Gang Presence in Social Network Sites
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mexican Raza!
Valuable Coupons Inside! Gratis! www.laprensatoledo.com Ohio & Michigan’s Oldest & Largest Latino Weekly «Tinta con sabor» • Proudly Serving Our Readers since 1989 • Check out our Classifieds! ¡Checa los Anuncios Clasificados! La Prensa’s Quinceañera Year August/agosto 18, 2004 Spanglish Weekly/Semanal 20 Páginas Vol. 35, No. 23 Taquería El Nacimiento Olympics: Puerto Rico defeats EEUU, page 15 Mexican DENTRO: EEUU permitirá más Restaurant largas para visitantes mexicanos........................3 Welcome! Horoscopes.....................5 Hours: Carry-Out Mon-Thur: 9AM-12AM Phone: 313.554.1790 Carla’s Krazy Fri & Sat: 9AM-3AM 7400 W. Vernor Hwy. Korner............................6 Sun: 9AM-12AM Detroit MI 48209 Grito de “HoOoOtT DoOoOgGs”..................6 • Jugos/Tepache • Carne a la Parrilla • Tacos • Burritos Deportes..........................7 • Aguas • Pollo Dorado • Mojarra Frita • Licuados Lottery Results.............7 • Tortas • Quesadillas Olympian Devin • Tostadas • Pozole Vargas.............................8 • Caldos • Carne de Puerco en salsa verde •Mariscos • Breakfast Super Burro Calendar of Events............................12 ¡Bienvenidos I-75 August 14: Gustavo (Gus) Hoyas de Nationwide, Ohio Insurance Director Ann Classifieds.............15-18 Raza! Womer Benjamin, and Angel Guzman, CEO of the Hispanic Business Association. Livernois Athens 2004..........14-15 W. Vernor Springwells Nationwide celebra apertura de nueva oficina en Cleveland Salon Unisex Breves: por Teodosio Feliciano, reportero y fotógrafo de La Prensa Latinoamérica es escenario Janet García se supone que Gibson (Bill) inmediatamente Janet no solo coordinó del 75% de los secuestros solamente iba organizar la vio que esta energética joven la gran apertura pero es en el mundo apertura de la oficina Cleve- latina tenia el talento, la agente asociada y ancla para Por NIKO PRICE land Community Insurance personalidad y actitud para la oficina para Nationwide de la agencia Gibson Insur- sobresalir en el negocio de Insurance y Financial Ser MEXICO (AP): Con una ance. -

Israel Convicts Eichmann of Crimes Against Jews
• I \ \ I • • ■ Stores Open 9.o*Ciock for Christmas mg Avitniffe Daily Net Prees Run For the Week Ended The Weather / December t, 1961 Forecast of D. S. Weather Bnreee Moderatdy cold tonight snow 13,518 or rain beatamlnc tomsrd day Member of the Audit break. Low 26 to 82. Tiieeday rain Burenu of OlreuUtlon Or snow changtor to rain. Hlah 85 to 40. ( ■ Manchester~^A City of Village Charm VOL. LXXXI, NO. 60 (EIGHTEEN PAGES) MANCHESI'ER, CONN., MONDAY, DECEMBER 11, 1961 (Classified AdvertlslnK on Page 16) PRICE FIVE CENTS Fire Lab Will Test State News How, Why Hospital R oundup Israel Convicts Eichmann Violent Death Fire Spread Rapidly Takes Five in Hartford, Dec. 11 (A*)— 6ame spread of the State Weekend m aterial. Of Crimes Against Jews Deputy State Fire Marshal "If It develops that this flame By THE ASSOCIATED PRESS Carroll E. Shaw will fly to spread is too high for reasonable Fire and highway accident.^ Chicago Wednesday to super safety, then we would ask tjie hos vise tests designed to deter pital to take immediate action to took five live.s in Connecticut mine how and why the Hart remove all materls’s of this kind over the weekend. 10 Changes still In use. We would also order Two persons. Including a 2-ycar- ford Hospital fire spread as the removal of this t>pe of material old boy. were killed in Area and Sentencing of Nazi rapidly as it did. from all other Connecticut hospi three tiled as a result of trafBc ac He will take with him Sgt. -

