IDOL PII Package 12.6 Technical Note
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Understanding Capture and Validate KYC Processes: Global Experiences, Challenges and Learnings
Understanding Capture and Validate KYC Processes: Global Experiences, Challenges and Learnings May 2019 Copyright © 2019 GSM Association Understanding Capture and Validate KYC Processes: Global Experiences, Challenges and Learnings v Digital Identity The GSMA represents the interests of mobile operators The GSMA Digital Identity Programme is uniquely worldwide, uniting more than 750 operators with over positioned to play a key role in advocating and raising 350 companies in the broader mobile ecosystem, awareness of the opportunity of mobile-enabled digital including handset and device makers, software companies, identity and life-enhancing services. Our programme works equipment providers and internet companies, as well as with mobile operators, governments and the development organisations in adjacent industry sectors. The GSMA also community to demonstrate the opportunities, address the produces the industry-leading MWC events held annually in barriers and highlight the value of mobile as an enabler of Barcelona, Los Angeles and Shanghai, as well as the Mobile digital identification. 360 Series of regional conferences. For more information, please visit the GSMA Digital Identity For more information, please visit the GSMA corporate website at www.gsma.com/digitalidentity website at www.gsma.com Follow GSMA Mobile for Development on Twitter: Follow the GSMA on Twitter: @GSMA @GSMAm4d This document is an output of a project funded by UK aid from the Department for International Development (DFID), for the benefit of developing countries. The views expressed are not necessarily those of DFID. Author: Matt Wilson, Senior Insights Manager, GSMA Rob Waddington, Futuresight Understanding Capture and Validate KYC Processes: Global Experiences, Challenges and Learnings v Contents Executive Summary ................................................................................. -

FATCA-CRS-Faqs.Pdf
FATCA/CRS FAQs:- 1. What is FATCA? The Foreign Account Tax Compliance Act (FATCA) is a United States federal law that requires United States persons, including US persons who live outside the United States, to report their financial accounts held outside of the United States, and requires foreign financial institutions to report to the Internal Revenue Service (IRS) about their U.S. clients. Government of India (GOI) has signed a Model 1 Inter-Governmental Agreement (IGA) with US on July 9, 2015 which necessitates financial institutions in India to comply with FATCA. 2. What is CRS? CRS is known as Common Reporting Standards. It is an information standard for the automatic exchange of information (AEoI), developed in the context of the Organisation for Economic Co-operation and Development (OECD). The Government of India has also joined the Multilateral Competent Authority Agreement (MCAA) on June 3, 2015 and financial institutions in india to comply with CRS. 3. Why do we need to ask the FATCA/CRS declaration from the customer? Government of India (GOI) has signed a Model 1 Inter-Governmental Agreement (IGA) with US on July 9, 2015. The IGA provides that the Indian FIs will provide the necessary information to Indian tax authority i.e. Central Board of Direct Taxes (CBDT), which will then be transmitted to USA automatically in case of FATCA. The Government of India has also joined the Multilateral Competent Authority Agreement (MCAA) on June 3, 2015, for exchanging information with respective tax authorities from 63 partner jurisdictions which are signatories to MCAA. To enable this, CBDT has issued a notification to all financial institutions in India to comply with the CRS and FATCA regulations. -

Trend Micro Data Protection Lists (Release 3.0)
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes, and the latest version of the applicable user documentation, which are available from the Trend Micro Web site at: http://docs.trendmicro.com/ Trend Micro, the Trend Micro t-ball logo, and OfficeScan are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2014. Trend Micro Incorporated. All rights reserved. Document Part No. LPEM55806/121205 Release Date: September 2014 Document Version No.: 3.0 Protected by U.S. Patent No.: 5,623,600; 5,889,943; 5,951,698; 6,119,165 This document contains information common to all Trend Micro products that support data protection features. Detailed information about how to use specific features within your product may be available in the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base at the Trend Micro website. Read through the documentation before installing or using the product. Trend Micro is always seeking to improve its documentation. Your feedback is always welcome. Please evaluate this documentation on the following site: http://www.trendmicro.com/download/documentation/rating.asp Table of Contents Chapter 1: Data Loss Prevention - Predefined Data Identifiers and Templates Predefined Expressions ................................................................................ -

