Dao Research: Securing Data and Applications in the Cloud
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Secure Authentication Mechanisms for the Management Interface in Cloud Computing Environments
UNIVERSITY OF BEIRA INTERIOR Engineering Secure Authentication Mechanisms for the Management Interface in Cloud Computing Environments Liliana Filipa Baptista Soares Dissertation Submitted in Partial Fulfillment of the Requirement for the Degree of Master of Science in Computer Science and Engineering (2nd Cycle Studies) Supervised by Prof. Dr. Pedro Ricardo Morais Inácio Covilhã, October 2013 ii To my beloved family, especially to my grandparents. iv Acknowledgements The endurance to overcome obstacles or predisposed objectives in life depends on how each one envisages them. It is up to each one to extract the most valuable lessons from each journey and transform them into knowledge. Without the guidance and support of very particular persons, it would have not been possible to accomplish this dissertation and many lessons would have not been learned. I hereby thank my mother and father, to whom I am mostly grateful, for helping me to achieve my goals, particularly those of my academic quest. I would like to thank my sister, Cátia, for her immeasurable support, and my grandparents, for always demonstrating their love and will to live. I am also grateful to my supervisor, Prof. Dr. Pedro Ricardo Morais Inácio, not only for the help, charisma and readiness he demonstrated to complete this stage, but also for being resourceful in aiding throughout other steps of my professional life. I also acknowledge the Multimedia Signal Processing – Covilhã Group at the Instituto de Telecomunicações, which hosted this dis- sertation work and the final project of my first degree, and the research folk in it, particularly Miguel Neto for lending me a smartcard reader temporarily. -

Using Oracle Application Container Cloud Service
Oracle® Cloud Using Oracle Application Container Cloud Service E64179-32 Sep 2019 Oracle Cloud Using Oracle Application Container Cloud Service, E64179-32 Copyright © 2015, 2019, Oracle and/or its affiliates. All rights reserved. Primary Authors: Rebecca Parks, Marilyn Beck, Rob Gray Contributing Authors: Michael W. Williams This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency- specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -

Oracle Cloud Infrastructure and Microsoft Azure – Benefits
Scenarios and Use Cases Bernhard Düchting Bernhard Düchting Phone +49.30.3909.7278 Email: [email protected] Disclosure statement This is a preliminary document and may be changed substantially Microsoft makes no warranties, express or implied, in this document. prior to final commercial release of the software described herein. Complying with all applicable copyright laws is the responsibility of The information contained in this document represents the current the user. Without limiting the rights under copyright, no part of this view of Microsoft Corporation on the issues discussed as of the date document may be reproduced, stored in, or introduced into a retrieval of publication. Because Microsoft must respond to changing market system, or transmitted in any form or by any means (electronic, conditions, it should not be interpreted to be a commitment on the mechanical, photocopying, recording, or otherwise), or for any part of Microsoft, and Microsoft cannot guarantee the accuracy of any purpose, without the express written permission of Microsoft information presented after the date of publication. This Corporation. Microsoft may have patents, patent applications, documentation is for informational purposes only. trademarks, copyrights, or other intellectual property rights covering THE INFORMATION CONTAINED IN THIS PRESENTATION IS subject matter in this document. Except as expressly provided in any MICROSOFT CONFIDENTIAL. written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, This presentation is for NDA Disclosure ONLY. Dates and capabilities copyrights, or other intellectual property. are subject to change. Supported geographies for upcoming previews or releases are subject to change. -

Oracle® Linux Virtualization Manager Getting Started Guide
Oracle® Linux Virtualization Manager Getting Started Guide F25124-11 September 2021 Oracle Legal Notices Copyright © 2019, 2021 Oracle and/or its affiliates. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, reproduction, duplication, release, display, disclosure, modification, preparation of derivative works, and/or adaptation of i) Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs), ii) Oracle computer documentation and/or iii) other Oracle data, is subject to the rights and limitations specified in the license contained in the applicable contract. -

