Aadhaar – an Indian Megatrend
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

FATCA-CRS-Faqs.Pdf
FATCA/CRS FAQs:- 1. What is FATCA? The Foreign Account Tax Compliance Act (FATCA) is a United States federal law that requires United States persons, including US persons who live outside the United States, to report their financial accounts held outside of the United States, and requires foreign financial institutions to report to the Internal Revenue Service (IRS) about their U.S. clients. Government of India (GOI) has signed a Model 1 Inter-Governmental Agreement (IGA) with US on July 9, 2015 which necessitates financial institutions in India to comply with FATCA. 2. What is CRS? CRS is known as Common Reporting Standards. It is an information standard for the automatic exchange of information (AEoI), developed in the context of the Organisation for Economic Co-operation and Development (OECD). The Government of India has also joined the Multilateral Competent Authority Agreement (MCAA) on June 3, 2015 and financial institutions in india to comply with CRS. 3. Why do we need to ask the FATCA/CRS declaration from the customer? Government of India (GOI) has signed a Model 1 Inter-Governmental Agreement (IGA) with US on July 9, 2015. The IGA provides that the Indian FIs will provide the necessary information to Indian tax authority i.e. Central Board of Direct Taxes (CBDT), which will then be transmitted to USA automatically in case of FATCA. The Government of India has also joined the Multilateral Competent Authority Agreement (MCAA) on June 3, 2015, for exchanging information with respective tax authorities from 63 partner jurisdictions which are signatories to MCAA. To enable this, CBDT has issued a notification to all financial institutions in India to comply with the CRS and FATCA regulations. -

Trend Micro Data Protection Lists (Release 3.0)
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes, and the latest version of the applicable user documentation, which are available from the Trend Micro Web site at: http://docs.trendmicro.com/ Trend Micro, the Trend Micro t-ball logo, and OfficeScan are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2014. Trend Micro Incorporated. All rights reserved. Document Part No. LPEM55806/121205 Release Date: September 2014 Document Version No.: 3.0 Protected by U.S. Patent No.: 5,623,600; 5,889,943; 5,951,698; 6,119,165 This document contains information common to all Trend Micro products that support data protection features. Detailed information about how to use specific features within your product may be available in the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base at the Trend Micro website. Read through the documentation before installing or using the product. Trend Micro is always seeking to improve its documentation. Your feedback is always welcome. Please evaluate this documentation on the following site: http://www.trendmicro.com/download/documentation/rating.asp Table of Contents Chapter 1: Data Loss Prevention - Predefined Data Identifiers and Templates Predefined Expressions ................................................................................ -

