Rob Rice FYWS Cryptography 2 November 2010 the M-209 Cipher
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Hagelin) by Williaj-1 F
.. REF ID :A2436259 Declassified and approved for release by NSA on 07-22 2014 pursuant to E.O. 1352e REF ID:A2436259 '!'UP SECRE'l' REPORT"OF.VISIT 1Q. CRYPTO A.G. (HAGELIN) BY WILLIAJ-1 F. FRIEDI.W.if SPECIAL ASSISTANT TO THE DIRECTOR, NATIONAL SECURITY AGENCY 21 - 28 FEBRUARY 1955 ------------------ I -:-· INTRO:bUCTIOI~ 1. In accordance with Letter Orders 273 dated 27 January 1955, as modified by L.0.273-A dated~ February 1955, I left Washington via MATS at 1500 houri' on 18 'February 1955, arrived at Orly Field, Pe,ris, at 1430 hours on 19 February, ' • • f • I ' -,-:--,I." -'\ iII ~ ~ ,.oo4 • ,. ,.. \ • .... a .. ''I •:,., I I .arid at Zug, Switzerland, at 1830 the same day. I sp~~~ th~· ~e~t .few da;s· ~ Boris Hagelin, Junior, for the purpose of learning the status of their new deyelop- ' ments in crypto-apparatus and of makifie an approach and a proposal to Mr. Hagelin S~, 1 / as was recently authorized by.USCIB and concurred in by LSIB. ~ Upon completion of that part of my mission, I left Zug at 1400 hours on ··'··· 28 February and proceeded by atrb-eme:Bfle to Zll:N:ch, ·1.'fteu~ I l3e-a.d:ee: a s~f3:es ah3::i:nMP plE.t;i~ie to London, arriving i:n mndo-l't' at 1845 that evening, f;the schedu1 ed p1anli ed 2_. The following report is based upon notes made of the subste.nce of several talks with the Hagel~ns, at times in separate meetings with each of them and at other times in meetings with both of them. -

The Mathemathics of Secrets.Pdf
THE MATHEMATICS OF SECRETS THE MATHEMATICS OF SECRETS CRYPTOGRAPHY FROM CAESAR CIPHERS TO DIGITAL ENCRYPTION JOSHUA HOLDEN PRINCETON UNIVERSITY PRESS PRINCETON AND OXFORD Copyright c 2017 by Princeton University Press Published by Princeton University Press, 41 William Street, Princeton, New Jersey 08540 In the United Kingdom: Princeton University Press, 6 Oxford Street, Woodstock, Oxfordshire OX20 1TR press.princeton.edu Jacket image courtesy of Shutterstock; design by Lorraine Betz Doneker All Rights Reserved Library of Congress Cataloging-in-Publication Data Names: Holden, Joshua, 1970– author. Title: The mathematics of secrets : cryptography from Caesar ciphers to digital encryption / Joshua Holden. Description: Princeton : Princeton University Press, [2017] | Includes bibliographical references and index. Identifiers: LCCN 2016014840 | ISBN 9780691141756 (hardcover : alk. paper) Subjects: LCSH: Cryptography—Mathematics. | Ciphers. | Computer security. Classification: LCC Z103 .H664 2017 | DDC 005.8/2—dc23 LC record available at https://lccn.loc.gov/2016014840 British Library Cataloging-in-Publication Data is available This book has been composed in Linux Libertine Printed on acid-free paper. ∞ Printed in the United States of America 13579108642 To Lana and Richard for their love and support CONTENTS Preface xi Acknowledgments xiii Introduction to Ciphers and Substitution 1 1.1 Alice and Bob and Carl and Julius: Terminology and Caesar Cipher 1 1.2 The Key to the Matter: Generalizing the Caesar Cipher 4 1.3 Multiplicative Ciphers 6 -

Polish Mathematicians Finding Patterns in Enigma Messages
