Press Release, August 12, 1981
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

User Guide Ty Pe S 8143, 8144, 8146 Ty Pe S 8422, 8423, 8427
ThinkCentre™ User Guide Ty pe s 8143, 8144, 8146 Ty pe s 8422, 8423, 8427 ThinkCentre™ User Guide Ty pe s 8143, 8144, 8146 Ty pe s 8422, 8423, 8427 Note Before using this information and the product it supports, be sure to read the “Important safety information” on page v and Appendix D, “Notices,” on page 43. Second Edition (June 2004) © Copyright International Business Machines Corporation 2004. All rights reserved. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Important safety information . .v Erasing a lost or forgotten password (clearing Conditions that require immediate action. .v CMOS) . .24 General safety guidelines . .vi Replacing the cover and connecting the cables. .25 Service . .vi Power cords and power adapters . .vi Chapter 2. Using the IBM Setup Utility Extension cords and related devices . vii program . .27 Plugs and outlets . vii Starting the IBM Setup Utility program . .27 Batteries . vii Viewing and changing settings . .27 Heat and product ventilation . viii Using passwords . .27 CD and DVD drive safety . viii Password considerations . .27 Additional safety information . .ix User Password . .28 Lithium battery notice . .x Administrator Password . .28 Modem safety information. .x IDE Drive User Password . .28 Laser compliance statement . .xi IDE Drive Master Password . .28 Setting, changing, and deleting a password. .29 Overview . xiii Using Security Profile by Device . .29 Information resources. xiii Selecting a startup device. .29 Selecting a temporary startup device . .30 Chapter 1. Installing options . .1 Changing the startup sequence . .30 Features . .1 Exiting from the IBM Setup Utility program . .30 Available options . -

Introduction to MS-DOS
1.Introduction to MS-DOS : MS-DOS (Microsoft Disk Operating System) was the Microsoft-marketed version of the first widely-installed operating system in personal computers. It was essentially the same operating system that (Bill Gates's) young company developed for IBM as Personal Computer - Disk Operating System in 1981. Most users of either DOS system simply referred to their system as Disk Operating System. Like PC-DOS, MS-DOS was (and still is) a non-graphical line-oriented command- driven operating system, with a relatively simple interface but not overly "friendly" user interface. Its prompt to enter a command looks like this: C:\> MS-DOS does not care about anything called an icon, wallpaper or screen saver. Rather than being considered as a Graphical User Interface (GUI) MS-DOS is what is known as a command-line interface. You type commands on what is called the command line. MS-DOS is a single-user, single-tasking computer operating system. In spite of its very small size and relative simplicity, it is one of the most successful operating systems that has been developed to date. In DOS, a file name consists of eight character followed by a 3 character file extension. The size of a file is restricted to a 4 byte file descriptor, which limits a file’s maximum size to approximately 4 billion characters. The first release of DOS could not read or write to disk drives so users could only read and write to a floppy disc. DOS was not a state of the art operating system, even for its time. -

Chapter 1. Origins of Mac OS X
1 Chapter 1. Origins of Mac OS X "Most ideas come from previous ideas." Alan Curtis Kay The Mac OS X operating system represents a rather successful coming together of paradigms, ideologies, and technologies that have often resisted each other in the past. A good example is the cordial relationship that exists between the command-line and graphical interfaces in Mac OS X. The system is a result of the trials and tribulations of Apple and NeXT, as well as their user and developer communities. Mac OS X exemplifies how a capable system can result from the direct or indirect efforts of corporations, academic and research communities, the Open Source and Free Software movements, and, of course, individuals. Apple has been around since 1976, and many accounts of its history have been told. If the story of Apple as a company is fascinating, so is the technical history of Apple's operating systems. In this chapter,[1] we will trace the history of Mac OS X, discussing several technologies whose confluence eventually led to the modern-day Apple operating system. [1] This book's accompanying web site (www.osxbook.com) provides a more detailed technical history of all of Apple's operating systems. 1 2 2 1 1.1. Apple's Quest for the[2] Operating System [2] Whereas the word "the" is used here to designate prominence and desirability, it is an interesting coincidence that "THE" was the name of a multiprogramming system described by Edsger W. Dijkstra in a 1968 paper. It was March 1988. The Macintosh had been around for four years. -

