The Tim Ferriss Show Transcripts Episode 74: Samy Kamkar, Part 1 Show Notes and Links at Tim.Blog/Podcast
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Secure Authentication Mechanisms for the Management Interface in Cloud Computing Environments
UNIVERSITY OF BEIRA INTERIOR Engineering Secure Authentication Mechanisms for the Management Interface in Cloud Computing Environments Liliana Filipa Baptista Soares Dissertation Submitted in Partial Fulfillment of the Requirement for the Degree of Master of Science in Computer Science and Engineering (2nd Cycle Studies) Supervised by Prof. Dr. Pedro Ricardo Morais Inácio Covilhã, October 2013 ii To my beloved family, especially to my grandparents. iv Acknowledgements The endurance to overcome obstacles or predisposed objectives in life depends on how each one envisages them. It is up to each one to extract the most valuable lessons from each journey and transform them into knowledge. Without the guidance and support of very particular persons, it would have not been possible to accomplish this dissertation and many lessons would have not been learned. I hereby thank my mother and father, to whom I am mostly grateful, for helping me to achieve my goals, particularly those of my academic quest. I would like to thank my sister, Cátia, for her immeasurable support, and my grandparents, for always demonstrating their love and will to live. I am also grateful to my supervisor, Prof. Dr. Pedro Ricardo Morais Inácio, not only for the help, charisma and readiness he demonstrated to complete this stage, but also for being resourceful in aiding throughout other steps of my professional life. I also acknowledge the Multimedia Signal Processing – Covilhã Group at the Instituto de Telecomunicações, which hosted this dis- sertation work and the final project of my first degree, and the research folk in it, particularly Miguel Neto for lending me a smartcard reader temporarily. -

A the Hacker
A The Hacker Madame Curie once said “En science, nous devons nous int´eresser aux choses, non aux personnes [In science, we should be interested in things, not in people].” Things, however, have since changed, and today we have to be interested not just in the facts of computer security and crime, but in the people who perpetrate these acts. Hence this discussion of hackers. Over the centuries, the term “hacker” has referred to various activities. We are familiar with usages such as “a carpenter hacking wood with an ax” and “a butcher hacking meat with a cleaver,” but it seems that the modern, computer-related form of this term originated in the many pranks and practi- cal jokes perpetrated by students at MIT in the 1960s. As an example of the many meanings assigned to this term, see [Schneier 04] which, among much other information, explains why Galileo was a hacker but Aristotle wasn’t. A hack is a person lacking talent or ability, as in a “hack writer.” Hack as a verb is used in contexts such as “hack the media,” “hack your brain,” and “hack your reputation.” Recently, it has also come to mean either a kludge, or the opposite of a kludge, as in a clever or elegant solution to a difficult problem. A hack also means a simple but often inelegant solution or technique. The following tentative definitions are quoted from the jargon file ([jargon 04], edited by Eric S. Raymond): 1. A person who enjoys exploring the details of programmable systems and how to stretch their capabilities, as opposed to most users, who prefer to learn only the minimum necessary. -

2016 8Th International Conference on Cyber Conflict: Cyber Power
2016 8th International Conference on Cyber Conflict: Cyber Power N.Pissanidis, H.Rõigas, M.Veenendaal (Eds.) 31 MAY - 03 JUNE 2016, TALLINN, ESTONIA 2016 8TH International ConFerence on CYBER ConFlict: CYBER POWER Copyright © 2016 by NATO CCD COE Publications. All rights reserved. IEEE Catalog Number: CFP1626N-PRT ISBN (print): 978-9949-9544-8-3 ISBN (pdf): 978-9949-9544-9-0 CopyriGHT AND Reprint Permissions No part of this publication may be reprinted, reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written permission of the NATO Cooperative Cyber Defence Centre of Excellence ([email protected]). This restriction does not apply to making digital or hard copies of this publication for internal use within NATO, and for personal or educational use when for non-profit or non-commercial purposes, providing that copies bear this notice and a full citation on the first page as follows: [Article author(s)], [full article title] 2016 8th International Conference on Cyber Conflict: Cyber Power N.Pissanidis, H.Rõigas, M.Veenendaal (Eds.) 2016 © NATO CCD COE Publications PrinteD copies OF THIS PUBlication are availaBLE From: NATO CCD COE Publications Filtri tee 12, 10132 Tallinn, Estonia Phone: +372 717 6800 Fax: +372 717 6308 E-mail: [email protected] Web: www.ccdcoe.org Head of publishing: Jaanika Rannu Layout: Jaakko Matsalu LEGAL NOTICE: This publication contains opinions of the respective authors only. They do not necessarily reflect the policy or the opinion of NATO CCD COE, NATO, or any agency or any government. -

