Notes on German High Level Cryptography and Cryptanalysis
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Battle Management Language: History, Employment and NATO Technical Activities
Battle Management Language: History, Employment and NATO Technical Activities Mr. Kevin Galvin Quintec Mountbatten House, Basing View, Basingstoke Hampshire, RG21 4HJ UNITED KINGDOM [email protected] ABSTRACT This paper is one of a coordinated set prepared for a NATO Modelling and Simulation Group Lecture Series in Command and Control – Simulation Interoperability (C2SIM). This paper provides an introduction to the concept and historical use and employment of Battle Management Language as they have developed, and the technical activities that were started to achieve interoperability between digitised command and control and simulation systems. 1.0 INTRODUCTION This paper provides a background to the historical employment and implementation of Battle Management Languages (BML) and the challenges that face the military forces today as they deploy digitised C2 systems and have increasingly used simulation tools to both stimulate the training of commanders and their staffs at all echelons of command. The specific areas covered within this section include the following: • The current problem space. • Historical background to the development and employment of Battle Management Languages (BML) as technology evolved to communicate within military organisations. • The challenges that NATO and nations face in C2SIM interoperation. • Strategy and Policy Statements on interoperability between C2 and simulation systems. • NATO technical activities that have been instigated to examine C2Sim interoperation. 2.0 CURRENT PROBLEM SPACE “Linking sensors, decision makers and weapon systems so that information can be translated into synchronised and overwhelming military effect at optimum tempo” (Lt Gen Sir Robert Fulton, Deputy Chief of Defence Staff, 29th May 2002) Although General Fulton made that statement in 2002 at a time when the concept of network enabled operations was being formulated by the UK and within other nations, the requirement remains extant. -

IMPLEMENTASI ALGORITMA CAESAR, CIPHER DISK, DAN SCYTALE PADA APLIKASI ENKRIPSI DAN DEKRIPSI PESAN SINGKAT, Lumasms
Prosiding Seminar Ilmiah Nasional Komputer dan Sistem Intelijen (KOMMIT 2014) Vol. 8 Oktober 2014 Universitas Gunadarma – Depok – 14 – 15 Oktober 2014 ISSN : 2302-3740 IMPLEMENTASI ALGORITMA CAESAR, CIPHER DISK, DAN SCYTALE PADA APLIKASI ENKRIPSI DAN DEKRIPSI PESAN SINGKAT, LumaSMS Yusuf Triyuswoyo ST. 1 Ferina Ferdianti ST. 2 Donny Ajie Baskoro ST. 3 Lia Ambarwati ST. 4 Septiawan ST. 5 1,2,3,4,5Jurusan Manajemen Sistem Informasi, Universitas Gunadarma [email protected] Abstrak Short Message Service (SMS) merupakan salah satu cara berkomunikasi yang banyak digunakan oleh pengguna telepon seluler. Namun banyaknya pengguna telepon seluler yang menggunakan layanan SMS, tidak diimbangi dengan faktor keamanan yang ada pada layanan tersebut. Banyak pengguna telepon seluler yang belum menyadari bahwa SMS tidak menjamin integritas dan keamanan pesan yang disampaikan. Ada beberapa risiko yang dapat mengancam keamanan pesan pada layanan SMS, diantaranya: SMS spoofing, SMS snooping, dan SMS interception. Untuk mengurangi risiko tersebut, maka dibutuhkan sebuah sistem keamanan pada layanan SMS yang mampu menjaga integritas dan keamanan isi pesan. Dimana tujuannya ialah untuk menutupi celah pada tingkat keamanan SMS. Salah satu penanggulangannya ialah dengan menerapkan algoritma kriptografi, yaitu kombinasi atas algoritma Cipher Disk, Caesar, dan Scytale pada pesan yang akan dikirim. Tujuan dari penulisan ini adalah membangun aplikasi LumaSMS, dengan menggunakan kombinasi ketiga algoritma kriptografi tersebut. Dengan adanya aplikasi ini diharapkan mampu mengurangi masalah keamanan dan integritas SMS. Kata Kunci: caesar, cipher disk, kriptografi, scytale, SMS. PENDAHULUAN dibutuhkan dikarenakan SMS mudah digunakan dan biaya yang dikeluarkan Telepon seluler merupakan salah untuk mengirim SMS relatif murah. satu hasil dari perkembangan teknologi Namun banyaknya pengguna komunikasi. -