Fall 2006 Chris Christensen MAT/CSC 483 Machine Ciphers Polyalphabetic ciphers are good ways to destroy the usefulness of frequency analysis. Implementation can be a problem, however. The key to a polyalphabetic cipher specifies the order of the ciphers that will be used during encryption. Ideally there would be as many ciphers as there are letters in the plaintext message and the ordering of the ciphers would be random – an one-time pad. More commonly, some rotation among a small number of ciphers is prescribed. But, rotating among a small number of ciphers leads to a period, which a cryptanalyst can exploit. Rotating among a “large” number of ciphers might work, but that is hard to do by hand – there is a high probability of encryption errors. Maybe, a machine. During World War II, all the Allied and Axis countries used machine ciphers. The United States had SIGABA, Britain had TypeX, Japan had “Purple,” and Germany (and Italy) had Enigma. SIGABA http://en.wikipedia.org/wiki/SIGABA 1 A TypeX machine at Bletchley Park. 2 From the 1920s until the 1970s, cryptology was dominated by machine ciphers. What the machine ciphers typically did was provide a mechanical way to rotate among a large number of ciphers. The rotation was not random, but the large number of ciphers that were available could prevent depth from occurring within messages and (if the machines were used properly) among messages. We will examine Enigma, which was broken by Polish mathematicians in the 1930s and by the British during World War II. The Japanese Purple machine, which was used to transmit diplomatic messages, was broken by William Friedman’s cryptanalysts. -

LIBRARIES Building a Global Information Assurance Program.Pdf
Building a Global Information Assurance Program OTHER AUERBACH PUBLICATIONS The ABCs of IP Addressing Information Security Management Gilbert Held Handbook, 4th Edition, Volume 4 ISBN: 0-8493-1144-6 Harold F. Tipton and Micki Krause, Editors The ABCs of TCP/IP ISBN: 0-8493-1518-2 Gilbert Held Information Security Policies, ISBN: 0-8493-1463-1 Procedures, and Standards: Building an Information Security Guidelines for Effective Information Awareness Program Security Management Mark B. Desman Thomas R. Peltier ISBN: 0-8493-0116-5 ISBN: 0-8493-1137-3 Building a Wireless Office Information Security Risk Analysis Gilbert Held Thomas R. Peltier ISBN: 0-8493-1271-X ISBN: 0-8493-0880-1 The Complete Book of Middleware A Practical Guide to Security Engineering Judith Myerson and Information Assurance ISBN: 0-8493-1272-8 Debra Herrmann ISBN: 0-8493-1163-2 Computer Telephony Integration, 2nd Edition The Privacy Papers: William A. Yarberry, Jr. Managing Technology and Consumers, ISBN: 0-8493-1438-0 Employee, and Legislative Action Rebecca Herold Cyber Crime Investigator’s Field Guide ISBN: 0-8493-1248-5 Bruce Middleton ISBN: 0-8493-1192-6 Secure Internet Practices: Best Practices for Securing Systems in Cyber Forensics: A Field Manual for the Internet and e-Business Age Collecting, Examining, and Preserving Patrick McBride, Jody Patilla, Evidence of Computer Crimes Craig Robinson, Peter Thermos, Albert J. Marcella and Robert S. Greenfield, and Edward P. Moser Editors ISBN: 0-8493-1239-6 ISBN: 0-8493-0955-7 Securing and Controlling Cisco Routers Global Information Warfare: Peter T. Davis How Businesses, Governments, and ISBN: 0-8493-1290-6 Others Achieve Objectives and Attain Competitive Advantages Securing E-Business Applications and Andy Jones, Gerald L. -

