ISSN: 2320-5407 Int. J. Adv. Res. 5(9), 958-965
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
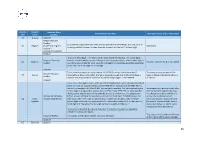
Country Code Country Name National Client Identifier Format
Country Country National client Format of the identifier Potential source of the information code name identifier AT Austria CONCAT Belgian National Number 11 numerical digits where the first 6 are the date of birth (YYMMDD), the next 3 are an BE Belgium (Numéro de registre National ID ordering number (uneven for men, even for women) and the last 2 a check digit. national - Rijksregisternummer) CONCAT It consists of 10 digits. The first 6 are the date of birth (YYMMDD). The next 3 digits Bulgarian Personal have information about the area in Bulgaria and the order of birth, and the ninth digit is BG Bulgaria Passport, National ID, Driving Licence Number even for a boy and odd for a girl. Seventh and eighth are randomly generated according to the city. The tenth digit is a check digit. CONCAT The number for passports issued before 13/12/2010 consists of the character 'E' The passport is issued by the Civil National Passport CY Cyprus followed by 6 digits i.e E123456. Biometric passports issued after 13/12/2010 have a Registry Department of the Ministry Number number that starts with the character 'K', followed by 8 digits. i.e K12345678 of Interior. CONCAT It is a nine or ten-digit number in the format of YYXXDD/SSSC, where XX=MM (month of birth) for male, i.e. numbers 01-12, and XX=MM+50 (or exceptionally XX=MM+70) for female, i.e. numbers 51-62 (or 71-82). For example, a number 785723 representing the It is assigned to a person shortly after first six digits is assigned to a woman born on 23rd of July 1978. -

FATCA-CRS-Faqs.Pdf
FATCA/CRS FAQs:- 1. What is FATCA? The Foreign Account Tax Compliance Act (FATCA) is a United States federal law that requires United States persons, including US persons who live outside the United States, to report their financial accounts held outside of the United States, and requires foreign financial institutions to report to the Internal Revenue Service (IRS) about their U.S. clients. Government of India (GOI) has signed a Model 1 Inter-Governmental Agreement (IGA) with US on July 9, 2015 which necessitates financial institutions in India to comply with FATCA. 2. What is CRS? CRS is known as Common Reporting Standards. It is an information standard for the automatic exchange of information (AEoI), developed in the context of the Organisation for Economic Co-operation and Development (OECD). The Government of India has also joined the Multilateral Competent Authority Agreement (MCAA) on June 3, 2015 and financial institutions in india to comply with CRS. 3. Why do we need to ask the FATCA/CRS declaration from the customer? Government of India (GOI) has signed a Model 1 Inter-Governmental Agreement (IGA) with US on July 9, 2015. The IGA provides that the Indian FIs will provide the necessary information to Indian tax authority i.e. Central Board of Direct Taxes (CBDT), which will then be transmitted to USA automatically in case of FATCA. The Government of India has also joined the Multilateral Competent Authority Agreement (MCAA) on June 3, 2015, for exchanging information with respective tax authorities from 63 partner jurisdictions which are signatories to MCAA. To enable this, CBDT has issued a notification to all financial institutions in India to comply with the CRS and FATCA regulations. -

Tax ID Table
Country Flag Country Name Tax Identification Number (TIN) type TIN structure Where to find your TIN For individuals, the TIN consists of the letter "E" or "F" followed by 6 numbers and 1 control letter. TINs for Número d’Identificació residents start with the letter "F." TINs for non-residents AD Andorra Administrativa (NIA) start with the letter "E". AI Anguilla N/A All individuals and businesses receive a TIN (a 6-digit number) when they register with the Inland Revenue Department. See http://forms.gov. AG Antigua & Barbuda TIN A 6-digit number. ag/ird/pit/F50_Monthly_Guide_Individuals2006.pdf CUIT. Issued by the AFIP to any individual that initiates any economic AR Argentina activity. The CUIT consists of 11 digits. The TIN is generated by an automated system after registering relevant AW Aruba TIN An 8-digit number. data pertaining to a tax payer. Individuals generally use a TFN to interact with the Australian Tax Office for various purposes and, therefore, most individuals have a TFN. This includes submitting income tax returns, reporting information to the ATO, obtaining The Tax File Number (TFN) is an eight- or nine-digit government benefits and obtaining an Australian Business Number (ABN) AU Australia Tax File Number (TFN) number compiled using a check digit algorithm. in order to maintain a business. TINs are only issued to individuals who are liable for tax. They are issued by the Local Tax Office. When a person changes their residence area, the TIN AT Austria TIN Consists of 9 digits changes as well. TINs are only issued to people who engage in entrepreneurial activities and AZ Azerbaijan TIN TIN is a ten-digit code. -

