Z/OS Basic Skills Information Center: Mainframe Concepts
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Travelers IBM 1401 Exhibit Thematic Presentation, June 1984
THE TRAVELERS IBM 1401 EXHIBIT At The Computer Museum, Bay 3, Floor 5 THEMATIC PRESENTATION Overall The Travelers IBM 1401 Exhibit will illustrate general aspects of business computing in the mid-sixties. Four primary themes will be presented: the use of computers as information processors by businesses, the characteristics of this kind of computer operation, the rise in higher-level languages, and the replacement of punched cards by magnetic memory as the predominant secondary storage medium. The Travelers 1401 will exemplify these themes. In instances where reality does not quite serve the presentation artistic license will be exercized. Computers as Business Tools The use of the 1401 by The Travelers for policy processing and management report compilation will illustrate the general character of problems to which businesses a~plied computers. Charateristics of Computer Operation Batch-processing characterized the operation of computers in the mid-sixties. This reinforced the division between the machine and the programmers. Since only operators were allowed to run programs on the computer, the process of de-bugging a program was long and arduous. This method of operation will be contrasted with the contemporary operation of computers. The 1401 exhibit, by the relative position of the Programmer's Office and the Computer Room, and the contents thereof, will advance this theme. High-Level Languages The predominance of COBOL as the programming language for business illustrates the general move towards using higher-level languages which occured throughout the 1960's. The Travelers 1401 will be presented as being programmed in COBOL. The Fall of the Punched Card and the Ris~ of Magnetic Memory Inflexibility, serial storage, and size will be presented as three of the major problems of punched cards for data storage. -

1 ICT Fundamentals Lesson 1: Computing Fundamentals
ICT Fundamentals - Lesson 1: Computing Fundamentals 1-1 1 ICT Fundamentals Lesson 1: Computing Fundamentals LESSON SKILLS After completing this lesson, you will be able to: Define "computer" and explain how computers work. Describe functions of the computing cycle (i.e. input, processing, output, storage). Describe uses of computers (i.e. home, school, business). Identify the main types of computers (i.e. supercomputer, mainframe, microcomputer, notebook, tablet, handheld). Describe the four parts of a computer (i.e. hardware, software, data, user). List computer input and output devices (i.e. monitor, printer, projector, speakers, mice, keyboards) and describe their uses. Define "network," and explain network usage (i.e. home, school, work). Identify types of networks (i.e. LAN, WAN, MAN, VPN, intranet, extranet, the internet). KEY TERMS computer intranet server computer network mainframe computers software data microcomputers storage extranet notebook computers supercomputers handheld computers output tablet computer hardware processing user input SAMPLE © 2021 Certification Partners, LLC. — All Rights Reserved. Version 1.0 ICT Fundamentals - Lesson 1: Computing Fundamentals 1-2 Overview In this lesson, you will explain computing functions, systems and devices. You will also explain networking types and uses at home, school and work. What Is a Computer? Objectives 1.1.1: Define "computer" and explain how computers work. 1.1.2: Describe functions of the computing cycle (i.e. input, processing, output, storage). According to Dictionary.com (2016) a computer is, "a programmable electronic device designed to accept data, perform prescribed mathematical and logical operations at high speed and display the results of these operations. Mainframes, desktop and laptop computers, tablets, and smartphones are some of the different types of computers." As we can see from this definition, there are many different kinds of computers that are used in today’s world. -

