A S -CR.-- ,Cn/OJ0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Micro-Circuits for High Energy Physics*
MICRO-CIRCUITS FOR HIGH ENERGY PHYSICS* Paul F. Kunz Stanford Linear Accelerator Center Stanford University, Stanford, California, U.S.A. ABSTRACT Microprogramming is an inherently elegant method for implementing many digital systems. It is a mixture of hardware and software techniques with the logic subsystems controlled by "instructions" stored Figure 1: Basic TTL Gate in a memory. In the past, designing microprogrammed systems was difficult, tedious, and expensive because the available components were capable of only limited number of functions. Today, however, large blocks of microprogrammed systems have been incorporated into a A input B input C output single I.e., thus microprogramming has become a simple, practical method. false false true false true true true false true true true false 1. INTRODUCTION 1.1 BRIEF HISTORY OF MICROCIRCUITS Figure 2: Truth Table for NAND Gate. The first question which arises when one talks about microcircuits is: What is a microcircuit? The answer is simple: a complete circuit within a single integrated-circuit (I.e.) package or chip. The next question one might ask is: What circuits are available? The answer to this question is also simple: it depends. It depends on the economics of the circuit for the semiconductor manufacturer, which depends on the technology he uses, which in turn changes as a function of time. Thus to understand Figure 3: Logical NOT Circuit. what microcircuits are available today and what makes them different from those of yesterday it is interesting to look into the economics of producing microcircuits. The basic element in a logic circuit is a gate, which is a circuit with a number of inputs and one output and it performs a basic logical function such as AND, OR, or NOT. -

Computer Architecture Out-Of-Order Execution
Computer Architecture Out-of-order Execution By Yoav Etsion With acknowledgement to Dan Tsafrir, Avi Mendelson, Lihu Rappoport, and Adi Yoaz 1 Computer Architecture 2013– Out-of-Order Execution The need for speed: Superscalar • Remember our goal: minimize CPU Time CPU Time = duration of clock cycle × CPI × IC • So far we have learned that in order to Minimize clock cycle ⇒ add more pipe stages Minimize CPI ⇒ utilize pipeline Minimize IC ⇒ change/improve the architecture • Why not make the pipeline deeper and deeper? Beyond some point, adding more pipe stages doesn’t help, because Control/data hazards increase, and become costlier • (Recall that in a pipelined CPU, CPI=1 only w/o hazards) • So what can we do next? Reduce the CPI by utilizing ILP (instruction level parallelism) We will need to duplicate HW for this purpose… 2 Computer Architecture 2013– Out-of-Order Execution A simple superscalar CPU • Duplicates the pipeline to accommodate ILP (IPC > 1) ILP=instruction-level parallelism • Note that duplicating HW in just one pipe stage doesn’t help e.g., when having 2 ALUs, the bottleneck moves to other stages IF ID EXE MEM WB • Conclusion: Getting IPC > 1 requires to fetch/decode/exe/retire >1 instruction per clock: IF ID EXE MEM WB 3 Computer Architecture 2013– Out-of-Order Execution Example: Pentium Processor • Pentium fetches & decodes 2 instructions per cycle • Before register file read, decide on pairing Can the two instructions be executed in parallel? (yes/no) u-pipe IF ID v-pipe • Pairing decision is based… On data -