(Hagelin) by William F. Friedman
.. REF ID :A2436259 Declassified and approved for release by NSA on 07-22 2014 pursuant to E.O. 1352e REF ID:A2436259 '!'UP SECRE'l' REPORT"OF.VISIT 1Q. CRYPTO A.G. (HAGELIN) BY WILLIAJ-1 F. FRIEDI.W.if SPECIAL ASSISTANT TO THE DIRECTOR, NATIONAL SECURITY AGENCY 21 - 28 FEBRUARY 1955 ------------------ I -:-· INTRO:bUCTIOI~ 1. In accordance with Letter Orders 273 dated 27 January 1955, as modified by L.0.273-A dated~ February 1955, I left Washington via MATS at 1500 houri' on 18 'February 1955, arrived at Orly Field, Pe,ris, at 1430 hours on 19 February, ' • • f • I ' -,-:--,I." -'\ iII ~ ~ ,.oo4 • ,. ,.. \ • .... a .. ''I •:,., I I .arid at Zug, Switzerland, at 1830 the same day. I sp~~~ th~· ~e~t .few da;s· ~ Boris Hagelin, Junior, for the purpose of learning the status of their new deyelop- ' ments in crypto-apparatus and of makifie an approach and a proposal to Mr. Hagelin S~, 1 / as was recently authorized by.USCIB and concurred in by LSIB. ~ Upon completion of that part of my mission, I left Zug at 1400 hours on ··'··· 28 February and proceeded by atrb-eme:Bfle to Zll:N:ch, ·1.'fteu~ I l3e-a.d:ee: a s~f3:es ah3::i:nMP plE.t;i~ie to London, arriving i:n mndo-l't' at 1845 that evening, f;the schedu1 ed p1anli ed 2_. The following report is based upon notes made of the subste.nce of several talks with the Hagel~ns, at times in separate meetings with each of them and at other times in meetings with both of them. -
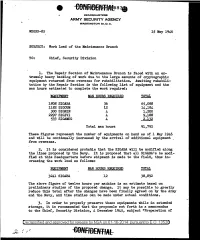
Work Load of the Maintenance Branch
HEADQUARTERS ARMY SECURITY AGENCY WASHINGTON 25, D. C. WDGSS-85 15 May 1946 SUBJECT: Work Load of the Maintenance Branch TO: Chief, Security Division 1. The Repair Section of Maintenance Branch is .faced with an ex tremely heavy backlog of' work due to the large amounts of' cryptographic equipment returned from overseas for rehabilitation. Awaiting rehabili tation by the Repair Section is the followi~g list of equipment and the man hours estimated to complete the work required.: EQUIPMENT MAN HOURS REQUIRED TOTAL 1808 SIGABA 36 65,088 1182 SIGCUM 12 14,184 300 SIGNIN 4 1,200 2297 SIGIVI 4 9,188 533 SIGAMUG 4, 2,132 Total man hours 91,792 These figures represent the number of equipments on hand as of 1 May 1946 and will be continually increased by the arrival of additional equipment . from overseas. 2. It is considered probable that the SIGABA will be modified along the lines proposed by the Navy. It is proposed that all SIGABA 1s be modi fied at this Headquarters before shipment is made to the field, thus in creasing the work load as follows: EQUIPMENT MAN HOURS REQUIRED 3241 SIGABA 12 The above figure of' twelve hours per machine is an estimate based on preliminary studies of' the proposed change. It may be possible to greatly reduce this total af'ter the changes have been f inaJ.ly agreed on by the .Army and the Navy, and time studies can be made under actual conditions. ,3. In order to properly preserve these equipments while in extended storage, it is recommended that the proposals set .forth in a memorandum to the Chief, Security Division, 4 December 1945, subject "Preparation of Declassified and approved for release by NSA on 01-16-2014 pursuantto E .0. -

