Competitive Effects of Internet Peering Policies
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PEERING: an AS for Us
PEERING: An AS for Us Brandon Schlinker1, Kyriakos Zarifis1, Italo Cunha2, Nick Feamster3, and Ethan Katz-Bassett1 1University of Southern California — 2Universidade Federal de Minas Gerais — 3Georgia Institute of Technology {bschlink, kyriakos, ethan.kb}@usc.edu — [email protected] — [email protected] ABSTRACT 29, 45]. BGP, the Internet’s interdomain routing protocol, Internet routing suffers from persistent and transient failures, can experience slow convergence [30] and persistent route circuitous routes, oscillations, and prefix hijacks. A ma- oscillations [17,54]. It lacks mechanisms to prevent spoof- jor impediment to progress is the lack of ways to conduct ing [5,27] and prefix hijacks [24,32,58]. Despite known impactful interdomain research. Most research is based ei- problems, little has changed with interdomain routing, and ther on passive observation of existing routes, keeping re- there has been little impactful research in recent years. searchers from assessing how the Internet will respond to This stagnancy in the face of known problems is in stark route or policy changes; or simulations, which are restricted contrast to the rapid innovation in other areas of network- by limitations in our understanding of topology and policy. ing. We are in an era of remarkable changes in networking We propose a new class of interdomain research: re- and its role in our lives, as mobile connectivity and stream- searchers can instantiate an AS of their choice, including ing video change how we use the Internet, and advances in its intradomain topology and interdomain interconnectivity, software defined networking and data centers change how and connect it with the “live” Internet to exchange routes we run networks. -

Interconnection
Interconnection 101 As cloud usage takes off, data production grows exponentially, content pushes closer to the edge, and end users demand data and applications at all hours from all locations, the ability to connect with a wide variety of players becomes ever more important. This report introduces interconnection, its key players and busi- ness models, and trends that could affect interconnection going forward. KEY FINDINGS Network-dense, interconnection-oriented facilities are not easy to replicate and are typically able to charge higher prices for colocation, as well as charging for cross-connects and, in some cases, access to public Internet exchange platforms and cloud platforms. Competition is increasing, however, and competitors are starting the long process of creating network-dense sites. At the same time, these sites are valuable and are being acquired, so the sector is consolidating. Having facili- ties in multiple markets does seem to provide some competitive advantage, particularly if the facilities are similar in look and feel and customers can monitor them all from a single portal and have them on the same contract. Mobility, the Internet of Things, services such as SaaS and IaaS (cloud), and content delivery all depend on net- work performance. In many cases, a key way to improve network performance is to push content, processing and peering closer to the edge of the Internet. This is likely to drive demand for facilities in smaller markets that offer interconnection options. We also see these trends continuing to drive demand for interconnection facilities in the larger markets as well. © 2015 451 RESEARCH, LLC AND/OR ITS AFFILIATES. -
Cologix Torix Case Study
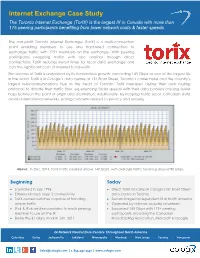
Internet Exchange Case Study The Toronto Internet Exchange (TorIX) is the largest IX in Canada with more than 175 peering participants benefiting from lower network costs & faster speeds The non-profit Toronto Internet Exchange (TorIX) is a multi-connection point enabling members to use one hardwired connection to exchange traffic with 175+ members on the exchange. With peering participants swapping traffic with one another through direct connections, TorIX reduces transit times for local data exchange and cuts the significant costs of Internet bandwidth. The success of TorIX is underlined by its tremendous growth, exceeding 145 Gbps as one of the largest IXs in the world. TorIX is in Cologix’s data centre at 151 Front Street, Toronto’s carrier hotel and the country’s largest telecommunications hub in the heart of Toronto. TorIX members define their own routing protocols to dictate their traffic flow, experiencing faster speeds with their data packets crossing fewer hops between the point of origin and destination. Additionally, by keeping traffic local, Canadian data avoids international networks, easing concerns related to privacy and security. Above: In Dec. 2014, TorIX traffic peaked above 140 Gbps, with average traffic hovering around 90 Gbps. Beginning Today Launched in July 1996 Direct TorIX on-ramp in Cologix’s151 Front Street Ethernet-based, layer 2 connectivity data centre in Toronto TorIX-owned switches capable of handling Second largest independent IX in North America ample traffic Operated by telecom industry volunteers IPv4 & IPv6 address provided to each peering Surpassed 145 Gbps with 175+ peering member to use on the IX participants, including the Canadian Broke the 61 Gbps mark in Jan. -

