Konkuk University, Seoul, South Korea Table of Contents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Curriculum Vitae
JUN-KOO KANG Canon Professorship in Finance and Distinguished Professor of Finance Division of Banking and Finance, Block S3-01b-54 Nanyang Business School Nanyang Technological University Nanyang Avenue, Singapore 639798 Tel: (+65) 6790-5662, Fax: (+65) 6791-3697 E-mail: [email protected] EDUCATION Ph.D., Finance, September 1986–August 1991, Ohio State University. M.S., Finance, August 1984–May 1986, Iowa State University. B.A., Business Administration, March 1975–February 1982, Korea University (Military Service for 2 ½ Years from 1978 to 1980). ACADEMIC APPOINTMENTS AND OTHER PROFESSIONAL EXPERIENCE Distinguished Professor, Nanyang Technological University (July 2008-Present). Canon Professorship in Finance, Nanyang Technological University (March 2015-Present). Executive Director, Insurance Risk and Finance Research Center, Nanyang Technological University (April 2011-December 2015). Head, Division of Banking and Finance, Nanyang Technological University (July 2010-June 2014). MSU Federal Credit Union Endowed Chair in Financial Institutions & Investments, Michigan State University (August 2001-August 2010). Professor, Michigan State University (July 2001- August 2010). Director of Doctoral Program in Finance, Michigan State University (August 1999-December 2002). Associate Professor, Korea University (March 1997-July 1999), Michigan State University (August 1999-June 2001). Assistant Professor, University of Rhode Island (July 1991-June 1995), University of California at Riverside (July 1995-August 1996), Korea University (Sep. 1996-Feb.1997). -

Schedule of Accreditations, by Year and University
Comprehensive University Accreditation System Schedule of Accreditations, by Year and University Korean Council for University Education Center for University Accreditation 2nd Cycle Accreditations (2001-2006) Table 1a: General Accreditations, by Year Conducted Section(s) of University Evaluated # of Year Universities Undergraduate Colleges Undergraduate Colleges Only Graduate Schools Only Evaluated & Graduate Schools 2001 Kyungpook National University 1 2002 Chonbuk National University Chonnam National University 4 Chungnam National University Pusan National University 2003 Cheju National University Mokpo National University Chungbuk National University Daegu University Daejeon University 9 Kangwon National University Korea National Sport University Sunchon National University Yonsei University (Seoul campus) 2004 Ajou University Dankook University (Cheonan campus) Mokpo National University 41 1 Name changed from Kyungsan University to Daegu Haany University in May 2003. 1 Andong National University Hanyang University (Ansan campus) Catholic University of Daegu Yonsei University (Wonju campus) Catholic University of Korea Changwon National University Chosun University Daegu Haany University1 Dankook University (Seoul campus) Dong-A University Dong-eui University Dongseo University Ewha Womans University Gyeongsang National University Hallym University Hanshin University Hansung University Hanyang University Hoseo University Inha University Inje University Jeonju University Konkuk University Korea -