R. V. Haevischer 2013 BCSC 2014
IN THE SUPREME COURT OF BRITISH COLUMBIA Citation: R. v. Haevischer, 2013 BCSC 2014 Date: 20131105 Docket: X072945-B Registry: New Westminster Regina v. Cody Rae Haevischer, Matthew James Johnston and Quang Vinh Thang Le Before: The Honourable Madam Justice Wedge Ruling re: Application No. 104 James Bacon’s Application for a Publication Ban Counsel for the Crown: L.J. Kenworthy Counsel for the Accused Haevischer: D. Dlab Counsel for the Accused Johnston: B.A. Martland Counsel for the Accused Le: B.A. Martland Counsel for Postmedia Network Inc. d.b.a. M.J. Wagner The Vancouver Sun, Canadian Broadcasting Corporation, Global Television Network Inc., and Postmedia Network Inc. d.b.a. The Province: Counsel for J. Bacon: B.R. Anderson Place and Date of Hearing: Vancouver, B.C. September 26, 2013 Place and Date of Judgment: Vancouver, B.C. November 5, 2013 R. v. Haevischer Page 2 I. INTRODUCTION AND BACKGROUND [1] This is an application by James Bacon for an order prohibiting the publication of certain trial evidence in these proceedings. [2] The accused are charged with conspiracy to murder and first degree murder in relation to the October 19, 2007 shooting deaths of the “Surrey Six”. Their trial by judge alone commenced on September 30, 2013. Mr. Bacon faces the same charges in relation to the same conspiracy but on a separate indictment. A date for his trial by judge and jury has yet to be set. It is not disputed that the evidence to be heard at the two trials is intertwined. [3] Part of the Crown’s case on the Haevischer trial comprises a body of discreditable conduct evidence that was earlier ruled admissible. -

SOF Role in Combating Transnational Organized Crime to Interagency Counterterrorism Operations
“…the threat to our nations’ security demands that we… Special Operations Command North (SOCNORTH) is a determine the potential SOF roles for countering and subordinate unified command of U.S. Special Operations diminishing these violent destabilizing networks.” Command (USSOCOM) under the operational control of U.S. Northern Command (USNORTHCOM). SOCNORTH Rear Admiral Kerry Metz enhances command and control of special operations forces throughout the USNORTHCOM area of responsi- bility. SOCNORTH also improves DOD capability support Crime Organized Transnational in Combating Role SOF to interagency counterterrorism operations. Canadian Special Operations Forces Command (CAN- SOF Role SOFCOM) was stood up in February 2006 to provide the necessary focus and oversight for all Canadian Special Operations Forces. This initiative has ensured that the Government of Canada has the best possible integrated, in Combating led, and trained Special Operations Forces at its disposal. Transnational Joint Special Operations University (JSOU) is located at MacDill AFB, Florida, on the Pinewood Campus. JSOU was activated in September 2000 as USSOCOM’s joint educa- Organized Crime tional element. USSOCOM, a global combatant command, synchronizes the planning of Special Operations and provides Special Operations Forces to support persistent, networked, and distributed Global Combatant Command operations in order to protect and advance our Nation’s interests. MENDEL AND MCCABE Edited by William Mendel and Dr. Peter McCabe jsou.socom.mil Joint Special Operations University Press SOF Role in Combating Transnational Organized Crime Essays By Brigadier General (retired) Hector Pagan Professor Celina Realuyo Dr. Emily Spencer Colonel Bernd Horn Mr. Mark Hanna Dr. Christian Leuprecht Brigadier General Mike Rouleau Colonel Bill Mandrick, Ph.D. -

