Policy Mechanisms for Increasing Transparency in Electronic Voting
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Open Licensing Toolkit for Staff
Open Licensing Toolkit for Staff The Hewlett Foundation Open Licensing Toolkit for Staff is licensed May 2015 under a Creative Commons Attribution 4.0 International License. Legal Disclaimer: This material is for general informational purposes only and does not represent legal advice as to any particular set of facts; nor does it represent any undertaking to keep recipients advised of any relevant legal developments. Please consult appropriate professional advisors as you deem necessary. The Hewlett Foundation shall not be held responsible for any claims or losses that may arise from any errors or omissions in this document. Hewlett Foundation Open Licensing Toolkit for Staff Table of Contents 1. Hewlett Foundation Commitment to Open Licensing 2. Hewlett Foundation Procedures a. Frequently Asked Questions b. Decision Tree c. Creative Commons License Types d. Guidelines for Marking Openly Licensed Documents 3. Sample Language a. Grantee Communications b. Grant Proposal Template c. Grant Reporting Requirements d. Grant Agreement Letter e. Direct Charitable Activities (DCA) Contract May 2015 Hewlett Foundation Open Licensing Toolkit for Staff Hewlett Foundation Commitment to Open Licensing As part of our commitment to openness and transparency, the Hewlett Foundation has long supported open licensing—an alternative for traditional copyright that allows and encourages sharing of intellectual property. Open licenses, such as those developed by our longtime grantee Creative Commons, protect authors’ rights while giving explicit permission to others to freely use, distribute, and build upon their work. The benefits of open licensing are clear: open licensing increases the chances that good ideas will get a hearing, that others will be able to do something with them, and ultimately that they will have their greatest impact. -

Creative Commons Open Licenses - What Is It All About?
CREATIVE COMMONS OPEN LICENSES - WHAT IS IT ALL ABOUT? Introductory presentation by Paul G. West Creative Commons South African Chapter Lead STATING THE UNNECESSARY This workshop is dedicated to providing a harassment-free experience for everyone regardless of gender, gender identity and expression, sexual orientation, disability, physical appearance, body size, race, age or religion. We do not tolerate harassment of participants or facilitators in any form. Sexual language and imagery is not appropriate, including in any online platform that may be used. AND IT IS IMPORTANT TO ADD THAT . • Nothing in this workshop should be construed as legal advice! • We will be talking about an interesting range of topics that touch on copyright, fair use and open licensing. • We will together learn more about copyright, open licensing and open practices in various communities. • Upon completion, you should feel a little more comfortable sharing facts about copyright and open licensing and good open practices. • I am NOT a lawyer – I am a supporter of Open Educational Resources (OER) and Creative Commons (CC) open licenses. THE STORY DOES NOT START IN 2002 UNESCO Forum on the Impact of Open Courseware for Higher Education in Developing Countries https://unesdoc.unesco.org/ark:/48223/pf0000181682 ORIGINS OF OER CREATION OF A MOVEMENT Larry Lessig and others founded the Creative Commons 2001 Charles M. Vest speaks of a meta-university 2007 a transcendent, accessible, empowering, dynamic, communally constructed framework of open materials and platforms -
Surveymonkey Analyze
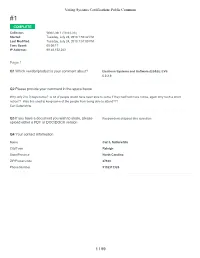
Voting Systems Certification: Public Comment #1 COMPLETE Collector: Web Link 1 (Web Link) Started: Tuesday, July 24, 2018 1:50:42 PM Last Modified: Tuesday, July 24, 2018 1:57:00 PM Time Spent: 00:06:17 IP Address: 99.46.152.243 Page 1 Q1 Which vendor/product is your comment about? Elections Systems and Software (ES&S): EVS 5.2.2.0 Q2 Please provide your comment in the space below Why only 2 to 3 days notice? A lot of people would have been able to come if they had had more notice, again why such a short notice?? Was this used to keep some of the people from being able to attend??? Carl Satterwhite Q3 If you have a document you wish to share, please Respondent skipped this question upload either a PDF or DOC/DOCX version Q4 Your contact information Name Carl L Satterwhite City/Town Raleigh State/Province North Carolina ZIP/Postal Code 27610 Phone Number 9192313328 1 / 59 Voting Systems Certification: Public Comment #2 COMPLETE Collector: Web Link 1 (Web Link) Started: Tuesday, July 24, 2018 2:01:57 PM Last Modified: Tuesday, July 24, 2018 2:04:52 PM Time Spent: 00:02:54 IP Address: 76.182.31.92 Page 1 Q1 Which vendor/product is your comment about? All Q2 Please provide your comment in the space below I would be very interested in attending, but I have to take my husband to an appointment at the VA Hospital. Q3 If you have a document you wish to share, please Respondent skipped this question upload either a PDF or DOC/DOCX version Q4 Your contact information Name Pauline Hoffmann City/Town Raleigh State/Province NC ZIP/Postal Code 27613 Country USA Email Address [email protected] 2 / 59 Voting Systems Certification: Public Comment #3 COMPLETE Collector: Web Link 1 (Web Link) Started: Wednesday, July 25, 2018 12:16:23 PM Last Modified: Wednesday, July 25, 2018 12:20:56 PM Time Spent: 00:04:32 IP Address: 99.173.129.35 Page 1 Q1 Which vendor/product is your comment about? All Q2 Please provide your comment in the space below You must include a paper ballot back up. -

