Personal Computers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
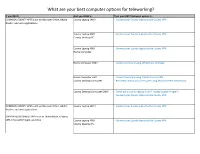
What Are Your Best Computer Options for Teleworking?
What are your best computer options for teleworking? If you NEED… And you HAVE a… Then your BEST telework option is… COMMON COUNTY APPS such as Microsoft Office, Adobe County Laptop ONLY - Connect your County laptop to the County VPN Reader, and web applications County Laptop AND - Connect your County laptop to the County VPN County Desktop PC County Laptop AND - Connect your County laptop to the County VPN Home Computer Home Computer ONLY - Connect remotely using VDI (Virtual Desktop) Home Computer AND - Connect remotely using Dakota County VPN County Desktop Computer - Remotely control your computer using Windows Remote Desktop County Desktop Computer ONLY - Check out a County laptop from IT Laptop Loaner Program - Connect your County laptop to the County VPN COMMON COUNTY APPS such as Microsoft Office, Adobe County Laptop ONLY - Connect your County laptop to the County VPN Reader, and web applications SUPPORTED BUSINESS APPS such as OneSolution, OnBase, SIRE, Microsoft Project, and Visio County Laptop AND - Connect your County laptop to the County VPN County Desktop PC If you NEED… And you HAVE a… Then your BEST telework option is… County Laptop AND - Connect your County laptop to the County VPN Home Computer Home Computer ONLY - Contact the County IT Help Desk at 651/438-4346 Home Computer AND - Connect remotely using Dakota County VPN County Desktop Computer - Remotely control your computer using Windows Remote Desktop County Desktop Computer ONLY - Check out a County laptop from IT Laptop Loaner Program - Connect your County laptop -

1 ICT Fundamentals Lesson 1: Computing Fundamentals
ICT Fundamentals - Lesson 1: Computing Fundamentals 1-1 1 ICT Fundamentals Lesson 1: Computing Fundamentals LESSON SKILLS After completing this lesson, you will be able to: Define "computer" and explain how computers work. Describe functions of the computing cycle (i.e. input, processing, output, storage). Describe uses of computers (i.e. home, school, business). Identify the main types of computers (i.e. supercomputer, mainframe, microcomputer, notebook, tablet, handheld). Describe the four parts of a computer (i.e. hardware, software, data, user). List computer input and output devices (i.e. monitor, printer, projector, speakers, mice, keyboards) and describe their uses. Define "network," and explain network usage (i.e. home, school, work). Identify types of networks (i.e. LAN, WAN, MAN, VPN, intranet, extranet, the internet). KEY TERMS computer intranet server computer network mainframe computers software data microcomputers storage extranet notebook computers supercomputers handheld computers output tablet computer hardware processing user input SAMPLE © 2021 Certification Partners, LLC. — All Rights Reserved. Version 1.0 ICT Fundamentals - Lesson 1: Computing Fundamentals 1-2 Overview In this lesson, you will explain computing functions, systems and devices. You will also explain networking types and uses at home, school and work. What Is a Computer? Objectives 1.1.1: Define "computer" and explain how computers work. 1.1.2: Describe functions of the computing cycle (i.e. input, processing, output, storage). According to Dictionary.com (2016) a computer is, "a programmable electronic device designed to accept data, perform prescribed mathematical and logical operations at high speed and display the results of these operations. Mainframes, desktop and laptop computers, tablets, and smartphones are some of the different types of computers." As we can see from this definition, there are many different kinds of computers that are used in today’s world. -

User Guide Ty Pe S 8143, 8144, 8146 Ty Pe S 8422, 8423, 8427
ThinkCentre™ User Guide Ty pe s 8143, 8144, 8146 Ty pe s 8422, 8423, 8427 ThinkCentre™ User Guide Ty pe s 8143, 8144, 8146 Ty pe s 8422, 8423, 8427 Note Before using this information and the product it supports, be sure to read the “Important safety information” on page v and Appendix D, “Notices,” on page 43. Second Edition (June 2004) © Copyright International Business Machines Corporation 2004. All rights reserved. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Important safety information . .v Erasing a lost or forgotten password (clearing Conditions that require immediate action. .v CMOS) . .24 General safety guidelines . .vi Replacing the cover and connecting the cables. .25 Service . .vi Power cords and power adapters . .vi Chapter 2. Using the IBM Setup Utility Extension cords and related devices . vii program . .27 Plugs and outlets . vii Starting the IBM Setup Utility program . .27 Batteries . vii Viewing and changing settings . .27 Heat and product ventilation . viii Using passwords . .27 CD and DVD drive safety . viii Password considerations . .27 Additional safety information . .ix User Password . .28 Lithium battery notice . .x Administrator Password . .28 Modem safety information. .x IDE Drive User Password . .28 Laser compliance statement . .xi IDE Drive Master Password . .28 Setting, changing, and deleting a password. .29 Overview . xiii Using Security Profile by Device . .29 Information resources. xiii Selecting a startup device. .29 Selecting a temporary startup device . .30 Chapter 1. Installing options . .1 Changing the startup sequence . .30 Features . .1 Exiting from the IBM Setup Utility program . .30 Available options . -