How to Analyze the Cyber Threat from Drones
C O R P O R A T I O N KATHARINA LEY BEST, JON SCHMID, SHANE TIERNEY, JALAL AWAN, NAHOM M. BEYENE, MAYNARD A. HOLLIDAY, RAZA KHAN, KAREN LEE How to Analyze the Cyber Threat from Drones Background, Analysis Frameworks, and Analysis Tools For more information on this publication, visit www.rand.org/t/RR2972 Library of Congress Cataloging-in-Publication Data is available for this publication. ISBN: 978-1-9774-0287-5 Published by the RAND Corporation, Santa Monica, Calif. © Copyright 2020 RAND Corporation R® is a registered trademark. Cover design by Rick Penn-Kraus Cover images: drone, Kadmy - stock.adobe.com; data, Getty Images. Limited Print and Electronic Distribution Rights This document and trademark(s) contained herein are protected by law. This representation of RAND intellectual property is provided for noncommercial use only. Unauthorized posting of this publication online is prohibited. Permission is given to duplicate this document for personal use only, as long as it is unaltered and complete. Permission is required from RAND to reproduce, or reuse in another form, any of its research documents for commercial use. For information on reprint and linking permissions, please visit www.rand.org/pubs/permissions. The RAND Corporation is a research organization that develops solutions to public policy challenges to help make communities throughout the world safer and more secure, healthier and more prosperous. RAND is nonprofit, nonpartisan, and committed to the public interest. RAND’s publications do not necessarily reflect the opinions of its research clients and sponsors. Support RAND Make a tax-deductible charitable contribution at www.rand.org/giving/contribute www.rand.org Preface This report explores the security implications of the rapid growth in unmanned aerial systems (UAS), focusing specifically on current and future vulnerabilities. -

(You Gotta) Fight for Your Right (To Party!) 3 AM ± Matchbox Twenty. 99 Red Ballons ± Nena
(You Gotta) Fight For Your Right (To Party!) 3 AM ± Matchbox Twenty. 99 Red Ballons ± Nena. Against All Odds ± Phil Collins. Alive and kicking- Simple minds. Almost ± Bowling for soup. Alright ± Supergrass. Always ± Bon Jovi. Ampersand ± Amanda palmer. Angel ± Aerosmith Angel ± Shaggy Asleep ± The Smiths. Bell of Belfast City ± Kristy MacColl. Bitch ± Meredith Brooks. Blue Suede Shoes ± Elvis Presely. Bohemian Rhapsody ± Queen. Born In The USA ± Bruce Springstein. Born to Run ± Bruce Springsteen. Boys Will Be Boys ± The Ordinary Boys. Breath Me ± Sia Brown Eyed Girl ± Van Morrison. Brown Eyes ± Lady Gaga. Chasing Cars ± snow patrol. Chasing pavements ± Adele. Choices ± The Hoosiers. Come on Eileen ± Dexy¶s midnight runners. Crazy ± Aerosmith Crazy ± Gnarles Barkley. Creep ± Radiohead. Cupid ± Sam Cooke. Don¶t Stand So Close to Me ± The Police. Don¶t Speak ± No Doubt. Dr Jones ± Aqua. Dragula ± Rob Zombie. Dreaming of You ± The Coral. Dreams ± The Cranberries. Ever Fallen In Love? ± Buzzcocks Everybody Hurts ± R.E.M. Everybody¶s Fool ± Evanescence. Everywhere I go ± Hollywood undead. Evolution ± Korn. FACK ± Eminem. Faith ± George Micheal. Feathers ± Coheed And Cambria. Firefly ± Breaking Benjamin. Fix Up, Look Sharp ± Dizzie Rascal. Flux ± Bloc Party. Fuck Forever ± Babyshambles. Get on Up ± James Brown. Girl Anachronism ± The Dresden Dolls. Girl You¶ll Be a Woman Soon ± Urge Overkill Go Your Own Way ± Fleetwood Mac. Golden Skans ± Klaxons. Grounds For Divorce ± Elbow. Happy ending ± MIKA. Heartbeats ± Jose Gonzalez. Heartbreak Hotel ± Elvis Presely. Hollywood ± Marina and the diamonds. I don¶t love you ± My Chemical Romance. I Fought The Law ± The Clash. I Got Love ± The King Blues. I miss you ± Blink 182. -