Peering Concepts and Definitions Terminology and Related Jargon
Peering Concepts and Definitions Terminology and Related Jargon Presentation Overview Brief On Peering Jargon Peering & Related Jargon BRIEF ON PEERING JARGON Brief On Peering Jargon A lot of terminologies used in the peering game. We shall look at the more common ones. Will be directly related to peering, as well as ancillary non-peering functions that support peering. PEERING & RELATED JARGON Peering & Related Jargon ASN (or AS - Autonomous System Number): . A unique number that identifies a collection/grouping of IP addresses or networks under the control of one entity on the Internet Bi-lateral (peering): . Peering relationships setup “directly” between two networks (see “Multi-lateral [peering]”). BGP (Border Gateway Protocol): . Routing protocol used on the Internet and at exchange points as the de-facto routing technique to share routing information (IPs and prefixes) between networks or between ASNs Peering & Related Jargon Carrier-neutral (data centre): . A facility where customers can purchase network services from “any” other networks within the facility. Cold-potato routing: . A situation where a network retains traffic on its network for as long as possible (see “Hot-potato routing”). Co-lo (co-location): . Typically a data centre where customers can house their network/service infrastructure. Peering & Related Jargon Dark fibre: . Fibre pairs offered by the owner, normally on a lease basis, without any equipment at each end of it to “activate” it (see “Lit fibre”). Data centre: . A purpose-built facility that provides space, power, cooling and network facilities to customers. Demarc (Demarcation): . Typically information about a co-lo customer, e.g., rack number, patch panel and port numbers, e.t.c. -

Peering Personals at TWNOG 4.0
Peering Personals at TWNOG 4.0 6 Dec. 2019 請注意, Peering Personal 場次將安排於下午時段的演講結束前進行, 請留意議程進行以 確保報告人當時在現場 Please note that Peering Personals will be done in the afternoon sessions so please check with Agenda and be on site. AS number 10133 (TPIX) and 17408 (Chief Telecom) Traffic profile Internet Exchange (Balanced) + ISP (Balanced) Traffic Volume TPIX: 160 Gbps ( https://www.tpix.net.tw/traffic.html ); Chief: 80 Gbps (2015- 10.7G; 2016- 25.9G; 2017- 58G; 2018- 96G) Peering Policy Open Peering Locations Taiwan: TPIX, Chief LY, Chief HD HK: HKIX, AMS-IX, EIE (HK1), Mega-i Europe: AMS-IX Message Biggest IX in Taiwan in both traffic and AS connected (59). Contact •[email protected] or •https://www.peeringdb.com/ix/823 •[email protected] or •https://www.peeringdb.com/net/8666 AS number 7527(JPIX) Traffic profile Internet Exchange (Balanced) Traffic Volume JPIX Tokyo 1.2T &JPIX Osaka 600G Peering Policy Open Peering Locations Tokyo: KDDI Otemachi, NTT Data Otemachi ,Comspace I, Equinix, Tokyo, AT Tokyo, COLT TDC1, NTT DATA Mitaka DC East, NTT COM Nexcenter DC, Meitetsucom DC (Nagoya),OCH DC (Okinawa), BBT New Otemachi DC Osaka: NTT Dojima Telepark, KDDI TELEHOUSE Osaka2, Equinix OS1,Meitetsucom DC (Nagoya), OBIS DC (Okayama) Site introduction: https://www.jpix.ad.jp/en/service_introduction.php Message Of connected ASN: Tokyo 211 Osaka 70 Remarks Our IX switch in Nagoya can offer both JPIX Tokyo vlan and Osaka one. Contact •[email protected] or [email protected] AS number 41095 Traffic profile 1:3 Balanced where content prevail Traffic Volume -

Mapping Peering Interconnections to a Facility
Mapping Peering Interconnections to a Facility Vasileios Giotsas Georgios Smaragdakis Bradley Huffaker CAIDA / UC San Diego MIT / TU Berlin CAIDA / UC San Diego [email protected] [email protected] bhuff[email protected] Matthew Luckie kc claffy University of Waikato CAIDA / UC San Diego [email protected] [email protected] ABSTRACT CCS Concepts Annotating Internet interconnections with robust phys- •Networks ! Network measurement; Physical topolo- ical coordinates at the level of a building facilitates net- gies; work management including interdomain troubleshoot- ing, but also has practical value for helping to locate Keywords points of attacks, congestion, or instability on the In- Interconnections; peering facilities; Internet mapping ternet. But, like most other aspects of Internet inter- connection, its geophysical locus is generally not pub- lic; the facility used for a given link must be inferred to 1. INTRODUCTION construct a macroscopic map of peering. We develop a Measuring and modeling the Internet topology at the methodology, called constrained facility search, to infer logical layer of network interconnection, i. e., autonomous the physical interconnection facility where an intercon- systems (AS) peering, has been an active area for nearly nection occurs among all possible candidates. We rely two decades. While AS-level mapping has been an im- on publicly available data about the presence of net- portant step to understanding the uncoordinated forma- works at different facilities, and execute traceroute mea- tion and resulting structure of the Internet, it abstracts surements from more than 8,500 available measurement a much richer Internet connectivity map. For example, servers scattered around the world to identify the tech- two networks may interconnect at multiple physical lo- nical approach used to establish an interconnection. -