Scaling the Digital Divide: Home Computer Technology and Student Achievement
Scaling the Digital Divide Home Computer Technology and Student Achievement J a c o b V i g d o r a n d H e l e n l a d d w o r k i n g p a p e r 4 8 • j u n e 2 0 1 0 Scaling the Digital Divide: Home Computer Technology and Student Achievement Jacob L. Vigdor [email protected] Duke University Helen F. Ladd Duke University Contents Acknowledgements ii Abstract iii Introduction 1 Basic Evidence on Home Computer Use by North Carolina Public School Students 5 Access to home computers 5 Access to broadband internet service 7 How Home Computer Technology Might Influence Academic Achievement 10 An Adolescent's time allocation problem 10 Adapting the rational model to ten-year-olds 13 Estimation strategy 14 The Impact of Home Computer Technology on Test Scores 16 Comparing across- and within-student estimates 16 Extensions and robustness checks 22 Testing for effect heterogeneity 25 Examining the mechanism: broadband access and homework effort 29 Conclusions 34 References 36 Appendix Table 1 39 i Acknowledgements The authors are grateful to the William T. Grant Foundation and the National Center for Analysis of Longitudinal Data in Education Research (CALDER), supported through Grant R305A060018 to the Urban Institute from the Institute of Education Sciences, U.S. Department of Education for research support. They wish to thank Jon Guryan, Jesse Shapiro, Tim Smeeding, Andrew Leigh, and seminar participants at the University of Michigan, the University of Florida, Cornell University, the University of Missouri‐ Columbia, the University of Toronto, Georgetown University, Harvard University, the University of Chicago, Syracuse University, the Australian National University, the University of South Australia, and Deakin University for helpful comments on earlier drafts. -

The Video Game Industry an Industry Analysis, from a VC Perspective
The Video Game Industry An Industry Analysis, from a VC Perspective Nik Shah T’05 MBA Fellows Project March 11, 2005 Hanover, NH The Video Game Industry An Industry Analysis, from a VC Perspective Authors: Nik Shah • The video game industry is poised for significant growth, but [email protected] many sectors have already matured. Video games are a large and Tuck Class of 2005 growing market. However, within it, there are only selected portions that contain venture capital investment opportunities. Our analysis Charles Haigh [email protected] highlights these sectors, which are interesting for reasons including Tuck Class of 2005 significant technological change, high growth rates, new product development and lack of a clear market leader. • The opportunity lies in non-core products and services. We believe that the core hardware and game software markets are fairly mature and require intensive capital investment and strong technology knowledge for success. The best markets for investment are those that provide valuable new products and services to game developers, publishers and gamers themselves. These are the areas that will build out the industry as it undergoes significant growth. A Quick Snapshot of Our Identified Areas of Interest • Online Games and Platforms. Few online games have historically been venture funded and most are subject to the same “hit or miss” market adoption as console games, but as this segment grows, an opportunity for leading technology publishers and platforms will emerge. New developers will use these technologies to enable the faster and cheaper production of online games. The developers of new online games also present an opportunity as new methods of gameplay and game genres are explored. -
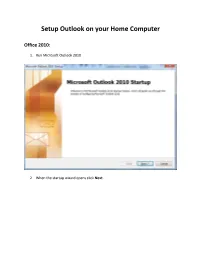
Setup Outlook on Your Home Computer
Setup Outlook on your Home Computer Office 2010: 1. Run Microsoft Outlook 2010 2. When the startup wizard opens click Next. 3. When prompted to configure an E-mail Account select Yes and then click Next. 4. The Auto Account Setup will display next, select E-mail Account and fill in the information. Your password is your network password, the same one you use to log into computers on campus. After you fill the information in click Next. 5. Outlook will begin to setup your account; it may take a few minutes before the next window pops up. 6. You will be prompted with some sort of login screen. The one shown here offers 3 choices (Select the middle one if this is the case), but others may only offer 1. Type in the same username you use to login to campus computers but precede it with sdsmt\ Your password will be the same one you use to login on campus. Click OK to continue. 7. Outlook will finish setting up your account; this may take a few minutes. When it is done press the Finish button. 8. Outlook will start up and will begin to download your emails, contacts, and calendar from the server. This may take several minutes; there will be a green loading bar at the bottom of the window. Office 2007: 1. Run Microsoft Outlook 2007 2. When the startup wizard opens click Next. 3. When prompted to configure an E-mail Account select Yes and then click Next. 4. The Auto Account Setup will display next, select E-mail Account and fill in the information. -