Cloud Accelerates Linux Adoption IDC ANALYZE the FUTURE
IDC White Paper | Cloud Accelerates Linux Adoption IDC ANALYZE THE FUTURE Sponsored by: Cloud Accelerates Linux Adoption Oracle Corp. IDC OPINION Authors: Ashish Nadkarni Cloud has become a crucial foundation for digital transformation (DX) initiatives and Gary Chen is shaping the IT strategy of enterprises today. Companies are extending their IT February 2018 infrastructure into the cloud for running business-critical applications, developing new applications, and delivering new cloud-based services. Applications are the lifeblood of modern enterprises. They are the foundation on which businesses maintain their existing revenue streams while examining ways to create new ones. A sound application strategy is a must for frms to be successful in expanding their competitive differentiation in the digital economy. Operating systems (OSs) provide a common foundational layer that enables IT to run current and new generations of applications in traditional IT environments, on its own private cloud, and in public clouds and utilize a variety of computing options such as bare metal, virtualization, and containerization. The increased reliance of IT on the cloud has accelerated the adoption of open source operating systems, Linux being the chief among them. Over the past decade, Linux has evolved to be a versatile platform for current- and new-generation applications — a platform that can run in the cloud or on-premises and can include open source tools and frameworks used in modern application development. Enterprise platform functionality and -

Technical Design of Open Social Web for Crowdsourced Democracy
Project no. 610349 D-CENT Decentralised Citizens ENgagement Technologies Specific Targeted Research Project Collective Awareness Platforms D4.3 Technical Design of Open Social Web for Crowdsourced Democracy Version Number: 1 Lead beneficiary: OKF Due Date: 31 October 2014 Author(s): Pablo Aragón, Francesca Bria, Primavera de Filippi, Harry Halpin, Jaakko Korhonen, David Laniado, Smári McCarthy, Javier Toret Medina, Sander van der Waal Editors and reviewers: Robert Bjarnason, Joonas Pekkanen, Denis Roio, Guido Vilariño Dissemination level: PU Public X PP Restricted to other programme participants (including the Commission Services) RE Restricted to a group specified by the consortium (including the Commission Services) CO Confidential, only for members of the consortium (including the Commission Services) Approved by: Francesca Bria Date: 31 October 2014 This report is currently awaiting approval from the EC and cannot be not considered to be a final version. FP7 – CAPS - 2013 D-CENT D4.3 Technical Design of Open Social Web for Crowdsourced Democracy Contents 1 Executive Summary ........................................................................................................................................................ 6 Description of the D-CENT Open Democracy pilots ............................................................................................. 8 Description of the lean development process .......................................................................................................... 10 Hypotheses statements -

Getting the Most from Oracle Database in the Cloud with Oracle Exadata
White Paper Getting the Most from Oracle Database in the Cloud with Oracle Exadata Sponsored by: Oracle Carl W. Olofson Ashish Nadkarni November 2019 IN THIS WHITE PAPER It has been well established that the best possible environment for running Oracle Database is Oracle Exadata. This white paper focuses on the best solution for Oracle Database users who wish to enjoy the power and reliability of Exadata in conjunction with SaaS and other applications they are running on public cloud services. The paper considers the inherent compromises involved in running Oracle Database on non-Oracle, generic public cloud services, which do not support Oracle Exadata. Finally, the paper examines a solution that involves deploying Exadata in a colocation center that has a high- speed interconnect with the leading public cloud services, delivering Exadata power while overcoming the latency issue of connecting to applications in the public cloud. SITUATION OVERVIEW Oracle Database in the Public Cloud Increasingly, Oracle Database users are looking to move their applications to the public cloud or, in some cases, adopt SaaS applications while seeking to deploy Oracle Database in that public cloud, alongside the application. If the application is an Oracle application, the most straightforward way to do this is to move to the Oracle Cloud version of that application. For other applications, users are often choosing other cloud services, such as AWS, Microsoft Azure, or Google Cloud Platform (GCP). For databases that do not have significant performance or scalability requirements, deployment in public cloud environments may be just fine. Many Oracle customers, however, depend on the performance, scalability, and robustness that they have come to expect from the Oracle Exadata platform. -