APMS 2018 International Conference
Call for Papers APMS 2018 International International Conference Federation for Information Advances in Production Management Systems Processing August 26-30, 2018 Seoul National University, Seoul, Korea “Smart production management for data-driven, intelligent, collaborative, and sustainable manufacturing” Honorary Co-chairs Objectives and Scopes of APMS 2018 Dimitris Kiritsis The objectives of the APMS 2018 conference are: (1) to share up-to-date EPFL, Switzerland Jinwoo Park issues and knowledge of production management among leading experts Seoul National University, Korea from academia and industry, (2) to disseminate research papers, case studies, and state-of-the-arts reports on production management, and Conference Chair Ilkyeong Moon (3) to provide guidelines and insights to pave the way for future Seoul National University, Korea manufacturing systems. Advisory Committee Program Byoung-Kyu Choi The program includes presentations and discussions of high-quality KAIST, Korea Chi–Hyuck Jun peer-reviewed papers, in addition to insightful keynote speeches. A POSTECH, Korea doctoral workshop (26th), special sessions (27th-29th), and industry tour Kap Hwan Kim Pusan National University, Korea (30th) are included in the conference program. Tae–Eog Lee KAIST, Korea Conference topics Young Hoon Lee Topics of interest include, but are not limited to, the following. Yonsei University, Korea Global Supply Chains Knowledge based Production Management International Advisory Mass customization Intelligent manufacturing systems Committee Social & cultural aspects Knowledge engineering http://www.apms-conference.org/ committees/international-advisory- Reshoring Agile and flexible manufacturing committee/ Simulation of large-scale Modeling and simulation supply chains Automatic learning systems Program Co-chairs Gregor Von Cieminski Production planning & control ZF Friedrichshafen AG, Germany Collaborative Networks Gyu M. -
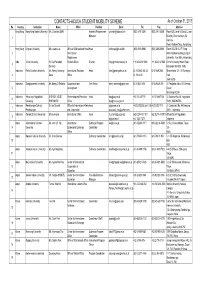
CONTACTS-ACUCA STUDENT MOBILITY SCHEME As of October 31, 2013 No
CONTACTS-ACUCA STUDENT MOBILITY SCHEME As of October 31, 2013 No. Country Institution Name Office Position Email Tel. Fax. Address Hong Kong Hong Kong Baptist University Ms. Christina CHAN Assistant Programmem [email protected] (852) 3411 5328 (852) 3411 5568 Room 825, Level 8, David C. Lam Manager Building, Shaw Campus, 34 1 Renfrew Road, Kowloon Tong, Hong Kong Hong Kong Lingnan University Ms. Joanne Lai Office of Mainland and Head Head [email protected] (852) 2616-8990 (852) 2465-9660 Room AD-208/1, 2/F, Wong 2 International Administration Building, Lingnan Programmes University, Tuen Mun, Hong Kong India Christ University Fr. Viju Painadath Student Affairs Director [email protected] + 91 80 4012 9008 +91 80 4012 9000 Christ University, Hosur Road, 3 Devassy Bangalore 560 029 , India Indonesia Petra Christian University Ms. Renny Novemsy International Relations Head [email protected] 62 31 298 3185, 62 62 31 849 2583 Siwalankerto 121-131 Surabaya, 4 Dese Office 31 298 3187 East Java 60236 Indonesia Soegijapranata University Mr. Benny D Setianto Cooperation and Vice Rector [email protected] 62 24 8441 555 62 24 8445 265 Jl. Pawiyatan Luhur IV/I Bendan 5 Development Duwur Semarang 50234 Indonesia Atma Jaya Yogyakarta M.SI IGN. AGUS Partnership and Promotion Head [email protected] +62 274 487711 +62 274 487748 Jl. Babarsari No. 44 Yogyakarta 6 University PUTRANTO Office [email protected] 55281, INDONESIA Indonesia Parahyangan Catholic Dr. Ida Susanti Office for International AffairsHead [email protected] +62222032655 (ext 125)+62222031110 Jl. Ciumbuleuit No. -

United Board for Christian Higher Education in Asia 2016-17 Institutional Grants Program
United Board for Christian Higher Education in Asia 2016-17 Institutional Grants Program This packet contains the instructions and forms needed to apply for a 2016-17 Institutional Grant. Table of Contents Guidelines for Proposals ............................................................................................................. 2 United Board Program Areas ..................................................................................................... 6 Eligible Institutions ...................................................................................................................... 8 Outline for Institutional Grants Proposal ............................................................................... 10 Institutional Profile .................................................................................................................... 13 Funded Projects: Reporting Requirements ............................................................................. 17 1 United Board for Christian Higher Education in Asia 2016-17 Institutional Grants Program Guidelines for Proposals The United Board for Christian Higher Education in Asia (United Board) has long promoted whole person education (WPE) in the tradition of the liberal arts colleges and universities in Asia. WPE addresses the varied academic, professional, personal, and spiritual needs of students. It empowers students for their own personal and professional growth, and nurtures a sense of responsibility that encourages them to apply their knowledge in -

