Classification of Coordination and Awareness Mechanisms in Collaboration Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Koblenz-Trier
Quelle: DeutscheQuelle:Quelle: Bahn DeutscheDB AG/ Netz Oliver Bahn AG Lang AG Vorserienprojekt Digitales Stellwerk Koblenz-Trier Impressum Redaktion Kommunikation der Digitale Leit- und Sicherungstechnik Kontakt per Mail an: [email protected] oder auf DB Planet: http://t1p.de/DLST Vorserienprojekt Digitales Stellwerk Koblenz-Trier Digitale Leit- und Sicherungstechnik In vier Phasen zum Flächenrollout Die DB Netz AG betreibt aktuell über 2.600 Stellwerke Um eine neue Technologie auszurollen, muss diese diverser Bauarten und Generationen. Dies stellt eine entwickelt, erprobt und zugelassen werden. Im Fall der große Herausforderung für die heutige und künftige Digitalen Leit- und Sicherungstechnik wurde der Weg Leit- und Sicherungstechnik der DB Netz AG dar. zum Flächenrollout in vier Phasen eingeteilt. Herstellerspezifische Technik, unterschiedliche Schnitt- In Referenzimplementierungen sind bereits unter- stellen und individuelle Einzellösungen bedeuten einen schiedliche und standardisierte Schnittstellen in Betrieb höheren Aufwand für die Instandhaltung der Anlagen gegangen. Nachdem die einzelnen Komponenten die sowie höhere Kosten in der Ersatzteilbeschaffung. Referenzimplementierungen absolviert haben, erfolgt Schritt für Schritt soll die Digitale Leit- und Siche- der Einsatz der gesamten DLST im Rahmen der rungstechnik (DLST) die teilweise über 100 Jahre alte Vorserie. Folgende Projekte sind Teil der Vorserie: Infrastruktur modernisieren. Damit wird die Infrastruktur • Warnemünde wesentlich wirtschaftlicher und wettbewerbsfähiger. Außerdem wird eine deutlich höhere Verfügbarkeit für • Meitingen-Mertingen den Bahnbetrieb erreicht. • Harz-Weser-Netz • Koblenz-Trier Digitale Stellwerke (DSTW) In der darauffolgenden Phase, den Industrialisie- Diese Bauform ist ein wichtiger Baustein für die Bahn rungsprojekten sowie dem Starterpaket, werden u.a. der Zukunft. Bei der neuen Stellwerksgeneration wird Planungsgrundlagen erprobt und in das Regelwerk eine maßgeblich durch die DB Netz AG konzipierte, überführt. -
Studying in Germany a Good Choice for Your Child 15 Questions And
Studying in Germany A Good Choice for Your Child 15 Questions and Answers for Parents AnzElternFlyer_105x210_HD_Aula_02_1_en_vek_rz.indd 1 26.01.2010 17:36:27 Uhr Studying in Germany A Good Choice for Your Child 15 Questions and Answers for Parents 2nd Edition Who are we? The German Academic Exchange Service (DAAD) is a joint organisation of German institutions of higher education and student bodies. Our task is to support academic cooperation around the world, especially by promoting the exchange of students and academics. You can find more information about studying and living in Germany in our info brochures, at www.daad.de and on our DAAD branch office and information centre websites. Studying in Germany 3 Dear Parents, We are happy that you and your child are considering Germany as a place to study abroad. Studying in a foreign country is a big challenge. As a mother myself, I am very aware of the concerns parents have about their children’s well-being and professional future. You’re probably a little nervous about how your child will fare in a foreign country. And you may have many questions that still need answering. This brochure should help you find those answers. Germany is a great place to study and has much to offer your child. German universities have an excellent reputation around the world – a reputation that has endured for hundreds of years. This might explain why Germany is one of the most popular destinations for international students. There are more than 260,000 young people from around the world who study and research in Germany today. -

Amtsübergabe Der Vizepräsidenten Feierliche Amtsübergabe Der Vizepräsidenten Am Campus Koblenz