November 1, 2020 PUBLICATIONS OF
November 1, 2020 PUBLICATIONS OF JEFFREY C. LAGARIAS A. Books 1. Mathematical Developments Arising from Linear Programming (J. C. Lagarias and M. J. Todd, Eds), Contemporary Math. Vol. 114, Amer. Math. Soc. 1990. 2. The Ultimate Challenge: The 3x + 1 Problem (J. C. Lagarias, Ed.), Amer. Math. Society, Providence, RI 2010. 3. The Kepler Conjecture: The Hales-Ferguson proof, by Thomas C. Hales, Samuel P. Ferguson (J. C. Lagarias, Ed.), Springer-Verlag: New York 2011. B. Book Chapters 1. J. C. Lagarias, Point Lattices, Chapter 19 in: Handbook of Combinatorics, Amster- dam: Elsevier Science Publ. 1995, pp. 919{966. C. Papers in Peer-Reviewed Journals or Conference Volumes 1. J. C. Lagarias, Discrete Balancing Games, Bulletin of the Institute of Mathematics, Academia Sinica 5 (1977), 363{373. 2. J. C. Lagarias and A. M. Odlyzko, Effective Versions of the Chebotarev Density The- orem, in: Algebraic Number Fields, L-Functions and Galois Properties, Proceedings of the 1975 Durham Symposium, (A. Fr¨ohlich, Ed.), Academic Press (1977), 409{464. 3. F. K. Hwang and J. C. Lagarias, Minimum Range Sequences of all k-subsets of a Set, Discrete Mathematics 19 (1977), 257{264. 4. J. C. Lagarias, Signatures of Units and Congruences (mod 4) in Certain Real Quadratic Fields, J. reine angew. Math. 301 (1978), 142{146. 5. J. C. Lagarias and A. M. Odlyzko, On Computing Artin L-functions in the Critical Strip, Mathematics of Computation 33 (1979), 1081{1095. 6. J. C. Lagarias, H.L.Montgomery and A.M.Odlyzko, A bound for the least prime ideal in the Chebotarev density theorem, Inventiones math. -

SIS and Cipher Machines: 1930 – 1940
SIS and Cipher Machines: 1930 – 1940 John F Dooley Knox College Presented at the 14th Biennial NSA CCH History Symposium, October 2013 This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 United States License. 1 Thursday, November 7, 2013 1 The Results of Friedman’s Training • The initial training regimen as it related to cipher machines was cryptanalytic • But this detailed analysis of the different machine types informed the team’s cryptographic imaginations when it came to creating their own machines 2 Thursday, November 7, 2013 2 The Machines • Wheatstone/Plett Machine • M-94 • AT&T machine • M-138 and M-138-A • Hebern cipher machine • M-209 • Kryha • Red • IT&T (Parker Hitt) • Purple • Engima • SIGABA (M-134 and M-134-C) • B-211(and B-21) 3 Thursday, November 7, 2013 3 The Wheatstone/Plett Machine • polyalphabetic cipher disk with gearing mechanism rotates the inner alphabet. • Plett’s improvement is to add a second key and mixed alphabet to the inner ring. • Friedman broke this in 1918 Principles: (a) The inner workings of a mechanical cryptographic device can be worked out using a paper and pencil analog of the device. (b) if there is a cycle in the mechanical device (say for particular cipher alphabets), then that cycle can be discovered by analysis of the paper and pencil analog. 4 Thursday, November 7, 2013 4 The Army M-94 • Traces its roots back to Jefferson and Bazieres • Used by US Army from 1922 to circa 1942 • 25 mixed alphabets. Disk order is the key. -

A Complete Bibliography of Publications in Cryptologia
