Remote Peering: More Peering Without Internet Flattening
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PEERING: an AS for Us
PEERING: An AS for Us Brandon Schlinker1, Kyriakos Zarifis1, Italo Cunha2, Nick Feamster3, and Ethan Katz-Bassett1 1University of Southern California — 2Universidade Federal de Minas Gerais — 3Georgia Institute of Technology {bschlink, kyriakos, ethan.kb}@usc.edu — [email protected] — [email protected] ABSTRACT 29, 45]. BGP, the Internet’s interdomain routing protocol, Internet routing suffers from persistent and transient failures, can experience slow convergence [30] and persistent route circuitous routes, oscillations, and prefix hijacks. A ma- oscillations [17,54]. It lacks mechanisms to prevent spoof- jor impediment to progress is the lack of ways to conduct ing [5,27] and prefix hijacks [24,32,58]. Despite known impactful interdomain research. Most research is based ei- problems, little has changed with interdomain routing, and ther on passive observation of existing routes, keeping re- there has been little impactful research in recent years. searchers from assessing how the Internet will respond to This stagnancy in the face of known problems is in stark route or policy changes; or simulations, which are restricted contrast to the rapid innovation in other areas of network- by limitations in our understanding of topology and policy. ing. We are in an era of remarkable changes in networking We propose a new class of interdomain research: re- and its role in our lives, as mobile connectivity and stream- searchers can instantiate an AS of their choice, including ing video change how we use the Internet, and advances in its intradomain topology and interdomain interconnectivity, software defined networking and data centers change how and connect it with the “live” Internet to exchange routes we run networks. -

Hacking the Master Switch? the Role of Infrastructure in Google's
Hacking the Master Switch? The Role of Infrastructure in Google’s Network Neutrality Strategy in the 2000s by John Harris Stevenson A thesis submitteD in conformity with the requirements for the Degree of Doctor of Philosophy Faculty of Information University of Toronto © Copyright by John Harris Stevenson 2017 Hacking the Master Switch? The Role of Infrastructure in Google’s Network Neutrality Strategy in the 2000s John Harris Stevenson Doctor of Philosophy Faculty of Information University of Toronto 2017 Abstract During most of the decade of the 2000s, global Internet company Google Inc. was one of the most prominent public champions of the notion of network neutrality, the network design principle conceived by Tim Wu that all Internet traffic should be treated equally by network operators. However, in 2010, following a series of joint policy statements on network neutrality with telecommunications giant Verizon, Google fell nearly silent on the issue, despite Wu arguing that a neutral Internet was vital to Google’s survival. During this period, Google engaged in a massive expansion of its services and technical infrastructure. My research examines the influence of Google’s systems and service offerings on the company’s approach to network neutrality policy making. Drawing on documentary evidence and network analysis data, I identify Google’s global proprietary networks and server locations worldwide, including over 1500 Google edge caching servers located at Internet service providers. ii I argue that the affordances provided by its systems allowed Google to mitigate potential retail and transit ISP gatekeeping. Drawing on the work of Latour and Callon in Actor– network theory, I posit the existence of at least one actor-network formed among Google and ISPs, centred on an interest in the utility of Google’s edge caching servers and the success of the Android operating system. -

