenverarbeitung © 1980–1993 Karl-Heinz Dittberner FREIE UNIVERSITÄT BERLIN Hard Mit der folgenden Liste wird versucht, die ID-Bezeichnung, die relative (auf die Als Quellen wurden diverse DEC-Pu- alle von der Firma Digital Equipment VAX-11/780 bezogene) Leistungsfähig- blikationen verwendet sowie die Beschrei- Corporation (DEC) produzierten Modelle keit in VUPS, die in etwa dem MIPS bungen von SYS$GETSYI in der VMS- der Computer-Familien der VAX und der entspricht, die Typen der vorhandenen I/ Dokumentation und von $PRDEF, $VAX- Alpha AXP in einer konzentrierten Form O-Busse, der Modell-Name sowie der DEF und $ALPHADEF in der System zu erfassen. Tarnname (code name). Macro Library. Das Verzeichnis wurde im Die Übersicht ist nach Prozessor-Fa- Bei den Bus-Bezeichnungen bedeu- März 1993 der im UseNET von Paul Hardy milien und innerhalb dieser nach Subtypen ten: U = UniBus, M = MassBus, C = CI- (Email: [email protected]) veröffentlichten (X bzw. S) gegliedert. Angegeben sind für Bus, Q = Q-Bus, B = BI-Bus, D = DSSI, X Liste angepaßt. Alle zur Zeit noch aktuel- die einzelnen Computer-Modelle die SID- = XMI, T = TurboChannel, S = SCSI, F = len Modelle sind hinter dem Code-Namen Bezeichnung, die den CPU-Typ enthält, FutureBus+, E = EISA-Bus. mit einem * versehen. SID X ID VUPS Bus Model Name Code Name SID X ID VUPS Bus Model Name Code Name —— 1977: 700 series ———————————————————————————— —— 1991: NVAX+ chip series ———– Decimal SID = 385875968 ———————— 0100xxxx – 780 1.0 -

VAX VMS at 20
1977–1997... and beyond Nothing Stops It! Of all the winning attributes of the OpenVMS operating system, perhaps its key success factor is its evolutionary spirit. Some would say OpenVMS was revolutionary. But I would prefer to call it evolutionary because its transition has been peaceful and constructive. Over a 20-year period, OpenVMS has experienced evolution in five arenas. First, it evolved from a system running on some 20 printed circuit boards to a single chip. Second, it evolved from being proprietary to open. Third, it evolved from running on CISC-based VAX to RISC-based Alpha systems. Fourth, VMS evolved from being primarily a technical oper- ating system, to a commercial operat- ing system, to a high availability mission-critical commercial operating system. And fifth, VMS evolved from time-sharing to a workstation environment, to a client/server computing style environment. The hardware has experienced a similar evolution. Just as the 16-bit PDP systems laid the groundwork for the VAX platform, VAX laid the groundwork for Alpha—the industry’s leading 64-bit systems. While the platforms have grown and changed, the success continues. Today, OpenVMS is the most flexible and adaptable operating system on the planet. What start- ed out as the concept of ‘Starlet’ in 1975 is moving into ‘Galaxy’ for the 21st century. And like the universe, there is no end in sight. —Jesse Lipcon Vice President of UNIX and OpenVMS Systems Business Unit TABLE OF CONTENTS CHAPTER I Changing the Face of Computing 4 CHAPTER II Setting the Stage 6 CHAPTER -