And PC 750 (Type 6887)
Technical Information Manual PC 730 (Type 6877) and PC 750 (Type 6887) Technical Information Manual IBM PC 730 (Type 6877) and PC 750 (Type 6887) Note Before using this information and the product it supports, be sure to read the general information under Appendix B, “Notices and Trademarks” on page 65. First Edition (June 1996) The following paragraph does not apply to the United Kingdom or any country where such provisions are inconsistent with local law: INTERNATIONAL BUSINESS MACHINES CORPORATION PROVIDES THIS PUBLICATION “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer of express or implied warranties in certain transactions, therefore, this statement may not apply to you. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. IBM may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time. It is possible that this publication may contain reference to, or information about, IBM products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such IBM products, programming, or services in your country. Requests for technical information about IBM products should be made to your IBM reseller or IBM marketing representative. IBM may have patents or pending patent applications covering subject matter in this document. -

The Origins of Word Processing and Office Automation
Remembering the Office of the Future: The Origins of Word Processing and Office Automation Thomas Haigh University of Wisconsin Word processing entered the American office in 1970 as an idea about reorganizing typists, but its meaning soon shifted to describe computerized text editing. The designers of word processing systems combined existing technologies to exploit the falling costs of interactive computing, creating a new business quite separate from the emerging world of the personal computer. Most people first experienced word processing using a word processor, we think of a software as an application of the personal computer. package, such as Microsoft Word. However, in During the 1980s, word processing rivaled and the early 1970s, when the idea of word process- eventually overtook spreadsheet creation as the ing first gained prominence, it referred to a new most widespread business application for per- way of organizing work: an ideal of centralizing sonal computers.1 By the end of that decade, the typing and transcription in the hands of spe- typewriter had been banished to the corner of cialists equipped with technologies such as auto- most offices, used only to fill out forms and matic typewriters. The word processing concept address envelopes. By the early 1990s, high-qual- was promoted by IBM to present its typewriter ity printers and powerful personal computers and dictating machine division as a comple- were a fixture in middle-class American house- ment to its “data processing” business. Within holds. Email, which emerged as another key the word processing center, automatic typewriters application for personal computers with the and dictating machines were rechristened word spread of the Internet in the mid-1990s, essen- processing machines, to be operated by word tially extended word processing technology to processing operators rather than secretaries or electronic message transmission. -

Microcomputers: NQS PUBLICATIONS Introduction to Features and Uses
of Commerce Computer Science National Bureau and Technology of Standards NBS Special Publication 500-110 Microcomputers: NQS PUBLICATIONS Introduction to Features and Uses QO IGf) .U57 500-110 NATIONAL BUREAU OF STANDARDS The National Bureau of Standards' was established by an act ot Congress on March 3, 1901. The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides; (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to promote public safety. The Bureau's technical work is per- formed by the National Measurement Laboratory, the National Engineering Laboratory, and the Institute for Computer Sciences and Technology. THE NATIONAL MEASUREMENT LABORATORY provides the national system of physical and chemical and materials measurement; coordinates the system with measurement systems of other nations and furnishes essential services leading to accurate and uniform physical and chemical measurement throughout the Nation's scientific community, industry, and commerce; conducts materials research leading to improved methods of measurement, standards, and data on the properties of materials needed by industry, commerce, educational institutions, and Government; provides advisory and research services to other Government agencies; develops, produces, and -

