Forcepoint DLP Predefined Policies and Classifiers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
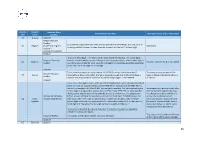
Country Code Country Name National Client Identifier Format
Country Country National client Format of the identifier Potential source of the information code name identifier AT Austria CONCAT Belgian National Number 11 numerical digits where the first 6 are the date of birth (YYMMDD), the next 3 are an BE Belgium (Numéro de registre National ID ordering number (uneven for men, even for women) and the last 2 a check digit. national - Rijksregisternummer) CONCAT It consists of 10 digits. The first 6 are the date of birth (YYMMDD). The next 3 digits Bulgarian Personal have information about the area in Bulgaria and the order of birth, and the ninth digit is BG Bulgaria Passport, National ID, Driving Licence Number even for a boy and odd for a girl. Seventh and eighth are randomly generated according to the city. The tenth digit is a check digit. CONCAT The number for passports issued before 13/12/2010 consists of the character 'E' The passport is issued by the Civil National Passport CY Cyprus followed by 6 digits i.e E123456. Biometric passports issued after 13/12/2010 have a Registry Department of the Ministry Number number that starts with the character 'K', followed by 8 digits. i.e K12345678 of Interior. CONCAT It is a nine or ten-digit number in the format of YYXXDD/SSSC, where XX=MM (month of birth) for male, i.e. numbers 01-12, and XX=MM+50 (or exceptionally XX=MM+70) for female, i.e. numbers 51-62 (or 71-82). For example, a number 785723 representing the It is assigned to a person shortly after first six digits is assigned to a woman born on 23rd of July 1978. -

Doing Business Guide in EMEIA: Payroll Operations
Payroll Operations in Europe, the Middle East, India and Africa — essential compliance and reporting considerations Introduction This booklet contains market-by-market newly established, stand-alone guidance1 on key HR payroll matters to operations. Where the EMEIA operation be considered as you expand your is a regional headquarters or a holding operations across EMEIA. company for foreign subsidiaries, or if In our experience, careful consideration there are existing operations in EMEIA, of these matters at the outset is the other considerations must be taken into most effective way of avoiding any account. issues and ensuring an optimal setup In all situations, we recommend that you structure of your business and seek specific professional advice from employees in new EMEIA markets. the contacts listed in each chapter. They This booklet is general in nature and not will take into consideration your specific to be relied on as professional advice. circumstances and objectives. Furthermore, the chapters focus on NB: This guide will work best with Adobe Acrobat Pro. 1 This information was compiled in July 2019. 2 Payroll Operations in Europe, the Middle East, India and Africa — essential compliance and reporting considerations EY contacts Payroll Operate Services Sheri Sullivan Michael Van Den Brand EY Global Payroll Operate Leader EY EMEIA Payroll Operate Leader T: +17168435050 T: +34 933 666 340 E: [email protected] E: [email protected] Country Payroll leader Email address Armenia Kamo Karapetyan [email protected] -

Payments Insights. Opinions. Volume 24
#payments insights. opinions. Tap. Touch. Speak. Grab and Seven themes impacting the future of payments go. The way we make payments is changing faster than any Winners in the future payments ecosystem will be those that make the right decisions other area of financial services. today. Understanding these seven key themes reshaping payments will help leaders make those decisions and determine how best to differentiate themselves in this New technology and changing fast-changing landscape. customer expectations are shattering the status quo and ushering in a growing number Continued on page 3 of new players that are challenging the traditional role of banks. Volume 24 03 Seven themes impacting the future of payments Understanding the themes transforming payments can help banks make strategic investment decisions and emerge as winners. 07 Why real-time payments are the new normal — and how payments providers can adapt As RTP schemes expand, providers will need to assess readiness and define a clear strategy for platforms, operations, risk and customer experience. Editorial 10 How the mPOS business model expands This newsletter comes to you as many of us prepare to meet again at beyond payments acceptance Sibos – the world’s premier financial services event, held this year in London, 23 to 26 September 2019. EY is a proud sponsor of Sibos, and commends As pure payments acceptance becomes a their efforts to bring together the global financial services and payments commodity for smaller merchants and fees from transaction processing come under community. pressure, mPOS providers are putting a This year’s theme is an exciting one that touches on many of the issues we strategic focus on value-added services to are covering in this #payments issue: “Thriving in a hyperconnected world” continue their high growth. -