Interconnection
Interconnection 101 As cloud usage takes off, data production grows exponentially, content pushes closer to the edge, and end users demand data and applications at all hours from all locations, the ability to connect with a wide variety of players becomes ever more important. This report introduces interconnection, its key players and busi- ness models, and trends that could affect interconnection going forward. KEY FINDINGS Network-dense, interconnection-oriented facilities are not easy to replicate and are typically able to charge higher prices for colocation, as well as charging for cross-connects and, in some cases, access to public Internet exchange platforms and cloud platforms. Competition is increasing, however, and competitors are starting the long process of creating network-dense sites. At the same time, these sites are valuable and are being acquired, so the sector is consolidating. Having facili- ties in multiple markets does seem to provide some competitive advantage, particularly if the facilities are similar in look and feel and customers can monitor them all from a single portal and have them on the same contract. Mobility, the Internet of Things, services such as SaaS and IaaS (cloud), and content delivery all depend on net- work performance. In many cases, a key way to improve network performance is to push content, processing and peering closer to the edge of the Internet. This is likely to drive demand for facilities in smaller markets that offer interconnection options. We also see these trends continuing to drive demand for interconnection facilities in the larger markets as well. © 2015 451 RESEARCH, LLC AND/OR ITS AFFILIATES. -
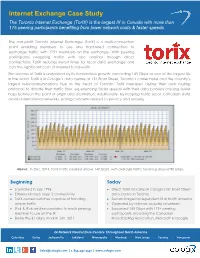
Cologix Torix Case Study
Internet Exchange Case Study The Toronto Internet Exchange (TorIX) is the largest IX in Canada with more than 175 peering participants benefiting from lower network costs & faster speeds The non-profit Toronto Internet Exchange (TorIX) is a multi-connection point enabling members to use one hardwired connection to exchange traffic with 175+ members on the exchange. With peering participants swapping traffic with one another through direct connections, TorIX reduces transit times for local data exchange and cuts the significant costs of Internet bandwidth. The success of TorIX is underlined by its tremendous growth, exceeding 145 Gbps as one of the largest IXs in the world. TorIX is in Cologix’s data centre at 151 Front Street, Toronto’s carrier hotel and the country’s largest telecommunications hub in the heart of Toronto. TorIX members define their own routing protocols to dictate their traffic flow, experiencing faster speeds with their data packets crossing fewer hops between the point of origin and destination. Additionally, by keeping traffic local, Canadian data avoids international networks, easing concerns related to privacy and security. Above: In Dec. 2014, TorIX traffic peaked above 140 Gbps, with average traffic hovering around 90 Gbps. Beginning Today Launched in July 1996 Direct TorIX on-ramp in Cologix’s151 Front Street Ethernet-based, layer 2 connectivity data centre in Toronto TorIX-owned switches capable of handling Second largest independent IX in North America ample traffic Operated by telecom industry volunteers IPv4 & IPv6 address provided to each peering Surpassed 145 Gbps with 175+ peering member to use on the IX participants, including the Canadian Broke the 61 Gbps mark in Jan. -

Peering Concepts and Definitions Terminology and Related Jargon
Peering Concepts and Definitions Terminology and Related Jargon Presentation Overview Brief On Peering Jargon Peering & Related Jargon BRIEF ON PEERING JARGON Brief On Peering Jargon A lot of terminologies used in the peering game. We shall look at the more common ones. Will be directly related to peering, as well as ancillary non-peering functions that support peering. PEERING & RELATED JARGON Peering & Related Jargon ASN (or AS - Autonomous System Number): . A unique number that identifies a collection/grouping of IP addresses or networks under the control of one entity on the Internet Bi-lateral (peering): . Peering relationships setup “directly” between two networks (see “Multi-lateral [peering]”). BGP (Border Gateway Protocol): . Routing protocol used on the Internet and at exchange points as the de-facto routing technique to share routing information (IPs and prefixes) between networks or between ASNs Peering & Related Jargon Carrier-neutral (data centre): . A facility where customers can purchase network services from “any” other networks within the facility. Cold-potato routing: . A situation where a network retains traffic on its network for as long as possible (see “Hot-potato routing”). Co-lo (co-location): . Typically a data centre where customers can house their network/service infrastructure. Peering & Related Jargon Dark fibre: . Fibre pairs offered by the owner, normally on a lease basis, without any equipment at each end of it to “activate” it (see “Lit fibre”). Data centre: . A purpose-built facility that provides space, power, cooling and network facilities to customers. Demarc (Demarcation): . Typically information about a co-lo customer, e.g., rack number, patch panel and port numbers, e.t.c. -

