PRELIMINARY DRAFT DO NOT CITE REVISION / February 28, 2005
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Regime Change Consensus: Iraq in American Politics, 1990-2003
THE REGIME CHANGE CONSENSUS: IRAQ IN AMERICAN POLITICS, 1990-2003 Joseph Stieb A dissertation submitted to the faculty at the University of North Carolina at Chapel Hill in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Department of History in the College of Arts and Sciences. Chapel Hill 2019 Approved by: Wayne Lee Michael Morgan Benjamin Waterhouse Daniel Bolger Hal Brands ©2019 Joseph David Stieb ALL RIGHTS RESERVED ii ABSTRACT Joseph David Stieb: The Regime Change Consensus: Iraq in American Politics, 1990-2003 (Under the direction of Wayne Lee) This study examines the containment policy that the United States and its allies imposed on Iraq after the 1991 Gulf War and argues for a new understanding of why the United States invaded Iraq in 2003. At the core of this story is a political puzzle: Why did a largely successful policy that mostly stripped Iraq of its unconventional weapons lose support in American politics to the point that the policy itself became less effective? I argue that, within intellectual and policymaking circles, a claim steadily emerged that the only solution to the Iraqi threat was regime change and democratization. While this “regime change consensus” was not part of the original containment policy, a cohort of intellectuals and policymakers assembled political support for the idea that Saddam’s personality and the totalitarian nature of the Baathist regime made Iraq uniquely immune to “management” strategies like containment. The entrenchment of this consensus before 9/11 helps explain why so many politicians, policymakers, and intellectuals rejected containment after 9/11 and embraced regime change and invasion. -

2003 Iraq War: Intelligence Or Political Failure?
2003 IRAQ WAR: INTELLIGENCE OR POLITICAL FAILURE? A Thesis submitted to the Faculty of The School of Continuing Studies and of The Graduate School of Arts and Sciences in partial fulfillment of the requirements for the degree of Master of Arts in Liberal Studies By Dione Brunson, B.A. Georgetown University Washington, D.C. April, 2011 DISCLAIMER THE VIEWS EXPRESSED IN THIS ACADEMIC RESEARCH PAPER ARE THOSE OF THE AUTHOR AND DO NOT REFLECT THE OFFICIAL POLICIES OR POSITIONS OF THE U.S. GOVERNMENT, DEPARTMENT OF DEFENSE, OR THE U.S. INTELLIGENCE COMMUNITY. ALL INFORMATION AND SOURCES FOR THIS PAPER WERE DRAWN FROM OPEN SOURCE MATERIALS. ii 2003 IRAQ WAR: INTELLIGENCE OR POLITICAL FAILURE? Dione Brunson, B.A. MALS Mentor: Ralph Nurnberger, Ph.D. ABSTRACT The bold U.S. decision to invade Iraq in 2003 was anchored in intelligence justifications that would later challenge U.S. credibility. Policymakers exhibited unusual bureaucratic and public dependencies on intelligence analysis, so much so that efforts were made to create supporting information. To better understand the amplification of intelligence, the use of data to justify invading Iraq will be explored alongside events leading up to the U.S.-led invasion in 2003. This paper will examine the use of intelligence to invade Iraq as well as broader implications for politicization. It will not examine the justness or ethics of going to war with Iraq but, conclude with the implications of abusing intelligence. iii ACKNOWLEDGMENTS Thank you God for continued wisdom. Thank you Dr. Nurnberger for your patience. iv DEDICATION This work is dedicated to Mom and Dad for their continued support. -

