EMPA-Libro-Persuasiv
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

E-Books: Understanding the Basics June 2009 by Jane Lee, California Digital Library
E-books: Understanding the Basics June 2009 by Jane Lee, California Digital Library What exactly is an e-book anyway? Before we can talk about ebooks and the issues surrounding them, we must define what an e- book is. This is not as easy as one may think. Although e-books appear in headlines with regular frequency these days, there is still confusion about what exactly an e-book is that makes it difficult to focus on the real issues. For many people, especially in the last few years, an e-book is a handheld device whose main purpose is to look and act like a book. For others, an e-book is a book that one can read on one’s computer. And for a growing number of people, an e-book is something that you can read on your PDA, smartphone, iPod, etc. E-books made their first big splash on the market a decade ago, but they didn’t quite catch on with the general public. PDAs were taking a foothold, and companies began developing software that allowed people to read books on them. Subscription services for e-books – NetLibrary, for example – have been available to library patrons who have access to the required platform. The first dedicated, handheld electronic reading device, the Rocket ebook, made its appearance in 19981, but it wasn’t until the release of the Sony Reader and Amazon’s Kindle that e-book readers seemed commercially viable2. The arguments and questions about e-books – about their past, present, and future – that people formulate are shaped by how they define e-books for themselves. -

The Electronic Book As a Disruptive Technology." Disrupting Society from Tablet to Tablet
Western Oregon University Digital Commons@WOU History of the Book: Disrupting Society from Student Scholarship Tablet to Tablet 6-2015 Chapter 14 - The lecE tronic Book as a Disruptive Technology Janel Chandler Western Oregon University, [email protected] Follow this and additional works at: https://digitalcommons.wou.edu/history_of_book Part of the Critical and Cultural Studies Commons, Cultural History Commons, and the History of Science, Technology, and Medicine Commons Recommended Citation Chandler, Janel. "The Electronic Book as a Disruptive Technology." Disrupting Society from Tablet to Tablet. 2015. CC BY-NC. This is brought to you for free and open access by the Student Scholarship at Digital Commons@WOU. It has been accepted for inclusion in History of the Book: Disrupting Society from Tablet to Tablet by an authorized administrator of Digital Commons@WOU. For more information, please contact [email protected]. 14 The Electronic Book as a Disruptive Technology -Janel Chandler- In 2011, the United States made $90.3 million in the ebook market1. The electronic book, or ebook, is a book that is read on a computer or other electronic device2. Ebooks were invented in 1971 with Michael Hart’s “Project Gutenberg,” and Electronic books like the Nook and the Kindle have later took the world by storm in revolutionized the reading market1. 1998 with the invention of the ereader by Peanut Press2,3. Ebooks were originally just digital copies of books that someone typed up and put on the Internet. This new technology was a disruptive innovation because it granted instant availability, allowed for easier storage, was more convenient, and completely revolutionized the book market1. -
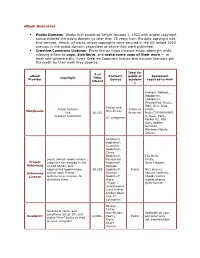
Ebook Resources Public Domain: Works First Published Before
eBook Resources Public Domain: Works first published before January 1, 1923 with proper copyright notice entered the public domain no later than 75 years from the date copyright was first secured. Hence, all works whose copyrights were secured in the US before 1923 are now in the public domain, regardless of where they were published. Creative Commons License: Every license helps creators retain copyright while allowing others to copy, distribute, and make some uses of their work — at least non-commercially. Every Creative Commons license also ensures licensors get the credit for their work they deserve. Ideal for # of eBook Content/ public or Equipment Copyright Titles Provider Genres academi required to view offered c Android, BeBook, Blackberry, eBookman, iPhone/iPod Touch, iPod, iRex, iLiad, Fiction and Public Domain Public or Kindle , Manybooks Non-Fiction and 26,021 Academic Nokia770/N800/N81 Creative Commons 0, Nook, Palm, 62 categories Pocket PC, PSP, Sony Reader, Symbian, Windows Mobile, Zaurus. Children's Bookshelf, Countries Bookshelf, Crime Bookshelf, The Nook, public domain books whose Periodicals Kindle, Project copyright has expired in the Bookshelf, Sony Ereader, Gutenberg United States, and Religion copyrighted books whose 30,000 Bookshelf, Public MP3 players, Gutenberg author gave Project Science gaming systems, License Gutenberg permission to Bookshelf, eBook readers, distribute them. Wars, mobile phones (Those 7 QiOO format. Subcategorie s are further broken down into 77 categories) Essays, Fiction, No area of terms and Non-Fiction, Readable on your conditions listed. Site just Readprint 8,000+ Poetry, Public computer only, states "Free" books to read Plays, not downloadable. on your computer. -