Peering Personals at TWNOG 4.0
Peering Personals at TWNOG 4.0 6 Dec. 2019 請注意, Peering Personal 場次將安排於下午時段的演講結束前進行, 請留意議程進行以 確保報告人當時在現場 Please note that Peering Personals will be done in the afternoon sessions so please check with Agenda and be on site. AS number 10133 (TPIX) and 17408 (Chief Telecom) Traffic profile Internet Exchange (Balanced) + ISP (Balanced) Traffic Volume TPIX: 160 Gbps ( https://www.tpix.net.tw/traffic.html ); Chief: 80 Gbps (2015- 10.7G; 2016- 25.9G; 2017- 58G; 2018- 96G) Peering Policy Open Peering Locations Taiwan: TPIX, Chief LY, Chief HD HK: HKIX, AMS-IX, EIE (HK1), Mega-i Europe: AMS-IX Message Biggest IX in Taiwan in both traffic and AS connected (59). Contact •[email protected] or •https://www.peeringdb.com/ix/823 •[email protected] or •https://www.peeringdb.com/net/8666 AS number 7527(JPIX) Traffic profile Internet Exchange (Balanced) Traffic Volume JPIX Tokyo 1.2T &JPIX Osaka 600G Peering Policy Open Peering Locations Tokyo: KDDI Otemachi, NTT Data Otemachi ,Comspace I, Equinix, Tokyo, AT Tokyo, COLT TDC1, NTT DATA Mitaka DC East, NTT COM Nexcenter DC, Meitetsucom DC (Nagoya),OCH DC (Okinawa), BBT New Otemachi DC Osaka: NTT Dojima Telepark, KDDI TELEHOUSE Osaka2, Equinix OS1,Meitetsucom DC (Nagoya), OBIS DC (Okayama) Site introduction: https://www.jpix.ad.jp/en/service_introduction.php Message Of connected ASN: Tokyo 211 Osaka 70 Remarks Our IX switch in Nagoya can offer both JPIX Tokyo vlan and Osaka one. Contact •[email protected] or [email protected] AS number 41095 Traffic profile 1:3 Balanced where content prevail Traffic Volume -

Mapping Peering Interconnections to a Facility
Mapping Peering Interconnections to a Facility Vasileios Giotsas Georgios Smaragdakis Bradley Huffaker CAIDA / UC San Diego MIT / TU Berlin CAIDA / UC San Diego [email protected] [email protected] bhuff[email protected] Matthew Luckie kc claffy University of Waikato CAIDA / UC San Diego [email protected] [email protected] ABSTRACT CCS Concepts Annotating Internet interconnections with robust phys- •Networks ! Network measurement; Physical topolo- ical coordinates at the level of a building facilitates net- gies; work management including interdomain troubleshoot- ing, but also has practical value for helping to locate Keywords points of attacks, congestion, or instability on the In- Interconnections; peering facilities; Internet mapping ternet. But, like most other aspects of Internet inter- connection, its geophysical locus is generally not pub- lic; the facility used for a given link must be inferred to 1. INTRODUCTION construct a macroscopic map of peering. We develop a Measuring and modeling the Internet topology at the methodology, called constrained facility search, to infer logical layer of network interconnection, i. e., autonomous the physical interconnection facility where an intercon- systems (AS) peering, has been an active area for nearly nection occurs among all possible candidates. We rely two decades. While AS-level mapping has been an im- on publicly available data about the presence of net- portant step to understanding the uncoordinated forma- works at different facilities, and execute traceroute mea- tion and resulting structure of the Internet, it abstracts surements from more than 8,500 available measurement a much richer Internet connectivity map. For example, servers scattered around the world to identify the tech- two networks may interconnect at multiple physical lo- nical approach used to establish an interconnection. -

Société, Information Et Nouvelles Technologies: Le Cas De La Grande
Société, information et nouvelles technologies : le cas de la Grande-Bretagne Jacqueline Colnel To cite this version: Jacqueline Colnel. Société, information et nouvelles technologies : le cas de la Grande-Bretagne. Sciences de l’information et de la communication. Université de la Sorbonne nouvelle - Paris III, 2009. Français. NNT : 2009PA030015. tel-01356701 HAL Id: tel-01356701 https://tel.archives-ouvertes.fr/tel-01356701 Submitted on 26 Aug 2016 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. UNIVERSITE SORBONNE NOUVELLE – PARIS 3 UFR du Monde Anglophone THESE DE DOCTORAT Discipline : Etudes du monde anglophone AUTEUR Jacqueline Colnel SOCIETE, INFORMATION ET NOUVELLES TECHNOLOGIES : LE CAS DE LA GRANDE-BRETAGNE Thèse dirigée par Monsieur Jean-Claude SERGEANT Soutenue le 14 février 2009 JURY : Mme Renée Dickason M. Michel Lemosse M. Michaël Palmer 1 REMERCIEMENTS Je remercie vivement Monsieur le Professeur Jean-Claude SERGEANT, mon directeur de thèse, qui a accepté de diriger mes recherches, m’a guidée et m’a prodigué ses précieux conseils avec bienveillance tout au long de ces années avec beaucoup de disponibilité. Mes remerciements vont aussi à ma famille et à mes amis qui m’ont beaucoup soutenue pendant cettre entreprise. -

