A+ Guide to Managing & Maintaining Your PC, 8Th Edition
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Z/OS ♦ Z Machines Hardware ♦ Numbers and Numeric Terms ♦ the Road to Z/OS ♦ Z/OS.E ♦ Z/OS Futures ♦ Language Environment ♦ Current Compilers ♦ UNIX System Services
Mainframes The Future of Mainframes Is Now ♦ z/Architecture ♦ z/OS ♦ z Machines Hardware ♦ Numbers and Numeric Terms ♦ The Road to z/OS ♦ z/OS.e ♦ z/OS Futures ♦ Language Environment ♦ Current Compilers ♦ UNIX System Services by Steve Comstock The Trainer’s Friend, Inc. http://www.trainersfriend.com 800-993-8716 [email protected] Copyright © 2002 by Steven H. Comstock 1 Mainframes z/Architecture z/Architecture ❐ The IBM 64-bit mainframe has been named "z/Architecture" to contrast it to earlier mainframe hardware architectures ♦ S/360 ♦ S/370 ♦ 370-XA ♦ ESA/370 ♦ ESA/390 ❐ Although there is a clear continuity, z/Architecture also brings significant changes... ♦ 64-bit General Purpose Registers - so 64-bit integers and 64-bit addresses ♦ 64-bit Control Registers ♦ 128-bit PSW ♦ Tri-modal addressing (24-bit, 31-bit, 64-bit) ♦ Over 140 new instructions, including instructions to work with ASCII and UNICODE strings Copyright © 2002 by Steven H. Comstock 2 z/Architecture z/OS ❐ Although several operating systems can run on z/Architecture machines, z/OS is the premier, target OS ❐ z/OS is the successor to OS/390 ♦ The last release of OS/390 was V2R10, available 9/2000 ♦ The first release of z/OS was V1R1, available 3/2001 ❐ z/OS can also run on G5/G6 and MP3000 series machines ♦ But only in 31-bit or 24-bit mode ❐ Note these terms: ♦ The Line - the 16MiB address limit of MVS ♦ The Bar - the 2GiB limit of OS/390 ❐ For some perspective, realize that 16EiB is... ♦ 8 billion times 2GiB ♦ 1 trillion times 16MiB ❐ The current release of z/OS is V1R4; V1R5 is scheduled for 1Q2004 Copyright © 2002 by Steven H. -

Broadband/IP/Cloud Computing
Broadband/IP/Cloud Computing Presentation to the Colorado Telecommunications Association www.cellstream.com (c) 2011 CellStream, Inc. 1 www.cellstream.com (c) 2011 CellStream, Inc. 2 www.cellstream.com (c) 2011 CellStream, Inc. 3 www.cellstream.com (c) 2011 CellStream, Inc. 4 www.cellstream.com (c) 2011 CellStream, Inc. 5 Past vs. Present The Past – 20th Century The Present – 21st Century • Peer-to-Peer with broadcast • Many-to-Many with multicast • Mix of Analog and Digital • All media is digital – single • Producers supply transport Consumers • All media is connected • Peer-to-Peer is 1:1 • Many-to-Many is M:N o Traditional Telephone • Producers and Consumers • Broadcast is 1:N do both o Newspaper o CNN takes reports from Twitter o TV/Radio o End users send pictures and reports www.cellstream.com (c) 2011 CellStream, Inc. 6 Where are we in Phone Evolution? PHONE 1.0 PHONE 2.0 PHONE 3.0 Soft phone Your Phone Number Your Phone Number Your Phone Number represents where you represents you represents an IP Address – are (e.g. 972-747- regardless of where you independent of location 0300 is home, 214- are. and appliance you are 405-3708 is work) using (e.g. IP Phone, Cell Phone, PDA, Computer, Television, etc.) www.cellstream.com (c) 2011 CellStream, Inc. 7 Phone 3.X • Examples of Phone 3.0 are Skype, Google Talk, others on a PC. • Phone 3.1 – Skype on an iTouch • Phone 3.2 – Android OS from Google – a phone Centric OS that runs on cellular appliances • Phone 3.3 – Android OS from Google that runs on a Phone Appliance www.cellstream.com (c) 2011 CellStream, Inc. -

Etir Code Lists
eTIR Code Lists Code lists CL01 Equipment size and type description code (UN/EDIFACT 8155) Code specifying the size and type of equipment. 1 Dime coated tank A tank coated with dime. 2 Epoxy coated tank A tank coated with epoxy. 6 Pressurized tank A tank capable of holding pressurized goods. 7 Refrigerated tank A tank capable of keeping goods refrigerated. 9 Stainless steel tank A tank made of stainless steel. 10 Nonworking reefer container 40 ft A 40 foot refrigerated container that is not actively controlling temperature of the product. 12 Europallet 80 x 120 cm. 13 Scandinavian pallet 100 x 120 cm. 14 Trailer Non self-propelled vehicle designed for the carriage of cargo so that it can be towed by a motor vehicle. 