COMPETITION for EXCHANGE STUDIES at Non-EU/EEA COUNTRIES (Erasmus+ and VMU Bilateral Exchange)1
ATTENTION TO ALL VMU STUDENTS! COMPETITION FOR EXCHANGE STUDIES AT non-EU/EEA COUNTRIES (Erasmus+ and VMU Bilateral Exchange)1 Students are invited to participate in a competition for one semester exchange studies at non- EU/EEA countries with Erasmus+ or VMU Mobility scholarship. Students have to submit completed online application form (Outgoing – Application for Bilateral and Erasmus Study Exchange) until 1st of March, 2020 Selection criteria: compatibility between the plan for studies or research at the Higher Education Institution abroad and the study programme at VMU; motivation; results of studies or research during the last two semesters (for VMU Mobility scholarship GPA should be no less than 8.0); good knowledge of the language in which lectures will be taught. Selected students will receive Erasmus+ or VMU Mobility scholarship. Students will be personally informed via email about the results of first selection stage and invitation to second stage – interview. More information about: Erasmus+ studies VMU Bilateral Exchange Contact Erasmus+ coordinators at Contact coordinator International Cooperation Department: International Cooperation Department Eglė Januškevičienė Vaidas Dačiola E-mail: [email protected] E-mail: [email protected] Phone: 8 37 327 981 Phone: 8 37 327 981 Education Academy Sofija Pivoriūnienė E-mail: [email protected] Phone: 8 5 275 8113 Agriculture Academy Raimundas Rukuiža E-mail: [email protected] Phone: 8 37 752 398 1 Partner countries: Western Balkans, Eastern Partnership countries, Russian Federation, South-Mediterranean countries, Asia countries, Central Asia countries, Latin America countries and other countries. COMPETITION FOR 2020/2021 AUTUMN SEMESTER: VMU mobility scholarship 450 – 550 Eur / month (Size of the scholarship depends on the country groups. -

Academic Collaboration in the Field of Development Cooperation : a Case of South Korea
Academic Collaboration in the field of development cooperation : A case of South Korea DR. SUNG GYU KIM (RESEARCH FELLOW, SEOUL NATIONAL UNIVERSITY ASIA CENTER) Ⅰ Introduction ‘What is academic collaboration?‘ : enlargement of participating ways, channels, opportunities or methods of university or another academic organization in the field of international development cooperation. ◦ Introduction of the participating types of Korean academic organizations in terms of development cooperation ◦ mention about challenges of academic collaboration in South Korea. Ⅱ Status of International cooperation of Korean universities MOU status of Korean Universities (Top 20, number) China 1251 France 108 USA 733 England 103 Japan 498 Canada 93 Philippines 167 Thailand 90 Vietnam 160 Mongolia 84 Russia 159 India 71 Taiwan 133 Malaysia 59 Germany 116 Spain 57 Australia 114 Kazakhstan 47 Indonesia 111 Mexico 44 Source: Jang, 2014: 135 current status : mainly engaged with neighbor countries (China and Japan), advanced countries. the universities in developing countries such as the Philippines, Vietnam and Indonesia. academic exchanges (cooperation) are concentrated mainly in the English-speaking countries, in Korea's academic interests areas (Southeast Asia), and in the countries which more developed in terms of economic aspect. This trend is highly relevant to the effectiveness of the business. Ⅲ Types of academic collaboration in the field of development cooperation four categories First type includes collaborative research and social survey from the perspective of development cooperation. • include a construction project of database and statistical infrastructure. • For example, the Seoul National University Asia Center (SNUAC) is set up as a research project in the local poverty area in Blacan, Philippines. Types of academic collaboration Second type is an academic exchange program through workshops, seminars and forum etc. -