Programmierung Unter GNU/Linux Für Einsteiger
Programmierung unter GNU/Linux fur¨ Einsteiger Edgar 'Fast Edi' Hoffmann Community FreieSoftwareOG [email protected] 7. September 2016 Programmierung (von griechisch pr´ogramma Vorschrift\) bezeichnet die T¨atigkeit, " Computerprogramme zu erstellen. Dies umfasst vor Allem die Umsetzung (Implementierung) des Softwareentwurfs in Quellcode sowie { je nach Programmiersprache { das Ubersetzen¨ des Quellcodes in die Maschinensprache, meist unter Verwendung eines Compilers. Programmierung Begriffserkl¨arung 2 / 35 Dies umfasst vor Allem die Umsetzung (Implementierung) des Softwareentwurfs in Quellcode sowie { je nach Programmiersprache { das Ubersetzen¨ des Quellcodes in die Maschinensprache, meist unter Verwendung eines Compilers. Programmierung Begriffserkl¨arung Programmierung (von griechisch pr´ogramma Vorschrift\) bezeichnet die T¨atigkeit, " Computerprogramme zu erstellen. 2 / 35 Programmierung Begriffserkl¨arung Programmierung (von griechisch pr´ogramma Vorschrift\) bezeichnet die T¨atigkeit, " Computerprogramme zu erstellen. Dies umfasst vor Allem die Umsetzung (Implementierung) des Softwareentwurfs in Quellcode sowie { je nach Programmiersprache { das Ubersetzen¨ des Quellcodes in die Maschinensprache, meist unter Verwendung eines Compilers. 2 / 35 Programme werden unter Verwendung von Programmiersprachen formuliert ( kodiert\). " In eine solche Sprache ubersetzt\¨ der Programmierer die (z. B. im Pflichtenheft) " vorgegebenen Anforderungen und Algorithmen. Zunehmend wird er dabei durch Codegeneratoren unterstutzt,¨ die zumindest -

P Palmtop Aper
u.s. $7.95 Publisher's Message ................................ , Letters to the Editor .................................. ~ - E New Third Party Ln Products and Services ............................ .E ..... =Q) HP Palmtop Users Groups ...................... J E :::J User to User ............................................ 1( :z Hal reports on the excitement at the HP Handheld - P Palmtop User's Conference, a new book by David Packard "<t" describing the history of HP, our new 200LXI1000CX Q) loaner p'rogram for developers, the 1995/1996 E Subscnbers PowerDisk and some good software :::J that didn't make it into thePowerDisk, but is on this o issue's ON DISK and CompuServe. > aper PalmtoD Wisdom .................................... 2< Know ~here you stand with your finances; Keep impqrtant information with you, and keep it secure; The best quotes may not tie in the quotes books. Built·in Apps on Vacation: To Africa and Back with the HP Palmtop ....................................... 1E acafTen/ The HP 200LX lielps a couple from Maryland prepare for their dream vacation to Africa. Built·in Apps on Vacation: Editor on Vacation .................................. 2( Even on vacation, Rich Hall, managing editor for The HP Palmtop Paper, finds the Palmtop to be an indispensable companion. AP~ointment Book: ~n ~~l~epP~~'~~~~~~.~~.~~...................... 2~ Appointment Book provides basic prol'ect management already built into the HP Pa mtop. DataBase: Print Your Database in the Format You Want .......................... 3( Create a custom database and print Hout in the for mat you want using the built-in DataBase program and Smart Clip. Lotus 1·2·3 Column: Basic Training for 1-2-3 Users ............... 3~ Attention first-time Lotus users, or those needing a bH of a refresher - get out your HP Palmtop and fonow along with this review of the basics. -

And PC 750 (Type 6887)
Technical Information Manual PC 730 (Type 6877) and PC 750 (Type 6887) Technical Information Manual IBM PC 730 (Type 6877) and PC 750 (Type 6887) Note Before using this information and the product it supports, be sure to read the general information under Appendix B, “Notices and Trademarks” on page 65. First Edition (June 1996) The following paragraph does not apply to the United Kingdom or any country where such provisions are inconsistent with local law: INTERNATIONAL BUSINESS MACHINES CORPORATION PROVIDES THIS PUBLICATION “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer of express or implied warranties in certain transactions, therefore, this statement may not apply to you. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. IBM may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time. It is possible that this publication may contain reference to, or information about, IBM products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such IBM products, programming, or services in your country. Requests for technical information about IBM products should be made to your IBM reseller or IBM marketing representative. IBM may have patents or pending patent applications covering subject matter in this document. -