The Path to 9/11 | Vanity Fair
The Path to 9/11 | Vanity Fair https://www.vanityfair.com/news/2004/11/path-to-9-11-200411 Sign In Subscribe The Price of Failure THE PATH TO 9/11: LOST WARNINGS AND FATAL ERRORS By the time the hijackers made their way into the U.S., memos, photographs, and intercepts had sounded alarms inside the C.I.A., White House, F.B.I., and European intelligence services. Could better cooperation have stopped the attacks? Ned Zeman, David Wise, David Rose, and Bryan Burrough show how the hideous “Planes Operation” took shape as the C.I.A.’s bin Laden point man, Mike Scheuer, counterterrorism czar Richard Clarke, the F.B.I.’s John MacGaffin, and others fought—yet couldn’t work together—to prevent it. BY NED ZEMAN, DAVID WISE, DAVID ROSE, AND BRYAN BURROUGH ! " # DECEMBER 19, 2008 12:00 AM ith his salt-and-pepper hair, white shirt, and sensible shoes, Mike Scheuer, 44, looked like a rumpled academician, or maybe a consultant for one of the many defense contractors [#image: /photos/54cbf62044a199085e88c698]sprinkled around the W Washington Beltway. In reality, his job was considerably more interesting. Starting in 1996, he was the man the C.I.A. had assigned to hunt down, capture, or kill Osama bin Laden. Of all the agency’s far-flung stations—from Moscow to Prague to Beijing—Scheuer’s was unique. Known among the spooks as a “virtual station,” it was not overseas but near the C.I.A. headquarters, in Langley, Virginia, eight miles west of Washington. 3 ARTICLES LEFT Subscribe Sign In 1 of 53 11/11/18, 17:18 The Path to 9/11 | Vanity Fair https://www.vanityfair.com/news/2004/11/path-to-9-11-200411 The station was the first to target an individual rather than a country. -

Location, Event&Q
# from what/ where which how why who for MOBILE versi on click here when who who where when index source "location, event" "phys, pol, med, doc" detail physical detail political name "9/11 Truth Interactive Spreadsheet Click on dow n arrow to sort / filter, click again to undo." Top 100 / compilations entity entity detail country / state date Item .. right-click on li nk to open in new tab 1 "Francis, Stephen NFU" WTC physical Controlled demolition Explosive experts "Overwhelming evidence indicates that a combination of n uclear, thermitic and conventional explosives were used in a controlled demoliti on of the WTC on 9/11. Nanothermite contributed but does not have sufficient det onation velocity to pulverize the WTC into dust. Architects & Engineers for 9/11 Truth is leading gatekeeper trying to deflect Israel's role. See Cozen O'Connor 9/11 lawsuit." pic "9/11 Truth, anti-Zionists" Engineers / Scie ntists "U.S., Israel, SA, Britain" 2 "Francis, Stephen NFU" "WTC, Pentagon, PA" political False flag Cabal "The cabal: U.S., Britain, Saudi Arabia and Israel execu ted the 9/11 false flag attack in order to usher in a new 'war on terror' along with the Iraq and Afghanistan wars and fullfil the PNAC's 'Full Spectrum Dominan ce' of the Middle East and its resources ... all have roots that go back to Zion ist / Nazi Germany, the Cold War ... 9/11 was a planned step." lnk Intel ag encies "Cabal: US, UK, Israel & SA" Mossad / Sayeret Matkal "U.S., Israel, S A, Britain" 3 "Fox, Donald" WTC 1-2 physical "Mini Neutron, Fissionless Fusio n" Controlled demolition "VeteransToday: Fox, Kuehn, Prager, Vike n,Ward, Cimono & Fetzer on mini neutron bombs discuss all major WTC theories micr o nuke (neutron) most promising comparatively low blast effects, a quick blast o f radiation that doesn't linger, a series of shape charged mini-neutron bombs we re detonated from top to bottom to simulate a free fall collapse. -

Total Terror Plots*
NSA DATA COLLECTION PROGRAM: THE CHALLENGE OF ASSESING EFFECTIVENESS Item Type text; Electronic Thesis Authors DEIBEL, CHARLES LOUIS, II Publisher The University of Arizona. Rights Copyright © is held by the author. Digital access to this material is made possible by the University Libraries, University of Arizona. Further transmission, reproduction or presentation (such as public display or performance) of protected items is prohibited except with permission of the author. Download date 28/09/2021 10:48:12 Item License http://rightsstatements.org/vocab/InC/1.0/ Link to Item http://hdl.handle.net/10150/613829 NSA DATA COLLECTION PROGRAM: THE CHALLENGE OF ASSESING EFFECTIVENESS By CHARLES LOUIS DEIBEL II ____________________ A Thesis Submitted to The Honors College In Partial Fulfillment of the Bachelors degree With Honors in Political Science THE UNIVERSITY OF ARIZONA M A Y 2 0 1 6 Approved by: ____________________________ Dr. John Tidd School of Government and Public Policy Abstract The National Security Agency (NSA) has played a key role in the United States Government’s counterterror program since September 11. Over the last 15 years, the NSA has faced considerable controversy regarding its counterterrorism data collection program and the legal authority behind it. This paper, however, is concerned with whether or not that program has been effective in preventing Islamist related or inspired terror attacks inside the United States. As NSA capabilities and authorities have expanded since 9/11, has it been effective in helping to prevent attacks in the U.S.? Definitively answering this question is extremely difficult, given significant challenges regarding the amount and quality of public information concerning NSA’s involvement in prevented terror attacks. -