Parallel Computing
Lecture 1: Computer Organization 1 Outline • Overview of parallel computing • Overview of computer organization – Intel 8086 architecture • Implicit parallelism • von Neumann bottleneck • Cache memory – Writing cache-friendly code 2 Why parallel computing • Solving an × linear system Ax=b by using Gaussian elimination takes ≈ flops. 1 • On Core i7 975 @ 4.0 GHz,3 which is capable of about 3 60-70 Gigaflops flops time 1000 3.3×108 0.006 seconds 1000000 3.3×1017 57.9 days 3 What is parallel computing? • Serial computing • Parallel computing https://computing.llnl.gov/tutorials/parallel_comp 4 Milestones in Computer Architecture • Analytic engine (mechanical device), 1833 – Forerunner of modern digital computer, Charles Babbage (1792-1871) at University of Cambridge • Electronic Numerical Integrator and Computer (ENIAC), 1946 – Presper Eckert and John Mauchly at the University of Pennsylvania – The first, completely electronic, operational, general-purpose analytical calculator. 30 tons, 72 square meters, 200KW. – Read in 120 cards per minute, Addition took 200µs, Division took 6 ms. • IAS machine, 1952 – John von Neumann at Princeton’s Institute of Advanced Studies (IAS) – Program could be represented in digit form in the computer memory, along with data. Arithmetic could be implemented using binary numbers – Most current machines use this design • Transistors was invented at Bell Labs in 1948 by J. Bardeen, W. Brattain and W. Shockley. • PDP-1, 1960, DEC – First minicomputer (transistorized computer) • PDP-8, 1965, DEC – A single bus -

Programmable Digital Microcircuits - a Survey with Examples of Use
- 237 - PROGRAMMABLE DIGITAL MICROCIRCUITS - A SURVEY WITH EXAMPLES OF USE C. Verkerk CERN, Geneva, Switzerland 1. Introduction For most readers the title of these lecture notes will evoke microprocessors. The fixed instruction set microprocessors are however not the only programmable digital mi• crocircuits and, although a number of pages will be dedicated to them, the aim of these notes is also to draw attention to other useful microcircuits. A complete survey of programmable circuits would fill several books and a selection had therefore to be made. The choice has rather been to treat a variety of devices than to give an in- depth treatment of a particular circuit. The selected devices have all found useful ap• plications in high-energy physics, or hold promise for future use. The microprocessor is very young : just over eleven years. An advertisement, an• nouncing a new era of integrated electronics, and which appeared in the November 15, 1971 issue of Electronics News, is generally considered its birth-certificate. The adver• tisement was for the Intel 4004 and its three support chips. The history leading to this announcement merits to be recalled. Intel, then a very young company, was working on the design of a chip-set for a high-performance calculator, for and in collaboration with a Japanese firm, Busicom. One of the Intel engineers found the Busicom design of 9 different chips too complicated and tried to find a more general and programmable solu• tion. His design, the 4004 microprocessor, was finally adapted by Busicom, and after further négociation, Intel acquired marketing rights for its new invention. -
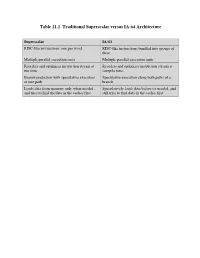
Table 21.1 Traditional Superscalar Versus IA-64 Architecture
Table 21.1 Traditional Superscalar versus IA-64 Architecture Superscalar IA-64 RISC-like instructions, one per word RISC-like instructions bundled into groups of three Multiple parallel execution units Multiple parallel execution units Reorders and optimizes instruction stream at Reorders and optimizes instruction stream at run time compile time Branch prediction with speculative execution Speculative execution along both paths of a of one path branch Loads data from memory only when needed, Speculatively loads data before its needed, and and tries to find the data in the caches first still tries to find data in the caches first Table 21.2 Relationship Between Instruction Type and Execution Unit Type Instruction Type Description Execution Unit Type A Integer ALU I-unit or M-unit I Non-ALU integer I-unit M Memory M-unit F Floating-point F-unit B Branch B-unit X Extended I-unit/B-unit Table 21.3 Template Field Encoding and Instruction Set Mapping Template Slot 0 Slot 1 Slot 2 00 M-unit I-unit I-unit 01 M-unit I-unit I-unit 02 M-unit I-unit I-unit 03 M-unit I-unit I-unit 04 M-unit L-unit X-unit 05 M-unit L-unit X-unit 08 M-unit M-unit I-unit 09 M-unit M-unit I-unit 0A M-unit M-unit I-unit 0B M-unit M-unit I-unit 0C M-unit F-unit I-unit 0D M-unit F-unit I-unit 0E M-unit M-unit F-unit 0F M-unit M-unit F-unit 10 M-unit I-unit B-unit 11 M-unit I-unit B-unit 12 M-unit B-unit B-unit 13 M-unit B-unit B-unit 16 B-unit B-unit B-unit 17 B-unit B-unit B-unit 18 M-unit M-unit B-unit 19 M-unit M-unit B-unit 1C M-unit F-unit B-unit 1D M-unit F-unit B-unit Table 21.5 IA-64 Application Registers Kernel registers (KR0-7) Convey information from the operating system to the application. -