Polish Mathematicians Finding Patterns in Enigma Messages
Fall 2006 Chris Christensen MAT/CSC 483 Machine Ciphers Polyalphabetic ciphers are good ways to destroy the usefulness of frequency analysis. Implementation can be a problem, however. The key to a polyalphabetic cipher specifies the order of the ciphers that will be used during encryption. Ideally there would be as many ciphers as there are letters in the plaintext message and the ordering of the ciphers would be random – an one-time pad. More commonly, some rotation among a small number of ciphers is prescribed. But, rotating among a small number of ciphers leads to a period, which a cryptanalyst can exploit. Rotating among a “large” number of ciphers might work, but that is hard to do by hand – there is a high probability of encryption errors. Maybe, a machine. During World War II, all the Allied and Axis countries used machine ciphers. The United States had SIGABA, Britain had TypeX, Japan had “Purple,” and Germany (and Italy) had Enigma. SIGABA http://en.wikipedia.org/wiki/SIGABA 1 A TypeX machine at Bletchley Park. 2 From the 1920s until the 1970s, cryptology was dominated by machine ciphers. What the machine ciphers typically did was provide a mechanical way to rotate among a large number of ciphers. The rotation was not random, but the large number of ciphers that were available could prevent depth from occurring within messages and (if the machines were used properly) among messages. We will examine Enigma, which was broken by Polish mathematicians in the 1930s and by the British during World War II. The Japanese Purple machine, which was used to transmit diplomatic messages, was broken by William Friedman’s cryptanalysts. -

Cipher Disk A
Make It@Home: Cipher Disk A. Materials 1 Tack 1 Small Cipher Disk 1 Large Cipher Disk 1 Small Eraser Scissors B. Directions 1. Download and print the Cipher Disk.pdf document. 2. Cut out the two cipher disks. 3. Put the smaller disk on top of the larger disk and stick the tack thru the center of both disks. 4. Stick the sharp end of the tack into the eraser. This will prevent you from sticking yourself while turning the disks to make your ciphers. C. Encrypting A Code 1. Pick a letter from the smaller disk on top - this will be used as the KEY that will be shared between you and your friends to encrypt and decrypt the message. Once you have picked a letter from the smaller disk, line it up with the “A” from the larger disk. Example Key: LARGE DISK: A SMALL DISK: M KEY = A:M 2. Begin encrypting each letter of your secret message. Find the first letter of your message on the larger disk and write down the cipher letter which appears underneath it on the smaller disk. In the example below, A=M, B=L, C=K, etc. LARGE DISK: ABCDEFGHIJKLMNOPQRSTUVWXYZ SMALL DISK: MLKJIHGFEDCBAZYXWVUTSRQPON 3. Continue finding each letter until your message has been encrypted. Once you are finished, send your friend the encrypted message and KEY seperately. PLAINTEXT: MAKING CODES IS FUN CIPHERTEXT: AMCEZG KYJIU EU HSZ NOTE: Make sure your friend knows the KEY so they can use their Cipher Disk to break the code. For a super secure cipher, create a new KEY every time you send a message OR change the KEY every time you encrypt a letter. -

Historical Cryptography 2
Historical cryptography 2 CSCI 470: Web Science • Keith Vertanen Overview • Historical cryptography – WWI • Zimmerman telegram – WWII • Rise of the cipher machines • Engima • Allied encryption 2 WWI: Zimmermann Telegram • 1915, U-boat sinks Lusitania – 1,198 drown including 128 US – Germany agrees to surface 1st • 1916, new Foreign Minister – Arthur Zimmermann • 1917, unrestricted submarine warfare – Zimmermann hatches plan • Keep American busy at home • Persuade Mexico to: invade US and invite Japan to attack US as well Arthur Zimmermann 3 4 Mechanization of secret writing • Pencil and paper – Security limited by what humans can do quickly and accurately in the heat of battle • Enter the machine Thomas Jefferson's wheel cipher Captain Midnight's Code-o-Graph 5 Enigma machine • Enigma cipher machine – 1918, patented by German engineer Arthur Scherbius Arthur Scherbius – A electrical/mechanical implementation of a polyalphabetic substitution cipher 6 7 Enigma rotors • Rotor (wheel, drum) – Monoalphabetic substitution cipher implemented via complex wiring pattern – One of 26 initial positions – Geared: rotates after each letter • Rotor set – 3 rotors in 3!=6 possible orders • Eventually increased to 3 out of 5 • Navy used even more – Possible keys: • 3! * 263 = 6 * 17,576 = 105,456 8 Enigma plugboard • Plugboard – Operator inserts cables to swap letters – Initially 6 cables • Swaps 6 pairs of letters • Leaves 14 letters unswapped – Possible configurations: • 100,391,791,500 • Total keys: – 17,576 * 6 * 100,391,791,500 ≈ 10,000,000,000,000,000 -

