Cryptanalysis of SIGABA Wing Chan San Jose State University
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Polish Mathematicians Finding Patterns in Enigma Messages
Fall 2006 Chris Christensen MAT/CSC 483 Machine Ciphers Polyalphabetic ciphers are good ways to destroy the usefulness of frequency analysis. Implementation can be a problem, however. The key to a polyalphabetic cipher specifies the order of the ciphers that will be used during encryption. Ideally there would be as many ciphers as there are letters in the plaintext message and the ordering of the ciphers would be random – an one-time pad. More commonly, some rotation among a small number of ciphers is prescribed. But, rotating among a small number of ciphers leads to a period, which a cryptanalyst can exploit. Rotating among a “large” number of ciphers might work, but that is hard to do by hand – there is a high probability of encryption errors. Maybe, a machine. During World War II, all the Allied and Axis countries used machine ciphers. The United States had SIGABA, Britain had TypeX, Japan had “Purple,” and Germany (and Italy) had Enigma. SIGABA http://en.wikipedia.org/wiki/SIGABA 1 A TypeX machine at Bletchley Park. 2 From the 1920s until the 1970s, cryptology was dominated by machine ciphers. What the machine ciphers typically did was provide a mechanical way to rotate among a large number of ciphers. The rotation was not random, but the large number of ciphers that were available could prevent depth from occurring within messages and (if the machines were used properly) among messages. We will examine Enigma, which was broken by Polish mathematicians in the 1930s and by the British during World War II. The Japanese Purple machine, which was used to transmit diplomatic messages, was broken by William Friedman’s cryptanalysts. -
Work Load of the Maintenance Branch
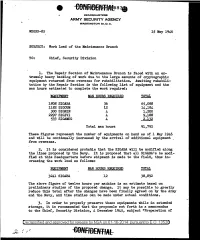
HEADQUARTERS ARMY SECURITY AGENCY WASHINGTON 25, D. C. WDGSS-85 15 May 1946 SUBJECT: Work Load of the Maintenance Branch TO: Chief, Security Division 1. The Repair Section of Maintenance Branch is .faced with an ex tremely heavy backlog of' work due to the large amounts of' cryptographic equipment returned from overseas for rehabilitation. Awaiting rehabili tation by the Repair Section is the followi~g list of equipment and the man hours estimated to complete the work required.: EQUIPMENT MAN HOURS REQUIRED TOTAL 1808 SIGABA 36 65,088 1182 SIGCUM 12 14,184 300 SIGNIN 4 1,200 2297 SIGIVI 4 9,188 533 SIGAMUG 4, 2,132 Total man hours 91,792 These figures represent the number of equipments on hand as of 1 May 1946 and will be continually increased by the arrival of additional equipment . from overseas. 2. It is considered probable that the SIGABA will be modified along the lines proposed by the Navy. It is proposed that all SIGABA 1s be modi fied at this Headquarters before shipment is made to the field, thus in creasing the work load as follows: EQUIPMENT MAN HOURS REQUIRED 3241 SIGABA 12 The above figure of' twelve hours per machine is an estimate based on preliminary studies of' the proposed change. It may be possible to greatly reduce this total af'ter the changes have been f inaJ.ly agreed on by the .Army and the Navy, and time studies can be made under actual conditions. ,3. In order to properly preserve these equipments while in extended storage, it is recommended that the proposals set .forth in a memorandum to the Chief, Security Division, 4 December 1945, subject "Preparation of Declassified and approved for release by NSA on 01-16-2014 pursuantto E .0. -

SIS and Cipher Machines: 1930 – 1940
SIS and Cipher Machines: 1930 – 1940 John F Dooley Knox College Presented at the 14th Biennial NSA CCH History Symposium, October 2013 This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 United States License. 1 Thursday, November 7, 2013 1 The Results of Friedman’s Training • The initial training regimen as it related to cipher machines was cryptanalytic • But this detailed analysis of the different machine types informed the team’s cryptographic imaginations when it came to creating their own machines 2 Thursday, November 7, 2013 2 The Machines • Wheatstone/Plett Machine • M-94 • AT&T machine • M-138 and M-138-A • Hebern cipher machine • M-209 • Kryha • Red • IT&T (Parker Hitt) • Purple • Engima • SIGABA (M-134 and M-134-C) • B-211(and B-21) 3 Thursday, November 7, 2013 3 The Wheatstone/Plett Machine • polyalphabetic cipher disk with gearing mechanism rotates the inner alphabet. • Plett’s improvement is to add a second key and mixed alphabet to the inner ring. • Friedman broke this in 1918 Principles: (a) The inner workings of a mechanical cryptographic device can be worked out using a paper and pencil analog of the device. (b) if there is a cycle in the mechanical device (say for particular cipher alphabets), then that cycle can be discovered by analysis of the paper and pencil analog. 4 Thursday, November 7, 2013 4 The Army M-94 • Traces its roots back to Jefferson and Bazieres • Used by US Army from 1922 to circa 1942 • 25 mixed alphabets. Disk order is the key. -

