Technical Design of Open Social Web for Crowdsourced Democracy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Secure Authentication Mechanisms for the Management Interface in Cloud Computing Environments
UNIVERSITY OF BEIRA INTERIOR Engineering Secure Authentication Mechanisms for the Management Interface in Cloud Computing Environments Liliana Filipa Baptista Soares Dissertation Submitted in Partial Fulfillment of the Requirement for the Degree of Master of Science in Computer Science and Engineering (2nd Cycle Studies) Supervised by Prof. Dr. Pedro Ricardo Morais Inácio Covilhã, October 2013 ii To my beloved family, especially to my grandparents. iv Acknowledgements The endurance to overcome obstacles or predisposed objectives in life depends on how each one envisages them. It is up to each one to extract the most valuable lessons from each journey and transform them into knowledge. Without the guidance and support of very particular persons, it would have not been possible to accomplish this dissertation and many lessons would have not been learned. I hereby thank my mother and father, to whom I am mostly grateful, for helping me to achieve my goals, particularly those of my academic quest. I would like to thank my sister, Cátia, for her immeasurable support, and my grandparents, for always demonstrating their love and will to live. I am also grateful to my supervisor, Prof. Dr. Pedro Ricardo Morais Inácio, not only for the help, charisma and readiness he demonstrated to complete this stage, but also for being resourceful in aiding throughout other steps of my professional life. I also acknowledge the Multimedia Signal Processing – Covilhã Group at the Instituto de Telecomunicações, which hosted this dis- sertation work and the final project of my first degree, and the research folk in it, particularly Miguel Neto for lending me a smartcard reader temporarily. -

Pega Customer Service Reference Guide Iii
Pega Customer Service 7.1.4 Version REFERENCE GUIDE © Copyright 2015 Pegasystems Inc., Cambridge, MA All rights reserved. Trademarks For Pegasystems Inc. trademarks and registered trademarks, all rights reserved. Other brand or product names are trademarks of their respective holders. Consult the 718ThirdPartyLicense.pdf file on the installation media for information about the software delivered with the product. Notices This publication describes and/or represents products and services of Pegasystems Inc. It may contain trade secrets and proprietary information that are protected by various federal, state, and international laws, and distributed under licenses restricting their use, copying, modification, distribution, or transmittal in any form without prior written authorization of Pegasystems Inc. This publication is current as of the date of publication only. Changes to the publication may be made from time to time at the discretion of Pegasystems Inc. This publication remains the property of Pegasystems Inc. and must be returned to it upon request. This publication does not imply any commitment to offer or deliver the products or services described herein. This publication may include references to Pegasystems Inc. product features that have not been licensed by you or your company. If you have questions about whether a particular capability is included in your installation, please consult your Pegasystems Inc. services consultant. Although Pegasystems Inc. strives for accuracy in its publications, any publication may contain inaccuracies or typographical errors, as well as technical inaccuracies. Pegasystems Inc. may make improvements and/or changes to the publication at any time. Any references in this publication to non-Pegasystems websites are provided for convenience only and do not serve as an endorsement of these websites. -

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -
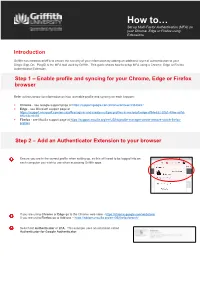
How to Install MFA Browser Authenicator Extension
How to… Set up Multi-Factor Authentication (MFA) on your Chrome, Edge or Firefox using Extensions Introduction Griffith has introduced MFA to ensure the security of your information by adding an additional layer of authentication to your Single Sign-On. PingID is the MFA tool used by Griffith. This guide shows how to setup MFA using a Chrome, Edge or Firefox Authenticator Extension. Step 1 – Enable profile and syncing for your Chrome, Edge or Firefox browser Refer to links below for information on how to enable profile and syncing for each browser: • Chrome - see Google support page at https://support.google.com/chrome/answer/2364824? • Edge - see Microsoft support page at https://support.microsoft.com/en-us/office/sign-in-and-create-multiple-profiles-in-microsoft-edge-df94e622-2061-49ae-ad1d- 6f0e43ce6435 • Firefox - see Mozilla support page at https://support.mozilla.org/en-US/kb/profile-manager-create-remove-switch-firefox- profiles Step 2 – Add an Authenticator Extension to your browser Ensure you are in the correct profile when setting up, as this will need to be logged into on each computer you wish to use when accessing Griffith apps. If you are using Chrome or Edge go to the Chrome web store - https://chrome.google.com/webstore/ If you are using Firefox go to Add-ons – https://addons.mozilla.org/en-GB/firefox/search/ Search for Authenticator or 2FA. This example uses an extension called Authenticator for Google Authenticator. Select Add Select Add Extension Your browser will confirm the extension has been added. Step 3 – Set up the Authenticator Extension as the primary authenticating method Once the Authenticator extension is added, click on the extension icon then click on the Pencil icon. -