A Complete Bibliography of Publications in Cryptologia Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 04 September 2021 Version 3.64 Title word cross-reference 10016-8810 [?, ?]. 1221 [?]. 125 [?]. 15.00/$23.60.0 [?]. 15th [?, ?]. 16th [?]. 17-18 [?]. 18 [?]. 180-4 [?]. 1812 [?]. 18th (t; m)[?]. (t; n)[?, ?]. $10.00 [?]. $12.00 [?, ?, ?, ?, ?]. 18th-Century [?]. 1930s [?]. [?]. 128 [?]. $139.99 [?]. $15.00 [?]. $16.95 1939 [?]. 1940 [?, ?]. 1940s [?]. 1941 [?]. [?]. $16.96 [?]. $18.95 [?]. $24.00 [?]. 1942 [?]. 1943 [?]. 1945 [?, ?, ?, ?, ?]. $24.00/$34 [?]. $24.95 [?, ?]. $26.95 [?]. 1946 [?, ?]. 1950s [?]. 1970s [?]. 1980s [?]. $29.95 [?]. $30.95 [?]. $39 [?]. $43.39 [?]. 1989 [?]. 19th [?, ?]. $45.00 [?]. $5.95 [?]. $54.00 [?]. $54.95 [?]. $54.99 [?]. $6.50 [?]. $6.95 [?]. $69.00 2 [?, ?]. 200/220 [?]. 2000 [?]. 2004 [?, ?]. [?]. $69.95 [?]. $75.00 [?]. $89.95 [?]. th 2008 [?]. 2009 [?]. 2011 [?]. 2013 [?, ?]. [?]. A [?]. A3 [?, ?]. χ [?]. H [?]. k [?, ?]. M 2014 [?]. 2017 [?]. 2019 [?]. 20755-6886 [?, ?]. M 3 [?]. n [?, ?, ?]. [?]. 209 [?, ?, ?, ?, ?, ?]. 20th [?]. 21 [?]. 22 [?]. 220 [?]. 24-Hour [?, ?, ?]. 25 [?, ?]. -Bit [?]. -out-of- [?, ?]. -tests [?]. 25.00/$39.30 [?]. 25.00/839.30 [?]. 25A1 [?]. 25B [?]. 26 [?, ?]. 28147 [?]. 28147-89 000 [?]. 01Q [?, ?]. [?]. 285 [?]. 294 [?]. 2in [?, ?]. 2nd [?, ?, ?, ?]. 1 [?, ?, ?, ?]. 1-4398-1763-4 [?]. 1/2in [?, ?]. 10 [?]. 100 [?]. 10011-4211 [?]. 3 [?, ?, ?, ?]. 3/4in [?, ?]. 30 [?]. 310 1 2 [?, ?, ?, ?, ?, ?, ?]. 312 [?]. 325 [?]. 3336 [?, ?, ?, ?, ?, ?]. affine [?]. [?]. 35 [?]. 36 [?]. 3rd [?]. Afluisterstation [?, ?]. After [?]. Aftermath [?]. Again [?, ?]. Against 4 [?]. 40 [?]. 44 [?]. 45 [?]. 45th [?]. 47 [?]. [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. Age 4in [?, ?]. [?, ?]. Agencies [?]. Agency [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. -

Hagelin) by William F
.. REF ID :A2436259 Declassified and approved for release by NSA on 07-22 2014 pursuant to E.O. 13s2e REF ID:A2436259 '!'UP SECRE'I' REPO'.RT·oF.VISIT 1Q. CRYPTO A.G. (HAGELIN) BY WILLIAM F. FRIEDMAlif SPECIAL ASSISTANT TO THE DIRECTOR, NATIONAL SECURITY AGENCY 21 - 28 FEBRUARY 1955 ----------~------- I -:-· INTRO:bUCTIOI~ 1. In accordance with Letter Orders 273 dated 27 January 1955, as modified by L.0.273-A dated~ February 1955, I left Washington via MATS at 1500 hour~ on 18 'February 1955, arrived at Orly Field, Pe,ris, at 1430 hours on 19 February, • • • f ' I ' -,-:--, I." -'\ i I I ~ ~ ,.o"4 • ,. ... \ • .... a .. ''I •:,,., I I .arid at Zug, Switzerland, at 1830 the same day. I sp~~~ th~- ~e~t .few da;s· ~ Boris Hagelin, Junior, for the purpose of learning the status of their new deyelop- ' ments in crypto-apparatus and of makifie an approach and a proposal to Mr. Hagelin S~, 1 / as was recently authorized by.USCIB and concurred in by LSIB. ~ Upon completion of that part of rrry mission, I left Zug at 1400 hours on ··'··· 28 February and proceeded by atrb-eme:afle to Zttr-3:ch, wfl:eie I l3e-a.d:ee: a s~"3:es ah3::i:nMP plet;ille to London, arriving :H1 i:Jendo-l't' at 1845 that evening, f,the schedll1 ed plan'i ed 2_. The following report is based upon notes made of the subste.nce of several talks with the Hagel~ns, at times in separate meetings with each of them and at other times in meetings with both of them. -