Asheville, Tenth Month 2009
Southern Appalachian Young Friends Epistle Asheville October, 2009 This weekend was amazing. Everything from the maze to the tacos and the dancing was great. I hadn’t really heard of the Jerk until now but its really fun, even though I can barely do it yet. I got more sleep this retreat than most which is good and I wish we could all just stay here and not go back to school. I missed the last one so this time I got to see a lot of 2bies who had come to the last one. Jacob and Xavier’s dancing was great lo,=) I had fun talking with Heather and Chantal is really awesome. Anyway, I hope the November one is just as good and everyone and more comes. ~ Emanuel Huber Feely SAYF was fun this weekend. For me it was a relaxing weekend compared to my first retreat. This is my second and I feel like you all are like family to me. Although I was betrayed four times by a certain someone and once by another certain someone I forgive them. But watch your backs next time I come here. I will have revenge! I love you guys. You take me away from the real world and put me in a world where everyone’s happy and always having fun. To Chrissy I love you and thanks for allowing me to tag along again. To Santha thanks for my neck-a-lace. To Katie thanks for hugs. And to everyone else thanks for accepting me. I still cannot write passive aggressive haikus but I wrote a pretty beasty poem. -

Rhythms of Relation: Black Popular Music and Mobile Technologies
Rhythms of Relation: Black Popular Music and Mobile Technologies Alexander G. Weheliye In this essay I focus on the singular performances of the interface between (black) subjectivity and informational technologies in popular music, ask- ing how these performances impact current definitions of the technologi- cal. After a brief examination of those aspects of mobile technologies that gesture beyond disembodied communication, I turn to the multifarious manifestations of techno-informational gadgets (especially cellular/mobile telephones) in contemporary R&B, a genre that is acutely concerned, both in content and form, with the conjuring of interiority, emotion, and affect. The genre’s emphasis on these aspects provides an occasion to analyze how technology thoroughly permeates spheres that are thought to represent the hallmarks of humanist hallucinations of humanity. I outline the extensive and intensive interdependence of contemporary (black) popular music and mobile technologies in order to ascertain how these sonic formations refract communication and embodiment and ask how this impacts rul- ing definitions of the technological. The first group of musical examples surveyed consists of recordings released between 1999 and 2001; the sec- ond set are recordings from years 2009–2010. Since ten years is almost an eternity in the constantly changing universes of popular music and mobile technologies, analyzing the sonic archives from two different historical moments allows me to stress the general co-dependence of mobiles and music without silencing the breaks that separate these “epochs.” Finally, I gloss a visual example that stages overlooked dimensions of mobile tech- nologies so as to amplify the rhythmic flow between the scopic and the sonic. -