Introductory Lecture & FLOSS
Introductory Lecture & FLOSS Lecture 1 TU Wien, 193.067 Free and Open Technologies (WS 2019/2020) Christoph Derndorfer and Lukas F. Lang This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. Introduction Organization ● Lectures: ○ Weekly lecture to cover course materials (until Christmas) ○ Lectures take place on Tuesdays, 17:00–19:00, Argentinierstraße 8, Seminarraum/Bibliothek 194-05 ○ Attendance is mandatory ● Group project: ○ In groups of 4 students ○ 3 meetings with lecturers during the semester (week 44/2019, week 48/2019, week 2/2020) ○ Final presentations at the end of January (week 4/2020) ● Final paper: ○ In groups of 2 students ○ Final presentations at the end of January (week 5/2020) ○ Deadline: Sunday, February 9, 2020, 23:59 CET (no exceptions!) Organization ● Grading: ○ 50% group project ○ 35% seminar paper ○ 15% participation during lectures ○ All course components need to be passed in order to pass the overall course! ● Course materials: ○ Will be provided at https://free-and-open-technologies.github.io ● For further questions: ○ Email [email protected] and [email protected] Lecture outline 1. FLOSS (Free/Libre and Open Source Software) 2. Open Hardware 3. Open Data 4. Open Content/Open Educational Resources 5. Open Science/Research 6. Open Access 7. Open Spaces/Open Practices: Metalab Vienna 8. Guest Lecture: Stefanie Wuschitz (Mz* Baltazar’s Lab) Group project ● Goal: ○ Extend, contribute to, or create a new open project within scope of lecture topics ● Choose topic from a list (see course website) or (even better) suggest your own: ○ Groups of 4 students ○ Send a 1-page proposal until Friday, October 25, via email to both lecturers ■ Define the idea, goal, (potential) impact, requirements, and estimated effort ■ State deliverables (should be broken down into three milestones to discuss in meetings) ● Requirements: ○ Open and accessible (Git repository, openly licensed) → others can access/use/study/extend ○ Use time sheet to track and compare estimated vs. -