Energy Consumption of Personal Computer Workstations
Energy Consumption of Personal Computer Workstations Richard F. Szydlowski and William D. Chvála, Jr.r Pacific Northwest Laboratory A field study directly measured the electric demand of 189 personal computer workstations for 1-week intervals, and a survey recorded the connected equipment at 1,846 workstations in six buildings. Each separate workstation component (e.g., computer, monitor, printer, modem, and other peripheral) was individually monitored to obtain detailed electric demand profiles. Other analyses included comparison of nameplate power rating with measured power consumption and the energy savings potential and cost-effectiveness of a controller that automatically turns off computer workstation equipment during inactivity. An important outcome of the work is the development of a standard workstation demand profile and a technique for estimating a whole-building demand profile. Together, these provide a method for transferring this information to utility energy analysts, design engineers, building energy modelers, and others. A life-cycle cost analysis was used to determine the cost-effectiveness of three energy conservation measures: 1) energy awareness education, 2) retrofit power controller installation, and 3) purchase of energy-efficient PCs. Introduction The explosive growth of the information age has had a a positive step toward creating a market for more energy- profound effect on the appearance of today’s office. efficient computer equipment by encouraging buyers to Although the telephone still remains an important part of purchase equipment that meets energy conservation stan- the information exchange and processing system within an dards set by the EPA. The standards dictate that Energy office, other electronic devices are now considered re- Star computers and video display monitors have a power- quired equipment within this environment. -

Microsoft Plays Hardball: Use of Exclusionary Pricing and Technical
Antitrust Bulletin, XL:2, Summer 1995, 265-315 MICROSOFT PLAYS HARDBALL: The Use of Exclusionary Pricing and Technical Incompatibility to Maintain Monopoly Power in Markets for Operating System Software† by KENNETH C. BASEMAN* FREDERICK R. WARREN-BOULTON* and GLENN A. WOROCH** May 1995 ___________________ * Principals, MiCRA: Microeconomic Consulting and Research Associates, Inc., Washington, DC. ** University of California, Berkeley. † Forthcoming, Antitrust Bulletin, June 1995. We would like to express our appreciation for helpful comments and other assistance to Sturge Sobin, Linnet Harlan, Paul Dennis and the participants at the Columbia Business School's Institute for Tele-Information's Seminar on Sustaining Competition in Network Industries through Regulating and Pricing Access, especially Janusz Ordover and Bobby Willig. TABLE OF CONTENTS I. INTRODUCTION AND SUMMARY ................................... 1 II. BACKGROUND .................................................... 3 A. THE MARKET FOR PERSONAL COMPUTER OPERATING SYSTEMS ............................................................ 3 TABLE: NEW SHIPMENTS OF PERSONAL COMPUTER OPERATING SYSTEMS .............................................. 8 B. MICROSOFT'S PRACTICES ..................................... 9 III. FIRST-DEGREE PRICE DISCRIMINATION vs. INEFFICIENT SUBSTITUTION ................................................... 15 A. FIRST-DEGREE PRICE DISCRIMINATION ........................ 16 B. INEFFICIENT SUBSTITUTION ................................. 20 IV. ANTIFRAUD AND ANTIPIRACY -

Getting to Know Computers
Computer Basics Getting to Know Computers Page 1 What is a Computer? A computer is an electronic device that manipulates information, or "data." It has the ability to store, retrieve, and process data. You can use a computer to type documents, send email, and browse the internet. You can also use it to handle spreadsheets, accounting, database management, presentations, games, and more. Watch the video to learn about different types of computers. Watch the video (2:39). Need help? Computers Simplified For beginning computer users, the computer aisles at an electronics store can be quite a mystery, not to mention overwhelming. However, computers really aren't that mysterious. All types of computers consist of two basic parts: Hardware is any part of your computer that has a physical structure, such as the computer monitor or keyboard. Software is any set of instructions that tells the hardware what to do. It is what guides the hardware and tells it how to accomplish each task. Some examples of software are web browsers, games, and word processors such as Microsoft Word. A motherboard (hardware) Microsoft Word (software) Anything you buy for your computer can be classified as either hardware or software. Once you learn more about these items, computers are actually very straightforward. The first electronic computer, the Electronic Numerical Integrator and Computer (ENIAC), was developed in ©1998-2013 Goodwill Community Foundation, Inc. All rights reserved. 1946. It took up 1,800 square feet and weighed 30 tons. Page 2 What are the Different Types of Computers? When most people hear the word "computer," they think of a personal computer such as a desktop or laptop computer. -