Technical Design of Open Social Web for Crowdsourced Democracy
Project no. 610349 D-CENT Decentralised Citizens ENgagement Technologies Specific Targeted Research Project Collective Awareness Platforms D4.3 Technical Design of Open Social Web for Crowdsourced Democracy Version Number: 1 Lead beneficiary: OKF Due Date: 31 October 2014 Author(s): Pablo Aragón, Francesca Bria, Primavera de Filippi, Harry Halpin, Jaakko Korhonen, David Laniado, Smári McCarthy, Javier Toret Medina, Sander van der Waal Editors and reviewers: Robert Bjarnason, Joonas Pekkanen, Denis Roio, Guido Vilariño Dissemination level: PU Public X PP Restricted to other programme participants (including the Commission Services) RE Restricted to a group specified by the consortium (including the Commission Services) CO Confidential, only for members of the consortium (including the Commission Services) Approved by: Francesca Bria Date: 31 October 2014 This report is currently awaiting approval from the EC and cannot be not considered to be a final version. FP7 – CAPS - 2013 D-CENT D4.3 Technical Design of Open Social Web for Crowdsourced Democracy Contents 1 Executive Summary ........................................................................................................................................................ 6 Description of the D-CENT Open Democracy pilots ............................................................................................. 8 Description of the lean development process .......................................................................................................... 10 Hypotheses statements -

Stuxnet : Analysis, Myths and Realities
ACTUSÉCU 27 XMCO David Helan STUXNET : ANALYSIS, MYTHS AND REALITIES CONTENTS Stuxnet: complete two-part article on THE virus of 2010 Keyboard Layout: analysis of the MS10-073 vulnerability used by Stuxnet Current news: Top 10 hacking techniques, zero-day IE, Gsdays 2010, ProFTPD... Blogs, softwares and our favorite Tweets... This document is the property of XMCO Partners. Any reproduction is strictly prohibited. !!!!!!!!!!!!!!!!! [1] Are you concerned by IT security in your company? ACTU SÉCU 27 XMCO Partners is a consultancy whose business is IT security audits. Services: Intrusion tests Our experts in intrusion can test your networks, systems and web applications Use of OWASP, OSSTMM and CCWAPSS technologies Security audit Technical and organizational audit of the security of your Information System Best Practices ISO 27001, PCI DSS, Sarbanes-Oxley PCI DSS support Consulting and auditing for environments requiring PCI DSS Level 1 and 2 certification. CERT-XMCO: Vulnerability monitoring Personalized monitoring of vulnerabilities and the fixes affecting your Information System CERT-XMCO: Response to intrusion Detection and diagnosis of intrusion, collection of evidence, log examination, malware autopsy About XMCO Partners: Founded in 2002 by experts in security and managed by its founders, we work in the form of fixed-fee projects with a commitment to achieve results. Intrusion tests, security audits and vulnerability monitoring are the major areas in which our firm is developing. At the same time, we work with senior management on assignments providing support to heads of information- systems security, in drawing up master plans and in working on awareness-raising seminars with several large French accounts. -
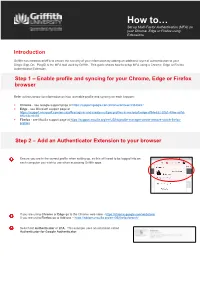
How to Install MFA Browser Authenicator Extension
How to… Set up Multi-Factor Authentication (MFA) on your Chrome, Edge or Firefox using Extensions Introduction Griffith has introduced MFA to ensure the security of your information by adding an additional layer of authentication to your Single Sign-On. PingID is the MFA tool used by Griffith. This guide shows how to setup MFA using a Chrome, Edge or Firefox Authenticator Extension. Step 1 – Enable profile and syncing for your Chrome, Edge or Firefox browser Refer to links below for information on how to enable profile and syncing for each browser: • Chrome - see Google support page at https://support.google.com/chrome/answer/2364824? • Edge - see Microsoft support page at https://support.microsoft.com/en-us/office/sign-in-and-create-multiple-profiles-in-microsoft-edge-df94e622-2061-49ae-ad1d- 6f0e43ce6435 • Firefox - see Mozilla support page at https://support.mozilla.org/en-US/kb/profile-manager-create-remove-switch-firefox- profiles Step 2 – Add an Authenticator Extension to your browser Ensure you are in the correct profile when setting up, as this will need to be logged into on each computer you wish to use when accessing Griffith apps. If you are using Chrome or Edge go to the Chrome web store - https://chrome.google.com/webstore/ If you are using Firefox go to Add-ons – https://addons.mozilla.org/en-GB/firefox/search/ Search for Authenticator or 2FA. This example uses an extension called Authenticator for Google Authenticator. Select Add Select Add Extension Your browser will confirm the extension has been added. Step 3 – Set up the Authenticator Extension as the primary authenticating method Once the Authenticator extension is added, click on the extension icon then click on the Pencil icon. -

