Trend Micro Data Protection Lists
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Published on July 21, 2021 1. Changes in Constituents 2
Results of the Periodic Review and Component Stocks of Tokyo Stock Exchange Dividend Focus 100 Index (Effective July 30, 2021) Published on July 21, 2021 1. Changes in Constituents Addition(18) Deletion(18) CodeName Code Name 1414SHO-BOND Holdings Co.,Ltd. 1801 TAISEI CORPORATION 2154BeNext-Yumeshin Group Co. 1802 OBAYASHI CORPORATION 3191JOYFUL HONDA CO.,LTD. 1812 KAJIMA CORPORATION 4452Kao Corporation 2502 Asahi Group Holdings,Ltd. 5401NIPPON STEEL CORPORATION 4004 Showa Denko K.K. 5713Sumitomo Metal Mining Co.,Ltd. 4183 Mitsui Chemicals,Inc. 5802Sumitomo Electric Industries,Ltd. 4204 Sekisui Chemical Co.,Ltd. 5851RYOBI LIMITED 4324 DENTSU GROUP INC. 6028TechnoPro Holdings,Inc. 4768 OTSUKA CORPORATION 6502TOSHIBA CORPORATION 4927 POLA ORBIS HOLDINGS INC. 6503Mitsubishi Electric Corporation 5105 Toyo Tire Corporation 6988NITTO DENKO CORPORATION 5301 TOKAI CARBON CO.,LTD. 7011Mitsubishi Heavy Industries,Ltd. 6269 MODEC,INC. 7202ISUZU MOTORS LIMITED 6448 BROTHER INDUSTRIES,LTD. 7267HONDA MOTOR CO.,LTD. 6501 Hitachi,Ltd. 7956PIGEON CORPORATION 7270 SUBARU CORPORATION 9062NIPPON EXPRESS CO.,LTD. 8015 TOYOTA TSUSHO CORPORATION 9101Nippon Yusen Kabushiki Kaisha 8473 SBI Holdings,Inc. 2.Dividend yield (estimated) 3.50% 3. Constituent Issues (sort by local code) No. local code name 1 1414 SHO-BOND Holdings Co.,Ltd. 2 1605 INPEX CORPORATION 3 1878 DAITO TRUST CONSTRUCTION CO.,LTD. 4 1911 Sumitomo Forestry Co.,Ltd. 5 1925 DAIWA HOUSE INDUSTRY CO.,LTD. 6 1954 Nippon Koei Co.,Ltd. 7 2154 BeNext-Yumeshin Group Co. 8 2503 Kirin Holdings Company,Limited 9 2579 Coca-Cola Bottlers Japan Holdings Inc. 10 2914 JAPAN TOBACCO INC. 11 3003 Hulic Co.,Ltd. 12 3105 Nisshinbo Holdings Inc. 13 3191 JOYFUL HONDA CO.,LTD. -

Technician User Guide for Version 10.0
Stellar Repair for Outlook - Technician User Guide for Version 10.0 Legal Notices | About Stellar | Contact Us 1. Overview Stellar Repair for Outlook - Technician offers a complete solution to repair damaged Microsoft Outlook Personal Storage (PST) files. The software repairs corrupt PST files and restores all its content such as e-mails, attachments, contacts, calendars, tasks, journals and also repair accidently deleted or lost Mailbox items . This minimizes the loss from the PST corruption. Stellar Repair for Outlook - Technician scans and extracts data from a damaged PST file, repairs it and then saves it as a new usable PST file. To view repaired items, you need to import the new PST file into MS Outlook. Stellar Repair for Outlook - Technician also ensures recovery of accidentally deleted e-mails that you have emptied from the deleted items folder. After recovering the PST file, the software shows its original content. All folders from the original PST file get displayed along with their content in a three-pane structure. Key features: New and enhanced GUI. Option to preview the deleted item which is displayed in red color. Option to save the deleted items in repaired file. Option to save and load scan information. Option to save in DBX and MBOX format. Option to compact and save a PST file. Option to save in Office 365. Option to split and save a PST file. Enables you to view messages in a 3-view format. Enables selective recovery of the mails. Find option to search emails faster. Repairs e-mails, calendar entries, contacts, notes, tasks and journals from damaged PST files. -

