Remain in Touch Remain in Touch
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

October 2009 to September 2010
Remain in Touch Freedom Through Vigilance Association Annual History October 2009 – September 2010 Objective The overall objectives of the Freedom Through Vigilance Association (FTVA) are to foster continued awareness of the mission and accomplishments of the United States Air Force, in general, and specifically those of the Air Force Intelligence, Surveillance and Reconnaissance Agency – and to provide Association members a forum for desirable social, educational and humanitarian services. Period of history This history covers October 2009 – September 2010 and spans the social year of the FTVA. Organization The Kelly AFB Commander, Col. John Webb, organized the Freedom Through Vigilance Association, formerly known as the USAFSS/ESC Association and the USAFSS/ESC Alumni Association, on October 26, 1981, with the approval of the Association’s Constitution and Bylaws. The Alumni charter was granted on December 2, 1981. William T. Ballard was the chartering president. 1 FTVA Board of Directors The Association’s 2010 officers and directors consisted of the following: Executive Board Lee Anthony – President Ron Haygood – Vice President Bob Cope – Treasurer Loren (Phred) Sevening – Secretary Chris Cook – Immediate Past President Directors Barnie Gavin – Historian Bob Baert – Membership/Webmaster Dennis “Rass” Rassmussen – Newsletter Chairman Jim McLendon – Official activities Joe Hurst – Sports Ken Williams – Social Chairman Kenny O’Neal – Membership Chairman A.J. Harrison – Picnic Chairman Directors Emeritus Bill Ballard – Hall of Honor Grover -

Air Commando JOURNAL Summer 2014 Vol 3, Issue 2 4 Foreword Col (Ret) Ronald Terry 9 AC-130S in Operation Rice
summer 2014.indd 1 7/29/2014 3:32:13 PM OCT 16 - 19 RAMADA BEACH RESORT/FT WALTON BEACH, FL THURSDAY SATURDAY NIGHT BANQUET w Early Bird Social FRIDAY GOLF w Social Hour 1730-1900 w Guests of Honor: Gen (Ret) at Shalimar Pointe FRIDAY w Golf Tournament Norton Schwartz and Golf Club w Fish Fry Mr Kurt Muse w SATURDAY Air Commando Hall of Fame Presentations 85 rooms available at the w Professional Seminar/ Ramada Plaza Beach Resort Business Meeting Breakfast w AFSOC Commander’s located in Ft Walton Beach. w Banquet Leadership Awards Mention Air Commandos to w Entertainment receive a special rate of $99 (first SUNDAY come/first serve) w ACA Open House BANQUET DINNER Call 850-243-9161 to w Memorial Service reserve by Sep 1, 2014. Our dinner features a house salad to w BBQ accompany the entree of garlic blasted chicken breast and shrimp Montreal served with blistered tomato compote along with rosemary Online registration begins July 1st RSVP by Oct 10, 2014 roasted new potatoes, broccoli & carrots. The at www.aircommando.org dessert will be a praline cheesecake. or call 850-581-0099 Dress for Active Duty military is Service Dress Email: [email protected] WWW.AIRCOMMANDO.ORG summer 2014.indd 2 7/29/2014 3:32:14 PM Air Commando JOURNAL Summer 2014 Vol 3, Issue 2 4 Foreword Col (Ret) Ronald Terry 9 AC-130s in Operation Rice Bowl and Eagle Claw AC-130H aircraft #6568 “Night Stalker” crew. 20 16 Operation Continue Hope Bield Kirk and Blinking Light Somalia 1993-94 29 5 OCT 16 - 19 Spectre in Bosnia Chindit Chatter RAMADA BEACH RESORT/FT WALTON BEACH, FL 7 30 Hotwash Spirit 03 and the Golden Age of the Gunship 42 The Spectre Maintainer 35 The Opening Rounds 44 An Everlasting American Legacy ON THE COVER 45 CCT John Chapman AC-130H Spectre at the Battle of Takur Ghar Photo donated to the Air 51 Commando Association by 16th SOS Moving Forward Col (Ret) Sherman ‘Gene’ Eller. -