America's Alleged Intelligence Failure in The
University of Calgary PRISM: University of Calgary's Digital Repository Graduate Studies The Vault: Electronic Theses and Dissertations 2017 America’s Alleged Intelligence Failure in the Prelude to Operation Iraqi Freedom: A Study of Analytic Factors Cake, Timothy Cake, T. (2017). America’s Alleged Intelligence Failure in the Prelude to Operation Iraqi Freedom: A Study of Analytic Factors (Unpublished doctoral thesis). University of Calgary, Calgary, AB. doi:10.11575/PRISM/24784 http://hdl.handle.net/11023/3688 doctoral thesis University of Calgary graduate students retain copyright ownership and moral rights for their thesis. You may use this material in any way that is permitted by the Copyright Act or through licensing that has been assigned to the document. For uses that are not allowable under copyright legislation or licensing, you are required to seek permission. Downloaded from PRISM: https://prism.ucalgary.ca UNIVERSITY OF CALGARY America’s Alleged Intelligence Failure in the Prelude to Operation Iraqi Freedom: A Study of Analytic Factors by Timothy Cake A DISSERTATION SUBMITTED TO THE FACULTY OF GRADUATE STUDIES IN PARTIAL FULFILMENT OF THE REQUIREMENTS FOR THE DEGREE OF DOCTOR OF PHILOSOPHY GRADUATE PROGRAM IN MILITARY, SECURITY, AND STRATEGIC STUDIES CALGARY, ALBERTA APRIL, 2017 © Timothy Cake 2017 ABSTRACT In the prelude to Operation Iraqi Freedom (OIF), notables in the G. W. Bush administration declared Iraq to be an existential threat as it had weapons of mass destruction (WMD) and connections to transnational terrorist groups. After the 2003 invasion of that state, coalition forces engaged in a search effort that found no significant evidence of WMD. -
Nuclear Proliferation and Preventive War∗
Nothing to Fear but Fear Itself? Nuclear Proliferation and Preventive War∗ Alexandre Debsy and Nuno Monteiroz November 5, 2010 Abstract When does nuclear counterproliferation succeed? When does it lead to preventive war? We argue that the answers to these questions hinge on the effect of nuclearization on the balance of power relative to the cost of preventive war. When it is low, threats of preventive war are not credible; proliferation continues apace and peace prevails. Such was the case during the Cold War. When it is high, threats of preventive war are credible, slowing down the rate of proliferation. At the same time, since the decision to proliferate is not perfectly observable, there is a higher likelihood of mistaken preventive wars. This characterizes the post Cold War. We trace the logic of our argument by looking at the cases of Soviet nuclear acquisition in 1949 and the US-led invasion of Iraq in 2003. Keywords: deterrence, nuclear weapons, power, preventive war, proliferation. ∗We thank Jonathan Caverley, Jonathan Kirshner, Andrew Kydd, Barry Posen, Andrew Ross, Joshua Rovner, Bruce Russett, Duncan Snidal, workshop participants at Cornell, Madison, MIT, and Yale, and audiences at the ISSS/ISAC and PSS annual meetings for their comments and suggestions; and Will Bruno, Bonny Lin, and Hayden Stein for their research assistance. yDept. of Political Science, Yale University. Email: [email protected] zDept. of Political Science, Yale University. Email: [email protected] 1 1 Introduction In October 2002, pressing the case for invading Iraq, President Bush warned of terrible con- sequences should Saddam Hussein acquire nuclear weapons. -