15 Nonworking reefer container 20 ft A 20 foot refrigerated container that is not actively controlling temperature of the product. 16 Exchangeable pallet Standard pallet exchangeable following international convention. 17 Semi-trailer Non self propelled vehicle without front wheels designed for the carriage of cargo and provided with a kingpin. 18 Tank container 20 feet A tank container with a length of 20 feet. 19 Tank container 30 feet A tank container with a length of 30 feet. 20 Tank container 40 feet A tank container with a length of 40 feet. 21 Container IC 20 feet A container owned by InterContainer, a European railway subsidiary, with a length of 20 feet. 22 Container IC 30 feet A container owned by InterContainer, a European railway subsidiary, with a length of 30 feet. 23 Container IC 40 feet A container owned by InterContainer, a European railway subsidiary, with a length of 40 feet. -

Z/OS, Language Environment, and UNIX How They Work Together
The Trainer’s Friend, Inc. 256-B S. Monaco Parkway Telephone: (800) 993-8716 Denver, Colorado 80224 (303) 393-8716 U.S.A. Fax: (303) 393-8718 E-mail: [email protected] Internet: www.trainersfriend.com z/OS, Language Environment, and UNIX How They Work Together The following terms that may appear in these materials are trademarks or registered trademarks: Trademarks of the International Business Machines Corporation: AD/Cycle, AIX, AIX/ESA, Application System/400, AS/400, BookManager, CICS, CICS/ESA, COBOL/370, COBOL for MVS and VM, COBOL for OS/390 & VM, Common User Access, CORBA, CUA, DATABASE 2, DB2, DB2 Universal Database, DFSMS, DFSMSds, DFSORT, DOS/VSE, Enterprise System/3090, ES/3090, 3090, ESA/370, ESA/390, Hiperbatch, Hiperspace, IBM, IBMLink, IMS, IMS/ESA, Language Environment, MQSeries, MVS, MVS/ESA, MVS/XA, MVS/DFP, NetView, NetView/PC, Object Management Group, Operating System/400, OS/400, PR/SM, OpenEdition MVS, Operating System/2, OS/2, OS/390, OS/390 UNIX, OS/400, QMF, RACF, RS/6000, SOMobjects, SOMobjects Application Class Library, System/370, System/390, Systems Application Architecture, SAA, System Object Model, TSO, VisualAge, VisualLift, VTAM, VM/XA, VM/XA SP, WebSphere, z/OS, z/VM, z/Architecture, zSeries Trademarks of Microsoft Corp.: Microsoft, Windows, Windows NT, Windows ’95, Windows ’98, Windows 2000, Windows SE, Windows XP Trademark of Chicago-Soft, Ltd: MVS/QuickRef Trademark of Phoenix Software International: (E)JES Registered Trademarks of Institute of Electrical and Electronic Engineers: IEEE, POSIX Registered Trademark of The Open Group: UNIX Trademark of Sun Microsystems, Inc.: Java Registered Trademark of Linus Torvalds: LINUX Registered Trademark of Unicode, Inc.: Unicode Preface This document came about as a result of writing my first course for UNIX on the IBM mainframe. -

Breaking Through the Myths to Reality: a Future-Proof View Of
Breaking Through the Myths to Reality A Future-Proof View of Fiber Optic Inspection and Cleaning Dear Viewer: As presented at BICSI® in February- 2018, this seminar has video and animations that Edward J. Forrest, Jr. are not available as a .pdf file. If you would like the RMS(RaceMarketingServices) original version, please contact BICSI or the author. Bringing Ideas Together Caution: This Presentation is going to be controversial! IT IS BASED ON 2,500 YEARS OF SCIENCE AND PRODUCT DEVELOPMENT 2 Fact OR FICTION of Fiber Optic Cleaning and Inspection This seminarWE WILL mayDISCUSS contradictAND currentDEFINE: trends ➢ There➢ Cleaningand are what OTHER you’ve is notWAYS been important…BESIDES taught. VIDEO ➢ ➢➢“Automatic99.9%Debris➢ ➢ExistingA “Reagent FiberonS Detection” CIENTIFICthe standards, Optic surface Grade” ConnectorR isEALITY of such“good Isopropanola fiber… as enough”.is optic a is IECconnector“Pass 61300Let’sanI NSPECTIONanythingeffective- Fail”separate- 3surface-35, is is bettereasy are Factsfiberto is “Best determine thantwoto from optic understand nothing!-dimensional Practice”Fiction cleaner What we’veTwoif the ( ALL-Dimensional connector) been taught/bought/soldand is Structure“clean” over the last 30+Myth yearsfrom may“diameter”. Scientific not be the same Reality thing! 3 Fact OR FICTION of Fiber Optic Cleaning and Inspection ➢ A Fiber Optic Connector is a Two-Dimensional Structure ➢ 99.9% “Reagent Grade” Isopropanol is an effective fiber optic cleaner ➢ Cleaning is not important… anything is better than nothing! ➢ There are OTHER WAYS BESIDES VIDEO INSPECTION to determine if the connector is “clean” ➢ Debris on the surface of a fiber optic connector surface is two-dimensional “diameter”. ➢ “Automatic Detection” is “good enough”. -