The W3C Social Web Activity
Standardizing the Social Web: The W3C Social Web Activity Harry Halpin World Wide Web Consortium/MIT, 32 Vassar Street Cambridge, MA 02139 USA [email protected] Abstract. The focus of the Social Activity is on making “social” a first-class citizen of the Open Web Platform by enabling standardized protocols, APIs, and an architecture for standardized communication among Social Web applications. These technologies are crucial for both federated social networking and the success of social business between and within the enterprise. Keywords: decentralization, social web, RDF 1Introduction The focus of the W3C Social Activity is on making “social” a first-class citizen of the Open Web Platform by enabling standardized protocols, APIs,andan architecture for standardized communication among Social Web applications. These technologies are crucial for both federated social networking and social business between and within the enterprise and can be built on top of Linked Data. This work will knit together via interoperable standards a number of industry platforms, including IBM Connections, SAP Jam, Jive, SugarCRM, and grassroots efforts such as IndieWeb.1 The mission of the Social Web Working Group,2 part of the Social Activ- ity,3 is to define the technical protocols, Semantic Web vocabularies, andAPIs to facilitate access to social functionality as part of the Open Web Platform. These technologies should allow communication between independent systems, federation (also called “decentralization”) being part of the design. The Working Group is chaired by Tantek Celik (Mozilla), Evan Prodromou (E14N), and Ar- naud Le Hors (IBM). Also part of the Social Activity is the Social Interest Group 4 focuses on messaging and co-ordination in the larger space. -

AN EXPLORATORY STUDY of SCIENCE BLOGGERS Degree Candidate
ABSTRACT Title of Thesis: OPENING UP THE CONVERSATION: AN EXPLORATORY STUDY OF SCIENCE BLOGGERS Degree Candidate: Gregory Michael Masters Degree and Year: Master of Arts, 2013 Thesis Directed by: Dr. Carol L. Rogers Philip Merrill College of Journalism Over the past decade, science blogs have experienced tremendous growth and changes in organization, becoming an important part of what researchers have called the “evolving science media ecosystem.” This thesis explores the practices and perceptions of science bloggers through 20 in-depth interviews and through a review of the blogs themselves. The research suggests areas where this medium is having a unique impact on how science communication occurs. The interview results revealed that science bloggers are motivated mainly by enjoyment, have a wide variety of routines and reporting/writing processes, strive to incorporate a personal touch, and are very engaged with readers and fellow writers through social media. This research found that science blogs have important roles in complementing other forms of science communication, opening aspects of science to wider view, promoting conversations about science through blog comments and social media, and exploiting digital tools to enhance communication. OPENING UP THE CONVERSATION: AN EXPLORATORY STUDY OF SCIENCE BLOGGERS by Gregory Michael Masters Thesis submitted to the Faculty of the Graduate School of the University of Maryland, College Park, in partial fulfillment of the requirements for the degree of Master of Arts 2013 Advisory Committee: Dr. Carol L. Rogers, Chair Dr. Ira Chinoy Carl Sessions Stepp © Copyright by Greg Masters 2013 PREFACE As teenagers, my brother and I would often drive far into Western Maryland to escape the city lights, parking at the edge of fields in the middle of nowhere to lie on the hood and peer at the stars. -

Top Comment Or Flop Comment? Predicting and Explaining User Engagement in Online News Discussions
Top Comment or Flop Comment? Predicting and Explaining User Engagement in Online News Discussions Julian Risch, Ralf Krestel Hasso Plattner Institute, University of Potsdam, Germany fi[email protected] Abstract editors. This manual effort is costly and comes on top of the task of moderating hate speech and other banned content. Comment sections below online news articles enjoy growing Major news platforms allow users to upvote comments, popularity among readers. However, the overwhelming num- ber of comments makes it infeasible for the average news but for several reasons these platforms do not use votes as a consumer to read all of them and hinders engaging discus- ranking criterion for comments. First, there is the cold start sions. Most platforms display comments in chronological or- problem: Whenever a new comment is posted, it has not yet der, which neglects that some of them are more relevant to received any upvotes. An accordingly low rank affects the users and are better conversation starters. comment’s exposure to users and reduces its chance of ever In this paper, we systematically analyze user engagement in receiving any upvotes. Moreover, such a ranking algorithm the form of the upvotes and replies that a comment receives. can easily be gamed. Malicious users can register multiple Based on comment texts, we train a model to distinguish com- accounts or collaborate to break the ranking system and up- ments that have either a high or low chance of receiving many vote comments of their favored opinion. upvotes and replies. Our evaluation on user comments from Today’s platforms refrain from using an upvote-based TheGuardian.com compares recurrent and convolutional neu- ranking algorithm and simply sort comments chronologi- ral network models, and a traditional feature-based classifier. -