ISSN: 2320-5407 Int. J. Adv. Res. 5(9), 958-965
ISSN: 2320-5407 Int. J. Adv. Res. 5(9), 958-965 Journal Homepage: - www.journalijar.com Article DOI: 10.21474/IJAR01/5409 DOI URL: http://dx.doi.org/10.21474/IJAR01/5409 RESEARCH ARTICLE NATIONAL IDENTIFICATION SYSTEM IN THE COUNTRIES AROUND THE GLOBE: AN OUTSIDE REVIEW FROM ETHIOPIAN PERSPECTIVE. Dr. Gavendra Singh1, Mr Ashenafi Chalchissa2 and Mulugeta Kejela3. 1. Assistant Professor, Deptt. of Software Engineering, College of Computing and Informatics, Haramaya University, 138, Dire Dawa, Ethiopia. 2. HOD ,Deptt. of Software Engineering, College of Computing and Informatics, Haramaya University, 138, Dire Dawa, Ethiopia. 3. Deptt. of Software Engineering, College of Computing and Informatics, Haramaya University, 138, Dire Dawa, Ethiopia. …………………………………………………………………………………………………….... Manuscript Info Abstract ……………………. ……………………………………………………………… Manuscript History A national identification numberor national identity number is used by the governments of many countries as a means of tracking Received: 12 July 2017 their citizens, permanent residents, and temporary residents for the Final Accepted: 14 August 2017 purposes ofvarious e-governmentally-related functions. Published: September 2017 The ways in which such a system is implemented vary among Key words:- countries, but in most cases citizens are issued an identification e-ID, e-Government, Capitals, System, number upon reaching legal age, or when they are born.Identification is Identification, internet, face-to-face routinely used to help facilitate commercial and government transaction transactions [1].Such as taking out a loan or applying for government benefits. While individuals can use traditional forms of identification in face-to-face transactions, these forms of identification are less useful for conducting business on the Internet. Individuals can use an National Identification System to authenticate to online services, securely communicate online, purchase goods and services, and create legally-binding electronic signatures, such as to sign a contract. -
Trend Micro Data Protection Lists (Release 2.0)
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes, and the latest version of the applicable user documentation, which are available from the Trend Micro Web site at: http://docs.trendmicro.com/ Trend Micro, the Trend Micro t-ball logo, and OfficeScan are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2012. Trend Micro Incorporated. All rights reserved. Document Part No. LPEM55806/121205 Release Date: September 2014 Document Version No.: 2.0 Protected by U.S. Patent No.: 5,623,600; 5,889,943; 5,951,698; 6,119,165 This document contains information common to all Trend Micro products that support data protection features. Detailed information about how to use specific features within your product may be available in the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base at the Trend Micro website. Read through the documentation before installing or using the product. Trend Micro is always seeking to improve its documentation. Your feedback is always welcome. Please evaluate this documentation on the following site: http://www.trendmicro.com/download/documentation/rating.asp Table of Contents Chapter 1: Data Loss Prevention - Predefined Data Identifiers and Templates Predefined Expressions ................................................................................ -
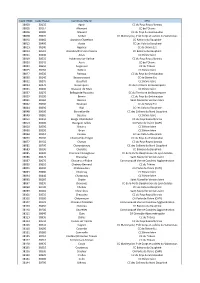
Code INSEE Code Postal Commune Mairie EPCI 38003 38150 Agnin
Code INSEE Code Postal Commune Mairie EPCI 38003 38150 Agnin CC du Pays Roussillonnais 38005 38114 Allemont CC de l'Oisans 38006 38580 Allevard CC du Pays du Grésivaudan 38008 38970 Ambel CC Matheysine, P de Corps et vallées du Valbonnais 38010 38460 Annoisin-Chatelans CC Balcons du Dauphiné 38012 38490 Aoste CC Les Vals du Dauphiné 38013 38140 Apprieu CC de Bièvre Est 38014 38510 Arandon/Arandon-Passins CC Balcons du Dauphiné 38015 38440 Artas CC Bièvre Isère 38019 38550 Auberives-sur-Varèze CC du Pays Roussillonnais 38020 38142 Auris CC de l'Oisans 38023 38650 Avignonet CC du Trièves 38025 38260 Balbins CC Bièvre Isère 38027 38530 Barraux CC du Pays du Grésivaudan 38030 38140 Beaucroissant CC de Bièvre Est 38032 38270 Beaufort CC Bièvre Isère 38034 38270 Beaurepaire CC du Territoire de Beaurepaire 38035 38440 Beauvoir-de-Marc CC Bièvre Isère 38037 38270 Bellegarde-Poussieu CC du Territoire de Beaurepaire 38039 38190 Bernin CC du Pays du Grésivaudan 38041 38160 Bessins Saint Marcellin Vercors Isère 38042 38690 Bevenais CC de Bièvre Est 38044 38690 Biol CC Les Vals du Dauphiné 38048 38090 Bonnefamille CC des Collines du Nord Dauphiné 38049 38260 Bossieu CC Bièvre Isère 38051 38150 Bouge-Chambalud CC du Pays Roussillonnais 38053 38300 Bourgoin-Jallieu CA Porte de l'Isère (CAPI) 38058 38590 Brezins CC Bièvre Isère 38060 38590 Brion CC Bièvre Isère 38064 38110 Cessieu CC Les Vals du Dauphiné 38070 38190 Champ-Près-Froges CC du Pays du Grésivaudan 38072 38150 Chanas CC du Pays Roussillonnais 38081 38790 Charantonnay CC des Collines du Nord -

Developer Guide Table of Contents
SAP Data Quality Management SDK Document Version: 4.2 Support Package 3 (14.2.3.0) - 2014-09-05 Developer Guide Table of Contents 1 Data Quality Management SDK overview............................................10 1.1 Installing Data Quality Management SDK..............................................10 1.1.1 Upgrading.............................................................11 1.1.2 Installing the SDK on Windows...............................................11 1.1.3 Installing the SDK on Unix..................................................11 2 Directory data................................................................13 2.1 Directory listing and update schedule................................................ 13 2.2 U.S. directory expiration..........................................................14 2.2.1 U.S. National and Auxiliary files..............................................15 2.3 Where to copy directories.........................................................15 2.4 To install and set up SAP Download Manager...........................................16 2.5 To download directory files........................................................16 2.6 Extracting directory files..........................................................16 3 Samples.....................................................................18 3.1 Sample program files............................................................18 3.2 Building samples...............................................................18 3.3 Running samples...............................................................19 -