File Organization and Management Com 214 Pdf
File organization and management com 214 pdf Continue 1 1 UNESCO-NIGERIA TECHNICAL - VOCATIONAL EDUCATION REVITALISATION PROJECT-PHASE II NATIONAL DIPLOMA IN COMPUTER TECHNOLOGY FILE Organization AND MANAGEMENT YEAR II- SE MESTER I THEORY Version 1: December 2 2 Content Table WEEK 1 File Concepts... 6 Bit:... 7 Binary figure... 8 Representation... 9 Transmission... 9 Storage... 9 Storage unit... 9 Abbreviation and symbol More than one bit, trit, dontcare, what? RfC on trivial bits Alternative Words WEEK 2 WEEK 3 Identification and File File System Aspects of File Systems File Names Metadata Hierarchical File Systems Means Secure Access WEEK 6 Types of File Systems Disk File Systems File Systems File Systems Transactional Systems File Systems Network File Systems Special Purpose File Systems 3 3 File Systems and Operating Systems Flat File Systems File Systems according to Unix-like Operating Systems File Systems according to Plan 9 from Bell Files under Microsoft Windows WEEK 7 File Storage Backup Files Purpose Storage Primary Storage Secondary Storage Third Storage Out Storage Features Storage Volatility Volatility UncertaintyAbility Availability Availability Performance Key Storage Technology Semiconductor Magnetic Paper Unusual Related Technology Connecting Network Connection Robotic Processing Robotic Processing File Processing Activity 4 4 Technology Execution Program interrupts secure mode and memory control mode Virtual Memory Operating Systems Linux and UNIX Microsoft Windows Mac OS X Special File Systems Journalized File Systems Graphic User Interfaces History Mainframes Microcomputers Microsoft Windows Plan Unix and Unix-like operating systems Mac OS X Real-time Operating Systems Built-in Core Development Hobby Systems Pre-Emptification 5 5 WEEK 1 THIS WEEK SPECIFIC LEARNING OUTCOMES To understand: The concept of the file in the computing concept, field, character, byte and bits in relation to File 5 6 6 Concept Files In this section, we will deal with the concepts of the file and their relationship. -
IBM-IS-DCI-UR-Newsletter.Pdf
Monthly Newsletter Mar 2016 Monthly Journal on Technology Know-How of IBM’s Technology space Tech Updates on Mainframe Platform “Mainframe“ the IBM Dictionary Of Computing defines "mainframe" as "a large computer, in particular one to which other computers can be connected so that they can share facilities the mainframe provides (for example, a System/370 computing system to which personal computers are attached so that they can upload and download programs and data). The term “Mainframe “ usually refers to hardware only, namely, main storage, execution circuitry and peripheral units“ level, as opposed to trying to do it all from the System z platform. Did you know that mainframes and all other computers have two types of physical storage: Internal and external. Physical storage located on the mainframe processor itself. This is called processor storage, real storage or central storage; think of it as memory for the mainframe. Physical storage external to the mainframe, including storage on direct access devices, such as disk drives and tape drives. This storage is called paging storage or auxiliary storage. The primary difference between the two kinds of storage relates to the way in which it is accessed, as follows: Central storage is accessed synchronously with the processor. That is, the processor must wait while data is retrieved from central storage. Auxiliary storage is accessed asynchronously. The processor accesses auxiliary storage through an input/output (I/O) request, which is scheduled to run amid other work requests in the system. During an I/O request, the processor is free to execute other, unrelated work. -