NSX Data Security Reference Guide
NSX Data Security Reference Guide Update 1 Modi®ed on 30 JUN 2016 VMware NSX Data Center for vSphere 6.2 NSX Data Security Reference Guide You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation, submit your feedback to [email protected] VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com Copyright © 2010–2017 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents NSX Data Security Reference Guide 8 1 Data Security Regulations 9 Arizona SB-1338 11 ABA Routing Numbers 11 Australia Bank Account Numbers 12 Australia Business and Company Numbers 12 Australia Medicare Card Numbers 12 Australia Tax File Numbers 13 California AB-1298 13 California SB-1386 14 Canada Social Insurance Numbers 14 Canada Drivers License Numbers 14 Colorado HB-1119 15 Connecticut SB-650 15 Credit Card Numbers 16 Custom Account Numbers 16 EU Debit Card Numbers 16 FERPA (Family Educational Rights and Privacy Act) 16 Florida HB-481 16 France IBAN Numbers 17 France National Identification Numbers Policy 17 Georgia SB-230 Policy 17 Germany BIC Numbers Policy 17 Germany Driving License Numbers Policy 18 Germany IBAN Numbers Policy 18 Germany National Identification Numbers Policy 18 Germany VAT Numbers Policy 18 Hawaii SB-2290 Policy 18 HIPAA (Healthcare Insurance Portability and Accountability Act) Policy 19 Idaho SB-1374 Policy 19 Illinois SB-1633 19 Indiana HB-1101 Policy 20 Italy Driving License Numbers Policy 20 Italy IBAN Numbers Policy. 20 Italy National Identification Numbers Policy 21 Kansas SB-196 Policy 21 Louisiana SB-205 Policy 21 VMware, Inc. -

Trend Micro Data Protection Lists (Release 3.0)
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes, and the latest version of the applicable user documentation, which are available from the Trend Micro Web site at: http://docs.trendmicro.com/ Trend Micro, the Trend Micro t-ball logo, and OfficeScan are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2014. Trend Micro Incorporated. All rights reserved. Document Part No. LPEM55806/121205 Release Date: September 2014 Document Version No.: 3.0 Protected by U.S. Patent No.: 5,623,600; 5,889,943; 5,951,698; 6,119,165 This document contains information common to all Trend Micro products that support data protection features. Detailed information about how to use specific features within your product may be available in the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base at the Trend Micro website. Read through the documentation before installing or using the product. Trend Micro is always seeking to improve its documentation. Your feedback is always welcome. Please evaluate this documentation on the following site: http://www.trendmicro.com/download/documentation/rating.asp Table of Contents Chapter 1: Data Loss Prevention - Predefined Data Identifiers and Templates Predefined Expressions ................................................................................ -

OECD REFERENCE GUIDE on SOURCES of INFORMATION from ABROAD Update of 26Th January 2006
OECD REFERENCE GUIDE ON SOURCES OF INFORMATION FROM ABROAD Update of 26th January 2006 R2+>R3 @26 January 2006 TABLE OF CONTENTS OECD REFERENCE GUIDE ON SOURCES OF INFORMATION FROM ABROAD.............................. 1 REFERENCE GUIDE ON SOURCES OF INFORMATION FROM ABROAD ......................................... 3 INTRODUCTION....................................................................................................................................... 3 AUSTRALIA .............................................................................................................................................. 4 AUSTRIA.................................................................................................................................................. 14 BELGIUM................................................................................................................................................. 23 CANADA.................................................................................................................................................. 34 CZECH REPUBLIC ................................................................................................................................. 65 DENMARK............................................................................................................................................... 70 FINLAND ................................................................................................................................................. 78 FRANCE .................................................................................................................................................. -