Licensing; Oracle Software; Cloud Computing Environment
Licensing Oracle Software in the Cloud Computing Environment Approved Vendors This policy applies to cloud computing environments from the following vendors: Amazon Web Services – Amazon Elastic Compute Cloud (EC2), Amazon Relational Database Service (RDS) and Microsoft Azure Platform (collectively, the ‘Authorized Cloud Environments’). This policy applies to these Oracle programs. For the purposes of licensing Oracle programs in an Authorized Cloud Environment, customers are required to count as follows: Amazon EC2 and RDS - count two vCPUs as equivalent to one Oracle Processor license if hyper-threading is enabled, and one vCPU as equivalent to one Oracle Processor license if hyper-threading is not enabled. Microsoft Azure – count two vCPUs as equivalent to one Oracle Processor license if hyper- threading is enabled, and one vCPU as equivalent to one Oracle Processor license if hyper- threading is not enabled. When counting Oracle Processor license requirements in Authorized Cloud Environments, the Oracle Processor Core Factor Table is not applicable. When licensing Oracle programs with Standard Edition One, Standard Edition 2, or Standard Edition in the product name, the pricing is based on the size of the instance. Authorized Cloud Environment instances with four or fewer Amazon vCPUs, or four or fewer Azure vCPUs, are counted as 1 socket, which is considered equivalent to an Oracle processor license. For Authorized Cloud Environment instances with more than four Amazon vCPUs, or more than four Azure vCPUs, every four Amazon vCPUs used (rounded up to the nearest multiple of four), and every four Azure vCPUs used (rounded up to the nearest multiple of four) equate to a licensing requirement of one socket. -

Oracle Netsuite Service Descriptions
Oracle NetSuite Service Descriptions Effective Date: 18-August-2020 Oracle NetSuite V081820 Page 1 of 13 TABLE OF CONTENTS Metrics 3 Service Descriptions 4 Oracle NetSuite Planning and Budgeting Cloud Service - Instance 4 Oracle NetSuite Planning and Budgeting Cloud Service – Hosted Named User 4 Oracle Additional Storage for Oracle NetSuite Planning and Budgeting Cloud Service - 50 Gigabytes 5 Oracle Enterprise Planning and Budgeting Cloud Service - Hosted Named User 5 Oracle Warehouse Management Enterprise Cloud Service – Hosted Named User 6 Oracle Warehouse Workforce Management Cloud Service - Hosted Named User 7 Virtual Private Network for Warehouse Management Cloud Service – VPN Connection 7 Virtual Private Network Setup for Warehouse Management Cloud Service – VPN Connection 8 Oracle Enterprise Performance Management Standard Cloud Service - Hosted Named User 9 Oracle Additional Application for Oracle Enterprise Performance Management Standard Cloud Service - Hosted Environment 9 Oracle Integration Cloud Service for Oracle SaaS – Standard – 1 Million Messages 11 Oracle Integration Cloud Service for Oracle SaaS – Enterprise – 1 Million Messages 12 Oracle NetSuite v081820 Page 2 of 13 METRICS 50 Gigabytes: is defined as a 50 Gigabytes of additional computer storage space used by a storage filer equal to fifty billion bytes through the Cloud Service. For products such as Oracle Planning and Budgeting Cloud Service, that include two environments per Subscription ID, “50 Gigabytes” provides entitlement to an additional 50 Gigabytes of storage per environment (production and non- production). 1 Million Messages: is defined as the number of 1,000,000 message quantities per month used as part of the Oracle Cloud Service. A message is defined as up to 50Kb of in-and-out transmission from/to the Oracle Cloud Service. -
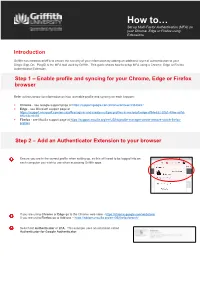
How to Install MFA Browser Authenicator Extension
How to… Set up Multi-Factor Authentication (MFA) on your Chrome, Edge or Firefox using Extensions Introduction Griffith has introduced MFA to ensure the security of your information by adding an additional layer of authentication to your Single Sign-On. PingID is the MFA tool used by Griffith. This guide shows how to setup MFA using a Chrome, Edge or Firefox Authenticator Extension. Step 1 – Enable profile and syncing for your Chrome, Edge or Firefox browser Refer to links below for information on how to enable profile and syncing for each browser: • Chrome - see Google support page at https://support.google.com/chrome/answer/2364824? • Edge - see Microsoft support page at https://support.microsoft.com/en-us/office/sign-in-and-create-multiple-profiles-in-microsoft-edge-df94e622-2061-49ae-ad1d- 6f0e43ce6435 • Firefox - see Mozilla support page at https://support.mozilla.org/en-US/kb/profile-manager-create-remove-switch-firefox- profiles Step 2 – Add an Authenticator Extension to your browser Ensure you are in the correct profile when setting up, as this will need to be logged into on each computer you wish to use when accessing Griffith apps. If you are using Chrome or Edge go to the Chrome web store - https://chrome.google.com/webstore/ If you are using Firefox go to Add-ons – https://addons.mozilla.org/en-GB/firefox/search/ Search for Authenticator or 2FA. This example uses an extension called Authenticator for Google Authenticator. Select Add Select Add Extension Your browser will confirm the extension has been added. Step 3 – Set up the Authenticator Extension as the primary authenticating method Once the Authenticator extension is added, click on the extension icon then click on the Pencil icon. -