The MSX Red Book (Revised Version 1997/08/06) Notes from The
The MSX Red Book (revised version 1997/08/06) Notes from the editor: - The book was scanned and converted (via O.C.R.) by one person and edited by another (using an IBM PC compatible), independently. - All pages have a fix size of 64 lines. The width was not justified to make future modifications easier, though no line is longer than 80 columns. - This book only covers standard MSX. The BIOS entry points from 0000H to 01B5H should be used instead of the called entries described in the book, because other machines (MSX2, MSX2+, MSX turbo R and customized ones) have different positions for the routines. The use of internal BIOS routine addresses are responsible for many programs only running in MSX. - Some errors present in the original book were fixed, though it was tried to keep it as unaltered as possible. All page numbers match the originals, except undetected errors already present in the original. - Most figures were modificated due to the text-only nature of this file. The character set used during edition was the International IBM PC's one. The following special characters were used and should be changed to the corresponding ones of other character sets: Frame ÚÄÂÄ¿ Pound: œ characters: ³ ³ ³ Micro: æ ÃÄÅÄ´ ³ ³ ³ ÀÄÁÄÙ ------------------------------------------------------------------------------- CONTENTS Introduction .............................. 1 1. Programmable Peripheral Interface ...... 3 2. Video Display Processor ................ 8 3. Programmable Sound Generator ........... 21 4. ROM BIOS ............................... 26 5. ROM BASIC Interpreter .................. 89 6. Memory Map ............................. 208 7. Machine Code Programs .................. 240 Contents Copyright 1985 Avalon Software Iver Lane, Cowley, Middx, UB8 2JD MSX is a trademark of Microsoft Corp. -

Classification of Computers
Chapter-2 Classification of Computers Computers can be classified many different ways -- by size, by function, or by processing capacity. Functionality wise 4 types a) Micro computer b) Mini Computer c) Mainframe Computer d) Super Computer Microcomputers Microcomputers are connected to networks of other computers. The price of a microcomputer varies from each other depending on the capacity and features of the computer. Microcomputers make up the vast majority of computers. Single user can interact with this computer at a time. It is a small and general purpose computer. Mini Computer Mini Computer is a small and general purpose computer. It is more expensive than a micro computer. It has more storage capacity and speed. It designed to simultaneously handle the needs of multiple users. Mainframe Computer Large computers are called Mainframes. Mainframe computers process data at very high rates of speed, measured in the millions of instructions per second. They are very expensive than micro computer and mini computer. Mainframes are designed for multiple users and process vast amounts of data quickly. Examples: - Banks, insurance companies, manufacturers, mail-order companies, and airlines are typical users. Super Computers The largest computers are Super Computers. They are the most powerful, the most expensive, and the fastest. They are capable of processing trillions of instructions per second. It uses governmental agencies, such as:- Chemical analysis in laboratory Space exploration National Defense Agency National Weather Service Bio-Medical research Design of many other machines Limitations of Computer Computer cannot take over all activities simply because they are less flexible than humans. It does not hold intelligence of its own. -

Inside the Computer Microcomputer Minicomputer Mainframe
Inside the computer Microcomputer Classification of Systems: • Personal Computer / Workstation. – Microcomputer • Desktop machine, including portables. – Minicomputer • Used for small, individual tasks - such as – Mainframe simple desktop publishing, small business – Supercomputer accounting, etc.... • Typical cost : £500 to £5000. • Chapters 1-5 in Capron • Example : The PCs in the labs are microcomputers. Minicomputer Mainframe • Medium sized server • Large server / Large Business applications • Desk to fridge sized machine. • Large machines in purpose built rooms. • Used for distributed data processing and • Used as large servers and for intensive multi-user server support. business applications. • Typical cost : £5,000 to £500,000. • Typical cost : £500,000 to £10,000,000. • Example : Scarlet is a minicomputer. • Example : IBM ES/9000, IBM 370, IBM 390. Supercomputer • Scientific applications • Large machines. • Typically employ parallel architecture (multiple processors running together). • Used for VERY numerically intensive jobs. • Typical cost : £5,000,000 to £25,000,000. • Example : Cray supercomputer 1 What's in a Computer System? Software • The Onion Model - layers. • Divided into two main areas • Hardware • Operating system • BIOS • Used to control the hardware and to provide an interface between the user and the hardware. • Software • Manages resources in the machine, like • Where does the operating system come in? • Memory • Disk drives • Applications • includes games, word-processors, databases, etc.... Interfaces Hardware • The chunky stuff! •CUI • If you can touch it... it's probably hardware! • Command Line Interface • The mother board. •GUI • If we have motherboards... surely there must be • Graphical User Interface fatherboards? right? •WIMP • What about sonboards, or daughterboards?! • Windows, Icons, Mouse, Pulldown menus • Hard disk drives • Monitors • Keyboards BIOS Basics • Basic Input Output System • Directly controls hardware devices like UARTS (Universal Asynchronous Receiver-Transmitter) - Used in COM ports.