Introduction to Mainframe Networking TCP/IP Problem Determination
z/OS Basic Skills Information Center Networking on z/OS z/OS Basic Skills Information Center Networking on z/OS Note Before using this information and the product it supports, read the information in “Notices” on page 251. This edition applies to z/OS (product number 5694-A01). We appreciate your comments about this publication. Comment on specific errors or omissions, accuracy, organization, subject matter, or completeness of this book. The comments you send should pertain to only the information in this manual or product and the way in which the information is presented. For technical questions and information about products and prices, please contact your IBM branch office, your IBM business partner, or your authorized remarketer. When you send comments to IBM, you grant IBM a nonexclusive right to use or distribute your comments in any way it believes appropriate without incurring any obligation to you. IBM or any other organizations will only use the personal information that you supply to contact you about the issues that you state on this form. Send your comments through this web site: http://publib.boulder.ibm.com/infocenter/zoslnctr/v1r7/index.jsp?topic=/com.ibm.zcontact.doc/webqs.html © Copyright IBM Corporation 2006, 2010. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Before you begin the topic about Coupling channels ...........40 networking on z/OS .........vii Open Systems Adapter (OSA) .......40 HiperSockets ..............46 The I/O cage ..............48 Part 1. Introduction to networking on the mainframe...........1 Chapter 4. Sample network configuration ............49 Chapter 1. -
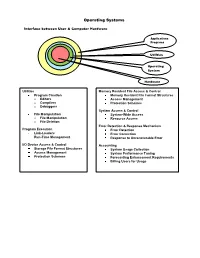
Operating Systems
Operating Systems Interface between User & Computer Hardware Applications Programs Utilities Operating System Hardware Utilities Memory Resident File Access & Control Program Creation Memory Resident File Format Structures o Editors Access Management o Compilers Protection Schemes o Debuggers System Access & Control File Manipulation System-Wide Access o File Manipulation Resource Access o File Deletion Error Detection & Response Mechanism Program Execution Error Detection Link-Loaders Error Correction Run-Time Management Response to Unrecoverable Error I/O Device Access & Control Accounting Storage File Format Structures System Usage Collection Access Management System Performance Tuning Protection Schemes Forecasting Enhancement Requirements Billing Users for Usage Resource Manager O/S KernelKernel I/O Controller Printers, Keyboards, I/O Controller Monitors, Portions of Cameras, the O/S Etc. currently in use Computer Main System Memory Portions of Various I/O Application Devices Programs Currently in use Operating System Data Application Programs I/O Controller Storage Processor Processor Data Processor Processor Operation Allocation of Main Memory is made jointly by both the O/S and Memory Management Hardware O/S controls access to I/O devices by Application Programs O/S controls access to and use of files O/S controls access to and use of the processors, i.e., how much time can be allocated to the execution of a particular Application Program Classification of Operating Systems Interactive O/S Keyboard & Monitor Access to O/S Immediate, -

IBM 1401 Simulator Usage 31-Mar-2015
IBM 1401 Simulator Usage 31-Mar-2015 COPYRIGHT NOTICE The following copyright notice applies to the SIMH source, binary, and documentation: Original code published in 1993-2015, written by Robert M Supnik Copyright (c) 1993-2015, Robert M Supnik Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL ROBERT M SUPNIK BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. Except as contained in this notice, the name of Robert M Supnik shall not be used in advertising or otherwise to promote the sale, use or other dealings in this Software without prior written authorization from Robert M Supnik. 1 Simulator Files ............................................................................................................. 3 2 IBM 1401 Features ...................................................................................................... 3 2.1 CPU ...................................................................................................................... 4 2.2 1402 Card Reader/Punch (CDR, CDP, STKR) .................................................... -

Acrobat Distiller, Job 2
A BRIEF HISTORY OF THE IBM ES/9000, SYSTEM/390 AND zSERIES 1990 IBM makes its most comprehensive product announcement in 25 years by introducing the System/390 family consisting of 18 Enterprise System/9000 processors ranging from midrange computers for office environments to the most powerful computers IBM has ever offered. Featuring enhanced function and capability to manage information systems, the System/390 provides increased processing power, better network management, improved communication among multivendor systems and the Enterprise System/9000 processors. In many cases, customers currently using IBM Enterprise System/3090 systems can easily upgrade their systems to System/390 processors. Other 1990 announcements include: several networking products to make it easier for customers to use their midrange, desktop and System/390 computers to communicate with non-IBM computers. 1991 IBM unveils seven new Enterprise System/9000 processors and operating system software — Advanced Interactive Executive/Enterprise System Architecture (AIX/ESA) — for the System/390 family. AIX/ESA is a further step in IBM’s implementation of open-systems computing across its product line and is based on UNIX and the Open Software Foundation’s OSF/1 standards. The company begins shipping in volume and on schedule two top-of-the-line ES/9000 models that were announced in September 1990. IBM Japan says it will supply Enterprise System/9000 processors and operating system software to Mitsubishi Electric Corp. for remarketing. The agreement marks the first time IBM has sold large processors as an original equipment manufacturer for resale. 1992 IBM introduces two entry-level Enterprise System/9000 processors and ships five new Enterprise System/9000 water-cooled processors — Models 520, 640, 660, 740 and 860 — one-to-four months ahead of schedule. -