Mein Nachbar
Das deutsche Nachrichten-Magazin Leitartikel Partner und Gegner zugleich Warum der SPIEGEL weitere geheime Dokumente über die NSA-Affäre enthüllt as Verhältnis Deutschlands zu den USA in Zeiten der Die Bundesregierung hat die Selbstherrlichkeit der Welt- NSA-Affäre gleicht dem Ritt auf einer Schiffschaukel: macht lange hingenommen. Sie hat manches geahnt, vieles DAus luftigen Höhen geht es atemberaubend in die verdrängt und einiges über die Allgegenwart der NSA gewusst, Tiefe. Im Sommer vergangenen Jahres, als die ersten Snowden- weil der Bundesnachrichtendienst bei den Operationen mit- Enthüllungen bekannt wurden, erklärte die Regierung Merkel mischt. Dass der BND mit der NSA intensiv kooperiert, nicht die Affäre schon für beendet, bevor sie ihre Wucht entfaltete. nur bei der Terrorbekämpfung, sondern auch bei der unter- Im Herbst aber, als bekannt wurde, das private Handy der schiedslosen Massenüberwachung globaler Kommunikations- Bundeskanzlerin sei überwacht worden, erreichte das Ver- ströme, belegen die neuen Snowden-Dokumente. Die Deut- hältnis einen Tiefpunkt. Nun war von Konsequenzen die Rede, schen sind Partner und Gegner zugleich. von einem anderen Umgang unter Verbündeten. Die Bundeskanzlerin hat einen Amtseid auf das Grund- Dann reiste die Kanzlerin nach Washington, und wieder gesetz geschworen. Spionage gegen Deutschland ist nach kehrte Friede ein. Seither würden Transatlantiker wie Sicher- dem Strafgesetz verboten. Die Grundrechte der Bürger sind heitsbehörden am liebsten zum normalen Geschäft übergehen, also keine flexible Größe, abhängig davon, wie es um das Ver- bei dem die Aufgaben verteilt hältnis Deutschlands zu den sind: Die NSA ist der omnipo- USA gerade bestellt sein mag. tente Weltgeheimdienst, die Entweder haben die ameri- Deutschen sind der verständ- kanische und die deutsche nisvolle, hilfreiche Bündnis- Regierung miteinander ab - partner. -

Penetrate, Exploit, Disrupt, Destroy: the Rise of Computer Network Operations As a Major Military Innovation
PENETRATE, EXPLOIT, DISRUPT, DESTROY: THE RISE OF COMPUTER NETWORK OPERATIONS AS A MAJOR MILITARY INNOVATION by Craig J. Wiener A Dissertation Submitted to the Graduate Faculty of George Mason University in Partial Fulfillment of The Requirements for the Degree of Doctor of Philosophy Biodefense Committee: _______________________________________ Gregory Koblentz, Chair _______________________________________ A. Trevor Thrall _______________________________________ Stuart Malawer _______________________________________ Gregory Koblentz, Program Director _______________________________________ Mark J. Rozell, Dean Date: __________________________________ Fall Semester 2016 George Mason University Fairfax, VA Penetrate, Exploit, Disrupt, Destroy: The Rise of Computer Network Operations as a Major Military Innovation A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy at George Mason University By Craig J. Wiener Master of Science George Mason University, 2010 Bachelor of Arts New York University 1992 Director: Gregory Koblentz, Associate Professor Schar School of Policy and Government Fall Semester 2016 George Mason University Fairfax, VA Copyright 2016 Craig J. Wiener All Rights Reserved ii DISCLAIMER Any errors herein are solely those of the author. Additionally, the views expressed herein are those of the author. iii DEDICATION To Betty: I wish you were here. iv ACKNOWLEDGEMENTS I have a tremendous number of people to thank who have helped me throughout my Master of Science and PhD studies, leading to the submission of my dissertation. It literally took a village, and although I cannot thank everyone here, please know the depth of my gratitude is significant and ongoing. I would like to thank the faculty and staff of the George Mason School of Policy, Government and International Affairs, and the Graduate School of Public and International Affairs for giving me an opportunity to pursue my studies in national security. -