CHAPTER 8 a History of Communications Security in New Zealand
CHAPTER 8 A History of Communications Security in New Zealand By Eric Morgon Early Days “Admiralty to Britannia Wellington. Comence hostilities at once with Germany in accordance with War Standing Orders.” This is an entry in the cipher log of HMS Philomel dated 5 August, 1914. HMS Philomel was a cruiser of the Royal Navy and took part in the naval operations in the Dardanelles during the ill-fated Gallipoli campaign. Philomel’s cipher logs covering the period 1914 to 1918 make interesting reading and show how codes and ciphers were used extensively by the Royal Navy during World War 1. New Zealand officers and ratings served on board Philomel and thus it can be claimed that the use of codes and ciphers by Philomel are part of the early history of communications security in New Zealand. Immediately following the codes to Navy Office, the Senior Naval Officer New Zealand was advised that Cypher G and Cypher M had been compromised and that telegrams received by landline in these ciphers were to be recoded in Code C before transmission by Wireless Telegraphy (W/T) Apparently Cypher G was also used for cables between the Commonwealth Navy Board in Melbourne and he British Consul in Noumea. The Rear Admiral Commanding Her Majesty’s Australian Fleet instructed that when signalling by WT every odd numbered code group was to be a dummy. It is interesting to note that up until the outbreak of hostilities no provision had been made for the storage of code books or for precautions to prevent them from falling into enemy hands. -

History and Modern Cryptanalysis of Enigma's Pluggable Reflector
History and Modern Cryptanalysis of Enigma’s Pluggable Reflector Olaf Ostwald and Frode Weierud ABSTRACT: The development history of Umkehrwalze Dora (UKWD), Enigma's pluggable reflector, is presented from the first ideas in the mid-1920s to the last development plans and its actual usage in 1945. An Enigma message in three parts, enciphered with UKWD and intercepted by the British on 11 March 1945, is shown. The successful recovery of the key of this message is described. Modern computer-based cryptanalysis is used to recover the wiring of the unknown “Uncle Dick,” which the British called this field-rewirable reflector. The attack is based on the known ciphertext and plaintext pair from the first part of the intercept. After recovery of the unknown reflector wiring and the daily key the plaintext of the second part of the message is revealed. KEYWORDS: Enigma, cryptanalysis, Uncle Dick, Umkehrwalze Dora, UKWD, unsolved ciphers Address correspondence to Frode Weierud, Bjerkealleen 17, 1385 Asker, Norway. Email: [email protected] 1. Introduction Uncle Dick,1 as it was called by the codebreakers of Bletchley Park (BP), or Umkehrwalze Dora (UKWD), as designated by the Germans, was the nickname of a special pluggable reflector,2 used as the leftmost wheel within the scrambler 3 of the Enigma. The electro-mechanical cipher machine Enigma (from Greek αίνιγµα for “riddle”) was the backbone of the German Wehrmacht during World War II. Arthur Scherbius, a German promoted electrical engineer and inventor of considerable standing, invented Enigma in 1918 [14]. Subsequently it was improved and then used by all three parts of the German armed forces, namely army (Heer), air force (Luftwaffe), and military navy (Kriegsmarine), for enciphering and deciphering of their secret messages. -
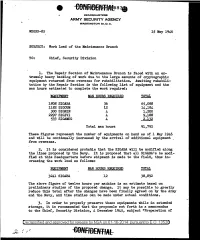
Work Load of the Maintenance Branch
HEADQUARTERS ARMY SECURITY AGENCY WASHINGTON 25, D. C. WDGSS-85 15 May 1946 SUBJECT: Work Load of the Maintenance Branch TO: Chief, Security Division 1. The Repair Section of Maintenance Branch is .faced with an ex tremely heavy backlog of' work due to the large amounts of' cryptographic equipment returned from overseas for rehabilitation. Awaiting rehabili tation by the Repair Section is the followi~g list of equipment and the man hours estimated to complete the work required.: EQUIPMENT MAN HOURS REQUIRED TOTAL 1808 SIGABA 36 65,088 1182 SIGCUM 12 14,184 300 SIGNIN 4 1,200 2297 SIGIVI 4 9,188 533 SIGAMUG 4, 2,132 Total man hours 91,792 These figures represent the number of equipments on hand as of 1 May 1946 and will be continually increased by the arrival of additional equipment . from overseas. 2. It is considered probable that the SIGABA will be modified along the lines proposed by the Navy. It is proposed that all SIGABA 1s be modi fied at this Headquarters before shipment is made to the field, thus in creasing the work load as follows: EQUIPMENT MAN HOURS REQUIRED 3241 SIGABA 12 The above figure of' twelve hours per machine is an estimate based on preliminary studies of' the proposed change. It may be possible to greatly reduce this total af'ter the changes have been f inaJ.ly agreed on by the .Army and the Navy, and time studies can be made under actual conditions. ,3. In order to properly preserve these equipments while in extended storage, it is recommended that the proposals set .forth in a memorandum to the Chief, Security Division, 4 December 1945, subject "Preparation of Declassified and approved for release by NSA on 01-16-2014 pursuantto E .0. -