Organised Crime Around the World
European Institute for Crime Prevention and Control, affiliated with the United Nations (HEUNI) P.O.Box 161, FIN-00131 Helsinki Finland Publication Series No. 31 ORGANISED CRIME AROUND THE WORLD Sabrina Adamoli Andrea Di Nicola Ernesto U. Savona and Paola Zoffi Helsinki 1998 Copiescanbepurchasedfrom: AcademicBookstore CriminalJusticePress P.O.Box128 P.O.Box249 FIN-00101 Helsinki Monsey,NewYork10952 Finland USA ISBN951-53-1746-0 ISSN 1237-4741 Pagelayout:DTPageOy,Helsinki,Finland PrintedbyTammer-PainoOy,Tampere,Finland,1998 Foreword The spread of organized crime around the world has stimulated considerable national and international action. Much of this action has emerged only over the last few years. The tools to be used in responding to the challenges posed by organized crime are still being tested. One of the difficulties in designing effective countermeasures has been a lack of information on what organized crime actually is, and on what measures have proven effective elsewhere. Furthermore, international dis- cussion is often hampered by the murkiness of the definition of organized crime; while some may be speaking about drug trafficking, others are talking about trafficking in migrants, and still others about racketeering or corrup- tion. This report describes recent trends in organized crime and in national and international countermeasures around the world. In doing so, it provides the necessary basis for a rational discussion of the many manifestations of organized crime, and of what action should be undertaken. The report is based on numerous studies, official reports and news reports. Given the broad topic and the rapidly changing nature of organized crime, the report does not seek to be exhaustive. -
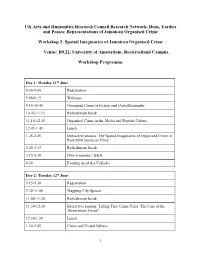
Workshop Programme
UK Arts and Humanities Research Council Research Network, Dons, Yardies and Posses: Representations of Jamaican Organised Crime Workshop 2: Spatial Imaginaries of Jamaican Organised Crime Venue: B9.22, University of Amsterdam, Roeterseiland Campus. Workshop Programme Day 1: Monday 11th June 8.45-9.00 Registration 9.00-9.15 Welcome 9.15-10.45 Organised Crime in Fiction and (Auto)Biography 10.45-11.15 Refreshment break 11.15-12.45 Organised Crime in the Media and Popular Culture 12.45-1.45 Lunch 1.45-2.45 Interactive session: The Spatial Imaginaries of Organised Crime in Post-2000 Jamaican Films 2.45-3.15 Refreshment break 3.15-5.30 Film screening / Q&A 6.30 Evening meal (La Vallade) Day 2: Tuesday 12th June 9.15-9.30 Registration 9.30-11.00 Mapping City Spaces 11.00-11.30 Refreshment break 11.30-12.30 Interactive session: Telling True Crime Tales. The Case of the Thom(p)son Twins? 12.30-1.30 Lunch 1.30-2.45 Crime and Visual Culture 1 2.45-3.15 Refreshment break 3.15-4.15 VisualiZing violence: An interactive session on representing crime and protection in Jamaican visual culture 4.15-5.15 Concluding discussion reflecting on the progress of the project, and future directions for the research 7.00 Evening meal (Sranang Makmur) Panels and interactive sessions Day 1: Monday 11th June 9.15. Organised crime in fiction and (auto)biography Kim Robinson-Walcott (University of the West Indies, Mona), ‘Legitimate Resistance: Drug Dons and Dancehall DJs as Jamaican Outlaws at the Frontier’ Lucy Evans (University of Leicester), ‘The Yardies Becomes Rudies Becomes Shottas’: Reworking Yardie Fiction in Marlon James’ A Brief History of Seven Killings’ Michael Bucknor (University of the West Indies, Mona), ‘Criminal Intimacies: Psycho-Sexual Spatialities of Jamaican Transnational Crime in Garfield Ellis’s Till I’m Laid to Rest (and Marlon James’s A Brief History of Seven Killings)’ Chair: Rivke Jaffe 11.15. -

If You Have Issues Viewing Or Accessing This File Contact Us at NCJRS.Gov
If you have issues viewing or accessing this file contact us at NCJRS.gov. " U.S. Department of Justice National Institute of Justice This document has been reproduced exactly as received from the person or organization originating it. Points of view or opinions stated In this document are those of the authors and do not necessarily represent the olficial position or policies of the National Institute of Justice. Permission to reproduce this ~ material has been 9f3nted by • • .' ubIlc !)Oma.ln u. s--:- ~eneral Accounting Office to the National Criminal Justice Reference Service (NCJRS). Further reproduction outside of the NCJRS system requires permis sion of the ~ owner. .f' 'i:':' ;i. 1 t t~-~-·--~---~--.----g-~-~~-~-~-~-~-c~-~-~-n-tm--g-O-f-fi-ce------------------------------ (-2---~--O--'--J·--?------- ~ Washmgton, D.C. 20548 v V .-J ,, Office of Special Investigations September 29, 1989 The Honorable Sam Nunn Chairman, Permanent Subcommittee on Investigations Committee on Governmental Affairs United States Senate Dear Mr. Chairman: The enclosed report responds to your March 31,1988, request that we examine information about Colombian, Jamaican, Chinese, and Vietnamese criminal gangs operating in the United States, and street gangs in Los Angeles. The report identifies and describes the gangs and their current organizational structures, and discusses recent major investigations into their criminal activities. Also, in response to your request, this report presents the opinions and insight of law enforcement officials regarding existing barriers to the effective investigation and prosecution of the gangs, the adequacy of current legislation in addressing gang activity, and the appropriate law enforcement responses to gang activity. As arranged with your representatives, unless you publicly announce its contents earlier, we plan no further distribution of this report until 30 days from the date of the report. -