V850E2S User's Manual: Architecture
User’s Manual User’s V850E2S 32 User’s Manual: Architecture RENESAS MCU V850E2S Microprocessor Core All information contained in these materials, including products and product specifications, represents information on the product at the time of publication and is subject to change by Renesas Electronics Corp. without notice. Please review the latest information published by Renesas Electronics Corp. through various means, including the Renesas Electronics Corp. website (http://www.renesas.com). www.renesas.com Rev.1.00 May, 2014 Notice 1. Descriptions of circuits, software and other related information in this document are provided only to illustrate the operation of semiconductor products and application examples. You are fully responsible for the incorporation of these circuits, software, and information in the design of your equipment. Renesas Electronics assumes no responsibility for any losses incurred by you or third parties arising from the use of these circuits, software, or information. 2. Renesas Electronics has used reasonable care in preparing the information included in this document, but Renesas Electronics does not warrant that such information is error free. Renesas Electronics assumes no liability whatsoever for any damages incurred by you resulting from errors in or omissions from the information included herein. 3. Renesas Electronics does not assume any liability for infringement of patents, copyrights, or other intellectual property rights of third parties by or arising from the use of Renesas Electronics products or technical information described in this document. No license, express, implied or otherwise, is granted hereby under any patents, copyrights or other intellectual property rights of Renesas Electronics or others. 4. -

(12) Patent Application Publication (10) Pub. No.: US 2015/0067389 A1 Galloway (43) Pub
US 2015 OO67389A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/0067389 A1 Galloway (43) Pub. Date: Mar. 5, 2015 (54) PROGRAMMABLE SUBSTITUTIONS FOR (52) U.S. Cl. MCROCODE CPC .......... G06F 1 1/1405 (2013.01); G06F 9/3016 (2013.01) (71) Applicant: ADVANCED MICRO DEVICES, USPC ............................................................ 71.4/10 INC., Sunnyvale, CA (US) (72) Inventor: Frank C. Galloway, Dripping Springs, TX (US) (57) ABSTRACT (73) Assignee: ADVANCED MICRO DEVICES, INC., Sunnyvale, CA (US) The apparatuses, systems, and methods in accordance with the embodiments disclosed herein may facilitate modifying (21) Appl. No.: 14/014,220 post silicon instruction behavior. Embodiments herein may provide registers in predetermined locations in an integrated (22) Filed: Aug. 29, 2013 circuit. These registers may be mapped to generic instruc Publication Classification tions, which can modify an operation of the integrated circuit. In some embodiments, these registers may be used to imple (51) Int. C. ment a patch routine to change the behavior of at least a G06F II/4 (2006.01) portion of the integrated circuit. In this manner, the original G06F 9/30 (2006.01) design of the integrated circuit may be altered. Peera Revices Processor Central Processing init (CPU) agrarirrate Comute act Output. {-n}init(s) Dynamic Randon evices) 165 Access Merroy 142 (DRAM) i 2 t South Eridge pi (evices) f Graphics Processing Unit (GP or Floating Point (Graphics Processor) B (EPU) 8 as 8 : Programmate -: agrariate Scrage Storage Paic nit as it 1 65 Patent Application Publication Mar. 5, 2015 Sheet 1 of 7 US 2015/0067389 A1 §6% Patent Application Publication Mar. -