SL8500 Modular Library System
StorageTek SL8500 Modular Library System Systems Assurance Guide Part Number: MT9229 May 2010 Revision: L Submit comments about this document by clicking the Feedback [+] link at: http://docs.sun.com StorageTek SL8500 Modular Library System - Systems Assurance Guide MT9229 Revision: L Copyright © 2004, 2010, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related software documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are “commercial computer software” or “commercial technical data” pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). -

Encryption Suite
comforte_Encryption_Suite.qxp_comforte_Encryption_Suite 29.10.17 13:33 Seite 1 comForte´scomforte’s encryptionencryptio nsuite suite ProtectProtect passwords passwords andand confidentialconfidential applicationapplication data data on on HP HP NonStopE Nonsto psystems systems SSecurCSecurCS Se SecurTNcurTN Se SecurFTPcurFTP Sec SecurLiburLib Secu SecurSHrSH Secu SecurPrintrPrint communication is our Forte comforte_Encryption_Suite.qxp_comforte_Encryption_Suite 29.10.17 13:33 Seite 2 Overview comForte offers a rich set of products The following diagram shows all products All our products take advantage of the most depending on the protocol you want to together. This diagram may look confusing widely used and accepted security protocols: encrypt. Even for a single protocol (such at first glance, but we do believe that our Depending on the product, connections are as Telnet) we offer different solutions rich set of products allows us to tailor our secured either via SSL (Secure Sockets Layer, depending on your requirements. solutions according to the customers’ now standardized by the IETF as Transport requirements rather than according to our Layer Security – TLS) or via SSH2 (Secure Shell product set. The purpose of this flyer is to protocol version 2). provide an overview of the different products and to help you find the right solution for All our solutions can restrict access to your your requirements. NonStop system to “encrypted only” and also provide some basic firewall capabilities. comforte_Encryption_Suite.qxp_comforte_Encryption_Suite 29.10.17 13:33 Seite 3 Telnet Encryption Many organizations are realizing that using Webbrowser access to NonStop 6530 single, integrated product. SecurTN replaces Telnet over a heterogenous TCP/IP network and 3270 applications and services, TELSERV, thereby eliminating the “256 session results in reduced security: all protective delivering them to users both inside only” limit of TELSERV. -

Interim Report-The Committee for Promoting Use of Advanced Means
Interim Report The Committee for Promoting November Use of Advanced Means of 2015 Payment in Israel Interim Report of the Committee for Promoting Use of Advanced Means of Payment in Israel Table of Contents 1. Introduction .................................................................................................................... 2 2. Executive summary ........................................................................................................ 3 3. Introduction .................................................................................................................... 6 4. Overview of advanced means of payment world-wide .................................................. 8 5. Overview of advanced means of payment in Israel ..................................................... 10 6. Advantages of using advanced means of payment ....................................................... 17 7. Alternatives for conducting transactions using advanced means of payment in the current payment systems .......................................................................................................... 19 8. Barriers to using advanced means of payment ............................................................. 23 9. Risk associated with use of advanced means of payment ............................................ 26 10. Legal aspects related to promoting use of advanced means of payment...................... 31 11. Summary and recommendations ................................................................................. -

Continuous Auditing of SSH Servers to Mitigate Brute-Force Attacks Phuong M
CAUDIT: Continuous Auditing of SSH Servers To Mitigate Brute-Force Attacks Phuong M. Cao, Yuming Wu, and Subho S. Banerjee, UIUC; Justin Azoff and Alex Withers, NCSA; Zbigniew T. Kalbarczyk and Ravishankar K. Iyer, UIUC https://www.usenix.org/conference/nsdi19/presentation/cao This paper is included in the Proceedings of the 16th USENIX Symposium on Networked Systems Design and Implementation (NSDI ’19). February 26–28, 2019 • Boston, MA, USA ISBN 978-1-931971-49-2 Open access to the Proceedings of the 16th USENIX Symposium on Networked Systems Design and Implementation (NSDI ’19) is sponsored by CAUDIT: Continuous Auditing of SSH Servers to Mitigate Brute-Force Attacks Phuong M. Cao1, Yuming Wu1, Subho S. Banerjee1, Justin Azoff2;3, Alexander Withers3, Zbigniew T. Kalbarczyk1, Ravishankar K. Iyer1 1University of Illinois at Urbana-Champaign, 2Corelight, 3National Center for Supercomputing Applications Abstract While only a small fraction of such attempts succeed, they This paper describes CAUDIT1, an operational system have led to major misuses in 51% of 1,800 surveyed organi- deployed at the National Center for Supercomputing Applica- zations, with a financial impact of up to $500,000 per organi- tions (NCSA) at the University of Illinois. CAUDIT is a fully zation [7]. automated system that enables the identification and exclusion This paper describes the production deployment of of hosts that are vulnerable to SSH brute-force attacks. Its CAUDIT at the National Center for Supercomputing Ap- key features include: 1) a honeypot for attracting SSH-based plications (NCSA) at the University of Illinois over a period attacks over a /16 IP address range and extracting key meta- of 463 days. -