Forcepoint DLP Predefined Policies and Classifiers
Forcepoint DLP Predefined Policies and Classifiers Predefined Policies and Classifiers | Forcepoint DLP | 8.7.1 For your convenience, Forcepoint DLP includes hundreds of predefined policies and content classifiers. ● Predefined policies help administrators quickly and easily define what type of content is considered a security breach at their organization. While choosing a policy or policy category, some items are set “off” by default. They can be activated individually in the Forcepoint Security Manager. ■ Data Loss Prevention policies, page 2 ■ Discovery policies, page 116 ● Predefined classifiers can be used to detect events and threats involving secured data. This article provides a list of all the predefined content classifiers that Forcepoint DLP provides for detecting events and threats involving secured data. This includes: ■ File-type classifiers ■ Script classifiers ■ Dictionaries ■ Pattern classifiers The predefined policies and classifiers are constantly being updated and improved. See Updating Predefined Policies and Classifiers for instructions on keeping policies and classifiers current. © 2020 Forcepoint LLC Data Loss Prevention policies Predefined Policies and Classifiers | Forcepoint DLP | 8.7.1 Use the predefined data loss prevention policies to detect sensitive content, compliance violations, and data theft. For acceptable use policies, see: ● Acceptable Use, page 3 The content protection policies fall into several categories: ● Company Confidential and Intellectual Property (IP), page 4 ● Credit Cards, page 9 ● Financial -

Micro Focus IDOL PII Package 12.8 Technical Note Add Your Feedback to the Email and Click Send
IDOL PII Package Software Version 12.8 Technical Note Document Release Date: February 2021 Software Release Date: February 2021 Technical Note Legal notices Copyright notice © Copyright 2020 Micro Focus or one of its affiliates. The only warranties for products and services of Micro Focus and its affiliates and licensors (“Micro Focus”) are as may be set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Micro Focus shall not be liable for technical or editorial errors or omissions contained herein. The information contained herein is subject to change without notice. Documentation updates The title page of this document contains the following identifying information: l Software Version number, which indicates the software version. l Document Release Date, which changes each time the document is updated. l Software Release Date, which indicates the release date of this version of the software. To check for updated documentation, visit https://www.microfocus.com/support-and-services/documentation/. Support Visit the MySupport portal to access contact information and details about the products, services, and support that Micro Focus offers. This portal also provides customer self-solve capabilities. It gives you a fast and efficient way to access interactive technical support tools needed to manage your business. As a valued support customer, you can benefit by using the MySupport portal to: l Search for knowledge documents of interest l Access product documentation l View software vulnerability alerts l Enter into discussions with other software customers l Download software patches l Manage software licenses, downloads, and support contracts l Submit and track service requests l Contact customer support l View information about all services that Support offers Many areas of the portal require you to sign in. -

Peoplesoft 8.8 Application Fundamentals for HRMS Peoplebook
PeopleSoft 8.8 Application Fundamentals for HRMS PeopleBook December 2002 PeopleSoft 8.8 Application Fundamentals for HRMS PeopleBook SKU HRMS88HAF-B 1202 PeopleBooks Contributors: Teams from PeopleSoft Product Documentation and Development. Copyright 1988-2002 PeopleSoft, Inc. All rights reserved. Printed in the United States. All material contained in this documentation is proprietary and confidential to PeopleSoft, Inc. ("PeopleSoft"), protected by copyright laws and subject to the nondisclosure provisions of the applicable PeopleSoft agreement. No part of this documentation may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, including, but not limited to, electronic, graphic, mechanical, photocopying, recording, or otherwise without the prior written permission of PeopleSoft. This documentation is subject to change without notice, and PeopleSoft does not warrant that the material contained in this documentation is free of errors. Any errors found in this document should be reported to PeopleSoft in writing. The copyrighted software that accompanies this document is licensed for use only in strict accordance with the applicable license agreement which should be read carefully as it governs the terms of use of the software and this document, including the disclosure thereof. PeopleSoft, PeopleTools, PS/nVision, PeopleCode, PeopleBooks, PeopleTalk, and Vantive are registered trademarks, and Pure Internet Architecture, Intelligent Context Manager, and The Real-Time Enterprise are trademarks of PeopleSoft, Inc. All other company and product names may be trademarks of their respective owners. The information contained herein is subject to change without notice. Open Source Disclosure This product includes software developed by the Apache Software Foundation (http://www.apache.org/). -