A Complete Bibliography of Publications in Cryptologia
A Complete Bibliography of Publications in Cryptologia Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 04 September 2021 Version 3.64 Title word cross-reference 10016-8810 [?, ?]. 1221 [?]. 125 [?]. 15.00/$23.60.0 [?]. 15th [?, ?]. 16th [?]. 17-18 [?]. 18 [?]. 180-4 [?]. 1812 [?]. 18th (t; m)[?]. (t; n)[?, ?]. $10.00 [?]. $12.00 [?, ?, ?, ?, ?]. 18th-Century [?]. 1930s [?]. [?]. 128 [?]. $139.99 [?]. $15.00 [?]. $16.95 1939 [?]. 1940 [?, ?]. 1940s [?]. 1941 [?]. [?]. $16.96 [?]. $18.95 [?]. $24.00 [?]. 1942 [?]. 1943 [?]. 1945 [?, ?, ?, ?, ?]. $24.00/$34 [?]. $24.95 [?, ?]. $26.95 [?]. 1946 [?, ?]. 1950s [?]. 1970s [?]. 1980s [?]. $29.95 [?]. $30.95 [?]. $39 [?]. $43.39 [?]. 1989 [?]. 19th [?, ?]. $45.00 [?]. $5.95 [?]. $54.00 [?]. $54.95 [?]. $54.99 [?]. $6.50 [?]. $6.95 [?]. $69.00 2 [?, ?]. 200/220 [?]. 2000 [?]. 2004 [?, ?]. [?]. $69.95 [?]. $75.00 [?]. $89.95 [?]. th 2008 [?]. 2009 [?]. 2011 [?]. 2013 [?, ?]. [?]. A [?]. A3 [?, ?]. χ [?]. H [?]. k [?, ?]. M 2014 [?]. 2017 [?]. 2019 [?]. 20755-6886 [?, ?]. M 3 [?]. n [?, ?, ?]. [?]. 209 [?, ?, ?, ?, ?, ?]. 20th [?]. 21 [?]. 22 [?]. 220 [?]. 24-Hour [?, ?, ?]. 25 [?, ?]. -Bit [?]. -out-of- [?, ?]. -tests [?]. 25.00/$39.30 [?]. 25.00/839.30 [?]. 25A1 [?]. 25B [?]. 26 [?, ?]. 28147 [?]. 28147-89 000 [?]. 01Q [?, ?]. [?]. 285 [?]. 294 [?]. 2in [?, ?]. 2nd [?, ?, ?, ?]. 1 [?, ?, ?, ?]. 1-4398-1763-4 [?]. 1/2in [?, ?]. 10 [?]. 100 [?]. 10011-4211 [?]. 3 [?, ?, ?, ?]. 3/4in [?, ?]. 30 [?]. 310 1 2 [?, ?, ?, ?, ?, ?, ?]. 312 [?]. 325 [?]. 3336 [?, ?, ?, ?, ?, ?]. affine [?]. [?]. 35 [?]. 36 [?]. 3rd [?]. Afluisterstation [?, ?]. After [?]. Aftermath [?]. Again [?, ?]. Against 4 [?]. 40 [?]. 44 [?]. 45 [?]. 45th [?]. 47 [?]. [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. Age 4in [?, ?]. [?, ?]. Agencies [?]. Agency [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. -