... auf den Punkt gebracht Themen: ZFUW unter neuer Leitung Absolventin der BioGeoWissenschaften auf Erfolgskurs und viele weitere Ausgabe 01 | 2013 Amtsübergabe der Vizepräsidenten Feierliche Amtsübergabe der Vizepräsidenten am Campus Koblenz Prof. Dr. J. Felix Hampe hat am Koblenzer Campus offiziell das Amt des terhin zur Verfügung. Dieses Amt ist im Vizepräsidenten übernommen. Die feierliche Übergabe war gleichzeitig Zuge der Umstrukturierung der Univer- Anlass, um seinen Vorgänger Prof. Dr. Peter Ullrich zu verabschieden, sitätsleitung aufgrund der besonderen der die Universität in vielerlei Hinsicht geprägt hat. Bedeutung der Lehrerbildung neu einge- richtet worden. Sein Amtskollege Prof. Dr. Ulrich Sarci- Laudatio Ullrichs Engagement, seinen Die Neustrukturierung der Leitungsebe- nelli, Vizepräsident am Campus Landau, Weitblick und seinen Willen zum ergeb- ne sei vor dem Hintergrund deutlich ver- bildete in seiner launigen Begrüßungs- nisorientierten Handeln. änderter Rahmenbedingungen erfolgt: rede drei sogenannte Westentaschenthe- Schon früh habe Ullrich auf die Notwen- Hochschulen bewegen sich immer stärker orien, die für Ullrichs Wirkungsmacht digkeit einer mittel- und langfristigen in Richtung Wettbewerb, so Heiligenthal. erklärungskräftig sein könnten: Anpassung des Studienangebots hinge- Es könnten nur die Hochschulen inter- 1. Die Zahlentheorie: Damit waren nicht wiesen. Unter seiner Verantwortung sei- national und national wettbewerbsfähig Arithmetik, diophantische Gleichungen en neue Studienangebote wie der Mas- sein, die ihre Organisationsstrukturen oder diskreter Logarithmus gemeint. Nein, terstudiengang „Ceramic Science and und -prozesse auf diese Herausforderung Ullrich galt im Präsidialkollegium als Engineering“ oder das berufliche Fach ausrichten. „Deshalb ist mit dem neuen ‚Herr der Zahlen’. Da sich der Rest der „Pflege“ für das Lehramt an Berufsbil- Vizepräsidenten am Campus Koblenz wissenschaftlichen Hochschulleitung bis- denden Schulen eingerichtet worden. -

Auswandererdatei Des Stadtarchivs Koblenz
Auswandererdatei des Stadtarchivs Koblenz (Stand: 11.11.2019) Anzahl der verzeichneten Auswanderer: 1765 Anzahl der verzeichneten Rückwanderer: 70, davon 10 unsicher Benutzte Akten des Landeshauptarchivs Koblenz (LHA Ko): Best. 403 (Oberpräsidium): Nr. 11191, 11219, 11242, 11243. Best. 441 (Regierung Koblenz): Nr. 5084, 5085, 17825, 23182, 23294, 23397, 23488, 23679, 23837, 23839, 23865, 23943, 24412, 24665. Best. 655,18 (Koblenz-Land): Nr. 276-279, 908, 1065, 1090, 1100, 1106-1108, 1333, 1417. Best. 655,71 (Bürgermeisterei Bassenheim): Nr. 21. Best. 655,69 (Bürgermeisterei St. Sebastian): Nr. 325, 326. Best. 700,77 (Nachlass van Ham): Nr. 9. Noch nicht benutzte Akten des LHA Ko: Best. 441 (Regierung Koblenz): Nr. 11242-11245: Verfahren gegen vormalige Deutsche bzw. sich hier aufhaltende Ausländer wegen deren Heranziehung zur Militärpflicht und eventueller Ausweisung, 1871-1913, Nr. 11219-11220: Verfahren gegen vormalige Deutsche und sich hier aufhaltende Ausländer hinsichtlich der Erfüllung ihrer Militärpflicht, 1846-1910; Nr. 11191: Verfahren gegen ausgetretene Militärpflichtige sowie gegen ausgewanderte Personen des Beurlaubtenstandes, 1829-1901. Benutzte Akten des Stadtarchivs Koblenz (StAK): Best. 623 (Stadt Koblenz): Nr. 1237, 1332, 1511, 1563, 1573, 1585, 2006, 2176, 2581, 4138, 4268, 4488, 4489, 4490, 4491, 4492, 4493, 6493, 6610, 6118, 7067. Best. 655,10 (Bürgermeisterei Ehrenbreitstein): Nr. 22, 538, 539, 540, 541, 542, 543, 550, 646, 789. Benutzte Websites: www.castlegarden.org (kostenpflichtig) www.familysearch.org www.immigrantships.net https://www.libertyellisfoundation.org/ 2 Abkürzungen : AB: Amtsblatt der Kgl. Regierung zu Koblenz CA: Coblenzer Anzeiger CT: Coblenzer Tageblatt CVZ: Coblenzer Volks-Zeitung CZ: Coblenzer Zeitung HStAD: Hauptstaatsarchiv Düsseldorf KGA: Coblenzer General-Anzeiger LHA Ko: Landeshauptarchiv Koblenz ÖA: Öffentlicher Anzeiger zum Amtsblatte der Kgl. -

Die Grössten Arbeitgeber in Rheinland-Pfalz 2019 Betriebe Ab 500 Beschäftigte