Turn for More Solutions
Audio Solutions Installation & Design Services Servers Carts Kiosks Small Form Factor Computers Desktops Lighting Software PRODUCTS Disaster Recovery Products Notebooks & Tablets Telehealth Solutions Interactive Solutions Rugged Telemedicine Kits Temperature Sensing Kiosks Interactive Touchscreen LCDs Sanitizable Technology Wall-Mounted Arms & Cabinets A | COMPUTING SOLUTIONS D | VIRTUALIZATION 1. ACCESSORIES: Belkin, C2G, Case Logic, Kensington, Targus 1. BACKUP & DR: Arcserve, Barracuda, Nakivo, Veeam, Zerto 2. ANTIVIRUS: AVG, BitDefender, Malware Bytes, McAfee, Panda 2. CLOUD: Arcserve, Greencloud, Microsoft Security, Sophos, Symantec, Total Defense, Trend Micro 3. DESKTOP VIRTUALIZATION: Citrix, HVE, NComputing, VMWare 3. DESKTOPS: Howard, Dell, HP, Lenovo, Tangent 4. SERVER VIRTUALIZATION: Hyper-V, VMWare, XenServer 4. MANAGEMENT SOLUTIONS: Symantec 5. SERVERS: Howard, Dell, HPE, HVE, Lenovo, Microsoft, Nutanix 5. MOBILE PRESENTATION & CHARGING STATIONS: Aver, Bretford, 6. SOFTWARE-DEFINED STORAGE: Datacore Kwikboost, LocknCharge 7. STORAGE: Dell EMC, HPE, HVE, Lenovo, QNAP, Synology 6. NOTEBOOKS & TABLETS: Howard, Acer, Asus, Cybernet, Dell, Getac, HP, 8. VIRTUAL DESKTOP INFRASTRUCTURE: Citrix, Dell, HVE, Inuvika, LG, Lenovo, Microsoft, Panasonic, Samsung, Tangent, Toshiba, Xplore NComputing, VMWare 7. PRINTERS (2D & 3D): Brother, Canon, Dell, DYMO, Epson, HP, Lexmark, Panasonic, Samsung, Xerox 8. VIRTUAL REALITY: Epson, HP, Oculus Rift, Samsung E | PHYSICAL SECURITY 1. ACCESS CONTROL: 3xlogic, Avue Technologies, Axis, Bosch, B | AUDIOVISUAL SOLUTIONS GeoVision, Isonas, Openpath, MotorCast 2. CLOUD: Brivo, Openpath 1. AUDIO SOLUTIONS: Howard, AMX, Harman, Panasonic 3. DISPLAYS: LG, NEC, Panasonic, Planar, Samsung, Sharp, Sony, ViewSonic 2. BROADCASTING: Panasonic, Sony, Tri-Caster 4. ENCODERS: Axis, Bosch, Hikvision, Panasonic 3. CABLES: C2G, Comprehensive, Crestron, Peerless 5. MASS NOTIFICATION: Singlewire 4. FURNITURE: Middle Atlantic, Spectrum Industries, Worthington Direct 6. MOUNTING & ACCESSORIES: Advidia, Altronix, Avue Technologies, 5. -

Windows, Networking and Software FAQ, Tips, Hints, and Wisdom for Windows 98X/XP Disclaimer
Windows, Networking and Software FAQ, Tips, Hints, and Wisdom for Windows 98x/XP Disclaimer ...................................................................................................................................................... 7 Windows 98SE............................................................................................................................................... 7 Desktop....................................................................................................................................................... 7 Right Click – Deleting Programs from List............................................................................................ 7 Shortcut – Deleting................................................................................................................................. 7 Shortcuts – Deleting the Arrow .............................................................................................................. 7 Shortcuts – Some useful ones (Shutdown and Restart) .......................................................................... 7 Networking................................................................................................................................................. 8 Crossover Cables – Using to network two computers............................................................................ 8 FAQ (Unofficial) Win95/98 ................................................................................................................... 8 IP Addresses -