Die Neue Medialität Des Lesens: Ebooks Und Ebook- Reader“
DIPLOMARBEIT Titel der Diplomarbeit „Die neue Medialität des Lesens: eBooks und eBook- Reader“ Verfasserin Daniela Drobna, Bakk.a phil Angestrebter akademischer Grad Magistra der Philosophie (Mag. phil.) Wien, im Februar 2013 Studienkennzahl lt. Studienblatt: A 332 Studienrichtung lt. Studienblatt: Deutsche Philologie Betreuer: Assoz. Prof. Dr. Günther Stocker Inhaltsverzeichnis 1. Einleitung ............................................................................................................................... 1 2. Medientheoretische Einleitung ............................................................................................... 5 2.1. Definition Buch, eBook und eBook-Reader ...................................................................... 5 2.2. Medienevolution und Paradigmenwandel ....................................................................... 11 2.3. Medium und Medialität ................................................................................................... 18 2.4. Entwicklung von eBooks und eBook-Readern ............................................................... 22 2.5. Trends .............................................................................................................................. 26 3. Theorie der neuen Medialität des Lesens ............................................................................. 31 3.1. Paratexte .......................................................................................................................... 32 3.1.1. Typotopographie -

Die Meilensteine Der Computer-, Elek
Das Poster der digitalen Evolution – Die Meilensteine der Computer-, Elektronik- und Telekommunikations-Geschichte bis 1977 1977 1978 1979 1980 1981 1982 1983 1984 1985 1986 1987 1988 1989 1990 1991 1992 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 2018 2019 2020 und ... Von den Anfängen bis zu den Geburtswehen des PCs PC-Geburt Evolution einer neuen Industrie Business-Start PC-Etablierungsphase Benutzerfreundlichkeit wird gross geschrieben Durchbruch in der Geschäftswelt Das Zeitalter der Fensterdarstellung Online-Zeitalter Internet-Hype Wireless-Zeitalter Web 2.0/Start Cloud Computing Start des Tablet-Zeitalters AI (CC, Deep- und Machine-Learning), Internet der Dinge (IoT) und Augmented Reality (AR) Zukunftsvisionen Phasen aber A. Bowyer Cloud Wichtig Zählhilfsmittel der Frühzeit Logarithmische Rechenhilfsmittel Einzelanfertigungen von Rechenmaschinen Start der EDV Die 2. Computergeneration setzte ab 1955 auf die revolutionäre Transistor-Technik Der PC kommt Jobs mel- All-in-One- NAS-Konzept OLPC-Projekt: Dass Computer und Bausteine immer kleiner, det sich Konzepte Start der entwickelt Computing für die AI- schneller, billiger und energieoptimierter werden, Hardware Hände und Finger sind die ersten Wichtige "PC-Vorläufer" finden wir mit dem werden Massenpro- den ersten Akzeptanz: ist bekannt. Bei diesen Visionen geht es um die Symbole für die Mengendarstel- schon sehr früh bei Lernsystemen. iMac und inter- duktion des Open Source Unterstüt- möglichen zukünftigen Anwendungen, die mit 3D-Drucker zung und lung. Ägyptische Illustration des Beispiele sind: Berkley Enterprice mit neuem essant: XO-1-Laptops: neuen Technologien und Konzepte ermöglicht Veriton RepRap nicht Ersatz werden. -

Electronic Books: an Overview of the First Two Generations
East Tennessee State University Digital Commons @ East Tennessee State University Electronic Theses and Dissertations Student Works 12-2001 Electronic Books: An Overview of the First Two Generations. Todd O. Doman East Tennessee State University Follow this and additional works at: https://dc.etsu.edu/etd Part of the Reading and Language Commons Recommended Citation Doman, Todd O., "Electronic Books: An Overview of the First Two Generations." (2001). Electronic Theses and Dissertations. Paper 108. https://dc.etsu.edu/etd/108 This Thesis - Open Access is brought to you for free and open access by the Student Works at Digital Commons @ East Tennessee State University. It has been accepted for inclusion in Electronic Theses and Dissertations by an authorized administrator of Digital Commons @ East Tennessee State University. For more information, please contact [email protected]. E-Books: The First Two Generations A thesis presented to the faculty of the Department of English East Tennessee State University In partial fulfillment of the requirements for the degree Master of Arts in English by Todd Doman December 2001 Dr. Jeff Powers-Beck, Chair Dr. Kevin O’Donnell Dr. Darryl Haley Keywords: Electronic text, E-book, Reader ABSTRACT Electronic Books: An Overview of the First Two Generations by Todd Doman The electronic text reading device, or e-book, is an idea that has reached the implementation stage. Technology has only recently made possible the production of a device to challenge the printed book’s dominance as the media for information transmission. These microprocessor-based devices are attempts to exceed the limitations of printed texts while retaining their strengths. -