PEERING PARTICIPANTS • Managedway Company • Merit Network Inc
DETROIT INTERNET EXCHANGE (DET-IX) 123NET PROVIDES ENTERPRISE DATA CENTER, NETWORK & VOICE SERVICES TO MICHIGAN BUSINESSES WHAT IS AN INTERNET EXCHANGE? The Detroit Internet Exchange (DET-IX) is a regional Internet Exchange Point (IXP) that was launched in 2015. The Internet exchange point (IXP) is where networks come together to peer or exchange traffic. While they allow network operators to exchange traffic with other network operators, an exchange point will not PEERING sell you a complete Internet connectivity. They are, instead, one of the building blocks around which the Internet is PARTICIPANTS built. When connecting to a major peering hub it greatly reduces traffic a provider must purchase from an upstream provider. The best part is that membership is free! • 123.net • A2 Hosting, Inc. WHO CONNECTS TO THEM? • ACD.net/ACD Telecom, Inc. Any network that wants to peer with other networks can connect to an exchange point. Traditionally, this meant Internet service providers (ISPs) but with the growing need for connections to alternative providers like content and • Acenet, Inc advertising, companies are connecting to exchanges. These companies are peering with ISPs to get their content to • Active Solutions Group their customer base. • Akamai Technologies • Amazon.com BENEFITS Bilateral Peering • Aptient Consulting Group Inc. Traffic exchanged directly between • Amplex Electric, Inc two members of the DET-IX over the • Clear Rate Communications, Inc shared exchange fabric. INTERNET CONTENT SERVICE PROVIDER PROVIDER • CloudFlare Multilateral Peering • Cloudsafe, Ltd. Traffic exchanged directly between • CMSInter.net, LLC members wishing to peer directly INTERNET CONTENT • D & P Communications with any carrier. SERVICE PROVIDER PROVIDER • Daystarr Communications Purchase Upstream • Everstream An added benefit of the exchange • Facebook is the ability to purchase upstream from the on-net carriers present in • Fastly, Inc. -

IPTP Networks 2 Contents
1 www.iptp.net IPTP Networks 2 Contents CONTENTS Our history ........................................................................ 4 About us ............................................................................... 6 Global partnership .............................................................. 10 1-Stop-IT-Shop .................................................................... 12 A-Z Infrastructure ................................................................13 Managed services ..............................................................14 Managed Security Services .................................................................................. 15 IPTP Pentest ........................................................................................................... 15 Global Network and Points of Presence Map ....................................................... 16 Managed Connectivity Services ............................................................................... 17 Internet Exchanges and peering facilities .................................................................. 19 Low Latency Routes Map ......................................................................................... 20 Map of Cable Systems ........................................................................................... 21 Data Centers ....................................................................... 24 Managed Datacenter Services ...................................................................................24 -

Peering Into the Comcast-Netflix Deal Daniel A
Boston College Law School Digital Commons @ Boston College Law School Boston College Law School Faculty Papers 3-5-2014 Peering into the Comcast-Netflix Deal Daniel A. Lyons Boston College Law School, [email protected] Follow this and additional works at: http://lawdigitalcommons.bc.edu/lsfp Part of the Antitrust and Trade Regulation Commons, Communications Law Commons, Consumer Protection Law Commons, Internet Law Commons, and the State and Local Government Law Commons Recommended Citation Daniel A. Lyons. "Peering into the Comcast-Netflix Deal." Perspectives from Free State Foundation Scholars 9, no.11 (2014). This Article is brought to you for free and open access by Digital Commons @ Boston College Law School. It has been accepted for inclusion in Boston College Law School Faculty Papers by an authorized administrator of Digital Commons @ Boston College Law School. For more information, please contact [email protected]. Perspectives from FSF Scholars March 5, 2014 Vol. 9, No. 11 Peering into the Comcast-Netflix Deal by Daniel A. Lyons * Introduction: The Internet of Bad Analogies Last week, the blogosphere was abuzz with the news that Netflix and Comcast had signed a “mutually beneficial interconnection agreement.”1 Although the companies did not disclose the terms of the deal, most assume that Netflix will pay to connect its servers directly to the Comcast network and stream content to Comcast customers more efficiently. Net neutrality proponents, already smarting from last month’s D.C. Circuit decision, quickly condemned the agreement as a revolutionary and ominous milestone: one called it “water in the basement for the Internet industry.”2 But when one strips away the rhetoric and engages in a more nuanced analysis than instant-punditry can provide, one sees much less cause for alarm. -