A Thesis Entitled Rogue State? the United States, Unilateralism, and the United Nations by Robert L. Macdonald Submitted As
A Thesis Entitled Rogue State? The United States, Unilateralism, and the United Nations By Robert L. MacDonald Submitted as partial fulfillment of the requirements for The Master of Arts in History ________________________ Advisor: Diane Britton ________________________ Graduate School The University of Toledo August 2006 Copyright © 2006 This document is copyrighted material. Under copyright law, no parts of this document may be reproduced without the expressed permission of the author. ii Acknowledgements This project could not have succeeded without the help, support, and encouragement of my family, friends, and professors during the past few years. I wish to thank Dr. Diane Britton for her commitment to be my advisor throughout this process and her open-mindedness in finding a link between her interests and research and the topic discussed in the following pages. I wish to thank Drs. Peter Linebaugh, Charles Beatty Medina, and Timothy Messer-Kruse for their willingness to serve as members of my committee and for their thoughtful questions and insightful commentary. I will keep their advice close at hand as I continue to develop my researching and writing skills. I wish to especially thank Dr. Ruth Herndon, who has served as a mentor during both my undergraduate and graduate years at the University of Toledo, for always seeing the best in my work while thoughtfully challenging me to do better. I wish also to thank all of the professors that I have worked with while at the University of Toledo, including of course William Longton, Michael Jakobson, Ron Lora, William O’Neal, Roger Ray, Charles Glaab, Robert Smith, and Alfred Cave. -

THE IRAQ WAR -- PART I: the U.S
1 THE IRAQ WAR -- PART I: The U.S. Prepares for Conflict, 2001 National Security Archive Electronic Briefing Book No. 326 Timeline By Joyce Battle 1985 – Academic Albert Wohlstetter supporter, neoconservative Richard Perle, introduces Iraqi expatriate Ahmad Chalabi reportedly raises most of the group’s to Paul Wolfowitz and Richard Perle, funding from defense contractors and a neoconservatives later influential in the right-wing foundation. Bandar attracts George W. Bush administration. 1 support from several Jewish organizations by telling them that if Saddam Hussein 1989 -- Petra Bank of Amman, founded were eliminated other governments in the by Ahmad Chalabi and influential through region would deal with the Arab-Israeli its strategic lending to prominent conflict on more “pragmatic terms."5 Jordanians, including the king of Jordan’s brother, is seized by the government for October 10, 1990 -- An informal alleged irregularities. Chalabi flees the association called the Congressional country in the trunk of a car. Two years Human Rights Caucus holds a hearing on later he is convicted in absentia for reported Iraqi atrocities. The association embezzlement and fraud and sentenced to is chaired by Tom Lantos (D-CA) and John 22 years in prison.2 Porter (R-IL) who also head the Congressional Human Rights Foundation, 1990 – Prominent neoconservative which is headquartered in free office space academic Bernard Lewis meets Ahmad at Hill & Knowlton's Washington, D.C. Chalabi and becomes one of his leading office. At the hearing a 15-year-old advocates.3 Kuwaiti girl says she witnessed Iraqi soldiers leaving babies on the floor to die August 2, 1990 -- Iraq invades Kuwait, in order to steal incubators; the story is accusing it of conspiring with the U.S. -

Team B Intelligence Coups Gordon R
Quarterly Journal of Speech Vol. 92, No. 2, May 2006, pp. 144Á173 Team B Intelligence Coups Gordon R. Mitchell The 2003 Iraq prewar intelligence failure was not simply a case of the U.S. intelligence community providing flawed data to policy-makers. It also involved subversion of the competitive intelligence analysis process, where unofficial intelligence boutiques ‘‘stovepiped’’ misleading intelligence assessments directly to policy-makers and undercut intelligence community input that ran counter to the White House’s preconceived preventive war of choice against Iraq. This essay locates historical precursors to such ‘‘Team B intelligence coups’’ in the original 1976 Team B exercise and the 1998 Rumsfeld Commission report on ballistic missile threats. Since competitive intelligence analysis exercises are designed to improve decision-making by institutionalizing the learning function of debate, their dynamics stand to be elucidated through critique informed by argumentation theory. Such inquiry has salience in the current political milieu, where intelligence reform efforts and the investigations that drive them tend to sidestep the Team B intelligence coup phenomenon. Keywords: Argumentation; Debate; Public Argument; Team B; Intelligence Analysis; Iraq War; Cold War The autumn 2004 rush to implement intelligence reform based on recommendations from the ‘‘9/11 Commission’’1 reminds some of Sancho Panza*Don Quixote’s squire who dutifully ‘‘galloped off in all directions’’ before mapping out a clear route.2 In the politically charged environment of a presidential election, leaders from both major U.S. political parties scrambled to embrace the 9/11 Commission’s proposals for wholesale restructuring of the intelligence community.3 Their hurried reform effort reached fruition with passage of the Intelligence Reform and Terrorism Gordon R. -