Printed Scholarly Books and E-Book Reading Devices: a Comparative Life Cycle Assessment of Two Book Options
Report No. CSS03-04 August 24, 2003 Printed Scholarly Books and E-book Reading Devices: A Comparative Life Cycle Assessment of Two Book Options Greg Kozak Printed Scholarly Books and E-book Reading Devices: A Comparative Life Cycle Assessment of Two Book Options By: Greg Kozak A project submitted in partial fulfillment of requirements for the degree of Master of Science (Resource Policy and Behavior) School of Natural Resources and Environment University of Michigan Ann Arbor August 23 , 2003 Faculty Advisors: Associate Research Scientist Gregory A. Keoleian, Chair Professor Jonathan Bulkley A report of the Center for Sustainable Systems Report No. CSS03-04 Document Description PRINTED SCHOLARLY BOOKS AND E-BOOK READING DEVICES: A COMPARATIVE LIFE CYCLE ASSESSMENT OF TWO BOOK OPTIONS Greg Kozak Center for Sustainable Systems, Report No. CSS03-04 University of Michigan, Ann Arbor, Michigan August 23, 2003 248 pp., tables, figures, 23 appendices This document is available online at: http://css.snre.umich.edu Center for Sustainable Systems School of Natural Resources and Environment University of Michigan 440 Church Street, Dana Building Ann Arbor, MI 48109-1041 Phone: 734-764-1412 Fax: 734-647-5841 Email: [email protected] Web: http://css.snre.umich.edu © Copyright 2003 by the Regents of the University of Michigan ABSTRACT Books have endured because they are remarkably well engineered; they are easy to use, portable, relatively cost-effective, and they require no instructions or manuals for their use. Despite their utility, however, conventional books published on paper have numerous limitations. Traditional, print-based books can be extremely costly to produce, store, ship, and sell. -

Unwrapping the Mystery of Ebook Reader Devices...For Christmas by Dorothy Mcfalls
Unwrapping the Mystery of Ebook Reader Devices...for Christmas By Dorothy McFalls I used to be like many readers out there, viewing the printed book as irreplaceable. There is something magical about holding a creative work. There’s a weight to them. A texture. It’s the tactile experience of turning the page to see what comes next... Wait a minute—did I just get a paper cut? On second thought, books are heavy. It takes two hands to hold them open. Fall asleep and let the book slip out of your hands—forget about finding your place again. And the typeface seems to be getting smaller and smaller...or perhaps I’m simply getting older. Not to mention publishers limiting the length of novels because of the rising cost of paper. Why not revolutionize how we read books? It has become perfectly acceptable to send an email instead of sitting down and penning a letter. The Internet has completely changed how we research new topics. Music downloads are fast becoming more popular than CDs. And more and more Americans are choosing the Internet as their main news source. Why not ebooks? For me, it was unknown—a confusion about exactly how ebooks worked—that held me back. I certainly wasn’t interested in reading books on my computer. I work at my computer, and reading is a pleasure. I want to curl up in my favorite chair or in my bed under a warm blanket, or lounge on the beach. Reading is all about comfort. And convenience. Can I really get that from an ebook? It took selling my first erotic romance to an e-publisher to get me to do some serious research on ebooks and ebook reader devices. -

Simpad SL4 Version V2.0
Technical Description SIMpad SL4 Version V2.0 SIMpad SL4 Technical Description Version V2.0 Important Notice! This document contains confidential technical information. Therefore, it is for internal use only. However, it can be forwarded to partners provided that they are bound to a non-disclosure agreement. Siemens AG 1/74 ICM CP 20.08.01, David Brunner Technical Description SIMpad SL4 Version V2.0 David Brunner, ICM CP PM I Version of 20.08.01 Copyright (C) Siemens AG, 2001 Published by ICM CP Right of technical modification reserved Technical data and features are binding only if they are individually and explicitly agreed in a written contract. Siemens AG 2/74 ICM CP 20.08.01, David Brunner Technical Description SIMpad SL4 Version V2.0 Table of Contents 1 Use and operation ...................................................................7 1.1 Housing and construction............................................................................7 1.2 Operation, controls .......................................................................................9 1.3 Operating states............................................................................................9 1.4 Resets.............................................................................................................9 2 Hardware ................................................................................11 2.1 Block diagram .............................................................................................11 2.2 Processor, graphic chip .............................................................................11 -