Introduction to MS-DOS
1.Introduction to MS-DOS : MS-DOS (Microsoft Disk Operating System) was the Microsoft-marketed version of the first widely-installed operating system in personal computers. It was essentially the same operating system that (Bill Gates's) young company developed for IBM as Personal Computer - Disk Operating System in 1981. Most users of either DOS system simply referred to their system as Disk Operating System. Like PC-DOS, MS-DOS was (and still is) a non-graphical line-oriented command- driven operating system, with a relatively simple interface but not overly "friendly" user interface. Its prompt to enter a command looks like this: C:\> MS-DOS does not care about anything called an icon, wallpaper or screen saver. Rather than being considered as a Graphical User Interface (GUI) MS-DOS is what is known as a command-line interface. You type commands on what is called the command line. MS-DOS is a single-user, single-tasking computer operating system. In spite of its very small size and relative simplicity, it is one of the most successful operating systems that has been developed to date. In DOS, a file name consists of eight character followed by a 3 character file extension. The size of a file is restricted to a 4 byte file descriptor, which limits a file’s maximum size to approximately 4 billion characters. The first release of DOS could not read or write to disk drives so users could only read and write to a floppy disc. DOS was not a state of the art operating system, even for its time. -

Chapter 1. Origins of Mac OS X
1 Chapter 1. Origins of Mac OS X "Most ideas come from previous ideas." Alan Curtis Kay The Mac OS X operating system represents a rather successful coming together of paradigms, ideologies, and technologies that have often resisted each other in the past. A good example is the cordial relationship that exists between the command-line and graphical interfaces in Mac OS X. The system is a result of the trials and tribulations of Apple and NeXT, as well as their user and developer communities. Mac OS X exemplifies how a capable system can result from the direct or indirect efforts of corporations, academic and research communities, the Open Source and Free Software movements, and, of course, individuals. Apple has been around since 1976, and many accounts of its history have been told. If the story of Apple as a company is fascinating, so is the technical history of Apple's operating systems. In this chapter,[1] we will trace the history of Mac OS X, discussing several technologies whose confluence eventually led to the modern-day Apple operating system. [1] This book's accompanying web site (www.osxbook.com) provides a more detailed technical history of all of Apple's operating systems. 1 2 2 1 1.1. Apple's Quest for the[2] Operating System [2] Whereas the word "the" is used here to designate prominence and desirability, it is an interesting coincidence that "THE" was the name of a multiprogramming system described by Edsger W. Dijkstra in a 1968 paper. It was March 1988. The Macintosh had been around for four years. -

Chapter 10 Introduction to Batch Files
Instructor’s Manual Chapter 10 Lecture Notes Introduction to Batch Files Chapter 10 Introduction to Batch Files LEARNING OBJECTIVES 1. Compare and contrast batch and interactive processing. 2. Explain how batch files work. 3. Explain the purpose and function of the REM, ECHO, and PAUSE commands. 4. Explain how to stop or interrupt the batch file process. 5. Explain the function and use of replaceable parameters in batch files. 6. Explain the function of pipes, filters, and redirection in batch files. STUDENT OUTCOMES 1. Use Edit to write batch files. 2. Use COPY CON to write batch files. 3. Write and execute a simple batch file. 4. Write a batch file to load an application program. 5. Use the REM, PAUSE, and ECHO commands in batch files. 6. Terminate a batch file while it is executing. 7. Write batch files using replaceable parameters. 8. Write a batch file using pipes, filters, and redirection. CHAPTER SUMMARY 1. Batch processing means running a series of instructions without interruption. 2. Interactive processing allows the user to interface directly with the computer and update records immediately. 3. Batch files allow a user to put together a string of commands and execute them with one command. 4. Batch files must have the .BAT or .CMD file extension. 5. Windows looks first internally for a command, then for a .COM files extension, then for a .EXE file extension, and finally for a .BAT or .CMD file extension. 6. Edit is a full-screen text editor used to write batch files. 7. A word processor, if it has a means to save files in ASCII, can be used to write batch files. -