Running Head: in and out of ABORIGINAL GANG LIFE-GOODWILL
IN AND OUT OF ABORIGINAL GANG LIFE: PERSPECTIVES OF ABORIGINAL EX-GANG MEMBERS by Alanaise O. Goodwill B.Sc., Simon Fraser University, 1998 M.A., The University of British Columbia, 2003 A THESIS SUBMITTED IN PARTIAL FULFILLMENT OF THE REQUIRMENTS FOR THE DEGREE OF DOCTOR OF PHILOSOPHY in The Faculty of Graduate Studies (Counselling Psychology) THE UNIVERISITY OF BRITISH COLUMBIA (Vancouver) June 2009 © Alanaise O. Goodwill, 2009 ii ABSTRACT This research project generated a categorical scheme to describe the facilitation of gang entry and exit for Aboriginal ex-gang members using the Critical Incident Technique (Flanagan, 1954; Woolsey, 1986) as a method of qualitative data analysis. Former gang members responded to the questions: (a) What facilitated gang entry for you? (b) What facilitated gang exit for you? Participants provided 103 and 136 critical incidents which were categorized into two separate category schemes each containing 13 different categories. The 13 categories for gang entry were; engaging in physical violence, proving one’s worth, hanging around delinquent activity, family involved in gangs and following a family pattern; going to prison, gang becoming family and support system, looking up to gang members and admiring gang lifestyle, becoming dependant on gang, experiencing unsafe or unsupportive parenting practices, gaining respect by rank increase, reacting to authority, caught in a cycle of fear, and partying. The 13 categories for gang exit were; working in the legal workforce, accepting support from family or girlfriend, helping others stay out of or move away from gang life, not wanting to go back to jail, accepting responsibility for family, accepting guidance and protection, participating in ceremony, avoiding alcohol, publically expressing that you are out of the gang, wanting legitimate relationships outside gang life, experiencing a native brotherhood, stopping self from reacting like a gangster, and acknowledging the drawbacks of gang violence. -

TRIADS Peter Yam Tat-Wing *
116TH INTERNATIONAL TRAINING COURSE VISITING EXPERTS’ PAPERS TRIADS Peter Yam Tat-wing * I. INTRODUCTION This paper will draw heavily on the experience gained by law enforcement Triad societies are criminal bodies in the HKSAR in tackling the triad organisations and are unlawful under the problem. Emphasis will be placed on anti- Laws of Hong Kong. Triads have become a triad law and Police enforcement tactics. matter of concern not only in Hong Kong, Background knowledge on the structure, but also in other places where there is a beliefs and rituals practised by the triads sizable Chinese community. Triads are is important in order to gain an often described as organized secret understanding of the spread of triads and societies or Chinese Mafia, but these are how triads promote illegal activities by simplistic and inaccurate descriptions. resorting to triad myth. With this in mind Nowadays, triads can more accurately be the paper will examine the following issues: described as criminal gangs who resort to triad myth to promote illegal activities. • History and Development of Triads • Triad Hierarchy and Structure For more than one hundred years triad • Characteristics of Triads activities have been noted in the official law • Differences between Triads, Mafia and police reports of Hong Kong. We have and Yakuza a long history of special Ordinances and • Common Crimes Committed by related legislation to deal with the problem. Triads The first anti-triad legislation was enacted • Current Triad Situation in Hong in 1845. The Hong Kong Special Kong Administrative Region (HKSAR) has, by • Anti-triad Laws in Hong Kong far, the longest history, amongst other • Police Enforcement Strategy jurisdictions, in tackling the problem of • International Cooperation triads and is the only jurisdiction in the world where specific anti-triad law exists. -