Ibl\1 PERSONAL SYSTEM/2(TM) and PERSONAL COMPUTER PVBLICATIO~ and EDUCATION REFERENCES
IBl\1 PERSONAL SYSTEM/2(TM) and PERSONAL COMPUTER PVBLICATIO~ and EDUCATION REFERENCES As of 01-13-89 The following list of PC publications is for marketing and market support purposes. This list was taken from the product Ivory Letters and all other known sources. The bulk of the publication numbers pertain to PC hardware products, as these are the ones in most demand. Some entries are listed in multiple categories because they pertain to each category within which they are shown. The publications shown in this list are only some of the PC publications available; most PC pub lications have been assigned 7 -digit part numbers instead of 8-digit form numbers. The follo\ving list is composed of only form numbers, so that you may readily order these publications from Mechanicsburg. Technical publications may be obtained from either an IBM Representative, an Authorized IBI'v1 Dealer, the Technical Directory (1-800-IBM-PCTB), or the IBM Software/Publications Response Line (1-800-327-5711); the latter is normally used by dealers. A change to the information since November 16, 1988 is indicated by a vertical line to the left of the change. Rich Berman Tieline 396-4887 RHBERMAN at DEM014 \Vestern Area Technical Support Ctr., Dept. CUU ii Table of Contents General/:\-liscellaneous ......................................................... 1 Managing \Vorkstations ....................................................... 11 Personal System/2 ............................................................ 12 PC AT ................................................................... -
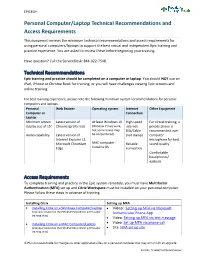
Personal Computer/Laptop Technical Requirements
EPIC4SJH Personal Computer/Laptop Technical Recommendations and Access Requirements This document reviews the minimum technical recommendations and access requirements for using personal computers/laptops to support the best virtual and independent Epic training and practice experience. You are asked to review these before beginning your training. Have question? Call the ServiceDesk: 844-922-7548. Technical Recommendations Epic training and practice should be completed on a computer or laptop. You should NOT use an iPad, iPhone or Chrome Book for training, or you will have challenges viewing Epic screens and online training. For best learning experience, please note the following minimum system recommendations for personal computers and laptops. Personal Web Brower Operating system Internet Other Equipment Computer or Connection Laptop Minimum screen Latest version of At least Windows 10 High speed For virtual training, a display size of 15” Chrome (preferred) (Window 7 may work, internet private phone is but some issues may DSL/Cable recommended over Audio capability Latest version of be encountered) (not dialup) computer Internet Explorer 11, microphone for best Microsoft Chromium MAC computer - Reliable sound quality Edge Catalina OS connection Comfortable headphones/ earbuds Access Requirements To complete training and practice in the Epic system remotely, you must have Multifactor Authentication (MFA) set up and Citrix Workspace must be installed on your personal computer. Please follow these steps in advance of training. Installing -

Inside OS/2 Warp Server for E-Business(PDF)
Inside OS/2 Warp Server for e-business Girish Basavalingaiah, Ron Bloor, Tonko De Rooy, Edgar Omar Gonzalez Espinosa, Roger Govind, Peter Marfatia, Oliver Mark, Frank Mueller, Indran Naick, Leon Van Der Linde, Frank Vanhulle International Technical Support Organization http://www.redbooks.ibm.com SG24-5393-00 SG24-5393-00 International Technical Support Organization Inside OS/2 Warp Server for e-business July 1999 Take Note! Before using this information and the product it supports, be sure to read the general information in Appendix C, “Special notices” on page 429. First Edition (July 1999) This edition applies to OS/2 Warp Server for e-business for use on Intel server hardware. Note This book is based on a pre-GA version of a product and may not apply when the product becomes generally available. We recommend that you consult the product documentation or follow-on versions of this redbook for more current information. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. DHHB, Building 003 Internal Zip 2834 11400 Burnet Road Austin, Texas 78758-3493 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright International Business Machines Corporation 1999. All rights reserved. Note to U.S Government Users – Documentation related to restricted rights – Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Contents Figures....................................................xi Tables................................................... xvii Preface...................................................xix The team that wrote this redbook.