Uni Hamburg – Mainframe Summit 2010 Z/OS – the Mainframe Operating System
Uni Hamburg – Mainframe Summit 2010 z/OS – The Mainframe Operating System Appendix 2 – JES and Batchprocessing Redelf Janßen IBM Technical Sales Mainframe Systems [email protected] © Copyright IBM Corporation 2010 Course materials may not be reproduced in whole or in part without the prior written permission of IBM. 4.0.1 Introduction to the new mainframe Chapter 7: Batch processing and the Job Entry Subsystem (JES) © Copyright IBM Corp., 2010. All rights reserved. Introduction to the new mainframe Chapter 7 objectives Be able to: • Give an overview of batch processing and how work is initiated and managed in the system. • Explain how the job entry subsystem (JES) governs the flow of work through a z/OS system. © Copyright IBM Corp., 2010. All rights reserved. 3 Introduction to the new mainframe Key terms in this chapter • batch processing • procedure • execution • purge • initiator • queue • job • spool • job entry subsystem (JES) • symbolic reference • output • workload manager (WLM) © Copyright IBM Corp., 2010. All rights reserved. 4 Introduction to the new mainframe What is batch processing? Much of the work running on z/OS consists of programs called batch jobs. Batch processing is used for programs that can be executed: • With minimal human interaction • At a scheduled time or on an as-needed basis. After a batch job is submitted to the system for execution, there is normally no further human interaction with the job until it is complete. © Copyright IBM Corp., 2010. All rights reserved. 5 Introduction to the new mainframe What is JES? In the z/OS operating system, JES manages the input and output job queues and data. -

Approaches to Optimize Batch Processing on Z/OS
Front cover Approaches to Optimize Batch Processing on z/OS Apply the latest z/OS features Analyze bottlenecks Evaluate critical path Alex Louwe Kooijmans Elsie Ramos Jan van Cappelle Lydia Duijvestijn Tomohiko Kaneki Martin Packer ibm.com/redbooks Redpaper International Technical Support Organization Approaches to Optimize Batch Processing on z/OS October 2012 REDP-4816-00 Note: Before using this information and the product it supports, read the information in “Notices” on page v. First Edition (October 2012) This edition applies to all supported z/OS versions and releases. This document created or updated on October 24, 2012. © Copyright International Business Machines Corporation 2012. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . .v Trademarks . vi Preface . vii The team who wrote this paper . vii Now you can become a published author, too! . viii Comments welcome. viii Stay connected to IBM Redbooks . ix Chapter 1. Getting started . 1 1.1 The initial business problem statement. 2 1.2 How to clarify the problem statement . 3 1.3 Process to formulate a good problem statement . 3 1.4 How to create a good business case . 5 1.5 Analysis methodology . 6 1.5.1 Initialization . 6 1.5.2 Analysis. 6 1.5.3 Implementation . 10 Chapter 2. Analysis steps. 13 2.1 Setting the technical strategy . 14 2.2 Understanding the batch landscape . 15 2.2.1 Identifying where batch runs and the available resources . 15 2.2.2 Job naming conventions . 15 2.2.3 Application level performance analysis. -

IBM Zenterprise BC12 (Zbc12) Enabling Enterprises of All Sizes to Build a Better Customer Experience with IBM Z Systems
IBM Systems and Technology Data Sheet IBM zEnterprise BC12 (zBC12) Enabling enterprises of all sizes to build a better customer experience with IBM z Systems Organizations around the world are recognizing the increasing role that Highlights technology plays in driving change as they shift investments from infra- structure maintenance towards new projects, such as cloud, data analytics ●● ●●Delivers increased performance, flexibility and mobile applications. To remain competitive, they must constantly and scale in a lower cost package adapt and respond with increased speed to deliver new services through ●● ●●Helps save money through consolidation multiple channels to customers, partners and employees. To capitalize on Linux® and an efficient cloud delivery on this opportunity, organizations must be able to tap into their valuable model data and energize applications without going over budget while keeping ●● ●●Enables workloads to be deployed where everything protected and secure to reduce organizational and reputation they run best and cost less with proven risk. This requires an optimized infrastructure that is integrated, agile, hybrid computing trusted and secure. ●● ●●Lets you secure it all with confidence on a trusted and resilient infrastructure The newest member of the IBM® zEnterprise® System family is the IBM zEnterprise BC12 (zBC12). Designed as an entry point for enterprise computing it embodies the same innovation and value, flexible growth options, industry-leading virtualization, trusted resiliency, secure cloud, enterprise mobility and operational analytics capabilities as the massively scalable IBM zEnterprise EC12. The zBC12 delivers a lower and more granular cost structure with significant improvements in pack- aging, performance and total system scalability over prior generations.