Translate's Localization Guide
Translate’s Localization Guide Release 0.9.0 Translate Jun 26, 2020 Contents 1 Localisation Guide 1 2 Glossary 191 3 Language Information 195 i ii CHAPTER 1 Localisation Guide The general aim of this document is not to replace other well written works but to draw them together. So for instance the section on projects contains information that should help you get started and point you to the documents that are often hard to find. The section of translation should provide a general enough overview of common mistakes and pitfalls. We have found the localisation community very fragmented and hope that through this document we can bring people together and unify information that is out there but in many many different places. The one section that we feel is unique is the guide to developers – they make assumptions about localisation without fully understanding the implications, we complain but honestly there is not one place that can help give a developer and overview of what is needed from them, we hope that the developer section goes a long way to solving that issue. 1.1 Purpose The purpose of this document is to provide one reference for localisers. You will find lots of information on localising and packaging on the web but not a single resource that can guide you. Most of the information is also domain specific ie it addresses KDE, Mozilla, etc. We hope that this is more general. This document also goes beyond the technical aspects of localisation which seems to be the domain of other lo- calisation documents. -

The Copyleft Movement: Creative Commons Licensing
Centre for the Study of Communication and Culture Volume 26 (2007) No. 3 IN THIS ISSUE The Copyleft Movement: Creative Commons Licensing Sharee L. Broussard, MS APR Spring Hill College AQUARTERLY REVIEW OF COMMUNICATION RESEARCH ISSN: 0144-4646 Communication Research Trends Table of Contents Volume 26 (2007) Number 3 http://cscc.scu.edu The Copyleft Movement:Creative Commons Licensing Published four times a year by the Centre for the Study of Communication and Culture (CSCC), sponsored by the 1. Introduction . 3 California Province of the Society of Jesus. 2. Copyright . 3 Copyright 2007. ISSN 0144-4646 3. Protection Activity . 6 4. DRM . 7 Editor: William E. Biernatzki, S.J. 5. Copyleft . 7 Managing Editor: Paul A. Soukup, S.J. 6. Creative Commons . 8 Editorial assistant: Yocupitzia Oseguera 7. Internet Practices Encouraging Creative Commons . 11 Subscription: 8. Pros and Cons . 12 Annual subscription (Vol. 26) US$50 9. Discussion and Conclusion . 13 Payment by check, MasterCard, Visa or US$ preferred. Editor’s Afterword . 14 For payments by MasterCard or Visa, send full account number, expiration date, name on account, and signature. References . 15 Checks and/or International Money Orders (drawn on Book Reviews . 17 USA banks; for non-USA banks, add $10 for handling) should be made payable to Communication Research Journal Report . 37 Trends and sent to the managing editor Paul A. Soukup, S.J. Communication Department In Memoriam Santa Clara University Michael Traber . 41 500 El Camino Real James Halloran . 43 Santa Clara, CA 95053 USA Transfer by wire: Contact the managing editor. Add $10 for handling. Address all correspondence to the managing editor at the address shown above. -

Elements of Free and Open Source Licenses: Features That Define Strategy
Elements Of Free And Open Source Licenses: Features That Define Strategy CAN: Use/reproduce: Ability to use, copy / reproduce the work freely in unlimited quantities Distribute: Ability to distribute the work to third parties freely, in unlimited quantities Modify/merge: Ability to modify / combine the work with others and create derivatives Sublicense: Ability to license the work, including possible modifications (without changing the license if it is copyleft or share alike) Commercial use: Ability to make use of the work for commercial purpose or to license it for a fee Use patents: Rights to practice patent claims of the software owner and of the contributors to the code, in so far these rights are necessary to make full use of the software Place warranty: Ability to place additional warranty, services or rights on the software licensed (without holding the software owner and other contributors liable for it) MUST: Incl. Copyright: Describes whether the original copyright and attribution marks must be retained Royalty free: In case a fee (i.e. contribution, lump sum) is requested from recipients, it cannot be royalties (depending on the use) State changes: Source code modifications (author, why, beginning, end) must be documented Disclose source: The source code must be publicly available Copyleft/Share alike: In case of (re-) distribution of the work or its derivatives, the same license must be used/granted: no re-licensing. Lesser copyleft: While the work itself is copyleft, derivatives produced by the normal use of the work are not and could be covered by any other license SaaS/network: Distribution includes providing access to the work (to its functionalities) through a network, online, from the cloud, as a service Include license: Include the full text of the license in the modified software. -