Measuring Platform Effects in Digital Democracy
Measuring Platform Effects in Digital Democracy Pablo Arag´on*y Vicen¸cG´omez* Andreas Kaltenbrunnery * Universitat Pompeu Fabra y Eurecat Barcelona, Spain Barcelona, Spain Abstract. Online discussions are the essence of many social platforms on the Internet. Conversations in online forums are traditionally pre- sented in a hierarchical structure. In contrast, online social networking services usually show discussions linearly by sorting messages in chrono- logical order. How discussion networks are affected by choosing a specific view has never been investigated in the literature. In this article we present an analysis of the discussion threads in Me- neame, the most popular Spanish social news platform. In January 2015, this site turned the original linear conversation view into a hierarchical one. Our findings prove that the new interface promoted new discussion network structures. In particular, the hierarchical view increased delib- eration and reciprocity based on the rhizomatic structure of discussions. Keywords: Digital democracy, Online deliberation, Online discussion, Human-Computer Interfaces, Conversation view 1 Introduction Online social platforms are playing a key role in the communication of cur- rent societies. According to Kemp (2016), more than two billion users are ac- tively participating in social media sites. The interest in online platforms has attracted increasing attention from academia over the last decade and several studies have examined the network structure of a wide array of online digital platforms, e.g. Facebook (Ugander et al., 2011), Twitter (Kwak et al., 2010), Google+ (Magno et al., 2012), Flickr (Cha et al., 2009), Youtube (Mislove et al., 2007), Wikipedia (Laniado et al., 2011), Digg (Lerman and Ghosh, 2010) and Slashdot (G´omezet al., 2008). -

Download Google Authenticator App Download Google Authenticator App
download google authenticator app Download google authenticator app. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67aa6d6ed8c98498 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Google Authenticator 4+ Google Authenticator works with 2-Step Verification for your Google Account to provide an additional layer of security when signing in. With 2-Step Verification, signing into your account will require both your password and a verification code you can generate with this app. Once configured, you can get verification codes without the need for a network or cellular connection. Features include: - Automatic setup via QR code - Support for multiple accounts - Support for time-based and counter-based code generation - Transfer accounts between devices via QR code. To use Google Authenticator with Google, you need to enable 2-Step Verification on your Google Account. Visit http://www.google.com/2step to get started. What’s New. - Added the ability to transfer many accounts to a different device - Added the ability of search for accounts - Added the ability to turn on Privacy Screen. -
K-ICT · Ver.2017 –
http://www.tta.or.kr K-ICT Ver.2017 – /SW/ SW· - ( / , / , ), SW( , SW ), SW· ( / , ) TTA - 16142 - SD Service offering ( | ) ~'19, JTC1 SC34, IDPF, W3C ( | ) ~'19, JTC1 SC29 WG11 AR/VR App. AV App. ( ) KS X 6070-1~5 (EPUB) 3.0 , (EPUB) 3.0, (EPUB) 3.0, e-Learning App. (TTA) TTA.KO-10.0611 - Digital Signage App. Web App. , 2016-118 ( | ) ~'18, JTC1 SC29 WG11, SC24 ( | ) ~'18, JTC1 SC29 WG11 (EPUB) 3.0, (EPUB) 3.0 / SNS App. (HMD) (TTA) TTAK.OT-10.0337 - EPUB 2 , .0338 - EPUB 3.0, .0339 - EPUB , 2016-119 PC (TTA) TTAK.KO-10.0874 – (TTA) TTAK.KO-10.0317- 3.0, .0340 - EPUB 3 , .0341 - EPUB 3.0, .0342 - EPUB A/V/Data Terminal Control, (HMD) / 3.0, .0727 - EPUB , KR04-1 - EPUB3 EDUPUB , -2 - EPUB Service Info. Management (JTC1) Exploration Part # 12(Free-viewpoint TV) 1.0, -3 - EPUB 1.0, -4 - EPUB 1.0 DRM Service (JTC1) ISO/IEC 23000-13 Information technology - Call for Evidence on Free-Viewpoint Television: (JTC1) ISO/IEC 14496-10:2012 , NTP/ (ODPF) KR03-1 - EPUB 3.0.1 , -2 - EPUB 3.0.1, -3 - EPUB 3.0.1, -4 - EPUB Discovery ID Network DHCP DNS IGMP - Multimedia application format (MPEG-A) -- Part Super-Multiview and Free Navigation – update, Information technology -- Coding of 3.0.1, -5 - EPUB 3.0.1, -6 - EPUB 3.0.1 ( | ) ~'19, Web3D, JTC1 SC24 WG6/WG9, JTC1 SC29, JTC1 SC35, JTC1 SC36 MPEG / H.264, 265 audio-visual objects -- Part 10: Advanced agent Provisioning SNTP 13: Augmented reality application format, ISO/IEC Exploration Part # 12(Free-viewpoint TV) - FTV HDR (ISO TC171 SC2) ISO 32000-1 - PDF(portable document format) 23005-5 Information -