Scripting the Openssh, SFTP, and SCP Utilities on I Scott Klement
Scripting the OpenSSH, SFTP, and SCP Utilities on i Presented by Scott Klement http://www.scottklement.com © 2010-2015, Scott Klement Why do programmers get Halloween and Christmas mixed-up? 31 OCT = 25 DEC Objectives Of This Session • Setting up OpenSSH on i • The OpenSSH tools: SSH, SFTP and SCP • How do you use them? • How do you automate them so they can be run from native programs (CL programs) 2 What is SSH SSH is short for "Secure Shell." Created by: • Tatu Ylönen (SSH Communications Corp) • Björn Grönvall (OSSH – short lived) • OpenBSD team (led by Theo de Raadt) The term "SSH" can refer to a secured network protocol. It also can refer to the tools that run over that protocol. • Secure replacement for "telnet" • Secure replacement for "rcp" (copying files over a network) • Secure replacement for "ftp" • Secure replacement for "rexec" (RUNRMTCMD) 3 What is OpenSSH OpenSSH is an open source (free) implementation of SSH. • Developed by the OpenBSD team • but it's available for all major OSes • Included with many operating systems • BSD, Linux, AIX, HP-UX, MacOS X, Novell NetWare, Solaris, Irix… and yes, IBM i. • Integrated into appliances (routers, switches, etc) • HP, Nokia, Cisco, Digi, Dell, Juniper Networks "Puffy" – OpenBSD's Mascot The #1 SSH implementation in the world. • More than 85% of all SSH installations. • Measured by ScanSSH software. • You can be sure your business partners who use SSH will support OpenSSH 4 Included with IBM i These must be installed (all are free and shipped with IBM i **) • 57xx-SS1, option 33 = PASE • 5733-SC1, *BASE = Portable Utilities • 5733-SC1, option 1 = OpenSSH, OpenSSL, zlib • 57xx-SS1, option 30 = QShell (useful, not required) ** in v5r3, had 5733-SC1 had to be ordered separately (no charge.) In v5r4 or later, it's shipped automatically. -

The Credit Card Industry in Israel
The credit card industry in Israel David Gilo, Faculty of Law, Tel-Aviv University Yossi Spiegel, Faculty of Management, Tel Aviv University, September 2005 2 Major Israeli banks and their credit card companies Banks and market shares in 2004 1998 – 2000 2000 – 2005 in terms of deposits by the public Bank Hapoalim - 29.8% Isracard (100% owned): Isracard (100% owned): • Isracard (100%) • Isracard (100%) • Mastercard (100%) • Mastercard (≈ 100%) • American Express (100%) • American Express (100%) • Visa (N/A) Bank Leumi - 25.6% CAL (65% owned): Leumi Card (100% owned): • Visa (84%) • Visa Leumi (≈ 50%) • Mastercard (N/A) Israel Discount Bank - 17.6% CAL (35% owned) CAL (51% owned): • Visa (≈ 50%) • Mastercard (N/A) Bank Hamizrachi - 10.7% First Int'l Bank - 8.5% Alpha Card (67% owned): CAL (20% owned) • Visa (16%) 3 Credit cards and market shares in acquisition (most of the data is from 2001) Credit card Cards Number of cards Market share in company (in millions) acquiring Isracard Isracard 1.1 47% Mastercard 0.3 American Express 0.15 Visa N/A Cal Visa Cal 1.1 31.8% Mastercard N/A Diners card 0.16 Leumi Card Visa Leumi 1.2 15.3% (2004) Mastercard N/A Others 5.9% Total active cards 3.8 (2004) Number of active cards grew at an annual rate of 9.1% since 1982 (from 0.55 million) 4 Main features of Israeli credit cards !"Deferred debit cards; virtually no credit cards and no debit cards !"Credit cards are also ATM cards and in effect are tied with bank accounts (Bank Leumi's clients were unilaterally transferred from CAL). -