Neoconservatism and Iraq Ryan Patrick Mchargue
Florida State University Libraries Electronic Theses, Treatises and Dissertations The Graduate School 2005 Neoconservatism and Iraq Ryan Patrick McHargue Follow this and additional works at the FSU Digital Library. For more information, please contact [email protected] THE FLORIDA STATE UNIVERSITY COLLEGE OF ARTS AND SCIENCES NEOCONSERVATISM AND IRAQ By RYAN PATRICK MCHARGUE A Thesis submitted to the Department of History in partial fulfillment of the requirements for the degree of Master of Arts Degree Awarded: Summer Semester, 2005 The members of the Committee approve the Thesis of Ryan Patrick McHargue defended on June 2, 2005. ___________________________ Peter P. Garretson Professor Directing Thesis ___________________________ James P. Jones Committee Member ___________________________ Max Friedman Committee Member The Office of Graduate Studies has verified and approved the above named committee members. ii This thesis is dedicated to my father, Rod McHargue, without whom I would have never developed such a keen interest in politics and policy. iii ACKNOWLEDGEMENTS I would like to give my utmost thanks to Dr. Peter Garretson for being just as interested as I am in the subject matter of this thesis. All of my friends, who put up with my constant complaining about the impending due date and subject matter of my thesis, all deserve many thanks for helping me through the writing process. And, of course, I would never be here if it wasn’t for the constant nagging (encouragement?) of my parents, who invested almost as much time and patience into my education as I did. iv TABLE OF CONTENTS ABSTRACT ...................................................................................................... Page vi INTRODUCTION.............................................................................................. Page 1 1. -
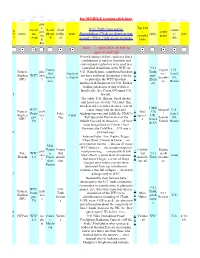
For MOBILE Version Click Here 9/11 Truth Interactive Spreadsheet Click on Down Arrow to Sort / Filter, Click Again to Undo. Item
what/ whi # from where ch how why who for MOBILE version click here when who who where when phy s, Top 100 locati detail detail 9/11 Truth Interactive countr in pol, / entity de source on, physic politic name entity y / date me Spreadsheet Click on down arrow compila detail x event al al state d, to sort / filter, click again to undo. tions doc Item ….. right-click on link to open in new tab Overwhelming evidence indicates that a combination of nuclear, thermitic and conventional explosives were used in a controlled demolition of the WTC on 9/11 Contro Engine U.S., Francis, phy 9/11. Nanothermite contributed but does p Truth, lled Explosiv ers / Israel, Stephen WTC sica not have sufficient detonation velocity i anti- demoli e experts Scientis SA, NFU l to pulverize the WTC into dust. c Zioni tion ts Britain Architects & Engineers for 9/11 Truth is sts leading gatekeeper trying to deflect Israel's role. See Cozen O'Connor 9/11 1 lawsuit. The cabal: U.S., Britain, Saudi Arabia and Israel executed the 9/11 false flag attack in order to usher in a new 'war on Cabal WTC, terror' along with the Iraq and Mossad U.S., Francis, poli l Intel : US, Penta False Afghanistan wars and fullfil the PNAC's / Israel, Stephen tica Cabal n agencie UK, gon, flag 'Full Spectrum Dominance' of the Sayeret SA, NFU l k s Israel PA Middle East and its resources ... all have Matkal Britain & SA roots that go back to Zionist / Nazi Germany, the Cold War ..