A Practical Introduction to Computer Architecture
A Practical Introduction to Computer Architecture Daniel Page [email protected] h i git # ba293a0e @ 2019-11-14 © Daniel Page [email protected] h i git # ba293a0e @ 2019-11-14 2 © Daniel Page [email protected] h i MATHEMATICAL PRELIMINARIES In Mathematics you don’t understand things. You just get used to them. – von Neumann The goal of this Chapter is to provide a fairly comprehensive overview of theory that underpins the rest of the book. At first glance the content may seem a little dry, and is often excluded in other similar books. It seems clear, however, that without a solid understanding of said theory, using the constituent topics to solve practical problems will be much harder. The topics covered all relate to the field of discrete Mathematics; they include propositional logic, sets and functions, Boolean algebra and number systems. These four topics combine to produce a basis for formal methods to describe, manipulate and implement digital systems. Readers with a background in Mathematics or Computer Science might skip this Chapter and use it simply for reference; those approaching it from some other background would be advised to read the material in more detail. 1 Propositional logic Definition 0.1. A proposition is a statement whose meaning, termed the truth value, is either true or false (less formally, we say the statement is true if it has a truth value of true and false if it has a truth value of false). A given proposition can involve one or more variables; only when concrete values are assigned to the variables can the meaning of a proposition be evaluated. -

The 2016 SNIA Dictionary
A glossary of storage networking data, and information management terminology SNIA acknowledges and thanks its Voting Member Companies: Cisco Cryptsoft DDN Dell EMC Evaluator Group Fujitsu Hitachi HP Huawei IBM Intel Lenovo Macrosan Micron Microsoft NetApp Oracle Pure Storage Qlogic Samsung Toshiba Voting members as of 5.23.16 Storage Networking Industry Association Your Connection Is Here Welcome to the Storage Networking Industry Association (SNIA). Our mission is to lead the storage industry worldwide in developing and promoting standards, technologies, and educational services to empower organizations in the management of information. Made up of member companies spanning the global storage market, the SNIA connects the IT industry with end-to-end storage and information management solutions. From vendors, to channel partners, to end users, SNIA members are dedicated to providing the industry with a high level of knowledge exchange and thought leadership. An important part of our work is to deliver vendor-neutral and technology-agnostic information to the storage and data management industry to drive the advancement of IT technologies, standards, and education programs for all IT professionals. For more information visit: www.snia.org The Storage Networking Industry Association 4360 ArrowsWest Drive Colorado Springs, Colorado 80907, U.S.A. +1 719-694-1380 The 2016 SNIA Dictionary A glossary of storage networking, data, and information management terminology by the Storage Networking Industry Association The SNIA Dictionary contains terms and definitions related to storage and other information technologies, and is the storage networking industry's most comprehensive attempt to date to arrive at a common body of terminology for the technologies it represents. -
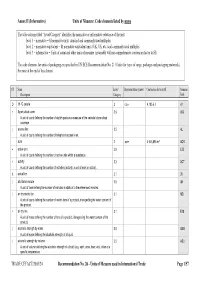
Units of Measure Used in International Trade Page 1/57 Annex II (Informative) Units of Measure: Code Elements Listed by Name