Soongsil University International Programs 03 02 Soongsil University
Soongsil University Soongsil University International International Programs Programs 02 01 Welcome Dear Students; It is with great pleasure and pride that I welcome you on your journey. Studying abroad cannot only be challenging but also an extremely rewarding experience, and one you will never forget. You probably have many questions about coming to study in a new country. Therefore, this guide has been designed to answer your many questions and help you prepare for your journey at Soongsil. We want to assure you that both the university staff and students will be available to assist you. If you have further questions, please do not hesitate to contact our office. We look forward to meeting you soon. Office of International Relations Soongsil University International Programs 03 02 Soongsil University Soongsil University is a private, Christian university located in Seoul, Korea. Since its establishment in 1897 in Pyeongyang by an American missionary, Dr. William M. Baird (1862- 1931), Soongsil University has played a leading role in the Korean national movement while also serving as a pioneer in the specialization and diversification of Korean education. Throughout Soongsil University’s over one hundred and ten year history, it has endeavored to preserve its founding philosophy of ‘Truth and Service.’ A philosophy derived indirectly from its name; Soong ( ), roughly meaning 崇 revering God with Sil ( ), truth and integrity. 實 Starting from its roots in Dr. Baird’s residence, Soongsil University strives to make every effort to provide quality education and services to its students, focusing specifically on cultivating global leaders and competent professionals who can lead Korea into the twenty-first century. -

2016-2017 United Board Institutional Grants Program Eligible Institutions
2016-2017 United Board Institutional Grants Program Eligible Institutions The institutions listed below have received a United Board grant within the last five years and are eligible to apply for a 2016 institutional grant. If your college or university is not listed below, and you are interested in applying for a grant, please contact the United Board program officer for your region to discuss potential eligibility (see page 5). Cambodia India Royal University of Phnom Penh All India Association for Christian Higher Education China The American College Central China Normal University Asian Centre for Cross-Cultural Studies Chinese Academy of Sciences Bishop Heber College Fudan University Christ University Fujian Hwa Nan Women's College Dharmaram Vidya Kshetram Bangalore Ginling Women's College, Nanjing Normal Indian Centre for Research & Development University of Community Education Guizhou Normal University Karunya University Institute of World Religions, Chinese Lady Doak College Academy of Social Sciences Madras Christian College Nanjing University Salesian College Ocean University of China Scottish Church College Peking University St. Ann's College of Education Renmin University of China Stella Maris College Shaanxi Normal University Union Christian College Shandong University University of Madras Sichuan University Women's Christian College Suzhou University Yunnan University Indonesia Zhongshan University Artha Wacana Christian University Association of Christian Universities and Hong Kong Colleges in Asia (ACUCA) The Chinese University -

KJMW2017 Technical Program List Remark : in the Bracket () Is The
KJMW2017 Technical Program list Remark : in the bracket () is the affiliation of the first author’s 11th Dec 10:45-11:00 <Post-dead line paper> (Chair : Koji Yamanaka, Mitsubishi Electric Corp.) Y.Gui, K. Norishima, M. Motoyoshi, S. Kameda and N. Suematsu (Tohoku University) “SNR Measurement of direct RF undersampling receiver for 28GHz band satellite communication” 11:00-11:20 Welcome Remarks <Plenary Talk> (Chair : Futoshi Kuroki, National Institute of Technology, Kure College) 11:20-12:00 Noriharu Suematsu (Tohoku University) “Direct Digital RF Technologies for Beyond Nyquist Frequency Range” 12:00-13:00 Lunch <Measurement Technique> (Chair : Koji Yamanaka, Mitsubishi Electric Corp.) 13:00-13:30 [Invited Talk] Toshiyuki Yakabe (The University of Electro-Communications) “Microwave Engineering for Students and Young Researchers” 13:30-13:45 Kouji Shibata (Department of Electrical and Electronic Systems, Hachinohe Institute of Technology) “A comparative formula without using a short termination for dielectric measurement in liquids via the open-ended cut-off waveguide reflection method” 13:45-14:00 Xiangyu Chen, Toshikazu Sekine and Yasuhiro Takahashi (Gifu University) “Estimation of Induced Positions of External Electromagnetic Fields by the Waveform at Both Ends of Transmission Line” 14:00-14:15 Coffee Break <Active Components> (Chairs : Jae-Sung Rieh, Korea University and Ryo Ishikawa, The University of Electro-Communications) 14:15-14:30 Dang-Duy Ninh, Ha-Van Nam, Chulhun Seo (Soongsil University) “A Concurrent Dual-Band Class-E Power -