Deploy the Oracle Cloud and Microsoft Azure Interconnect Using Hub-And-Spoke Topology
Deploy the Oracle Cloud and Microsoft Azure Interconnect Using Hub-and-Spoke Topology Access Oracle Cloud Infrastructure Resources from Microsoft Azure over a Private Interconnect September 2020 | Version 1.00 Copyright © 2020, Oracle and/or its affiliates Public PURPOSE STATEMENT This document provides an overview of the capabilities enabled by the cross-cloud direct interconnection between Oracle Cloud Infrastructure and Microsoft Azure Interconnect. It’s solely intended to help you assess the business benefits of migrating workloads to Oracle Cloud Infrastructure and plan your IT projects. DISCLAIMER This document in any form, software or printed matter, contains proprietary information that is the exclusive property of Oracle. Your access to and use of this confidential material is subject to the terms and conditions of your Oracle software license and service agreement, which has been executed and with which you agree to comply. This document and information contained herein may not be disclosed, copied, reproduced or distributed to anyone outside Oracle without prior written consent of Oracle. This document is not part of your license agreement nor can it be incorporated into any contractual agreement with Oracle or its subsidiaries or affiliates. This document is for informational purposes only and is intended solely to assist you in planning for the implementation and upgrade of the product features described. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described in this document remains at the sole discretion of Oracle. Due to the nature of the product architecture, it may not be possible to safely include all features described in this document without risking significant destabilization of the code. -

Power Your Cloud Infrastructure with Oracle VM and Cisco!
Power your cloud infrastructure with Oracle VM and Cisco! John Priest Director PM Oracle VM October 26/27, 2015 Copyright © 2015, Oracle and/or its affiliates. All rights reserved. | Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle. Copyright © 2015, Oracle and/or its affiliates. All rights reserved. | 2 Program Agenda 1 An overview of Oracle VM 2 Benefits of using Oracle VM in your Cloud 3 Flexible deployment options for Oracle VM in your Cloud 4 Q & A Copyright © 2015, Oracle and/or its affiliates. All rights reserved. | 3 The Cisco and Oracle Partnership 20+ year relationship Joint engineering engagement at many levels 38 leading performance benchmarks spanning Oracle Database Foundational customers to each other applications and middleware on Oracle Linux Joint Solutions : NetApp FlexPod, Nimble SmartSuite, EMC, Tegile, HDS Copyright © 2015, Oracle and/or its affiliates. All rights reserved. | 4 Solutions : Validated Configurations , Nimble SmartSuite Server Virtualization John Priest – Director PM – Oracle VM Copyright © 2015, Oracle and/or its affiliates. All rights reserved. | 5 The Foundation “You can't build a great building on a weak foundation. You must have a solid foundation if you're going to have a strong superstructure.” Gordon B. Hinckley Copyright © 2015, Oracle and/or its affiliates.