Linux Online Virtual Environments in Teaching Operating Systems
Linux Online Virtual Environments in Teaching Operating Systems Olena Holovnia[0000-0003-0095-7585] Zhytomyr Polytechnic State University, 103, Chudnivska str., Zhytomyr, 10005, Ukraine [email protected] Abstract. The article provides an overview of Linux ready-made online environments based on various virtualization technologies. Linux ready-made online virtual environments are systematized, the advantages and disadvantages of considering groups of online virtual environments are listed. The work also gives the comparison of standalone online Unix/Linux terminals in terms of their possible use for a course in operating systems. The author analyzes the experience of teaching a Linux operating system to students of different specializations, and in particular, discusses the virtualization tools used, including Linux online environments (Amazon EC2, Cloud 9, a virtual machine for NDG Linux Essentials course). The study states the need for developing an individually designed system to provide Linux online virtual environments and elaborates the requirements to this system. The work also discusses potential challenges which the developers of Linux online virtual environments for teaching operating systems may face, including the problem of finding a balance between availability and stability of virtual environments on the one hand and the realism of students’ learning experience on the other hand. Keywords: virtualization, Linux, operating systems. 1 Introduction A course in operating systems (OS) usually includes practical assignments on Unix- like operating systems (particularly, Linux). However, at the same time, university lab computers, students’ laptops and home desktop computers mostly come with Windows installation. That is one important reason why different virtualization technologies are often used for a course in operating systems. -

Finding Images for Manipulation
D003x.1: Applications of Linear Algebra, Part 1 Davidson College Library Finding Images for Manipulation Finding an image to use for your image manipulation project sounds easy, right? It can be, but you have to keep in mind that copyright laws restrict what you can use. Many of the images you’ll find in Google Images are protected by copyright. This guide is designed to help you find images you can use for your image manipulation project. Why Can’t I Just Use Any Image I Want? So, How Do I Find Images I Can Use? What If The Image I Want To Use Is Protected By Copyright? How Do I Give Credit? What Resources Can I Use To Find Images? Why Can’t I Just Use Any Image I Want? In the United States, most things created today have automatic copyright protection. This means that many of the images you find online cannot be used without permission from the owner. A good rule of thumb when searching for images is to assume that anything you find is copyrighted, unless it expressly says it is not. So, How Do I Find Images I Can Use? Although many images are protected by copyright, not all of them are. In addition, some copyrighted works have licenses that let you use them. When you find an image you like, look for information about the image that will tell you if you can use it for your manipulation project. Two types of images to look for are: Public Domain Images Images with a Creative Commons License Public Domain Images Works with an expired copyright are in the public domain, which means you can use them without permission from the creator. -