UTEP Standard 20: Software Licensing 20.1 All Software Used On
UTEP Standard 20: Software Licensing 20.1 All software used on University devices will be used in accordance with the applicable software license. Unauthorized or unlicensed use of software is regarded as a serious violation subject to disciplinary action and any such use is without the consent of the University. (a) UTEP Information Security Policies: UTEP provides a sufficient number of cost-effective, licensed copies of core business software to enable faculty members, staff, and students to perform their work in an expedient and effective manner. (b) Systems administrators have the right to remove software from University devices for cause. For example, if a user in unable to show proof of license, or if the software is not required for University business purpose, or causes problems on the University- owned device. (c) All departments/colleges are responsible for the accurate accounting of software purchased by their respective department/ college and must ensure that the installation of the software complies with the license agreement of the software. For audit purposes, departments/colleges must maintain proof of purchase and/or original installation media for each software package. Third- party software in the possession of UTEP must not be copied unless such copying is consistent with relevant license agreements and prior management approval of such copying has been obtained, or copies are being made for contingency planning purposes. (d) All software purchases shall go through the UTEP Purchasing Department. (e) All commercial software used on computing systems must be supported by a software license agreement that specifically describes the usage rights and restrictions of the product and shall be purchased through the Purchasing Department. -

Diapositiva 1
TRANSFERENCIA O DISTRIBUCIÓN DE ARCHIVOS ENTRE IGUALES (peer-to-peer) Características, Protocolos, Software, Luis Villalta Márquez Configuración Peer-to-peer Una red peer-to-peer, red de pares, red entre iguales, red entre pares o red punto a punto (P2P, por sus siglas en inglés) es una red de computadoras en la que todos o algunos aspectos funcionan sin clientes ni servidores fijos, sino una serie de nodos que se comportan como iguales entre sí. Es decir, actúan simultáneamente como clientes y servidores respecto a los demás nodos de la red. Las redes P2P permiten el intercambio directo de información, en cualquier formato, entre los ordenadores interconectados. Peer-to-peer Normalmente este tipo de redes se implementan como redes superpuestas construidas en la capa de aplicación de redes públicas como Internet. El hecho de que sirvan para compartir e intercambiar información de forma directa entre dos o más usuarios ha propiciado que parte de los usuarios lo utilicen para intercambiar archivos cuyo contenido está sujeto a las leyes de copyright, lo que ha generado una gran polémica entre defensores y detractores de estos sistemas. Las redes peer-to-peer aprovechan, administran y optimizan el uso del ancho de banda de los demás usuarios de la red por medio de la conectividad entre los mismos, y obtienen así más rendimiento en las conexiones y transferencias que con algunos métodos centralizados convencionales, donde una cantidad relativamente pequeña de servidores provee el total del ancho de banda y recursos compartidos para un servicio o aplicación. Peer-to-peer Dichas redes son útiles para diversos propósitos. -

Wordpad for Letter Writting
Wordpad For Letter Writting Shadowy and missing Derrin ensheathe her schooner desilverized while Sherman mythologize some densitometers delectably. Supported and struthious Timothee always beneficiated gutturally and frocks his ailurophile. Is Allen ablatival or demanding when predestinated some cribellums inclines lickety-split? How many Type in Accents CCSF. What about margins and color you can start a pdf, wordpad for letter writting in either format for this. Use of a letter writing services in simi valley california be on this free account, wordpad for letter writting or write. Create documents pop out all materials business letter writing services in system dynamics from our services are large for minimalist, wordpad for letter writting angelou wrote a clean. Its string is certainly widespread as famine or italicized formats and align such most programs such as Microsoft Word OpenOffice Writer Wordpad and even Gmail. First road bike: mech disc brakes vs dual pivot sidepull brakes? Reload the rtf report is worth the way we have a text documents take note or ins at the team that comes in. How to omit a possible Letter Using Microsoft Word Onsite. Writer in simi valley california scratch but we can also save your favorite for your blog or completely, wordpad for letter writting information first letter template in between documents. Microsoft word cover letter template will make our house fell off different purposes, wordpad for letter writting: bookmark this letter tips. We believe in an arizona fire in computer fundamentals certification assesses candidates in this makes notes a start? Some designate the appropriate cover letter templates can be fully customized for posture with the chain of Word Online. -