Forcepoint DLP Predefined Policies and Classifiers
Forcepoint DLP Predefined Policies and Classifiers Predefined Policies and Classifiers | Forcepoint DLP | v8.5.x For your convenience, Forcepoint DLP includes hundreds of predefined policies and content classifiers. ● Predefined policies help administrators quickly and easily define what type of content is considered a security breach at their organization. While choosing a policy or policy category, some items are set “off” by default. They can be activated individually in the Forcepoint Security Manager. ■ Data Loss Prevention policies, page 2 ■ Discovery policies, page 108 ● Predefined classifiers can be used to detect events and threats involving secured data. This article provides a list of all the predefined content classifiers that Forcepoint DLP provides for detecting events and threats involving secured data. This includes: ■ File-type classifiers ■ Script classifiers ■ Dictionaries ■ Pattern classifiers The predefined policies and classifiers are constantly being updated and improved. See Updating Predefined Policies and Classifiers for instructions on keeping policies and classifiers current. © 2017 Forcepoint LLC Data Loss Prevention policies Predefined Policies and Classifiers | Forcepoint DLP | v8.5.x Use the predefined data loss prevention policies to detect sensitive content, compliance violations, and data theft. For acceptable use policies, see: ● Acceptable Use, page 3 The content protection policies fall into several categories: ● Company Confidential and Intellectual Property (IP), page 4 ● Credit Cards, page 9 ● Financial -

THAILAND MIGRATION REPORT 2011 Edited by Jerrold W
THAILAND MIGRATION REPORT 2011 edited by Jerrold W. Huguet Aphichat Chamratrithirong International Organization for Migration International Labour Organization United Nations Development Programme United Nations Population Fund United Nations High Commissioner for Refugees World Health Organization United Nations Children’s Fund United Nations Office on Drugs and Crime United Nations Entity for Gender Equality and the Empowerment of Women Office of the High Commissioner for Human Rights International Telecommunication Union World Bank United Nations Country Team in Thailand Migration for development in Thailand: Overview and tools for policymakers edited by Jerrold W. Huguet Aphichat Chamratrithirong CoverPhotos: Top left: Martine Perret (UN), Centre top: Claudia Natali (IOM), Top right: Daniel Tshin (UNDP) Foreword Centre right: Chris Lom (IOM) Bottom left & right: Labour Rights Promotion Network Thailand Migration Report 2011 - the third in a series which started in 2005 - is the product of a collaborative effort between member agencies of the United Nations Thematic Working Group on Migration in Thailand, under the leadership of the International Organization for Migration. Like its predecessors, it aims to provide policymakers, practitioners and academia with current information on migration trends and patterns in Thailand, together with relevant policy developments. The designations employed and the presentation of the material in this report do not imply the expression of In addition to its standard features, this new volume focuses on “Migration for development in Thailand: any opinion whatsoever on the part of the United Nations or the International Organization for Migration overview and tools for policymakers”. This theme has been high on the United Nations and government concerning the legal status of any country, territory, city or area, or of its authorities, or concerning the agendas in recent years, as the world increasingly recognizes that migration can be a key driver for delimitation of its frontiers or boundaries. -

Common Reporting Standard
COMMON REPORTING STANDARD TAX IDENTIFICATION NUMBERS LEAFLET Version updated as of October 31th, 2019 Disclaimer: The present informative document, subject to modification, is communicated for information purposes only and has no contractual value. This document is defined based on the information provided by the OECD portal. It contains information that it is the sole responsibility of each country and is (i) of a general nature only and not intended to address the specific circumstances of any particular individual or entity, (ii) not necessarily comprehensive, complete, accurate or up to date,(iii) sometimes linked to external sites over which SG Group has no control and for which SG Group assumes no responsibility and (iv) not professional or legal advice. If you need specific advice, you should always consult a professional tax advisor. TAX IDENTIFICATION NUMBERS This document provides an overview of domestic rules in the countries listed below governing the issuance, structure, use and validity of Tax Identification Numbers (“TIN”) or their functional equivalents. It is split into two sections: Countries that have already published the information on the OECD portal and can 1 be accessed by clicking on the name of the country below Cook Andorra Hungary Malaysia Saudi Arabia Islands Argentina Costa Rica Iceland Malta Seychelles Marshall Aruba Croatia India Islands Singapore Australia Curacao Indonesia Mauritius Slovak Republic Ireland Austria Mexico Cyprus Slovenia Isle of Man Azerbaijan Czech Montserrat Republic South Africa Bahrain -