Cryptology: an Historical Introduction DRAFT
Cryptology: An Historical Introduction DRAFT Jim Sauerberg February 5, 2013 2 Copyright 2013 All rights reserved Jim Sauerberg Saint Mary's College Contents List of Figures 8 1 Caesar Ciphers 9 1.1 Saint Cyr Slide . 12 1.2 Running Down the Alphabet . 14 1.3 Frequency Analysis . 15 1.4 Linquist's Method . 20 1.5 Summary . 22 1.6 Topics and Techniques . 22 1.7 Exercises . 23 2 Cryptologic Terms 29 3 The Introduction of Numbers 31 3.1 The Remainder Operator . 33 3.2 Modular Arithmetic . 38 3.3 Decimation Ciphers . 40 3.4 Deciphering Decimation Ciphers . 42 3.5 Multiplication vs. Addition . 44 3.6 Koblitz's Kid-RSA and Public Key Codes . 44 3.7 Summary . 48 3.8 Topics and Techniques . 48 3.9 Exercises . 49 4 The Euclidean Algorithm 55 4.1 Linear Ciphers . 55 4.2 GCD's and the Euclidean Algorithm . 56 4.3 Multiplicative Inverses . 59 4.4 Deciphering Decimation and Linear Ciphers . 63 4.5 Breaking Decimation and Linear Ciphers . 65 4.6 Summary . 67 4.7 Topics and Techniques . 67 4.8 Exercises . 68 3 4 CONTENTS 5 Monoalphabetic Ciphers 71 5.1 Keyword Ciphers . 72 5.2 Keyword Mixed Ciphers . 73 5.3 Keyword Transposed Ciphers . 74 5.4 Interrupted Keyword Ciphers . 75 5.5 Frequency Counts and Exhaustion . 76 5.6 Basic Letter Characteristics . 77 5.7 Aristocrats . 78 5.8 Summary . 80 5.9 Topics and Techniques . 81 5.10 Exercises . 81 6 Decrypting Monoalphabetic Ciphers 89 6.1 Letter Interactions . 90 6.2 Decrypting Monoalphabetic Ciphers . -