IDOL PII Package 12.6 Technical Note
IDOL PII Package Software Version 12.6 Technical Note Document Release Date: June 2020 Software Release Date: June 2020 Technical Note Legal notices Copyright notice © Copyright 2020 Micro Focus or one of its affiliates. The only warranties for products and services of Micro Focus and its affiliates and licensors (“Micro Focus”) are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Micro Focus shall not be liable for technical or editorial errors or omissions contained herein. The information contained herein is subject to change without notice. Documentation updates The title page of this document contains the following identifying information: l Software Version number, which indicates the software version. l Document Release Date, which changes each time the document is updated. l Software Release Date, which indicates the release date of this version of the software. To check for updated documentation, visit https://www.microfocus.com/support-and-services/documentation/. Support Visit the MySupport portal to access contact information and details about the products, services, and support that Micro Focus offers. This portal also provides customer self-solve capabilities. It gives you a fast and efficient way to access interactive technical support tools needed to manage your business. As a valued support customer, you can benefit by using the MySupport portal to: l Search for knowledge documents of interest l Access product documentation l View software vulnerability alerts l Enter into discussions with other software customers l Download software patches l Manage software licenses, downloads, and support contracts l Submit and track service requests l Contact customer support l View information about all services that Support offers Many areas of the portal require you to sign in. -

Avant-Propos
AVANT-PROPOS L'information statistique sur les questions économiques et sociales est indispensable à tous ceux qui s'intéressent à la vie de la région. Les Tableaux Économiques de Haute-Normandie (TEHN) vous proposent les derniers chiffres disponibles. Ils offrent une image globale de la région et de ses départements. Une structure identique pour chacun des vingt domaines présentés facilite l’accès aux données, définitions et références bibliographiques. Document de base pour une bonne connaissance de la région, TEHN 2008-2009 est construit à l’image des autres tableaux économiques régionaux réalisés par chaque direction régionale de l’Insee. L’utilisateur pourra ainsi trouver, dans chaque ouvrage régional, un grand nombre de tableaux semblables permettant des comparaisons utiles. Le lecteur intéressé trouvera également sur le site www.insee.fr et sur sa déclinaison régionale www.insee.fr/haute-normandie de très nombreuses autres informations, tableaux et analyses. L'équipe de rédaction remercie les organismes statistiques qui ont contribué à la réalisation de ce document, et souhaite que cette édition 2008-2009 réponde aux attentes des utilisateurs. S O M M A I R E ESPACE - POPULATION 1 - ESPACE RÉGIONAL 1.1 - Climat, relief et infrastructures . 8 1.2 - Circonscriptions administratives . 12 1.3 - Villes . 14 1.4 - Espaces urbains, espaces ruraux. 16 1.5 - La Haute-Normandie et la France . 18 1.6 - La Haute-Normandie et l’Europe . 20 1.7 - Territoires . 22 2 - ENVIRONNEMENT 2.1 - Milieu naturel . 26 2.2 - Déchets, air et eau . 28 2.3 - Risques naturels et technologiques. 30 3 - POPULATION 3.1 - Évolution de la population . -

Forcepoint DLP Predefined Policies and Classifiers
Forcepoint DLP Predefined Policies and Classifiers Predefined Policies and Classifiers | Forcepoint DLP | 8.7.x For your convenience, Forcepoint DLP includes hundreds of predefined policies and content classifiers. ● Predefined policies help administrators quickly and easily define what type of content is considered a security breach at their organization. While choosing a policy or policy category, some items are set “off” by default. They can be activated individually in the Forcepoint Security Manager. ■ Data Loss Prevention policies, page 2 ■ Discovery policies, page 115 ● Predefined classifiers can be used to detect events and threats involving secured data. This article provides a list of all the predefined content classifiers that Forcepoint DLP provides for detecting events and threats involving secured data. This includes: ■ File-type classifiers ■ Script classifiers ■ Dictionaries ■ Pattern classifiers The predefined policies and classifiers are constantly being updated and improved. See Updating Predefined Policies and Classifiers for instructions on keeping policies and classifiers current. © 2019 Forcepoint LLC Data Loss Prevention policies Predefined Policies and Classifiers | Forcepoint DLP | 8.7.x Use the predefined data loss prevention policies to detect sensitive content, compliance violations, and data theft. For acceptable use policies, see: ● Acceptable Use, page 3 The content protection policies fall into several categories: ● Company Confidential and Intellectual Property (IP), page 4 ● Credit Cards, page 9 ● Financial