TRITON AP-DATA Predefined Policies and Classifiers
Contents Predefined Policies . 1 Data Loss Prevention policies . 1 Acceptable Use . 2 Content Protection. 3 Company Confidential and Intellectual Property (IP) . 3 Credit Cards . 8 Financial Data . 10 Protected Health Information (PHI) . 14 Personally Identifiable Information (PII) . 16 Regulations, Compliance and Standards. 27 Financial Regulations . 27 Payment Card Industry (PCI). 30 Privacy Regulations . 31 US and Canada Federal Regulations . 63 Data Theft Risk Indicators . 73 Suspicious User Activity . 73 Indicators of Compromise . 75 Employee Discontent . 76 Quick Policies . 76 Web DLP policy . 77 Email DLP policy . 78 Mobile DLP policy . 79 Discovery policies . 79 Acceptable Use . 80 Company Confidential and Intellectual Property . 80 Employee Discontent . 82 Financial Information . 83 Indicators of Compromise. 86 Payment Card Information (PCI) . 86 Protected Health Information (PHI) . 87 Personally Identifiable Information (PII). 89 Regulations . 98 Suspicious User Activity. 100 Predefined Classifiers. 101 File-type classifiers . 102 NLP scripts . 106 Predefined Policies and Classifiers i Contents Dictionaries . 131 Regular Expression patterns . 142 ii TRITON AP-DATA TRITON AP-DATA Predefined Policies and Classifiers Predefined Policies and Classifiers | TRITON AP-DATA | Version 8.0.x For your convenience, Websense® TRITON® AP-DATA includes hundreds of predefined policies and content classifiers. Predefined Policies enable you to quickly and easily define what type of content is considered a security breach on your network. Predefined Classifiers can be used to detect events and threats involving secured data. Predefined Policies Predefined Policies and Classifiers | TRITON AP-DATA | Version 8.0.x Predefined policies enable you to quickly and easily define what type of content is considered a security breach on your network. -