Openvms I/O User's Reference Manual
OpenVMS I/O User’s Reference Manual Order Number: AA–PV6SD–TK April 2001 This manual contains the information necessary to interface directly with the I/O device drivers supplied as part of the Compaq OpenVMS operating system. Several examples of programming techniques are included. This document does not contain information on I/O operations using the OpenVMS Record Management Services. Revision/Update Information: This manual supersedes the OpenVMS I/O User’s Reference Manual, OpenVMS Alpha Version 7.2, OpenVMS VAX Version 7.2 Software Version: OpenVMS Alpha Version 7.3 OpenVMS VAX Version 7.3 Compaq Computer Corporation Houston, Texas © 2001 Compaq Computer Corporation Compaq, VAX, VMS, and the Compaq logo Registered in U.S. Patent and Trademark Office. OpenVMS and Tru64 are trademarks of Compaq Information Technologies Group, L.P in the United States and other countries. Microsoft, MS-DOS, Visual C++, Windows, and Windows NT are trademarks of Microsoft Corporation in the United States and other countries. Intel, Intel Inside, and Pentium are trademarks of Intel Corporation in the United States and other countries. Motif, OSF/1, and UNIX are trademarks of The Open Group in the United States and other countries. All other product names mentioned herein may be trademarks of their respective companies. Confidential computer software. Valid license from Compaq required for possession, use, or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor’s standard commercial license. Compaq shall not be liable for technical or editorial errors or omissions contained herein. -

Database Integration
I DATABASE INTEGRATION ALPHA SERVERS & WORKSTATIONS Digital ALPHA 21164 CPU Technical Journal Editorial The Digital TechnicalJournal is a refereed Cyrix is a trademark of Cyrix Corporation. Jane C. Blake, Managing Editor journal published quarterly by Digital dBASE is a trademark and Paradox is Helen L. Patterson, Editor Equipment Corporation, 30 Porter Road a registered trademark of Borland Kathleen M. Stetson, Editor LJ02/D10, Littleton, Massachusetts 01460. International, Inc. Subscriptionsto the Journal are $40.00 Circulation (non-U.S. $60) for four issues and $75.00 EDA/SQL is a trademark of Information Catherine M. Phillips, Administrator (non-U.S. $115) for eight issues and must Builders, Inc. Dorothea B. Cassady, Secretary be prepaid in U.S. funds. University and Encina is a registered trademark of Transarc college professors and Ph.D. students in Corporation. Production the electrical engineering and computer Excel and Microsoft are registered pde- Terri Autieri, Production Editor science fields receive complimentary sub- marks and Windows and Windows NT are Anne S. Katzeff, Typographer scriptions upon request. Orders, inquiries, trademarks of Microsoft Corporation. Joanne Murphy, Typographer and address changes should be sent to the Peter R Woodbury, Illustrator Digital TechnicalJournal at the published- Hewlett-Packard and HP-UX are registered by address. Inquiries can also be sent elec- trademarks of Hewlett-Packard Company. Advisory Board tronically to [email protected]. Single copies INGRES is a registered trademark of Ingres Samuel H. Fuller, Chairman and back issues are available for $16.00 each Corporation. Richard W. Beane by calling DECdirect at 1-800-DIGITAL Donald Z. Harbert (1-800-344-4825). -

Thesis May Never Have Been Completed
UvA-DARE (Digital Academic Repository) Digital Equipment Corporation (DEC): A case study of indecision, innovation and company failure Goodwin, D.T. Publication date 2016 Document Version Final published version Link to publication Citation for published version (APA): Goodwin, D. T. (2016). Digital Equipment Corporation (DEC): A case study of indecision, innovation and company failure. General rights It is not permitted to download or to forward/distribute the text or part of it without the consent of the author(s) and/or copyright holder(s), other than for strictly personal, individual use, unless the work is under an open content license (like Creative Commons). Disclaimer/Complaints regulations If you believe that digital publication of certain material infringes any of your rights or (privacy) interests, please let the Library know, stating your reasons. In case of a legitimate complaint, the Library will make the material inaccessible and/or remove it from the website. Please Ask the Library: https://uba.uva.nl/en/contact, or a letter to: Library of the University of Amsterdam, Secretariat, Singel 425, 1012 WP Amsterdam, The Netherlands. You will be contacted as soon as possible. UvA-DARE is a service provided by the library of the University of Amsterdam (https://dare.uva.nl) Download date:26 Sep 2021 Digital Equipment Corporation (DEC) (DEC) Corporation Digital Equipment David Thomas David Goodwin Digital Equipment Corporation (DEC): A Case Study of Indecision, Innovation and Company Failure David Thomas Goodwin Digital Equipment Corporation (DEC): A Case Study of Indecision, Innovation and Company Failure David Thomas Goodwin 1 Digital Equipment Corporation (DEC): A Case Study of Indecision, Innovation and Company Failure ACADEMISCH PROEFSCHRIFT ter verkrijging van de graad van doctor aan de Universiteit van Amsterdam op gezag van de Rector Magnificus prof. -