Simulation and Computer-Aided Cryptanalysis of Angooki Taipu B
PURPLE Revealed: Simulation and Computer-aided Cryptanalysis of Angooki Taipu B Wes Freeman,1 Geoff Sullivan 2 and Frode Weierud 3 ADDRESSES: (1) 2527 Mardell Way, Mt View CA 94043 USA. Email: [email protected]; (2) 64 Tennyson Road, Headless Cross, Redditch, Worcs., B97 5BJ UNITED KINGDOM. Email: [email protected]; (3) Le Pre Vert, 1041 Rte de Mategnin, F-01280 Prevessin-Moens FRANCE. Email: [email protected] ABSTRACT: PURPLE was the designation given by U.S. cryptanalysts to the cipher machine used by the Japanese Foreign Office for secure communications before and during WW 2. We present the structure and internal wiring of the machine, as well as details of the keying procedures and a system of abbreviations, which was used in the messages. We have also written a computer simulation of the PURPLE machine. Operation of the simulator is demonstrated by deciphering portions of the 14-part message delivered to the United States on Dec. 7, 1941. Finally, an automated cryptanalysis method for the PURPLE system is presented. KEYWORDS: Pearl Harbor, PURPLE, RED, Rowlett, Stepping Switch, Computer Simulations, Hill Climbing, Roma-ji, Romazi. Introduction On December 6, 1941, the Japanese Government sent a message, which was divided for transmission into 14 parts (the 14-part message), to its embassy in Washington. An accompanying message directed that the 14-part message be delivered to the United States Government on December 7 at 1:00 p.m., which corresponded to 7:30 a.m. at Pearl Harbor, Hawaii. The 14-part message, which broke off negotiations between Japan and the United States, was enciphered on the PURPLE machine. -

George Lasry: Modern Cryptanalysis of Historical Ciphers
Modern Cryptanalysis of Historical Ciphers November 1, 2019 George Lasry Agenda • Introduction – Motivation – Difficulty – Generic approaches • Case studies – Hagelin M-209 – Playfair – Double transposition – SIGABA George Lasry 2 Agenda • Introduction – Motivation – Difficulty – Generic approaches • Case studies – Hagelin M-209 – Playfair – Double transposition – SIGABA George Lasry 3 Motivation • Historical cryptanalysis • Undecrypted texts • Public challenges • Fun George Lasry 4 Difficulty - Factors • System design – Diffusion – Confusion – Weaknesses • Key – Key space/length • Ciphertext – Length – Language George Lasry 5 Difficulty Easy Moderate Hard Very hard Intractable? Monoalphabetic Playfair Playfair Playfair Fialka substitution (long ciphertext) (short ciphertext) (very short) Transposition Transposition ADFGVX Double transposition Double transposition (short key) (long key) (long random key) Vigenere Enigma Enigma SIGABA (long ciphertext) (short ciphertext) (known plaintext) Hagelin M-209 Hagelin M-209 (long ciphertext) (short ciphertext) Hagelin M-209 Sturgeon T52 Sturgeon T52 (known plaintext) (regular stepping) (irregular stepping) George Lasry 6 Generic Approaches - 1 Exhaustive Combinatorial Stochastic Search Search Search ● Simple brute force ● Backtracking ● Hill climbing ● Dictionary search ● Meet in the Middle ● Simulated annealing (MITM) ● Hybrid (e.g., nested) ● Match some ● Others (e.g., genetic constraints (e.g., ● Match some algorithms) known plaintext) constraints ● Or optimize a scoring ● Optimize a fitness