Trey Songz LOL
LOL :-) Trey Songz I Luvvv Fisher Price 804 335 0051 (LOL smiley face LOL smiley face... Soulja boy Tell'Em) 804 335 0051 (GUCCI... LOL smiley face, LOL smiley face) Shawty just text me, say she wanna sex me (LOL smiley face, LOL smiley face) Shawty sent a Twit pic saying come and get this (LOL smiley face, LOL smiley face) Shawty called me phone I was busy (I was busy yup) Cruisin' in that Benz around the city (yup) Then I felt my phone buzz, I know that she like thugs I'm a bad boy like Diddy (take that) Then she sent a text that had said, "baby, I'm at home" Then she sent another one that said she's all alone So I texted her a smiley face and said, "let's do the grown" She said, "LOL boy you crazy, come on" Then she said "actually, you ain't gotta ask me" Sent that little face with the tongue 'cause I'm nasty I'm on my way (way), girl I can't wait (wait) Twitter me a picture, lemme see that OK Shawty just text me, say she wanna sex me (LOL smiley face, LOL smiley face) Shawty sent a Twit pic saying come and get this (LOL smiley face, LOL smiley face) Go to my page and follow And if you got a body like a Coke bottle Shawty sent a Twit pic (it's me Gucci) saying come and get this (LOL smiley face, LOL smiley face) You got me shawty, text Mane Send ya boy a smiley face Gucci Mane, X rated we can make a sex tape Pics on my iPhone Gucci on her iPod When she turn around, ass make ya say oh God Mami real beautiful Manicured cuticles Office job Student girl Holding down her cubicle And she got my number tell her man that's like a miracle Said she love my swag Pull up 6's on my vehicle G.A. -

Anti-Virus Issues, Malicious Software and Internet Attacks for Non-Technical Audiences
Known Knowns, Known Unknowns and Unknown Unknowns: Anti-virus issues, malicious software and Internet attacks for non-technical audiences By Daniel Bilar Introduction [Heading] The risks associated with the internet have changed significantly. A recent study claims that a typical Microsoft Windows machine is subjected to autonomous infiltration attempts - not just mere pings and probes - from worms and botnets looking for clients once every six minutes.1 Stealth – not exhibitionism or hubris – characterizes this breed of attacks and concomitantly deployed malicious software. Unbeknownst even to experienced human operators, surreptitious attacks are able to insert malicious code deep within the bowels of individual computers and the wider supporting internet communication and control infrastructure such as wireless access points, home routers, and domain name servers.2 In addition to stealth, social engineering via e-mail, Instant 1 Gabor Szappanos, ‘A Day in the Life of An Average User’, Virus Bulletin, January 2009, 10-13, available at http://www.virusbtn.com/. 2 Most users do not bother to change the default passwords on home devices such as routers. Browser vulnerabilities can then be exploited by malicious software to alter the DNS settings of the router, thereby directing any name lookup query to a DNS of the attacker’s choice. This may be used to spoof a bank web site, for instance. See Sid Stamm, Zulfikar Ramzan and Markus Jakobsson, ‘Drive-By Pharming’, Lecture Notes in Computer Science 4861, (Springer, 2007), 495-506 and Hristo Bojinov, Elie Bursztein, Eric Lovett and Dan Boneh, ‘Embedded Management Interfaces: Emerging Massive Insecurity’, Blackhat Technical Briefing, Blackhat USA 2009 (Las Vegas, USA, August 2009), available at http://www.blackhat.com/presentations/bh-usa- 09/BOJINOV/BHUSA09-Bojinov-EmbeddedMgmt-PAPER.pdf.