The Design of the VAX 4000 Model 100 and Microvax 3100 Model 90 Desktop Systems by Jonathan C. Crowell and David W. Maruska
The Design of the VAX 4000 Model 100 and MicroVAX 3100 Model 90 Desktop Systems By Jonathan C. Crowell and David W. Maruska 1 Abstract The MicroVAX 3100 Model 90 and VAX 4000 Model 100 systems were designed to meet the growing demand for low-cost, high-performance desktop servers and timesharing systems. Both systems are based on the NVAX CPU chip and a set of VLSI support chips, which provide outstanding CPU and I/O performance. Housed in like desktop enclosures, the two systems provide 24 times the CPU performance of the original VAX-11/780 computer. With over 2.5 gigabytes of disk storage and 128 megabytes of main memory, the complete base system fits in less than one cubic foot of space. The system design was highly leveraged from existing designs to help meet an aggressive schedule. 2 Introduction The demand for low-cost, high-performance desktop servers and timesharing systems is increasing rapidly. The MicroVAX 3100 Model 90 and VAX 4000 Model 100 systems were designed to meet this demand. Both systems are based on the NVAX CPU chip and a set of very large-scale integration (VLSI) support chips, which provide outstanding CPU and I/O performance.[1] Each member of the MicroVAX 3100 family of systems constitutes a low- cost, general-purpose, multiuser VAX system in an enclosure that fits on the desktop. This enclosure supports all the required components of a typical system, including the main memory, synchronous and asynchronous communication lines, thick-wire and ThinWire Ethernet, and up to five small computer system interface (SCSI)-based storage devices. -

The Computer History Simulation Project
The Computer History Simulation Project The Computer History Simulation Project The Computer History Simulation Project is a loose Internet-based collective of people interested in restoring historically significant computer hardware and software systems by simulation. The goal of the project is to create highly portable system simulators and to publish them as freeware on the Internet, with freely available copies of significant or representative software. Simulators SIMH is a highly portable, multi-system simulator. ● Download the latest sources for SIMH (V3.5-1 updated 15-Oct-2005 - see change log). ● Download a zip file containing Windows executables for all the SIMH simulators. The VAX and PDP-11 are compiled without Ethernet support. Versions with Ethernet support are available here. If you download the executables, you should download the source archive as well, as it contains the documentation and other supporting files. ● If your host system is Alpha/VMS, and you want Ethernet support, you need to download the VMS Pcap library and execlet here. SIMH implements simulators for: ● Data General Nova, Eclipse ● Digital Equipment Corporation PDP-1, PDP-4, PDP-7, PDP-8, PDP-9, PDP-10, PDP-11, PDP- 15, VAX ● GRI Corporation GRI-909 ● IBM 1401, 1620, 1130, System 3 ● Interdata (Perkin-Elmer) 16b and 32b systems ● Hewlett-Packard 2116, 2100, 21MX ● Honeywell H316/H516 ● MITS Altair 8800, with both 8080 and Z80 ● Royal-Mcbee LGP-30, LGP-21 ● Scientific Data Systems SDS 940 Also available is a collection of tools for manipulating simulator file formats and for cross- assembling code for the PDP-1, PDP-7, PDP-8, and PDP-11.