Annex II (Informative) Units of Measure: Code elements listed by name The table column titled “Level/Category” identifies the normative or informative relevance of the unit: level 1 – normative = SI normative units, standard and commonly used multiples level 2 – normative equivalent = SI normative equivalent units (UK, US, etc.) and commonly used multiples level 3 – informative = Units of count and other units of measure (invariably with no comprehensive conversion factor to SI) The code elements for units of packaging are specified in UN/ECE Recommendation No. 21 (Codes for types of cargo, packages and packaging materials). See note at the end of this Annex). ST Name Level/ Representation symbol Conversion factor to SI Common Description Category Code D 15 °C calorie 2 cal₁₅ 4,185 5 J A1 + 8-part cloud cover 3.9 A59 A unit of count defining the number of eighth-parts as a measure of the celestial dome cloud coverage. | access line 3.5 AL A unit of count defining the number of telephone access lines. acre 2 acre 4 046,856 m² ACR + active unit 3.9 E25 A unit of count defining the number of active units within a substance. + activity 3.2 ACT A unit of count defining the number of activities (activity: a unit of work or action). X actual ton 3.1 26 | additional minute 3.5 AH A unit of time defining the number of minutes in addition to the referenced minutes. | air dry metric ton 3.1 MD A unit of count defining the number of metric tons of a product, disregarding the water content of the product. -

Chapter 1: Data Storage
Chapter 1: Data Storage 1.1 Bits and Their Storage 1.2 Main Memory 1.3 Mass Storage 1.4 Representing Information as Bit Patterns 1.5 The Binary System 1.6 Storing Integers 1.7 Storing Fractions 1.8 Data Compression 1.9 Communication Errors 1 Computer == 0 and 1 ? Hmm…every movie says so…. Chapter 2 2 Why I can’t see any 0 and 1 when opening up a computer?? Chapter 2 3 What’s really in the computer With the help of an oscilloscope (示波器) Chapter 2 4 HIGH Bits LOW Bit Binary Digit The basic unit of information in a computer A symbol whose meaning depends on the application at hand. Numeric value (1 or 0) Boolean value (true or false) Voltage (high or low) For TTL, high=5V, low=0V 5 More bits? kilobit (kbit) 103 210 megabit (Mbit) 106 220 gigabit (Gbit) 109 230 terabit (Tbit) 1012 240 petabit (Pbit) 1015 250 exabit (Ebit) 1018 260 zettabit (Zbit) 1021 270 6 Bit Patterns All data stored in a computer are represented by patterns of bits: Numbers Text characters Images Sound Anything else… 7 Now you know what’s a ‘bit’, and then? How to ‘compute’ bits? How to ‘implement’ it ? How to ‘store’ bit in a computer? Chapter 2 8 How to do computation on Bits? Chapter 2 9 Boolean Operations Boolean operation any operation that manipulates one or more true/false values (e.g. 0=true, 1=false) Can be used to operate on bits Specific operations AND OR XOR NOT 10 AND, OR, XOR 11 Implement the Boolean operation on a computer Chapter 2 12 Gates Gates devices that produce the outputs of Boolean operations when given -

ESPPADOM Delivery Date: 30/03/2012 Comité Technique Statut: Travail Version: 00.02
EDISANTE ESPPADOM_Delivery Date: 30/03/2012 Comité Technique Statut: Travail Version: 00.02 ESPPADOM_Delivery Modèle des données structurées Date: 30/03/2012 Statut: Travail Version: 00.02 EDISANTE ESPPADOM_Delivery Date: 30/03/2012 Comité Technique Statut: Travail Version: 00.02 ESPPADOM_Delivery: Modèle des données structurées Mention légale Clause de cession de droit de reproduction. L'auteur de ce document est : EDISANTE Comité Technique Le présent document est la propriété de l'auteur. Par la présente, l'auteur cède à titre gracieux à l’utilisateur du présent document, un droit de reproduction non exclusif dans le seul but de l’intégrer dans une application informatique. Cette cession est valable sur supports papier, magnétique, optique, électronique, numérique, et plus généralement sur tout autre support de fixation connu à la date de la reproduction, et permettant à l’utilisateur de créer l’application visée au paragraphe précédent. Cette cession est consentie pour l’ensemble du territoire national, et pour la durée de protection prévue par le code de la propriété intellectuelle. L’utilisateur fera son affaire personnelle de tout dommage qu’il causerait à un tiers et qui trouverait son origine dans une violation des termes de la présente cession. Toute atteinte aux droits d’auteur constitue un délit et est passible des sanctions indiquées aux articles L.335-1 et suivants du Code de propriété intellectuelle. EDISANTE ESPPADOM_Delivery Date: 30/03/2012 Comité Technique Statut: Travail Version: 00.02 Table des matières Documentation