George Lasry: Modern Cryptanalysis of Historical Ciphers
Modern Cryptanalysis of Historical Ciphers November 1, 2019 George Lasry Agenda • Introduction – Motivation – Difficulty – Generic approaches • Case studies – Hagelin M-209 – Playfair – Double transposition – SIGABA George Lasry 2 Agenda • Introduction – Motivation – Difficulty – Generic approaches • Case studies – Hagelin M-209 – Playfair – Double transposition – SIGABA George Lasry 3 Motivation • Historical cryptanalysis • Undecrypted texts • Public challenges • Fun George Lasry 4 Difficulty - Factors • System design – Diffusion – Confusion – Weaknesses • Key – Key space/length • Ciphertext – Length – Language George Lasry 5 Difficulty Easy Moderate Hard Very hard Intractable? Monoalphabetic Playfair Playfair Playfair Fialka substitution (long ciphertext) (short ciphertext) (very short) Transposition Transposition ADFGVX Double transposition Double transposition (short key) (long key) (long random key) Vigenere Enigma Enigma SIGABA (long ciphertext) (short ciphertext) (known plaintext) Hagelin M-209 Hagelin M-209 (long ciphertext) (short ciphertext) Hagelin M-209 Sturgeon T52 Sturgeon T52 (known plaintext) (regular stepping) (irregular stepping) George Lasry 6 Generic Approaches - 1 Exhaustive Combinatorial Stochastic Search Search Search ● Simple brute force ● Backtracking ● Hill climbing ● Dictionary search ● Meet in the Middle ● Simulated annealing (MITM) ● Hybrid (e.g., nested) ● Match some ● Others (e.g., genetic constraints (e.g., ● Match some algorithms) known plaintext) constraints ● Or optimize a scoring ● Optimize a fitness -

Scamp Iv, Lecture V; History of the Invention And
REF ID:A38396 r I LECTURE V HISTORY OF THE INVENTION AND DEVELOHllENT OF CIPHER DEVICES AND MACHI.NF.$. Three or four years ago I was asked to give a lecture before the Communica- tions-Electronics Division of the Air University, USAF, on the subject of communications security (COMSEC). About that time there was 'hP r "o:s..ui.i.ered into our ears over the radio a slogan concerned wi+~ ~oile traffic safety rules • ..... ThE" o1iugta.n." was: "Don't learn your traffic laws by accident!" I thought the slogan useful. as the title of my talk but l modified it a little: "Don't learn your COMSEC laws by accident•" I began my talk by reading Webster's definition of the word accident. I know, of course, that this group here today is not concerned particularly with COMSEC duties of any sort. But the definition of the word accident will nevertheless be of interest 11l connection with what will be said in a moment or two, so I'll read Webster's definition if you'll bear with me. Webster: "Acc:ulent" - literally, a be:talling. ~ '\ a. An event that takes place without one's foresight or expectation, ) '\;r an undesigned, sudden, and unexpected event. @'pp roved for Release by NSA on 10-10-2013 pursuantto E .0. 1352a REF ID:A38396 b Hence, often, an undesigned and unforeseen occurrence of an afflictive or unfortunate character, a llll.Shap resulting in injury to a person or damage to a thing, a casualty, as to die by an accident Having defined the word, I'll now proceed by relating an interesting, minor, but nevertheless quite important episode of the war in the Pacific Theatre during WWII, and I will introduce the acrount of that episode by saying that: During the W'lr, the President of the United States, Chief of' Sta.ff of the Ar1ff3' 1 the Commander-in-Chief' of the U.S. -

Part I History and Machines of Cryptography
Part I History and machines of cryptography CHAPTER 14: MACHINES and HISTORY of CRYPTOGRAPHY MACHINES and HISTORY of CRYPTOGRAPHY IV054 1. History and machines of cryptography 2/78 PROLOGUE PROLOGUE IV054 1. History and machines of cryptography 3/78 WHAT to VALUE MORE As information becomes an increasingly valuable commodity, the encryption is the only way to protect our privacy and guarantee the success of the e-business. Some groups, for example businessmen and civil libertarians, require strong cryptography. The forces of law and order are pressing governments to restrict the use of cryptography. What to value more? Personal freedom? or the order and law? IV054 1. History and machines of cryptography 4/78 WHO are CODEBREAKERS The vision of codebreakers has changed through the history, depending on the tools used for encryption and cryptanalysis. Before computer era views; Codebreakers or cryptanalysts are linguistic alchemists, a mystical tribe attempting to conjure sensible words out of meaningless symbols. Current view: Codebreakers and cryptanalyst's are artists that can superbly use modern mathematics, informatics and computing super-technology. Three views of the history First World War was the war of chemists (deadly gases). Second World War was the war of physicists (atomic bombs) Third World War would be the war of informaticians (cryptographers and cryptanalysts). IV054 1. History and machines of cryptography 5/78 PERIODS of the HISTORY of CRYPTOGRAPHY Prehistory - before nontrivial machines period: till about 1930 - no electrical -