E-Books and Other E-Content E-Books and Other E-Content
You are at: ALA.org » PLA » Professional Tools » PLA Tech Notes » E-Books and Other E-Content E-Books and Other E-Content By Richard. W. Boss E-content—which includes electronic versions of books, journals, maps, media, and archival materials—has become a significant part of public libraries' resources. For most public libraries, the vast majority of e-content is made available from external sources; however, local e-image and e-manuscripts collections are common. While most content has been digitized from other formats, there increasingly are original electronic publications, especially e-journals. The major advantages of e-content are integrity of the collection, availability around the clock, remote access, and multiple simultaneous users. Unlike print, media, and archival materials; e-content is unlikely to be misplaced, stolen, or vandalized. It can be made available 24/7, rather than being available only during regular library hours. Except as there are licensing restrictions, e-content is available from anywhere and to multiple simultaneous users. However, electronic sources can be destroyed by system failures or hacking; therefore, almost all e-content providers maintain back-up files. The Tech Note focuses solely on e-content and the retrieval of it, not the tools required to create or maintain the content. The Library of Congress has inventoried tools and services for building collections of e-content. The index of tools and services is available at http://www.digitalpreservation.gov/partners/resources/tools/index.html or by searching for "LC index of digital preservation tools." The various types of e-content are discussed in the following paragraphs: E-Books The first major e-books effort dates back to 1971, earlier than the first e-journal effort, but has been slower to impact libraries and their users. -

EBOOKS Over the Past Two Decades the Publishing Industry Has Seen Disruptive Change
ROLE OF TECHNOLOGY IN EBOOKS Over the past two decades the publishing industry has seen disruptive change. This change has been primarily driven by evolution of digital books or eBooks as they are commonly known as. From rocket eBook reader in 1998 to the ever popular Amazon Kindle readers first launched in 2007 the dedicated reading devices have evolved tremendously. And so has the eBook standards from the OEB (Open eBook standard) to the current day EPUB3 and KF8. While the eBook industry is steadily moving from EPUB2 standards to EPUB3 and from mobi to KF8, for many publishers, digital publishing remains an alien planet. Many just wait for the technology to mature before investing others remain confused about how they can take advantage of the rich opportunities that are available in digital publishing. To simplify, technology in an eBook or digital publishing business can be broken down into three components – content, devices and platforms. In order to create a successful eBook business, a publisher needs to understand and leverage all the three components simultaneously. 01 CONTENT IS GOING TO BE THE KING At FutureBook 2014, keynote speaker George The trade and adult publishers on the other Berkowski said publishers need to focus on hand face a separate dilemma. Even though entertainment and media companies as real their content remains majorly text oriented, they competitors. To quote him: “You are not in the compete with the digital content that is available same industry, but the people who are reading across the internet. Fifty Shades of Grey and The Hunger Games are the same people sat on the tube reading Technology, while it enables amalgamation of BuzzFeed and every day. -

Turning the Page the Future of Ebooks
www.pwc.com Turning the Page The Future of eBooks Technology, Media & Telecommunications Today, it seems eBooks and eReaders This research is complemented by more Foreword provide more questions than answers for than 40 interviews with experts and senior the book industry: executives of reader manufacturers, a wide range of publishers, dealers, online • Will the industry face the same issues and traditional book shops, and libraries that music publishers did during its in Germany. The survey considers the digital transformation several years importance of eBooks and asks about their ago – primarily digital piracy and a loss market potential, drivers, obstacles for the of revenue as customers discovered future market development, and possible new methods of acquiring content and income models and marketing structures. adopted new listening habits? The survey focuses on the international Publishers, Internet bookstores, and • Who will purchase eReaders? Will market for eBooks and eReaders, companies that manufacture eReaders they be designed to appeal to a broad particularly with regard to mass market have high expectations for the digital group of customers or only to those books in the United States, United future of the book industry. A new who have a high degree of comfort Kingdom, the Netherlands, and Germany. generation of eReaders may, at last, with technology? Will people who read It also focuses on opportunities for digital achieve the long-awaited breakthrough once in a while want to buy an eReader, distribution of newspapers and magazines that lures consumers away from paper or will they only be purchased by the through tablets, such as the Apple iPad.