Cyber Center for Education & Innovation
VISION FOR THE NEW CYBER CENTER FOR EDUCATION & INNOVATION Home of the National Cryptologic Museum A PUBLIC-PRIVATE PARTNERSHIP WITH UNPARALLELED CYBER DEFENSE EXPERTISE. PLEASE JOIN US AND GET INVOLVED! The Cyber Center and our participation, volunteer Yleadership and support are urgently Museum Master needed to help us conceptualize, Plan includes: capitalize and construct the new Cyber Center for Education & Innovation, n A new state-of-the-art Home of the National Cryptologic Museum. Join us now! Museum To discuss your interest in supporting our efforts to create n The Conference Center this vital new resource, please contact: n Vigilance Air Park MGEN Roderick J. Isler, USA (Ret) n Classroom facilities Vice President, Cyber Center for Education & Innovation, New Museum Project Campaign n World class research National Cryptologic Museum Foundation and rare books library P.O. Box 1563 Millersville, MD 21108 n A comprehensive site and Office: 443-292-0091 land use concept Cell: 301-785-0896 Continued strong private and [email protected] public leadership is needed to realize this challenging vision. 1 CCEI-NCM Parking 498 Spaces 2 CCEI-NCM 3 Museum and Conference Center Drop-off 4 Service Road/ Loading Dock 5 Existing Museum 6 National Vigilance Park 7 Security Check Point 8 Colony Seven Road 9 Current NSA Parking (N1) 10 Current NSA Parking (N10) 11 Future VCP-1 12 86 foot Security Set Back 13 Entrance Signage PROPOSED SITE PLAN HELP US BUILD AND COMPLETE THIS NEW NATIONAL TREASURE. THE CYBER CENTER FOR EDUCATION & INNOVATION, HOME OF THE NATIONAL CRYPTOLOGIC MUSEUM is envisioned to be an integrated multi-purpose facility serving public and private stakeholders. -

Airpower Journal, Published Quarterly, Is the Professional Journal of the United States Air Force
Wínter 1994 JOURNAL rrM . Lü 1 Secretary of the Air Force Dr Sheila E. Widnall Air Force Chief of Staff Gen Ronald R. Fogleman Commander, Air Education and Training Command Gen Henry Viccellio, Jr. Commander, Air University Lt Gen Jay W. Kelley Commander, College of Aerospace Doctrine, Research, and Education Col Leroy Barnidge, Jr. Editor Col Thomas M. Kearney Associate Editor Maj John M. Poti Professional Staff Hugh Richardson, Contributing Editor Marvin W. Bassett, Contributing Editor Steven C. Garst, Director ofArt and Production Daniel M. Armstrong, Illustrator L. Susan Fair, Illustrator Thomas L. Howell, Prepress Production Manager The Airpower Journal, published quarterly, is the professional journal of the United States Air Force. It is designed to serve as an open forum for the presentation and stimulation of innovative think- ing on military doctrine, strategy, tactics, force structure, readiness, and other matters of national defense. The views and opinions expressed or im- plied in the Journal are those of the authors and should not be construed as carrying the official sanction of the Department of Defense, the Air Force, Air Education and Training Command, Air University, or other agencies or departments of the US government. Articles in this edition may be reproduced in whole or in part without permission. If they are reproduced, the Airpower Journal requests a cour- tesy line. JOURNAL Wlnter 1994. Vol. Vlll. No. 4 AJRP 101 Editorial 2 Desert Storm: The First Inform ation W ar? Col Edward Mann, USAF 4 M ilitary Ethics Col Richaxd Szafranski, USAF Dr James H. Toner lst Lt William D. Casebeer, USAF 15 N onlethal Concepts: Im plications for Air Force Intelligence Capt Edward F. -

Historical Dictionary of International Intelligence Second Edition
The historical dictionaries present essential information on a broad range of subjects, including American and world history, art, business, cities, countries, cultures, customs, film, global conflicts, international relations, literature, music, philosophy, religion, sports, and theater. Written by experts, all contain highly informative introductory essays on the topic and detailed chronologies that, in some cases, cover vast historical time periods but still manage to heavily feature more recent events. Brief A–Z entries describe the main people, events, politics, social issues, institutions, and policies that make the topic unique, and entries are cross- referenced for ease of browsing. Extensive bibliographies are divided into several general subject areas, providing excellent access points for students, researchers, and anyone wanting to know more. Additionally, maps, pho- tographs, and appendixes of supplemental information aid high school and college students doing term papers or introductory research projects. In short, the historical dictionaries are the perfect starting point for anyone looking to research in these fields. HISTORICAL DICTIONARIES OF INTELLIGENCE AND COUNTERINTELLIGENCE Jon Woronoff, Series Editor Israeli Intelligence, by Ephraim Kahana, 2006. Russian and Soviet Intelligence, by Robert W. Pringle, 2006. Cold War Counterintelligence, by Nigel West, 2007. World War II Intelligence, by Nigel West, 2008. Sexspionage, by Nigel West, 2009. Air Intelligence, by Glenmore S. Trenear-Harvey, 2009. Middle Eastern Intelligence, by Ephraim Kahana and Muhammad Suwaed, 2009. German Intelligence, by Jefferson Adams, 2009. Ian Fleming’s World of Intelligence: Fact and Fiction, by Nigel West, 2009. Naval Intelligence, by Nigel West, 2010. Atomic Espionage, by Glenmore S. Trenear-Harvey, 2011. Chinese Intelligence, by I. C. -