Database Integration
I DATABASE INTEGRATION ALPHA SERVERS & WORKSTATIONS Digital ALPHA 21164 CPU Technical Journal Editorial The Digital TechnicalJournal is a refereed Cyrix is a trademark of Cyrix Corporation. Jane C. Blake, Managing Editor journal published quarterly by Digital dBASE is a trademark and Paradox is Helen L. Patterson, Editor Equipment Corporation, 30 Porter Road a registered trademark of Borland Kathleen M. Stetson, Editor LJ02/D10, Littleton, Massachusetts 01460. International, Inc. Subscriptionsto the Journal are $40.00 Circulation (non-U.S. $60) for four issues and $75.00 EDA/SQL is a trademark of Information Catherine M. Phillips, Administrator (non-U.S. $115) for eight issues and must Builders, Inc. Dorothea B. Cassady, Secretary be prepaid in U.S. funds. University and Encina is a registered trademark of Transarc college professors and Ph.D. students in Corporation. Production the electrical engineering and computer Excel and Microsoft are registered pde- Terri Autieri, Production Editor science fields receive complimentary sub- marks and Windows and Windows NT are Anne S. Katzeff, Typographer scriptions upon request. Orders, inquiries, trademarks of Microsoft Corporation. Joanne Murphy, Typographer and address changes should be sent to the Peter R Woodbury, Illustrator Digital TechnicalJournal at the published- Hewlett-Packard and HP-UX are registered by address. Inquiries can also be sent elec- trademarks of Hewlett-Packard Company. Advisory Board tronically to [email protected]. Single copies INGRES is a registered trademark of Ingres Samuel H. Fuller, Chairman and back issues are available for $16.00 each Corporation. Richard W. Beane by calling DECdirect at 1-800-DIGITAL Donald Z. Harbert (1-800-344-4825). -

8086 CPU ARCHITECTURE the Microprocessors Functions As The
8086 CPU ARCHITECTURE The microprocessors functions as the CPU in the stored program model of the digital computer. Its job is to generate all system timing signals and synchronize the transfer of data between memory, I/O, and itself. It accomplishes this task via the three-bus system architecture previously discussed. The microprocessor also has a S/W function. It must recognize, decode, and execute program instructions fetched from the memory unit. This requires an Arithmetic-Logic Unit (ALU) within the CPU to perform arithmetic and logical (AND, OR, NOT, compare, etc) functions. The 8086 CPU is organized as two separate processors (or units), called the Bus Interface Unit (BIU) and the Execution Unit (EU). The BIU provides H/W functions, including generation of the memory and I/O addresses for the transfer of data between the outside world -outside the CPU, that is- and the EU. The EU receives program instruction codes and data from the BIU, executes these instructions, and store the results in the general registers. By passing the data back to the BIU, data can also be stored in a memory location or written to an output device. Note that the EU has no connection to the system buses. It receives and outputs all its data thru the BIU. The basic architecture of 8086 is shown below. The only difference between an 8088 microprocessor and an 8086 microprocessor is the BIU. In the 8088, the BIU data bus path is 8 bits wide versus the 8086's 16-bit data bus. Another difference is that the 8088 instruction queue is four bytes long instead of six bytes in 8086. -

Effective Compilation Support for Variable Instruction Set Architecture
Effective Compilation Support for Variable Instruction Set Architecture Jack Liu, Timothy Kong, Fred Chow Cognigine Corporation 6120 Stevenson Blvd. Fremont, CA 94538, USA g fjackl,timk,fredc @cognigine.com Abstract running embedded applications. these application specific instruction set processors (ASIPs) [1, 2] use instruction sets customized towards a specific type of application so they Traditional compilers perform their code generation can deliver efficient run-time performance for typical pro- tasks based on a fixed, pre-determined instruction set. This grams written for that application area. Because the instruc- paper describes the implementation of a compiler that de- tion set is pre-determined, the compiler is built and config- termines the best instruction set to use for a given pro- ured to generate code based on a custom, fixed instruction gram and generates efficient code sequence based on it. We set [16]. first give an overview of the VISC Architecture pioneered at Cognigine that exemplifies a Variable Instruction Set Ar- The Variable Instruction Set Communications Architec- chitecture. We then present three compilation techniques ture (VISC Architecture ÌÅ ) from Cognigine represents a that, when combined, enable us to provide effective com- very different approach in the attempt to provide greater pilation and optimization support for such an architecture. configurability in compiling embedded software. The VISC The first technique involves the use of an abstract opera- Architecture can perform a complex set of instructions con- tion representation that enables the code generator to op- sisting of multiple, fine and coarse grain operations that op- timize towards the core architecture of the processor with- erate on multiple operands at the same time in one fixed out committing to any specific instruction format. -