Made with Creative Commons MADE with CREATIVE COMMONS
ii Made With Creative Commons MADE WITH CREATIVE COMMONS PAUL STACEY AND SARAH HINCHLIFF PEARSON Made With Creative Commons iii Made With Creative Commons by Paul Stacey & Sarah Hinchliff Pearson © 2017, by Creative Commons. Published under a Creative Commons Attribution-ShareAlike license (CC BY-SA), version 4.0. ISBN 978-87-998733-3-3 Cover and interior design by Klaus Nielsen, vinterstille.dk Content editing by Grace Yaginuma Illustrations by Bryan Mathers, bryanmathers.com Downloadable e-book available at madewith.cc Publisher: Ctrl+Alt+Delete Books Husumgade 10, 5. 2200 Copenhagen N Denmark www.cadb.dk [email protected] Printer: Drukarnia POZKAL Spółka z o.o. Spółka komandytowa 88-100 Inowrocław, ul. Cegielna 10/12, Poland This book is published under a CC BY-SA license, which means that you can copy, redistribute, remix, transform, and build upon the content for any purpose, even commercially, as long as you give appropriate credit, provide a link to the license, and indicate if changes were made. If you remix, transform, or build upon the material, you must distribute your contributions under the same license as the original. License details: creativecommons.org/licenses/by-sa/4.0/ Made With Creative Commons is published with the kind support of Creative Commons and backers of our crowdfunding-campaign on the Kickstarter.com platform. iv Made With Creative Commons “I don’t know a whole lot about non- fiction journalism. The way that I think about these things, and in terms of what I can do is. essays like this are occasions to watch somebody reason- ably bright but also reasonably average pay far closer attention and think at far more length about all sorts of different stuff than most of us have a chance to in our daily lives.” - DAVID FOSTER WALLACE Made With Creative Commons v vi Made With Creative Commons CONTENTS Foreword xi Introduction xv PART 1: THE BIG PICTURE 1 The New World of Digital Commons by Paul Stacey 3 The Commons, the Market, and the State . -

Six Licenses for Sharing Your Work
Creative Commons makes sharing easy The internet makes it easy for people to Our free, easy-to-use licenses provide a simple, standardized share and build on each other’s creations. But way to give the public permission to share and use your creative sometimes the law makes it hard. work — on conditions of your choosing. CC licenses let you easily change your copyright terms from “all rights reserved” to Whenever you snap a photograph, record a “some rights reserved.” song, publish an article, or put your original Creative Commons licenses are not an alternative to copyright. Six licenses writing online, that work is automatically By default, copyright allows only limited reuses without your considered “all rights reserved” in the eyes of permission. CC licenses let you grant additional permissions copyright law. to the public, allowing reuse on the terms best suited to your needs while reserving some rights for yourself. for sharing In many cases, that means that other people We’ve collaborated with copyright experts around the world to can’t reuse or remix your work without asking ensure that our licenses work globally. for your permission first. your work If you are looking for content that you can freely and legally But what if you want others to reuse your work? use, there is a wealth of CC-licensed creativity available to you. There are hundreds of millions of works—from songs and videos to scientific and academic material—available to the public for If you want to give people the right to share, use, and even free and legal use under the terms of our licenses, with more build upon a work you’ve created, consider publishing under being contributed every day. -

About the Licenses - Creative Commons
About The Licenses - Creative Commons About Licenses Public Domain Support CC Projects Blog News Keep the internet creative, free and open. Donate to Creative Commons About The Licenses Wanna Work What our licenses do Together? The Creative Commons copyright licenses and tools forge from Creative Commons a balance inside the traditional “all rights reserved” setting that copyright law creates. Our tools give everyone from individual creators to large companies and institutions a What’s going on simple, standardized way to grant copyright permissions to their creative work. The combination of our tools and here? our users is a vast and growing digital commons, a pool Your browser doesn’t support our full player of content that can be copied, distributed, edited, remixed, and built upon, all within the boundaries of copyright law. License design and rationale All Creative Commons licenses have many important Our licenses do not affect freedoms that the law grants to features in common. Every license helps creators — we users of creative works otherwise protected by copyright, call them licensors if they use our tools — retain copyright such as exceptions and limitations to copyright law like while allowing others to copy, distribute, and make some fair dealing. Creative Commons licenses require uses of their work — at least non-commercially. Every licensees to get permission to do any of the things with a Creative Commons license also ensures licensors get the work that the law reserves exclusively to a licensor and credit for their work they deserve. Every Creative that the license does not expressly allow. Licensees must Commons license works around the world and lasts as credit the licensor, keep copyright notices intact on all long as applicable copyright lasts (because they are built copies of the work, and link to the license from copies of on copyright).