THE VULNERABLE Our Military Problems and How to Fix Them
AMERICA THE VULNERABLE Our Military Problems And How To Fix Them EDITED BY JOHN F. LEHMAN AND HARVEY SICHERMAN FOREIGN POLICY RESEARCH INSTITUTE PHILADELPHIA Dedication On a sad note, Colonel Harry G. Summers Jr., U.S. Army (ret.), who penned the article dealing with operations, procurement, and the defense industrial base and sat as a panelist for our second conference, passed away on November 14, 1999. Colonel Summers, a veteran of the Korean and Vietnam Wars, was the recipient of two Legions of Merit, the Silver Star, three Bronze Stars, two Purple Hearts, two Air Medals, and two awards of the Combat Infantryman’s Badge, and also authored numerous books, articles, and columns. He was, in short, the quintessential soldier- scholar. We dedicate this volume to his memory. TABLE OF CONTENTS Preface vii John H. Ball America the Vulnerable 1 John F. Lehman and Harvey Sicherman Roles and Missions 12 Donald Kagan Superpowers Don’t Do Windows 27 John Hillen The U.S. Presumption of Quick, Costless Wars 48 Andrew P. N. Erdmann Operations, Procurement, and Industrial Base 73 Harry G. Summers Jr. Civil-Military Relations 84 Eliot A. Cohen The U.S. Military Must Find Its Voice 96 Sam C. Sarkesian An Uninformed Debate on Military Culture 115 Don M. Snider Does Military Culture Matter? 134 Williamson Murray Must U.S. Military Culture Reform? 152 John Hillen The Case for National Missile Defense 171 Keith B. Payne v AMERICA THE VULNERABLE Rethinking Bio-Chemical Dangers 182 Henry Sokolski PREFACE Bad Medicine for Biological Terror 196 Andrew J. Bacevich Asymmetrical Adversaries 215 In 1996, the Foreign Policy Research Institute convened a Defense Winn Schwartau Task Force composed of distinguished scholars and practitioners The Risks of a Networked Military 225 to examine the increasingly important debates over U.S. -

NSA-FOIACASELOG-2016.Pdf
This document is made available through the declassification efforts and research of John Greenewald, Jr., creator of: The Black Vault The Black Vault is the largest online Freedom of Information Act (FOIA) document clearinghouse in the world. The research efforts here are responsible for the declassification of hundreds of thousands of pages released by the U.S. Government & Military. Discover the Truth at: http://www.theblackvault.com NATIONAL SECURITY AGENCY CENTRAL SECURITY SERVICE FORT GEORGE G. MEADE, MARYLAND 20755-6000 FOIA Case: 100503A 4 April 2017 JOHN GREENEWALD Dear Mr. Greenewald: This responds to your Freedom of Information Act (FOIA) request dated 1 January 2017 which was received by this office on 2 January 2017, for "a copy of the FOIA case log for calendar year 2016." For purposes of this request and based on the information you provided in your letter, you are considered an "all other" requester. As such, you are allowed 2 hours of search and the duplication of 100 pages at no cost. Since processing fees were minimal, no fees were assessed. Your request has been processed under the FOIA, and the logs for calendar year 2016 are enclosed, along with a FOIA Case Dispositions reference sheet that explains the final case dispositions. Please be advised that the logs do not contain the number of pages released. They contain a final disposition if the case was closed at the time the logs were created. If there is no final disposition, the case was still pending at the time the logs were created. Certain information has been deleted from the enclosures. -