Cryptanalysis of the SIGABA
UNIVERSITY OF CALIFORNIA Santa Barbara Cryptanalysis of the SIGABA A Thesis submitted in partial satisfaction of the requirements for the degree Master of Science in Computer Science by Michael Lee Committee in charge: Professor Alan G. Konheim, Chair Professor Richard A. Kemmerer Professor Giovanni Vigna June 2003 The Thesis of Michael Lee is approved. Richard A. Kemmerer Giovanni Vigna Alan G. Konheim, Committee Chair June 2003 Cryptanalysis of the SIGABA Copyright c 2003 by Michael Lee iii ABSTRACT Cryptanalysis of the SIGABA by Michael Lee The SIGABA is a rotor-based cryptosystem developed by the United States for use during World War II. Its history has been shrouded in secrecy, with the result that few people know of its significance in securing American communica- tions during and after World War II. SIGABA’s operational details were finally declassified in 1996, and the patent for its design was granted in 2001, more than 50 years after it was filed. In this thesis I present a generic model of rotor-based cryptosystems that represents a machine at least as difficult to break as the SIGABA. I present tech- niques that can be used for full plaintext recovery on a cryptosystem using one to three rotors, and I show how these techniques can be extended to systems using more rotors. These attacks compromise not only the generic model, but also the SIGABA and related cryptosystems. Keywords: rotor machines, cryptanalysis, cribbing, SIGABA, ECM Mark II, CSP-889, M-134-C. iv Contents List of Figures vii List of Tables viii 1 Introduction 1 2 Rotors 3 2.1 Rotor Construction . -

An Analysis of Factors That Have Influenced the Ve Olution of Information Assurance from World War I Through Vietnam to the Present
Air Force Institute of Technology AFIT Scholar Theses and Dissertations Student Graduate Works 3-17-2004 An Analysis of Factors That Have Influenced the vE olution of Information Assurance from World War I through Vietnam to the Present Kelvin B. Scott Follow this and additional works at: https://scholar.afit.edu/etd Part of the Management Information Systems Commons Recommended Citation Scott, Kelvin B., "An Analysis of Factors That Have Influenced the vE olution of Information Assurance from World War I through Vietnam to the Present" (2004). Theses and Dissertations. 4102. https://scholar.afit.edu/etd/4102 This Thesis is brought to you for free and open access by the Student Graduate Works at AFIT Scholar. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of AFIT Scholar. For more information, please contact [email protected]. AN ANALYSIS OF FACTORS THAT HAVE INFLUENCED THE EVOLUTION OF INFORMATION ASSURANCE FROM WORLD WAR I THROUGH VIETNAM TO THE PRESENT THESIS Kelvin B. Scott, Gunnery Sergeant, USMC AFIT/GIR/ENV/04M-22 DEPARTMENT OF THE AIR FORCE AIR UNIVERSITY AIR FORCE INSTITUTE OF TECHNOLOGY Wright-Patterson Air Force Base, Ohio APPROVED FOR PUBLIC RELEASE; DISTRIBUTION UNLIMITED The views expressed in this thesis are those of the author and do not reflect the official policy or position of the United States Marine Corps, United States Air Force, Department of Defense, or the United States Government. AFIT/GIR/ENV/04M-22 AN ANALYSIS OF FACTORS THAT HAVE INFLUENCED THE EVOLUTION OF INFORMATION ASSURANCE FROM WORLD WAR I THROUGH VIETNAM TO THE PRESENT THESIS Presented to the Faculty Department of Systems and Engineering Management Graduate School of Engineering and Management Air Force Institute of Technology Air University Air Education and Training Command In Partial Fulfillment of the Requirements for the Degree of Master of Science in Information Resource Management Kelvin B. -