Donttagyourhate: Reading Collecting and Curating As Genres of Participation in LGBT Youth Activism on Tumblr
DIGITAL CULTURE & EDUCATION, 9(1) 2017, ISSN 1836-8301 Digital Culture & Education (DCE) Publication details, including instructions for authors http://www.digitalcultureandeducation.com/ #donttagyourhate: Reading Collecting and Curating as Genres of Participation in LGBT Youth Activism on Tumblr Jon M Wargo Wayne State University Online Publication Date: 1st February 2017 To cite this Article: Wargo, J. M. (2017). #donttagyourhate: Reading Collecting and Curating as Genres of Participation in LGBT Youth Activism on Tumblr. Digital Culture & Education, 9(1), 14-31. URL: http://www.digitalcultureandeducation.com/cms/wp-content/uploads/2017/02/wargo.pdf PLEASE SCROLL DOWN FOR ARTICLE #donttagyourhate #donttagyourhate: READING COLLECTING AND CURATING AS GENRES OF PARTICIPATION IN LGBT YOUTH ACTIVISM ON TUMBLR Jon M Wargo Abstract: Interested in the semiotic stretches youth employ to navigate (in)equality online, this paper interrogates the seemingly mundane practices of youth writing with new media to read how “collecting” and “curating” were mobilized as facets of youth activism. By focusing on curating and collecting as two forms of remediated communicative practice, this paper interrogates the taking on of what youth in a larger “connective ethnography” (Hine, 2015; 2000; Leander, 2008) called a #socialjusticewarrior stance. Zeroing in and tracing the connective lives Zeke, Camille, and Jack (all names are pseudonyms) led across their networked connections of writing, this paper illuminates how issues of race, gender expression, and queer identities converged to collect a social justice orientation into the larger Kilgore and San Miguels communities. Comparatively, I provide a counter-story from one young person (Ben) whose curated work of self-presentation fostered a more cosmopolitan version of self. -

6. Visible Conversations: Seeing Meaning Beyond Words
MIT Press on COVID-19 • The Social Machine 6. Visible Conversations: Seeing Meaning beyond Words Published on: Apr 27, 2020 Updated on: Apr 28, 2020 MIT Press on COVID-19 • The Social Machine 6. Visible Conversations: Seeing Meaning beyond Words People participate in many social activities online: they post pictures and videos, write long, impassioned articles, and battle each other in multiplayer games. The predominant social activity, however, is conversation in its many forms: email; chat; discussion postings; status updates; comments exchanged about photos, games, and articles; and so on. Though the form may vary, all share the fundamental quality of being exchanges of words among two or more people.1 Conversation is much more than a means for exchanging information. It is a form of social grooming: it is how we form and maintain ties, hold our community together, and establish social norms (Dunbar 1996).2 Like face-to-face speech, online conversation is an exchange of words among people. Yet there are significant differences. Most spoken conversations are ephemeral: the words disappear into the past as soon as they are said. Many online conversations are persistent, their text permanently preserved in an archive. Spoken conversations occur in real time: you hear what I say as I say it and can respond immediately. In contrast, many online conversations are asynchronous: I write a message, and you might not read and respond to it until hours, days, or more have passed. Asynchrony adds convenience, for I can maintain a long discussion with you, even if we are never free to meet at the same time, but it also drastically changes the rhythm of discourse.