Internet Exchange Tour of the World
Internet Exchange tour of the World Version 2.0 Gaurab Raj Upadhaya NPIX / PCH / APNIC SIG-IX / APIX What is an Internet eXchange Point (IXP) ? • Internet eXchange Points (IXPs) are the most critical part of the Internet’s Infrastructure. It is the meeting point where ISPs interconnect with one another. With out IXPs, there would be no Internet. Interconnecting with other networks is the essence of the Internet. ISPs must interconnect with other networks to provide Internet services. • Private and Bi-Lateral Peering are considered to be a type of IXP. Background • The Internet is a decentralized network of autonomous commercial interests • Internet Service Providers (ISPs) operate by exchanging traffic at their borders, propagating data from its source to its destination • This exchange can be settlement-free (“Peering”) or paid (“Transit”) Why This is Important • If you have no domestic Internet exchange facility, your domestic ISPs must purchase transit from foreign ISPs • The large foreign ISPs who sell transit are American, Japanese, and British • This is an expensive and unnecessary exportation of capital to developed nations at the expense of your domestic Internet industry Second-Order Benefits of Domestic Exchange • A strong domestic Internet industry creates high-paying knowledge-worker jobs • Domestic traffic exchange reduces the importation of Foreign content and cultural values, in favor of domestic content authoring and publishing A Brief History of Internet Exchanges First Exchanges • Metropolitan Area Ethernet Washington, D.C. -

Rethinking Routing and Peering in the Era of Vertical Integration of Network Functions
University of Central Florida STARS Electronic Theses and Dissertations, 2004-2019 2019 Rethinking Routing and Peering in the era of Vertical Integration of Network Functions Prasun Kanti Dey University of Central Florida Part of the Computer Engineering Commons Find similar works at: https://stars.library.ucf.edu/etd University of Central Florida Libraries http://library.ucf.edu This Doctoral Dissertation (Open Access) is brought to you for free and open access by STARS. It has been accepted for inclusion in Electronic Theses and Dissertations, 2004-2019 by an authorized administrator of STARS. For more information, please contact [email protected]. STARS Citation Dey, Prasun Kanti, "Rethinking Routing and Peering in the era of Vertical Integration of Network Functions" (2019). Electronic Theses and Dissertations, 2004-2019. 6709. https://stars.library.ucf.edu/etd/6709 RETHINKING ROUTING AND PEERING IN THE ERA OF VERTICAL INTEGRATION OF NETWORK FUNCTIONS by PRASUN KANTI DEY M.S. University of Nevada Reno, 2016 A dissertation submitted in partial fulfilment of the requirements for the degree of Doctor of Philosophy in the Department of Electrical and Computer Engineering in the College of Engineering and Computer Science at the University of Central Florida Orlando, Florida Fall Term 2019 Major Professor: Murat Yuksel c 2019 Prasun Kanti Dey ii ABSTRACT Content providers typically control the digital content consumption services and are getting the most revenue by implementing an “all-you-can-eat” model via subscription or hyper-targeted ad- vertisements. Revamping the existing Internet architecture and design, a vertical integration where a content provider and access ISP will act as unibody in a sugarcane form seems to be the recent trend. -

INEX What Is an IXP?
1 What is an IXP? Beirut, March 2017 Nick Hilliard Chief Technical Officer Internet Neutral Exchange Association Company Limited by Guarantee 2 Just a Switching Platform 3 Switch 3 Switch Switch 3 Switch Switch Switch 4 80G clonshaugh ballycoolin 80G 80G 80G citywest 80G kilcarbery hume ave 30G 30G lavery ave 5 What is an IXP? IXPs - the IX-F Definition • An Internet Exchange Point (IXP) is a network facility that enables the interconnection and exchange of Internet traffic between more than two independent Autonomous Systems. • An IXP provides interconnection only for Autonomous Systems. • An IXP does not require the Internet traffic passing between any pair of participating Autonomous Systems to pass through any third Autonomous System, nor does it alter or otherwise interfere with such traffic. 6 What is an IXP? IXPs and IP connectivity • Generally speaking, three types of IP connectivity: • Private Network Interconnections (PI or PNI) • Internet eXchange Point (IXP) • Regular IP Transit (IPT) 6 What is an IXP? IXPs and IP connectivity • Generally speaking, three types of IP connectivity: • Private Network Interconnections (PI or PNI) • Internet eXchange Point (IXP) • Regular IP Transit (IPT) • “Quality” measured by: • latency • available bandwith • “control” - more recently we also consider mitigation against DDoS. 6 What is an IXP? IXPs and IP connectivity • Generally speaking, three types of IP connectivity: • Private Network Interconnections (PI or PNI) • Internet eXchange Point (IXP) • Regular IP Transit (IPT) Quality Improvement