State Intervention in Cross-Border Mergers and Acquisitions
Balancing Power without Weapons Why do states block some foreign direct investment on national security grounds even when it originates from within their own security com- munity? Government intervention into foreign takeovers of domestic companies is on the rise, and many observers find it surprising that states engage in such behavior not only against their strategic and mil- itary competitors, but also against their closest allies. Ashley Thomas Lenihan argues that such puzzling behavior can be explained by recog- nizing that states use intervention into cross-border mergers and acqui- sitions as a tool of statecraft to internally balance the economic and military power of other states through non-military means. This book tests this theory using quantitative and qualitative analysis of transac- tions in the United States, Russia, China, and fifteen European Union states. It deepens our understanding of why states intervene in foreign takeovers, the relationship between interdependence and conflict, the limits of globalization, and how states are balancing power in new ways. ashley thomas lenihan is a fellow at the Centre for Inter- national Studies at the London School of Economics and Political Science, and a term member of the Council on Foreign Relations. Her research focuses on the relationship between state power and foreign direct investment from an international relations perspective. Balancing Power without Weapons State Intervention into Cross-Border Mergers and Acquisitions Ashley Thomas Lenihan London School of Economics and Political Science University Printing House, Cambridge CB2 8BS, United Kingdom One Liberty Plaza, 20th Floor, New York, NY 10006, USA 477 Williamstown Road, Port Melbourne, VIC 3207, Australia 314–321, 3rd Floor, Plot 3, Splendor Forum, Jasola District Centre, New Delhi - 110025, India 79 Anson Road, #06-04/06, Singapore 079906 Cambridge University Press is part of the University of Cambridge. -
Amdocs and the NSA =Go to NFU Pages
NewsFollowUp NewsFollowUp.com search Franklin Scandal Omaha Obama sitemap home Amdocs Amdocs and the NSA =go to NFU pages News for the 99% ...................................Refresh F5...archive home 50th Anniversary of JFK assassination "Event of a Lifetime" at the Fess Parker Double Tree Inn. JFKSantaBarbara. Mossad, 9/11 Israeli Art Students Amdocs employee bailed out an 'Israeli art student' Gerald Shea, Memorandum to 9/11 Commission NFU MOST ACTIVE PA MP3 file of Fox News, Israeli Art Students, Amdocs Story Go to Alphabetic list Academic Freedom FOX NEWS CARL CAMERON FOUR-PART Conference REPORT: Fox News Series On Israeli Spying In Obama Death List Rothschild Timeline Bush / Clinton Body Count Narus / NSA / Boeing -- John O'neil , FBI agent killed on 9/11 Warrantless data mining ? in the WTC was investigating the Israeli Art Students, Amdocs Amdocs complicity Flight 77, Pentagon, 9/11? Amdocs / Narus / NSA 9/11 WTC art students Amdocs links DEA wire tap Fox News / Carl Cameron, Amdocs DEA / Amdocs links Whitehouse Telephone System Israeli art students / Amdocs Senate Select Committee on Intelligence Corporate Espionage John O'Neil, FBI, Israeli art students Israeli art students, 9/11 DEA, Amdocs, Israeli art students Fox News / Carl Cameron Report Amdocs and the NSA PROGRESSIVE REFERENCE CONSERVATIVE* AfroCubaWeb Israel Actions in the Americas Amdocs search: Narus AntiWar News: AMDOCS Dov Baharav, CEO Ron Moskovitz , CFO Antiwar pdf file art students, Israeli spies. Suspicious Rense 2001 All US Phone Call Records Michael Blum , Division Pres of Financial Services activities involving Israeli art students at DEA And Billing Done In Israel - Part 2 Carl Thomas G. -
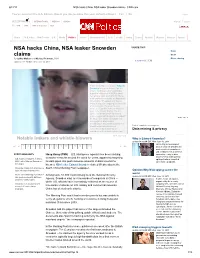
NSA Hacks China, NSA Leaker Snowden Claims - CNN.Com
6/12/13 NSA hacks China, NSA leaker Snowden claims - CNN.com You've selected the U.S. Edition. Would you like to make this your default edition? Yes | No Close SET EDITION: U.S. INTERNATIONAL MÉXICO ARABIC Sign up Log in TV: CNN CNNi CNN en Español HLN Home TV & Video CNN Trends U.S. World Politics Justice Entertainment Tech Health Living Travel Opinion iReport Money Sports NSA hacks China, NSA leaker Snowden SHARE THIS Print claims Email By Jethro Mullen and Michael Pearson, CNN More sharing Recommend 1.6k updated 4:05 PM EDT, Wed June 12, 2013 Former intelligence worker Edward Snowden revealed himself as the source of documents outlining a massive effort by the NSA to track cell phone calls and monitor the e- mail and Internet traffic of virtually all Americans. Snowden, 29, fled to Hong Kong after copying the last set of documents. He says he just wanted the public to know what the government was doing. "Even if you're not doing anything wrong you're being watched and recorded," he said. The Justice Department has begun a preliminary investigation into what it called "the unauthorized disclosure of Part of complete cov erage on classified information by an Data mining & privacy individual with authorized access." HIDE CAPTION Notable leakers and whistle-blowers Who is Edward Snowden? updated 9:32 AM EDT, Mon June 10, 2013 He's a high school dropout << < 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 > >> w ho w orked his w ay into the most secretive computers in U.S.