Tax Administration / Institutional Strengthening 10April 2011 Contents
Tax Administration / Institutional Strengthening 10April 2011 Contents Introduction Tax admInIsTraTIon / InsTITuTIonal sTrengThenIng • Transparency and Ethic as a Condition to Strengthen and Improve Institutional Effectiveness / Linda Lizzotte MacPherson. -- In: 44th CIAT General Assembly, Montevideo, Uruguay, 2010. • Management Tool and Relevant Contextual Aspects for Strengthening the Tax Administration / Andrew Reed. -- In: CIAT Technical Conference. Naples, Italy, 2009. • Strategies and Instruments for Improving Management in the Tax Administrations / Marcelo Lettieri Siqueira. -- In: 43th CIAT General Assembly, Santo Domingo, Dominican Republic, 2009. • Strategic Planning as Factor Contributing to the Improvement of Institutional Capacity/Néstor Díaz Saavedra. -- In: CIAT Technical Conference. Naples, Italy, 2009. • Strategic Planning as Factor Contributing to the Improvement of the Institutional Capacity / Mario Visco. -- In: CIAT Technical Conference. Naples, Italy, 2009. Introduction CIaT Tax Thematic series In an effort to provide an ever better and highly qualified tax information service to its member countries, the Inter-American Center of Tax Administrations hereby presents the tenth issue of the CIAT Tax Thematic Series. The purpose of this series is to disseminate relevant information on specific taxation issues to support the research and study work carried out by the tax administrations of the CIAT member countries. The bibliographical material of this tenth issue is devoted to “Tax administration/ Institutional strengthening”. The material gathered includes studies and papers prepared by technical officials for presentation either at the general assemblies or technical conferences, essays, research scholarships and articles published in the tax administration review, among others. To speed up the search and recovery of information a general table of contents and index is presented for each paper. -

Tax File Number – Application Or Enquiry for Individuals Living Outside Australia
Instructions and form for individuals living outside Australia Tax file number – application or enquiry for individuals living outside Australia NAT 2628‑07.2016 inTroducTion YOUR TAX FILE NUMBER (TFN) AND WHEN WILL I RECEIVE MY TFN? KEEPING IT SAFE You should receive your TFN within 28 days after we receive A TFN is a unique number we issue to individuals. It is an your completed application and required documents. We important part of your tax and superannuation records, as appreciate your patience during the processing period – do well as your identity. It is also an important part of locating not lodge another application during this time, and allow for and keeping track of your superannuation savings. In the possible delays with international mail. wrong hands, it could be used to commit fraud, so keep it safe.make sureyouprotectyouridentitybykeepingallyour HOW DO I APPLY? personal detailssecure,includingyourTfn. We only issue one TFN to you during your lifetime – even if Foreign residents you changejobs,changeyourname,ormove. visitato.gov.au/residency to check your Australian residency status for tax purposes. You can find out more about how to protect your TFN You can apply for a TFN using this form, if you are a foreign and avoididentitycrimeatato.gov.au/identitycrime resident for tax purposes and: n you receive rental income from an Australian property WHEN TO USE THIS FORM n you receive income from Australian business interests You can use this form if you: n your spouse is n have never had a TFN – an Australian resident, and n have a TFN, but cannot find it on any of your tax papers. -

Forcepoint DLP Predefined Policies and Classifiers
Forcepoint DLP Predefined Policies and Classifiers Predefined Policies and Classifiers | Forcepoint DLP | v8.5.x For your convenience, Forcepoint DLP includes hundreds of predefined policies and content classifiers. ● Predefined policies help administrators quickly and easily define what type of content is considered a security breach at their organization. While choosing a policy or policy category, some items are set “off” by default. They can be activated individually in the Forcepoint Security Manager. ■ Data Loss Prevention policies, page 2 ■ Discovery policies, page 108 ● Predefined classifiers can be used to detect events and threats involving secured data. This article provides a list of all the predefined content classifiers that Forcepoint DLP provides for detecting events and threats involving secured data. This includes: ■ File-type classifiers ■ Script classifiers ■ Dictionaries ■ Pattern classifiers The predefined policies and classifiers are constantly being updated and improved. See Updating Predefined Policies and Classifiers for instructions on keeping policies and classifiers current. © 2017 Forcepoint LLC Data Loss Prevention policies Predefined Policies and Classifiers | Forcepoint DLP | v8.5.x Use the predefined data loss prevention policies to detect sensitive content, compliance violations, and data theft. For acceptable use policies, see: ● Acceptable Use, page 3 The content protection policies fall into several categories: ● Company Confidential and Intellectual Property (IP), page 4 ● Credit Cards, page 9 ● Financial -