Competitive Effects of Internet Peering Policies
Competitive Effects of Internet Peering Policies by Paul Milgrom, Bridger Mitchell and Padmanabhan Srinagesh Reprinted from The Internet Upheaval, Ingo Vogelsang and Benjamin Compaine (eds), Cambridge: MIT Press (2000): 175-195. ABSTRACT This paper analyzes of two kinds of Internet interconnection arrangements: peering relationships between core Internet Service Providers (ISPs) and transit sales by core ISPs to other ISPs. Core backbone providers jointly produce an intermediate output -- full routing capability -- in an upstream market. All ISPs use this input to produce Internet-based services for end users in a downstream market. It is argued that a vertical market structure with relatively few core ISPs can be relatively efficient given the technological economies of scale and transaction costs arising from Internet addressing and routing. The analysis of costs identifies instances in which an incumbent core ISP’s refusal to peer with a rival or potential rival might promote economic efficiency. A separate bargaining analysis of peering relationships identifies conditions under which a core ISP might be able to use its larger size and associated network effects to refuse to peer with a rival, thus raising its rival’s costs and ultimately increasing prices to end users. An economic analysis of competitive harm arising from refusals to peer should consider cost-based, efficiency-enhancing justifications as well as attempts to raise rivals’ costs. Paul Milgrom Bridger Mitchell and Padmanabhan Srinagesh Department of Economics Charles River Associates Stanford University 285 Hamilton Avenue Stanford, CA 94305-6072 Palo Alto, CA 94301 2 1 Introduction This paper describes the technology and organization of Internet services markets and analyses how peering arrangements among core Internet Service Providers (ISPs) can affect efficiency and competition in these markets. -

A Vital Part of the Critical National Infrastructure Version
Telecommunications Networks – a vital part of the Critical National Infrastructure Version 1.0 The Essentials of Telecommunications - an introduction Version 1.0 1 Telecommunications Networks – A Vital Part of the Critical National Infrastructure CONTENTS page no Executive Summary 3 Introduction 4 Chapter 1: The Nature of UK Telecommunications Networks - Describes the nature of the UK telecommunications networks. If you are familiar with telecommunications, you may want to skip straight to Chapter 2. 5 Chapter 2: Types of Telecommunications Companies in the UK - Describes the commercial environment and the wide variety of telecommunications providers in the market, which collectively make up the ‘UK Network’. 14 Chapter 3: Threats to Continuity of Service - Describes the wide range of threats to the continuity of service over the UK networks. 16 Chapter 4: Resilience measures taken by telecommunications companies- Covers the typical measures taken by the network companies to meet the challenges posed by these threats and mentions some of the remaining residual problems. 18 Chapter 5: Statutory provisions concerning telecommunications resilience - Telecommunications is now a competitive private sector activity, there are a range of statutory provisions that touch on the government’s ability to assure the resilience of the UK networks and these are described in Chapter 5. 21 Chapter 6: Roles of Government departments, the regulator and other agencies - Sets out the roles and responsibilities of the various government departments, the regulator (Ofcom) and other agencies, describing how in practice they work together as an extended team in assuring resilience. 27 Chapter 7: Emergency Plans and response measures - Covers the present arrangements in the telecommunications sector which ensure that industry and government work effectively together in emergencies and other times of stress. -