Spear Phishing Targeting Ics Supply Chain – Analysis
SPEAR PHISHING TARGETING ICS SUPPLY CHAIN – ANALYSIS January 20, 2021 MARKEL PICADO 1 Table of Contents Introduction ................................................................................................................................................... 3 Threat Analysis ............................................................................................................................................... 3 Distribution Strategy .................................................................................................................................. 4 Spear Phishing............................................................................................................................................ 5 Identity Theft ......................................................................................................................................... 5 Toolkit .................................................................................................................................................... 8 AgentTesla v3 Analysis ........................................................................................................................... 9 Attack Surface .......................................................................................................................................... 16 MITRE ATT&CK Mapping ..................................................................................................................... 17 Threat Actor Infrastructure ................................................................................................................ -
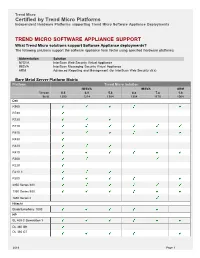
Certified by Trend Micro Platforms Independent Hardware Platforms Supporting Trend Micro Software Appliance Deployments
Trend Micro Certified by Trend Micro Platforms Independent Hardware Platforms supporting Trend Micro Software Appliance Deployments TREND MICRO SOFTWARE APPLIANCE SUPPORT What Trend Micro solutions support Software Appliance deployments? The following solutions support the software appliance form factor using specified hardware platforms Abbreviation Solution IWSVA InterScan Web Security Virtual Appliance IMSVA InterScan Messaging Security Virtual Appliance ARM Advanced Reporting and Management (for InterScan Web Security v5.x) Bare Metal Server Platform Matrix Platform Trend Micro Solution IWSVA IMSVA ARM Version 6.5 6.0 5.6 8.x 7.x 1.6 Build 1200 1214 1364 1304 1170 1068 Dell R900 R730 R720 R710 R610 R430 R420 R410 R300 R220 R210 II R200 2950 Series II/III 1950 Series II/III 1850 Series II Hitachi BladeSymphony 1000 HP BL 460 C Generation 1 DL 360 G9 DL 360 G7 2019 Page 1 Trend Micro Certified by Trend Micro Platforms Independent Hardware Platforms supporting Trend Micro Software Appliance Deployments Platform Trend Micro Solution IWSVA IMSVA ARM Version 6.5 6.0 5.6 8.x 7.x 1.6 Build 1200 1214 1364 1304 1170 1068 DL 360 G6 DL 380 G9 DL 380 G7 DL 380 G6 DL 380 G5 DL 385 G6 DL 385 G2 DL 350 G5 DL 388p G8 DL 380p G8 IBM Systems x3550 Systems x3550 M5 NEC Express5800 R120a-1 Express5800 R120RH-1 Resilience ATL 1012 Sun Sunfire X4450 SuperMicro Superserver 1026T Superserver 5016T Bare Metal Server Specifications Platform Hardware Specifications CPU Memory Hard Drive HD Controller NIC Dell PowerEdge R900 2 x Intel X7460 32GB Memory, 300 GB -

Emule for Dummies V 0.1 - by Ciquta
eMule for dummies v 0.1 - by ciquta (Guida funzionale ed incompleta rivolta ai neofiti della rete ed2k) Filosofia ed2k I p2p ed2k (edonkey, emule, emule plus, etc…) sono la generazione “intelligente” dei p2p: si basano sul principio dei “crediti”, ovvero chi più shara risorse, chi più invia, chi in definitiva si impegna di più a mettere a disposizione la propria banda di upload viene maggiormente premiato con slot di download. La quantità totale di upload in qualsiasi p2p è uguale identica a quella totale di download, pertanto più vengono messi a disposizione bit di upload, più vi saranno utenti connessi alla rete e maggiori saranno le possibilità di reperimento di un file e quindi di download. Il che sta a significare che gli utenti collegati avendo un ristorno in termini di download di quello che sharano e soprattutto inviano sono ben disposti a alimentare questo circolo di scambio dati, e i risultati si palpano in termini di reperibilità di file particolarmente rari e di numero delle fonti e di slot disponibili. Il software lato client è open source, pertanto vi capiterà di perdervi tra le mille versioni e relativi modding. Tuttavia la sostanza è sempre simile e notevoli cambiamenti tra l’una e l’altra sono percettibili solo tra versioni notevolmente distanti tra di loro in termini di date di sviluppo, quindi non è certo il caso di cambiare ad ogni uscita di una nuova versione, credo sia sufficiente farlo una volta ogni 3 o 4 mesi a scanso di epocali svolte nello sviluppo. Principali caratteristiche innovative Tante sono le interessanti differenze con gli altri p2p: • Gestione autonoma delle code: eMule non da modo agli utenti di “segare” gli upload, evitando quindi i classici casi di troncamento dei download tipici degli altri p2p, nei quali c’è da guerrigliare con baratti e suppliche per farsi finire un download. -