Angol-Magyar Nyelvészeti Szakszótár
PORKOLÁB - FEKETE ANGOL- MAGYAR NYELVÉSZETI SZAKSZÓTÁR SZERZŐI KIADÁS, PÉCS 2021 Porkoláb Ádám - Fekete Tamás Angol-magyar nyelvészeti szakszótár Szerzői kiadás Pécs, 2021 Összeállították, szerkesztették és tördelték: Porkoláb Ádám Fekete Tamás Borítóterv: Porkoláb Ádám A tördelés LaTeX rendszer szerint, az Overleaf online tördelőrendszerével készült. A felhasznált sablon Vel ([email protected]) munkája. https://www.latextemplates.com/template/dictionary A szótárhoz nyújtott segítő szándékú megjegyzéseket, hibajelentéseket, javaslatokat, illetve felajánlásokat a szótár hagyományos, nyomdai úton történő előállítására vonatkozóan az [email protected] illetve a [email protected] e-mail címekre várjuk. Köszönjük szépen! 1. kiadás Szerzői, elektronikus kiadás ISBN 978-615-01-1075-2 El˝oszóaz els˝okiadáshoz Üdvözöljük az Olvasót! Magyar nyelven már az érdekl˝od˝oközönség hozzáférhet német–magyar, orosz–magyar nyelvészeti szakszótárakhoz, ám a modern id˝ok tudományos világnyelvéhez, az angolhoz még nem készült nyelvészeti célú szak- szótár. Ennek a több évtizedes hiánynak a leküzdésére vállalkoztunk. A nyelvtudo- mány rohamos fejl˝odéseés differenciálódása tovább sürgette, hogy elkészítsük az els˝omagyar-angol és angol-magyar nyelvészeti szakszótárakat. Jelen kötetben a kétnyelv˝unyelvészeti szakszótárunk angol-magyar részét veheti kezébe az Olvasó. Tervünk azonban nem el˝odöknélküli vállalkozás: tudomásunk szerint két nyelvészeti csoport kísérelt meg a miénkhez hasonló angol-magyar nyelvészeti szakszótárat létrehozni. Az els˝opróbálkozás -

Communication Intelligence and Security, William F Friedman
UNCLASSIFIED DATE: 26 April 1960 NAME: Friedman, William F. PLACE: Breckinridge Hall, Marine Corp School TITLE: Communications Intelligence and Security Presentation Given to Staff and Students; Introduction by probably General MILLER (NFI) Miller: ((TR NOTE: Introductory remarks are probably made by General Miller (NFI).)) Gentleman, I…as we’ve grown up, there have been many times, I suppose, when we’ve been inquisitive about means of communication, means of finding out what’s going on. Some of us who grew up out in the country used to tap in on a country telephone line and we could find out what was going on that way—at least in the neighborhood. And then, of course, there were always a few that you’d read about in the newspaper who would carry this a little bit further and read some of your neighbor’s mail by getting at it at the right time, and reading it and putting it back. Of course, a good many of those people ended up at a place called Fort Leavenworth. This problem of security of information is with us in the military on a [sic] hour-to-hour basis because it’s our bread and butter. It’s what we focus on in the development of our combat plans in an attempt to project these plans onto an enemy and defeat him. And so, we use a good many devices. We spend a tremendous amount of effort and money in attempting to keep our secrets in fact secret—at least at the echelon where we feel this is necessary. -

SIS and Cipher Machines: 1930 – 1940
SIS and Cipher Machines: 1930 – 1940 John F Dooley Knox College Presented at the 14th Biennial NSA CCH History Symposium, October 2013 This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 United States License. 1 Thursday, November 7, 2013 1 The Results of Friedman’s Training • The initial training regimen as it related to cipher machines was cryptanalytic • But this detailed analysis of the different machine types informed the team’s cryptographic imaginations when it came to creating their own machines 2 Thursday, November 7, 2013 2 The Machines • Wheatstone/Plett Machine • M-94 • AT&T machine • M-138 and M-138-A • Hebern cipher machine • M-209 • Kryha • Red • IT&T (Parker Hitt) • Purple • Engima • SIGABA (M-134 and M-134-C) • B-211(and B-21) 3 Thursday, November 7, 2013 3 The Wheatstone/Plett Machine • polyalphabetic cipher disk with gearing mechanism rotates the inner alphabet. • Plett’s improvement is to add a second key and mixed alphabet to the inner ring. • Friedman broke this in 1918 Principles: (a) The inner workings of a mechanical cryptographic device can be worked out using a paper and pencil analog of the device. (b) if there is a cycle in the mechanical device (say for particular cipher alphabets), then that cycle can be discovered by analysis of the paper and pencil analog. 4 Thursday, November 7, 2013 4 The Army M-94 • Traces its roots back to Jefferson and Bazieres • Used by US Army from 1922 to circa 1942 • 25 mixed alphabets. Disk order is the key.