ACUCA 2Nd Qtr 2007
AA CC UU CC AA NN EE WW SS http://www.acuca.net ASSOCIATION OF CHRISTIAN UNIVERSITIES AND COLLEGES IN ASIA “Committed to the mission of Christian higher education of uniting all men in the community of service and fellowship.” Volume VII No. 2 April-June 2007 ACUCA MEMBER INSTITUTIONS Message from the President HONGKONG Chung Chi College, CUHK Hong Kong Baptist University ast July 3, the Ateneo de Manila University held Lingnan University its Second Ateneo MVP Annual Leadership Forum. INDONESIA Parahyangan Catholic University LSponsored by the Chairman of the Board of Trustees, Petra Christian University Manuel V. Pangilinan, who is also Chairman of Philippine Satya Wacana Christian University Universitas Kristen Indonesia Long Distance Telephone (PLDT), it invited as speaker Maranatha Christian University Aleksander Kwasniewski, President of Poland, 1995-2005. Duta Wacana Christian University President Kwasniewski gave an excellent address, Soegijapranata Catholic University Universitas Pelita Harapan speaking of the challenge of managing Poland’s democratic Krida Wacana Christian University transition and bringing Poland into NATO and the European Universitas Atma Jaya Yogyakarta JAPAN Union. He stressed the importance of dialogue and reaching International Christian University out to all, friend or foe, so the nation and community can Kwansei Gakuin University come together. Meiji Gakuin University Nanzan University The audience was composed of over 1,000 student Doshisha University leaders from different universities in Manila. What struck us Aoyama Gakuin University St. Andrew’s University was how engaged the student leaders were. The question- J.F. Oberlin University and-answer period went on for over an hour and a half and Tohoku Gakuin University they wanted more. -

On the 3Rd International Education Quality Assurance System(IEQAS)
Soongsil University Achieved 'Excellent Certification' on the 3rd International Education Quality Assurance System(IEQAS) Soongsil University has obtained the highest level of "excellent certification" in the third cycle (2021.3- 2023.2) of the International Education Quality Assurance System(IEQAS) analysis conducted by the Korean government (Ministry of Education). This means that the Korean government (Ministry of Education) guarantees that Soongsil University has excellent quality of education for undergraduate, graduate and Korean language programs. A total of 23 four-year universities, including Soongsil University, received "excellent certification" in this year's third-cycle of certification, and only the top 15 percent of the 150 four-year universities nationwide received an "excellent certification." ※ What is the International Education Quality Assurance System? The Korean government (Ministry of Education) evaluates the internationalization capabilities of universities using10 indicators and certifies them as "excellent certification university", which simplifies visa issuance process for international students, gives them a point when selecting GKS universities. ※ Excellent certification university of the 3rd IEQAS Classification Universities Soongsil University, Gangneung Wonju University, Kookmin University, Mokwon University, Seoul New certification Women's University, Sungshin Women's University, Suncheonhyang University, Changwon (10 universities) University, Korea Advanced Institute of Science and Technology, Hongik University 2018 Certification Sehan University, Pohang University of Science and Technology. (2 universities) Catholic University, Korea University, Dankook University, Daejeon University, Myongji 2019 Certification University, Sogang University, Seoul National University, Yonsei University (Mirae (11 Universities) Campus), Jeonbuk National University, Hanyang University(ERICA) .