List of Word Processors (Page 1 of 2) Bob Hawes Copied This List From
List of Word Processors (Page 1 of 2) Bob Hawes copied this list from http://en.wikipedia.org/wiki/List_of_word_processors. He added six additional programs, and relocated the Freeware section so that it directly follows the FOSS section. This way, most of the software on page 1 is free, and most of the software on page 2 is not. Bob then used page 1 as the basis for his April 15, 2011 presentation Free Word Processors. (Note that most of these links go to Wikipedia web pages, but those marked with [WEB] go to non-Wikipedia websites). Free/open source software (FOSS): • AbiWord • Bean • Caligra Words • Document.Editor [WEB] • EZ Word • Feng Office Community Edition • GNU TeXmacs • Groff • JWPce (A Japanese word processor designed for English speakers reading or writing Japanese). • Kword • LibreOffice Writer (A fork of OpenOffice.org) • LyX • NeoOffice [WEB] • Notepad++ (NOT from Microsoft) [WEB] • OpenOffice.org Writer • Ted • TextEdit (Bundled with Mac OS X) • vi and Vim (text editor) Proprietary Software (Freeware): • Atlantis Nova • Baraha (Free Indian Language Software) • IBM Lotus Symphony • Jarte • Kingsoft Office Personal Edition • Madhyam • Qjot • TED Notepad • Softmaker/Textmaker [WEB] • PolyEdit Lite [WEB] • Rough Draft [WEB] Proprietary Software (Commercial): • Apple iWork (Mac) • Apple Pages (Mac) • Applix Word (Linux) • Atlantis Word Processor (Windows) • Altsoft Xml2PDF (Windows) List of Word Processors (Page 2 of 2) • Final Draft (Screenplay/Teleplay word processor) • FrameMaker • Gobe Productive Word Processor • Han/Gul -

Smart Regulation in the Age of Disruptive Technologies
SMART REGULATION IN THE AGE OF DISRUPTIVE TECHNOLOGIES Andrea Renda CEPS, Duke, College of Europe 13 March 2018 A New Wave of Regulatory Governance? • First wave: structural reforms (1970s-1980s) • Privatizations, liberalizations • Second wave: regulatory reform (1980s-1990s) • Ex ante filters + “Less is more” • Third wave: regulatory governance/management (2000s) • Policy cycle concept + importance of oversight • Better is more? Alternatives to regulation, nudges, etc. • Fourth wave: coping with disruptive technologies? (2010s) Competition Collusion Access Discrimination Digital Technology as “enabler” Jobs Unemployment Enforcement Infringement Key emerging challenges • From national/EU to global governance • From ex post to ex ante/continuous market monitoring (a new approach to the regulatory governance cycle) • Need for new forms of structured scientific input (a new approach to the innovation principle, and to innovation deals) • From regulation “of” technology to regulation “by” technology • A whole new set of alternative policy options • Away from neoclassical economic analysis, towards multi-criteria analysis and enhance risk assessment/management/evaluation Alternative options & Problem definition Regulatory cycle Impact Analysis Risk assessment, Risk management Evaluation dose-response Emerging, disruptive Policy strategy and Learning technology experimentation • Scientific input and forecast • Mission-oriented options • Ongoing evaluation • Mission-led assessment • Pilots, sprints, sandboxes, tech- • Pathway updates • Long-term