Common Reporting Standard
COMMON REPORTING STANDARD TAX IDENTIFICATION NUMBERS LEAFLET Version updated as of October 31th, 2019 Disclaimer: The present informative document, subject to modification, is communicated for information purposes only and has no contractual value. This document is defined based on the information provided by the OECD portal. It contains information that it is the sole responsibility of each country and is (i) of a general nature only and not intended to address the specific circumstances of any particular individual or entity, (ii) not necessarily comprehensive, complete, accurate or up to date,(iii) sometimes linked to external sites over which SG Group has no control and for which SG Group assumes no responsibility and (iv) not professional or legal advice. If you need specific advice, you should always consult a professional tax advisor. TAX IDENTIFICATION NUMBERS This document provides an overview of domestic rules in the countries listed below governing the issuance, structure, use and validity of Tax Identification Numbers (“TIN”) or their functional equivalents. It is split into two sections: Countries that have already published the information on the OECD portal and can 1 be accessed by clicking on the name of the country below Cook Andorra Hungary Malaysia Saudi Arabia Islands Argentina Costa Rica Iceland Malta Seychelles Marshall Aruba Croatia India Islands Singapore Australia Curacao Indonesia Mauritius Slovak Republic Ireland Austria Mexico Cyprus Slovenia Isle of Man Azerbaijan Czech Montserrat Republic South Africa Bahrain -

Sharing Data: Where to Start
Sharing Data: Where To Start 100 75 50 25 0 2002 2003 2004 2005 2006 2007 An Emerging Approach To Migration Data Management Written and edited by Claus Folden, Marina Manke, and Thomas Mortensen Opinions expressed in this document are those of the authors and do not necessarily reflect the views of IOM. IOM is committed to the principle that humane and orderly migration benefits migrants and society. As an intergovernmental body, IOM acts with its partners in the international community to: assist in meeting the operational challenges of migration; advance understanding of migration issues; encourage social and economic development through migration; and uphold the human dignity and well-being of migrants. Publisher: Technical Cooperation Centre for Europe and Central Asia International Organization for Migration Nibelungengasse 13/4 1010 Vienna Austria Tel: +43 1 585 33 22 12 Fax: +43 1 585 33 22 30 Email: [email protected] Internet: http://www.tcc.iom.int http://www.dsm-migration.net ISBN 978 92 9068 390 2 Sharing Data – Where to Start: An Emerging Approach to Migration Data Management ISBN 978 92 9068 391 9 Sharing Data – Where to Start: An Emerging Approach to Migration Data Management (Russian version) © 2007 International Organization for Migration (IOM) All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise without the prior written permission of the publisher. Factual information in this book has been verified until December 2006. Cover design: Avocado Design Text editor: Caroline Mackenzie Text layout: Hubert Weitzer Sharing Data - Where to Start AN EMERGING APPROACH TO MIGRATION DATA MANAGEMENT Written and edited by Claus Folden, Marina Manke and Thomas Mortensen AACKNOWLEDGEMENTS This book is dedicated to those who unselfishly seek to let facts improve the lives of migrants. -

Digital Identities Advancing Digital Societies in Asia Pacific
Digital identities Advancing digital societies in Asia Pacific Copyright © 2018 GSM Association GSMA Intelligence The GSMA represents the interests of mobile GSMA Intelligence is the definitive source of global operators worldwide, uniting nearly 800 operators mobile operator data, analysis and forecasts, and with more than 300 companies in the broader publisher of authoritative industry reports and mobile ecosystem, including handset and device research. Our data covers every operator group, makers, software companies, equipment providers network and MVNO in every country worldwide and internet companies, as well as organisations – from Afghanistan to Zimbabwe. It is the most in adjacent industry sectors. The GSMA also accurate and complete set of industry metrics produces industry-leading events such as Mobile available, comprising tens of millions of individual World Congress, Mobile World Congress Shanghai, data points, updated daily. Mobile World Congress Americas and the Mobile GSMA Intelligence is relied on by leading 360 Series of conferences. operators, vendors, regulators, financial For more information, please visit the GSMA institutions and third-party industry players, to corporate website at www.gsma.com support strategic decision making and long- term investment planning. The data is used as an Follow the GSMA on Twitter: @GSMA industry reference point and is frequently cited by the media and by the industry itself. Our team of analysts and experts produce regular thought-leading research reports across a range of industry topics. www.gsmaintelligence.com [email protected] This report was authored by TRPC is a research consultancy with over 25 James Robinson, Senior Analyst years’ experience in the telecommunications and Barbara Arese Lucini, Senior Analyst information technology industries in the Asia-Pacific Jeanette Whyte, Senior Policy Manager – APAC region.