A Methodology for the Cryptanalysis of Classical Ciphers with Search
phers with Search Metaheuristics George Lasry A Methodology for the Cryptanalysis of A Methodology for the Cryptanalysis of Classical Ci Classical Ciphers with Search Metaheuristics ISBN 978-3-7376-0458-1 kassel university 9 783737 604581 George Lasry press kassel kassel university press !"# $ % !&' (&)) )*) # + ,)&) - .# +,)/ & + 0123405 / ! & ' & ' & ' 6 # 7 + ))) 8)+$ 9"#)9& )3405 7/':5;.<.5<51.4=>;.0(* 7/':5;.<.5<51.4=>:.;(.* &27++ ?)! ) 04)0:300 $",:5;<5<514=>:; "@'++ . #) +++4443.=4=>:3 '340;9 # !B9$ ) ). ) ,! “After climbing a great hill, one only finds that there are many more hills to climb.” Nelson Mandela Abstract Cryptography, the art and science of creating secret codes, and cryptanalysis, the art and science of breaking secret codes, underwent a similar and parallel course during history. Both fields evolved from manual encryption methods and manual codebreaking techniques, to cipher ma- chines and codebreaking machines in the first half of the 20th century, and finally to computer- based encryption and cryptanalysis from the second half of the 20th century. However, despite the advent of modern computing technology, some of the more challenging classical cipher systems and machines have not yet been successfully cryptanalyzed. For others, cryptanalytic methods exist, but only for special and advantageous cases, such as when large amounts of ciphertext are available. Starting from the 1990s, local search metaheuristics such as hill climbing, genetic algorithms, and simulated annealing have been employed, and in some cases, successfully, for the cryptanal- ysis of several classical ciphers. In most cases, however, results were mixed, and the application of such methods rather limited in their scope and performance. In this work, a robust framework and methodology for the cryptanalysis of classical ciphers using local search metaheuristics, mainly hill climbing and simulated annealing, is described. -

Rob Rice FYWS Cryptography 2 November 2010 the M-209 Cipher
Rob Rice FYWS Cryptography 2 November 2010 The M-209 Cipher Machine What does a person beg to have, but then immediately want to give away? The answer is a secret. In our daily lives, most of us only deal with minor, personal secrets that rarely have drastic consequences if leaked. But what about secrets concerning matters of national security? Even a small secret can be a powerful thing in the hands of the enemy, especially in times of war. In war, having a secure method of communication is invaluable. Knowing the enemy’s next move is a nearly insurmountable advantage, while being unable to shield communications from the enemy could prove fatal. The quality of a nation’s cryptography can be the difference between winning and losing a war. World War II provides some of the best examples of the monumental power of cryptography. The success of cryptanalysts at Bletchley Park in deciphering Enigma-enciphered messages prevented Germany from dominating naval combat on the Atlantic Ocean. American cryptanalysts gave U.S. forces the element of surprise at the Battle of Midway by deciphering a message enciphered using Purple, the Japanese cipher machine. 1 The Allies depended on deciphered German messages regarding troop positions along the French coast to form their invasion plans for D-Day.2 The importance of ciphers in the Second World War is indisputable. However, to fully appreciate a good cipher, one must understand its history and the way it works. This is certainly the case for the M-209, a cipher machine used by the U.S. -

States of a Rotor Machine
Rotor Machines Klaus Pommerening Fachbereich Physik, Mathematik, Informatik der Johannes-Gutenberg-Universit¨at Saarstraße 21 D-55099 Mainz December 3, 1999|English version November 9, 2013|last change January 19, 2021 1 K. Pommerening, Rotor Machines 2 1 One-Rotor Ciphers See the web page http://www.staff.uni-mainz.de/pommeren/Cryptology /Classic/5 Rotor/OneRotor.html K. Pommerening, Rotor Machines 3 2 Mathematical Description of Rotors Identify the alphabet Σ with Z=nZ, the integers mod n. Let ρ be the monoal- phabetic substitution that the rotor performs in its initial position. Moving the rotor by one position forward the new substitution is ρ(1)(a) = ρ(a − 1) + 1 Denote by τ the shift by 1 of the alphabet Σ = Z=nZ, that is τ(a) = a + 1. Then the formula looks like this: ρ(1)(a) = τρτ −1(a) By induction we immediately get part (i) of the following theorem: Theorem 1 (The secondary alphabets of a rotor) (i) If a rotor in its initial position performs the substitution with the pri- mary alphabet ρ, then after rotation by t positions forward it performs the substitution with the conjugate alphabet ρ(t) = τ tρτ −t. In particular all secondary alphabets have the same cycle type. (ii) The diagonals of the corresponding alphabet table each contain the standard alphabet (cyclically wrapped around). Proof. Assertion (i) is proved above. Assertion (ii) follows immediately by interpreting it as a formula: ρ(i)(j) = τ iρτ −i(j) = ρ(j − i) + i = ρ(i−1)(j − 1) + 1 3 The definition of \cycle type" was given in Appendix A.