Intel 8086 MICROPROCESSOR ARCHITECTURE
Intel 8086 MICROPROCESSOR ARCHITECTURE 1 Features • It is a 16-bit μp. • 8086 has a 20 bit address bus can access up to 220 memory locations (1 MB). • It can support up to 64K I/O ports. • It provides 14, 16 -bit registers. • Word size is 16 bits and double word size is 4 bytes. • It has multiplexed address and data bus AD0- AD15 and A16 – A19. 2 • 8086 is designed to operate in two modes, Minimum and Maximum. • It can prefetches up to 6 instruction bytes from memory and queues them in order to speed up instruction execution. • It requires +5V power supply. • A 40 pin dual in line package. • Address ranges from 00000H to FFFFFH 3 Intel 8086 Internal Architecture 4 Internal architecture of 8086 • 8086 has two blocks BIU and EU. • The BIU handles all transactions of data and addresses on the buses for EU. • The BIU performs all bus operations such as instruction fetching, reading and writing operands for memory and calculating the addresses of the memory operands. The instruction bytes are transferred to the instruction queue. • EU executes instructions from the instruction system byte queue. 5 • BIU contains Instruction queue, Segment registers, Instruction pointer, Address adder. • EU contains Control circuitry, Instruction decoder, ALU, Pointer and Index register, Flag register. 6 EXECUTION UNIT • Decodes instructions fetched by the BIU • Generate control signals, • Executes instructions. The main parts are: • Control Circuitry • Instruction decoder • ALU 7 EXECUTION UNIT – General Purpose Registers 16 bits 8 bits 8 bits AH AL AX Accumulator BH BL BX Base CH CL CX Count DH DL DX Data SP Stack Pointer Pointer BP Base Pointer SI Source Index Index DI Destination Index 8 EXECUTION UNIT – General Purpose Registers Register Purpose AX Word multiply, word divide, word I /O AL Byte multiply, byte divide, byte I/O, decimal arithmetic AH Byte multiply, byte divide BX Store address information CX String operation, loops CL Variable shift and rotate DX Word multiply, word divide, indirect I/O (Used to hold I/O address during I/O instructions. -

UNIT-I - OVERVIEW of EMBEDDED SYSTEMS Embedded System
UNIT-I - OVERVIEW OF EMBEDDED SYSTEMS Embedded System . An embedded system can be thought of as a computer hardware system having software embedded in it. An embedded system can be an independent system or it can be a part of a large system. An embedded system is a microcontroller or microprocessor based system which is designed to perform a specific task. For example, a fire alarm is an embedded system; it will sense only smoke. An embedded system has three components − It has hardware. It has application software. It has Real Time Operating system (RTOS) that supervises the application software and provide mechanism to let the processor run a process as per scheduling by following a plan to control the latencies. RTOS defines the way the system works. It sets the rules during the execution of application program. A small scale embedded system may not have RTOS. So we can define an embedded system as a Microcontroller based, software driven, reliable, real-time control system. Characteristics of an Embedded System Single-functioned − An embedded system usually performs a specialized operation and does the same repeatedly. For example: A pager always functions as a pager. Tightly constrained − All computing systems have constraints on design metrics, but those on an embedded system can be especially tight. Design metrics is a measure of an implementation's features such as its cost, size, power, and performance. It must be of a size to fit on a single chip, must perform fast enough to process data in real time and consume minimum power to extend battery life.