The Credit Card Industry in Israel
Preliminary and incomplete The credit card industry in Israel David Gilo* and Yossi Spiegel** September 2005 Abstract: Since 1998, the Israeli credit card industry was transformed from a duopoly with two credit card companies which offer proprietary cards to a triopoly with two large open systems, Visa and Mastercard, which are issued and acquired by each of the three credit card companies. Regulatory intervention by the Israeli Antitrust Authority (IAA) played a key role in bringing about this structural change. In this paper we first review the Israeli credit card industry and then discuss in detail the regulatory intervention by the IAA. * The Buchmann Faculty of Law, Tel-Aviv University, Ramat Aviv, Tel Aviv, 69978, Israel, email: [email protected]. ** Faculty of Management, Tel Aviv University, Ramat Aviv, Tel Aviv, 69978, Israel. Email: [email protected], http://www.tau.ac.il/~spiegel Both authors were economic experts for Supersol (the largest supermarket chain in Israel) in the Israeli credit card case. 1 1. A brief history of the credit card industry in Israel Until 1998, there were two main players in the Israeli credit cards industry: Isracard, which was established in 1975 and is 100% owned by the largest bank in Israel, Bank Hapoalim, and CAL which was established in 1978 and was jointly owned at the time by the second largest bank in Israel, Bank Leumi (65%), and the third largest bank, Israel Discount Bank (35%). Isracard issued its own brand of credit card, called Isracard, for domestic use in Israel, and Mastercard and American express card for use in Israel and abroad, while CAL issued both Visa cards, under the brand name Visa CAL, and Diners Club cards. -

FATCA-CRS-Faqs.Pdf
FATCA/CRS FAQs:- 1. What is FATCA? The Foreign Account Tax Compliance Act (FATCA) is a United States federal law that requires United States persons, including US persons who live outside the United States, to report their financial accounts held outside of the United States, and requires foreign financial institutions to report to the Internal Revenue Service (IRS) about their U.S. clients. Government of India (GOI) has signed a Model 1 Inter-Governmental Agreement (IGA) with US on July 9, 2015 which necessitates financial institutions in India to comply with FATCA. 2. What is CRS? CRS is known as Common Reporting Standards. It is an information standard for the automatic exchange of information (AEoI), developed in the context of the Organisation for Economic Co-operation and Development (OECD). The Government of India has also joined the Multilateral Competent Authority Agreement (MCAA) on June 3, 2015 and financial institutions in india to comply with CRS. 3. Why do we need to ask the FATCA/CRS declaration from the customer? Government of India (GOI) has signed a Model 1 Inter-Governmental Agreement (IGA) with US on July 9, 2015. The IGA provides that the Indian FIs will provide the necessary information to Indian tax authority i.e. Central Board of Direct Taxes (CBDT), which will then be transmitted to USA automatically in case of FATCA. The Government of India has also joined the Multilateral Competent Authority Agreement (MCAA) on June 3, 2015, for exchanging information with respective tax authorities from 63 partner jurisdictions which are signatories to MCAA. To enable this, CBDT has issued a notification to all financial institutions in India to comply with the CRS and FATCA regulations. -

Tax ID Table
Country Flag Country Name Tax Identification Number (TIN) type TIN structure Where to find your TIN For individuals, the TIN consists of the letter "E" or "F" followed by 6 numbers and 1 control letter. TINs for Número d’Identificació residents start with the letter "F." TINs for non-residents AD Andorra Administrativa (NIA) start with the letter "E". AI Anguilla N/A All individuals and businesses receive a TIN (a 6-digit number) when they register with the Inland Revenue Department. See http://forms.gov. AG Antigua & Barbuda TIN A 6-digit number. ag/ird/pit/F50_Monthly_Guide_Individuals2006.pdf CUIT. Issued by the AFIP to any individual that initiates any economic AR Argentina activity. The CUIT consists of 11 digits. The TIN is generated by an automated system after registering relevant AW Aruba TIN An 8-digit number. data pertaining to a tax payer. Individuals generally use a TFN to interact with the Australian Tax Office for various purposes and, therefore, most individuals have a TFN. This includes submitting income tax returns, reporting information to the ATO, obtaining The Tax File Number (TFN) is an eight- or nine-digit government benefits and obtaining an Australian Business Number (ABN) AU Australia Tax File Number (TFN) number compiled using a check digit algorithm. in order to maintain a business. TINs are only issued to individuals who are liable for tax. They are issued by the Local Tax Office. When a person changes their residence area, the TIN AT Austria TIN Consists of 9 digits changes as well. TINs are only issued to people who engage in entrepreneurial activities and AZ Azerbaijan TIN TIN is a ten-digit code.