DIE GRÖSSTEN ARBEITGEBER IN RHEINLAND-PFALZ 2019 BETRIEBE AB 500 BESCHÄFTIGTE . Vorwort Die vorliegende Übersicht „Die größten Arbeitgeber in Rheinland-Pfalz 2019” stellt beschäftigungs - starke Unternehmen aus Industrie, Handel und Dienstleistung vor und gibt diesen die Möglichkeit, ihre wirtschaftliche Bedeutung in der Öffentlichkeit zu präsentieren. Die 137 Unternehmen beschäftigen zwischen 500 und 35.000 Personen – in der Summe sind es rund 221.000 Arbeitsplätze. In den Betrieben arbeiten demzufolge rund 16 Prozent der landesweit rund 1,4 Mio. sozialversicherungspflichtig Beschäftigten. Darüber hinaus tragen diese großen Unter - nehmen wesentlich zur Wertschöpfung und auch mittelbar zum wirtschaftlichen Wohlstand der Region bei, indem sie Arbeitsplätze bei Lieferanten und Dienstleistern sichern. Die Industrie hat mit 83 Unternehmen einen bedeutenden Anteil an den größten Arbeitgebern in Rheinland-Pfalz. Hohe Beschäftigtenzahlen finden sich vor allem bei den Automobilzulieferern, dem Maschinen- und Fahrzeugbau sowie den Herstellern von Chemie-, Kunststoff- und Pharmaprodukten. Im Handel finden sich größere Arbeitgeber vor allem im Lebensmittelhandel, Bau- und Heimwerker - bedarf sowie Möbelhandel. Im Dienstleistungsbereich sind größere Belegschaften insbesondere im Gesundheitswesen, bei Kreditinstituten und Finanzdienstleistern anzutreffen. Befragt wurden IHK-Mitgliedsunternehmen ab 500 Mitarbeiter, die entweder ihren Hauptsitz, eine Zweigniederlassung oder eine große Einzelbetriebsstätte in Rheinland-Pfalz unterhalten. Die Angaben zu den Beschäftigtenzahlen (Vollzeit und Teilzeit) wurden von den meisten Unternehmen zum 1. März 2019 erhoben und sind für Rheinland-Pfalz, Deutschland und die gesamte Welt kumuliert. Nicht erfasst wurden Mini-Jobber, Aushilfen und andere Formen geringfügiger Beschäftigung. Die Liste wird alle drei Jahre aktualisiert. Die Übersicht beruht auf den freiwilligen Angaben der Unternehmen und erhebt keinen Anspruch auf Vollständigkeit. Die Auflistung wurde aus öffentlich zugänglichen Quellen ergänzt. -

Aleris Koblenz: from Complex Scheduling to Simple Automation
Dassault Systemes in 2014 and is now Quintiq was acquired by DELMIA Quintiq Case study Aleris Koblenz: From complex scheduling to simple automation ALERIS KOBLENZ ALERIS KOBLENZ: FROM COMPLEX SCHEDULING TO SIMPLE AUTOMATION ALERIS KOBLENZ | CASE STUDY “Our ability to react has significantly improved through the implementation of this collaborative scheduling solution – our people can work much more effectively.” – Gerd Refflinghaus Manager of Production Planning and Logistics Aleris Aluminium Walzprodukte GmbH is part of the Aleris Aluminium Rolled Products group, one of the largest producers of rolled and extruded aluminium products worldwide. Based in Koblenz, Germany, Aleris produces approximately 150,000 tons per year of rolled aluminium products in the form of coils, sheets and plates. End-use applications of the products include aircraft, heat exchangers, moldings and tools, shipbuilding and commercial vehicles. SUPPLY CHAIN PLANNING & OPTIMIZATION 2 ALERIS KOBLENZ: FROM COMPLEX SCHEDULING TO SIMPLE AUTOMATION ALERIS KOBLENZ | CASE STUDY The Koblenz Challenges The solution production process The production process at Koblenz includes multiple alloy As such, the Koblenz process was not without challenges. Quintiq and 4Production were asked to provide an casting stations, homogenization and preheating ovens From scheduling their operations for casting to hot- advanced scheduling tool that could help Koblenz create combined with scalping, brazing and hot rolling operations, problems included: better quality schedules and address the problems they rolling operations. faced. The approach was to implement a collaborative 1. The so-called “Domino-Effect,” where unexpected scheduling model that coupled the schedules of the Within this process are a large number of operational plant events at one resource adversely impacted individual resources to effectively act as one “single” constraints, for example, alloy and size restrictions, following production steps resource. -