CBC Nir Nov 08.Indd
A COMMUNITY FIGHTS GANGS AND GUNS Introduction Two-year-old Asia Saddleback was Descent Into Chaos Focus eating a bowl of soup at her family’s The shooting of The descent of Hobbema into chaos Asia Saddleback on kitchen table when a bullet ripped can be traced to a number of factors: the Samson Cree through the side of her house, striking substance abuse, shattered families, Reserve in Hobbema, her in the stomach. Asia was taken by poverty, unemployment, and the erosion Alberta, thrust the air ambulance to an Edmonton hospital. of Aboriginal traditions to name a few. national spotlight on The bullet hit her kidney and her spine, Couple these socio-economic factors Aboriginal gangs. This but the resilient girl survived—despite with evidence of systemic racism (much News in Review story the fact that doctors were unable to examines the problems of which was revealed in the now in Hobbema as well remove the bullet. Within days, two defunct residential school system that as the gang problem teenage boys, one 15 and one 18, were openly tried to destroy Aboriginal culture across Canada. charged in the drive-by attack. While it over its 100-year history) and it becomes was clear the boys didn’t intend to shoot clear why First Nations communities are Asia, police struggled to find out why in what seems to be a state of perpetual they fired on the house in the first place. crisis. Hobbema appears to be the current The incident horrified people living in epicentre of this crisis, as an array of Hobbema, and soon all of Canada would troubles have hit the town. -

A Massacre in Jamaica
A REPORTER AT LARGE A MASSACRE IN JAMAICA After the United States demanded the extradition of a drug lord, a bloodletting ensued. BY MATTATHIAS SCHWARTZ ost cemeteries replace the illusion were preparing for war with the Jamai- told a friend who was worried about an of life’s permanence with another can state. invasion, “Tivoli is the baddest place in illusion:M the permanence of a name On Sunday, May 23rd, the Jamaican the whole wide world.” carved in stone. Not so May Pen Ceme- police asked every radio and TV station in tery, in Kingston, Jamaica, where bodies the capital to broadcast a warning that n Monday, May 24th, Hinds woke are buried on top of bodies, weeds grow said, in part, “The security forces are ap- to the sound of sporadic gunfire. over the old markers, and time humbles pealing to the law-abiding citizens of FreemanO was gone. Hinds anxiously di- even a rich man’s grave. The most for- Tivoli Gardens and Denham Town who alled his cell phone and reached him at saken burial places lie at the end of a dirt wish to leave those communities to do so.” the house of a friend named Hugh Scully, path that follows a fetid gully across two The police sent buses to the edge of the who lived nearby. Freeman was calm, and bridges and through an open meadow, neighborhood to evacuate residents to Hinds, who had not been outside for far enough south to hear the white noise temporary accommodations. But only a three days, assumed that it was safe to go coming off the harbor and the highway. -

Gang Evidence: Issues for Criminal Defense Susan L
Santa Clara Law Review Volume 30 | Number 3 Article 3 1-1-1990 Gang Evidence: Issues for Criminal Defense Susan L. Burrell Follow this and additional works at: http://digitalcommons.law.scu.edu/lawreview Part of the Law Commons Recommended Citation Susan L. Burrell, Gang Evidence: Issues for Criminal Defense, 30 Santa Clara L. Rev. 739 (1990). Available at: http://digitalcommons.law.scu.edu/lawreview/vol30/iss3/3 This Article is brought to you for free and open access by the Journals at Santa Clara Law Digital Commons. It has been accepted for inclusion in Santa Clara Law Review by an authorized administrator of Santa Clara Law Digital Commons. For more information, please contact [email protected]. GANG EVIDENCE: ISSUES FOR CRIMINAL DEFENSE Susan L. Burrell* It is my belief we don't know a helluva lot about gangs. I don't know what the hell to do about it as a matter of fact. Los Angeles Police Chief Daryl F. Gates' The label "gang-related" has far-reaching ramifications in criminal cases. Gang cases are singled out for investigation and prosecution by special units. At trial, gang affiliation may raise a host of evidentiary problems. At sentencing, evidence of gang membership is sure to affect the court's exercise of discretion. This article will explore the major issues that may arise when gang evidence is presented in a criminal or juve- nile case. The primary focus will be on street gangs, rather than organized crime or prison gangs. I. GANG CASES IN A SOCIETAL CONTEXT Representation of a gang member must begin with an understanding of what gangs are and how society has treated them.