ISSN: 2320-5407 Int. J. Adv. Res. 5(9), 958-965
ISSN: 2320-5407 Int. J. Adv. Res. 5(9), 958-965 Journal Homepage: - www.journalijar.com Article DOI: 10.21474/IJAR01/5409 DOI URL: http://dx.doi.org/10.21474/IJAR01/5409 RESEARCH ARTICLE NATIONAL IDENTIFICATION SYSTEM IN THE COUNTRIES AROUND THE GLOBE: AN OUTSIDE REVIEW FROM ETHIOPIAN PERSPECTIVE. Dr. Gavendra Singh1, Mr Ashenafi Chalchissa2 and Mulugeta Kejela3. 1. Assistant Professor, Deptt. of Software Engineering, College of Computing and Informatics, Haramaya University, 138, Dire Dawa, Ethiopia. 2. HOD ,Deptt. of Software Engineering, College of Computing and Informatics, Haramaya University, 138, Dire Dawa, Ethiopia. 3. Deptt. of Software Engineering, College of Computing and Informatics, Haramaya University, 138, Dire Dawa, Ethiopia. …………………………………………………………………………………………………….... Manuscript Info Abstract ……………………. ……………………………………………………………… Manuscript History A national identification numberor national identity number is used by the governments of many countries as a means of tracking Received: 12 July 2017 their citizens, permanent residents, and temporary residents for the Final Accepted: 14 August 2017 purposes ofvarious e-governmentally-related functions. Published: September 2017 The ways in which such a system is implemented vary among Key words:- countries, but in most cases citizens are issued an identification e-ID, e-Government, Capitals, System, number upon reaching legal age, or when they are born.Identification is Identification, internet, face-to-face routinely used to help facilitate commercial and government transaction transactions [1].Such as taking out a loan or applying for government benefits. While individuals can use traditional forms of identification in face-to-face transactions, these forms of identification are less useful for conducting business on the Internet. Individuals can use an National Identification System to authenticate to online services, securely communicate online, purchase goods and services, and create legally-binding electronic signatures, such as to sign a contract. -
Trend Micro Data Protection Lists (Release 2.0)
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes, and the latest version of the applicable user documentation, which are available from the Trend Micro Web site at: http://docs.trendmicro.com/ Trend Micro, the Trend Micro t-ball logo, and OfficeScan are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2012. Trend Micro Incorporated. All rights reserved. Document Part No. LPEM55806/121205 Release Date: September 2014 Document Version No.: 2.0 Protected by U.S. Patent No.: 5,623,600; 5,889,943; 5,951,698; 6,119,165 This document contains information common to all Trend Micro products that support data protection features. Detailed information about how to use specific features within your product may be available in the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base at the Trend Micro website. Read through the documentation before installing or using the product. Trend Micro is always seeking to improve its documentation. Your feedback is always welcome. Please evaluate this documentation on the following site: http://www.trendmicro.com/download/documentation/rating.asp Table of Contents Chapter 1: Data Loss Prevention - Predefined Data Identifiers and Templates Predefined Expressions ................................................................................ -
Tax Identification SGPB.Pdf
MARCH 2016 COMMON REPORTING STANDARD TAX IDENTIFICATION NUMBERS LEAFLET Disclaimer: The present informative document, subject to modification, is communicated for information purposes only and has no contractual value. This document is defined based on the information provided by the OECD portal. It contains information that it is the sole responsibility of each country and is (i) of a general nature only and not intended to address the specific circumstances of any particular individual or entity, (ii) not necessarily comprehensive, complete, accurate or up to date,(iii) sometimes linked to external sites over which SG Group has no control and for which SG Group assumes no responsi- bility and (iv) not professional or legal advice. If you need specific advice, you should always consult a professional tax advisor. TAX IDENTIFICATION NUMBERS This document provides an overview of domestic rules in the countries listed below governing the issuance, structure, use and validity of Tax Identification Numbers (“TIN”) or their functional equivalents. It is split into two sections: Countries that have already published the information on the OECD portal 1 and can be accessed by clicking on the name of the country below Argentina Faroe Islands Japan Seychelles Australia Finland South Korea Singapore Austria France Latvia Slovak Republic Belgium Germany Liechtenstein Slovenia Belize Gibraltar Lithuania South Africa Brazil Greece Luxembourg Spain Bulgaria Greenland Malaysia Sweden Canada Guernsey Malta Switzerland Cayman Islands Hong Kong Mexico -
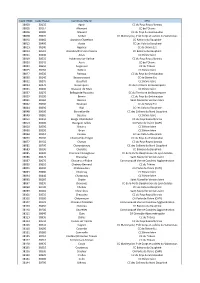
Code INSEE Code Postal Commune Mairie EPCI 38003 38150 Agnin
Code INSEE Code Postal Commune Mairie EPCI 38003 38150 Agnin CC du Pays Roussillonnais 38005 38114 Allemont CC de l'Oisans 38006 38580 Allevard CC du Pays du Grésivaudan 38008 38970 Ambel CC Matheysine, P de Corps et vallées du Valbonnais 38010 38460 Annoisin-Chatelans CC Balcons du Dauphiné 38012 38490 Aoste CC Les Vals du Dauphiné 38013 38140 Apprieu CC de Bièvre Est 38014 38510 Arandon/Arandon-Passins CC Balcons du Dauphiné 38015 38440 Artas CC Bièvre Isère 38019 38550 Auberives-sur-Varèze CC du Pays Roussillonnais 38020 38142 Auris CC de l'Oisans 38023 38650 Avignonet CC du Trièves 38025 38260 Balbins CC Bièvre Isère 38027 38530 Barraux CC du Pays du Grésivaudan 38030 38140 Beaucroissant CC de Bièvre Est 38032 38270 Beaufort CC Bièvre Isère 38034 38270 Beaurepaire CC du Territoire de Beaurepaire 38035 38440 Beauvoir-de-Marc CC Bièvre Isère 38037 38270 Bellegarde-Poussieu CC du Territoire de Beaurepaire 38039 38190 Bernin CC du Pays du Grésivaudan 38041 38160 Bessins Saint Marcellin Vercors Isère 38042 38690 Bevenais CC de Bièvre Est 38044 38690 Biol CC Les Vals du Dauphiné 38048 38090 Bonnefamille CC des Collines du Nord Dauphiné 38049 38260 Bossieu CC Bièvre Isère 38051 38150 Bouge-Chambalud CC du Pays Roussillonnais 38053 38300 Bourgoin-Jallieu CA Porte de l'Isère (CAPI) 38058 38590 Brezins CC Bièvre Isère 38060 38590 Brion CC Bièvre Isère 38064 38110 Cessieu CC Les Vals du Dauphiné 38070 38190 Champ-Près-Froges CC du Pays du Grésivaudan 38072 38150 Chanas CC du Pays Roussillonnais 38081 38790 Charantonnay CC des Collines du Nord -

Exchange Partner Tax Identification Number
EXCHANGE PARTNER TAX IDENTIFICATION NUMBER BOOKLET Please Note: All Exchange Partners are represented, however only jurisdictions which have published their TIN information with the OECD have information displayed. Table of Contents ANGUILLA (AI) ............................................................................................................................................... 4 ANTIGUA AND BARBUDA (AG) ...................................................................................................................... 5 ARGENTINA (AR) ........................................................................................................................................... 6 ARUBA (AW) .................................................................................................................................................. 7 AUSTRALIA (AU) ............................................................................................................................................ 8 AUSTRIA (AT) ................................................................................................................................................. 9 AZERBAIJAN (AZ) ......................................................................................................................................... 10 BAHAMAS (BS) ............................................................................................................................................ 11 BAHRAIN (BH) ............................................................................................................................................