8 March 2018, Dubai Pre-Event: Subsea Middle East Summit & 5 March Welcome Evening Reception
Middle East 2018 6 - 8 March 2018, Dubai Pre-Event: Subsea Middle East Summit & 5 March Welcome Evening Reception THANK YOU TO THE SPONSORS: HOST SPONSOR DIAMOND SPONSOR PLATINUM SPONSORS tawasul telecom ITW Logo Bold & Bigger GOLD SPONSORS SILVER SPONSORS ASSOCIATE SPONSORS 1587 450 ATTENDEES ORGANISATIONS 52% 80 C-LEVEL, PRESIDENT, VP, COUNTRIES REPRESENTED SVP, EVP, DIRECTOR & HEAD 54 128 INDUSTRY LEADING SPEAKERS NEW COMPANIES COUNTRIES IN ATTENDANCE AFGHANISTAN CZECH REPUBLIC ISRAEL NEPAL SOMALIA ALBANIA DJIBOUTI ITALY NETHERLANDS SOUTH AFRICA ARMENIA EGYPT JAPAN NEW ZEALAND SPAIN AUSTRALIA ESPANA JORDAN NORWAY SRI LANKA AUSTRIA ESTONIA KAZAKHSTAN OMAN SUDAN BAHRAIN FRANCE KENYA PAKISTAN SWEDEN BANGLADESH GERMANY KUWAIT PALESTINE SWITZERLAND BELGIUM GREECE KYRGYZSTAN POLAND TURKEY BERMUDA GUINEA LATVIA PORTUGAL UKRAINE BOSNIA AND HONG KONG LEBANON QATAR UNITED ARAB HERZEGOVINA HUNGARY LITHUANIA ROMANIA EMIRATES BRAZIL INDIA LUXEMBOURG RUSSIA UNITED KINGDOM BULGARIA INDONESIA MALAYSIA SAUDI ARABIA UNITED STATES CAMEROON IRAN MALTA SERBIA USA CANADA IRAQ MAURITIUS SINGAPORE UZBEKISTAN CHINA IRELAND MOROCCO SLOVENIA YEMEN CYPRUS WHAT SOME OF THE ATTENDEES HAD TO SAY “Capacity Middle East is one of the key events in the calendar. The attendance level is always very good in both num- “We are here at Capacity Middle East ber and seniority and it’s a great place as usual to meet our customers - the to be” old ones and the new” Ivan Botta Carl Roberts CEO CCO ENTER SRL EPSILON TELECOMMUNICATIONS “Capacity Middle East offers a great platform to meet with our clients. It’s a great opportuni- ty to meet a lot of new partners and connec- tions and grow the business. -

Abkürzungs-Liste ABKLEX
Abkürzungs-Liste ABKLEX (Informatik, Telekommunikation) W. Alex 1. Juli 2021 Karlsruhe Copyright W. Alex, Karlsruhe, 1994 – 2018. Die Liste darf unentgeltlich benutzt und weitergegeben werden. The list may be used or copied free of any charge. Original Point of Distribution: http://www.abklex.de/abklex/ An authorized Czechian version is published on: http://www.sochorek.cz/archiv/slovniky/abklex.htm Author’s Email address: [email protected] 2 Kapitel 1 Abkürzungen Gehen wir von 30 Zeichen aus, aus denen Abkürzungen gebildet werden, und nehmen wir eine größte Länge von 5 Zeichen an, so lassen sich 25.137.930 verschiedene Abkür- zungen bilden (Kombinationen mit Wiederholung und Berücksichtigung der Reihenfol- ge). Es folgt eine Auswahl von rund 16000 Abkürzungen aus den Bereichen Informatik und Telekommunikation. Die Abkürzungen werden hier durchgehend groß geschrieben, Akzente, Bindestriche und dergleichen wurden weggelassen. Einige Abkürzungen sind geschützte Namen; diese sind nicht gekennzeichnet. Die Liste beschreibt nur den Ge- brauch, sie legt nicht eine Definition fest. 100GE 100 GBit/s Ethernet 16CIF 16 times Common Intermediate Format (Picture Format) 16QAM 16-state Quadrature Amplitude Modulation 1GFC 1 Gigabaud Fiber Channel (2, 4, 8, 10, 20GFC) 1GL 1st Generation Language (Maschinencode) 1TBS One True Brace Style (C) 1TR6 (ISDN-Protokoll D-Kanal, national) 247 24/7: 24 hours per day, 7 days per week 2D 2-dimensional 2FA Zwei-Faktor-Authentifizierung 2GL 2nd Generation Language (Assembler) 2L8 Too Late (Slang) 2MS Strukturierte