THE GREAT JOURNEY Through EUROPE CRUISING the RHINE RIVER and FEATURING the GLACIER EXPRESS
distinctive travel for more than 35 years THE GREAT JOURNEY through EUROPE CRUISING the RHINE RIVER and FEATURING the GLACIER EXPRESS THE NETHERLANDS UNESCO North Sea World Heritage Site Amsterdam Cruise Itinerary R hi ne Land Routing R i v GERMANY Train Routing er Cologne Air Routing Koblenz Rüdesheim Rhine Rheingau FRANCE Valley Mannheim Heidelberg Strasbourg SWITZERLAND Basel Berne Zurich Lucerne Tasch Andermatt Zermatt Matterhorn ITALY Glacier Express Itinerary* This extraordinary 11-day “Grand Tour” of Europe Lucerne u Zermatt u Basel features an incredible combination of river, rail, lake and Strasbourg u Koblenz u Cologne mountain travel including five nights aboard the deluxe July 18 to 28, 2020 AMADEUS SILVER III. Journey through the western heart of the Continent through Switzerland, France, Germany and Day the Netherlands, cruising the fabled Rhine River. Specially 1 Depart the U.S. arranged guided excursions feature five great UNESCO 2 Zurich, Switzerland/Lucerne World Heritage sites—see the Jungfrau-Aletsch region of the Swiss Alps, walk through Berne’s Old Town, tour the Alsatian 3 Lucerne for Mount Pilatus city of Strasbourg, cruise through the Rhine River Valley, 4 Lucerne/Andermatt for Glacier Express to Zermatt and see Cologne’s Gothic cathedral. Also visit Germany’s 5 Zermatt for Matterhorn medieval Rüdesheim and 13th-century Heidelberg Castle. 6 Zermatt/Berne/Basel/ Spend two nights each in Lucerne and Zermatt, Switzerland; Embark Amadeus Silver III ride aboard three legendary railways—the Pilatus Railway; the world’s steepest cogwheel railway, the Gornergrat Bahn 7 Strasbourg, France for breathtaking views of the Matterhorn, and the Glacier 8 Mannheim, Germany, for Heidelberg Express from Andermatt to Zermatt—and enjoy a scenic 9 Rüdesheim/Koblenz cruise on Lake Lucerne. -

EGU2015-14379-3, 2015 EGU General Assembly 2015 © Author(S) 2015
Geophysical Research Abstracts Vol. 17, EGU2015-14379-3, 2015 EGU General Assembly 2015 © Author(s) 2015. CC Attribution 3.0 License. Floodplain mesocosm system for studying environmental fate and effects of engineered nanoparticles Gabriele E. Schaumann (1), Zacharias Steinmetz (1), George Metreveli (1), Hans-Jörg Vogel (2,3), Mirco Bundschuh (4,5), Thomas Baumann (6), Ralf Schulz (4), Friederike Lang (7), Frank Seitz (4), Ricki R. Rosenfeldt (4), and Werner Manz (8) (1) University Koblenz-Landau, Institute for Environmental Sciences, Group of Environmental and Soil Chemistry, Landau, Germany ([email protected]), (2) Department of Soil Physics, Helmholtz Centre for Environmental Research – UFZ, Theodor-Lieser-Strasse 4, D-06120 Halle, Germany, (3) Institute of Soil Science and Plant Nutrition, Martin-Luther-University Halle-Wittenberg, Von-Seckendorff-Platz 3, D-06120 Halle/Saale, Germany, (4) University Koblenz-Landau, Institute for Environmental Sciences, Group of Ecotoxicology and Environment, Landau, Germany, (5) Department of Aquatic Sciences and Assessment, Swedish University of Agricultural Sciences, Lennart Hjelms väg 9, SE-75007 Uppsala, Sweden, (6) Institute of Hydrochemistry, Technische Universität München, Marchioninistr. 17, D-81377 Munich, Germany, (7) Institute of Forest Sciences, Chair of Soil Ecology, Albert-Ludwigs-Universität Freiburg, D-79085 Freiburg i.Br., Germany, (8) Institute for Integrated Natural Sciences, Department of Biology, Universität Koblenz-Landau, Universitätsstr. 1, D-56070 Koblenz, Germany Once released into the environment, engineered inorganic nanoparticles (EINPs) will undergo chemical and phys- ical transformation processes. The fate, ecotoxicological potential, and mobility of EINPs in environmental com- partments will be influenced predominantly by their aging and current speciation status. In order to understand the aging mechanisms and impact of ENP transformations on their distribution and bioavailability in real envi- ronmental systems, mesocosm studies can be helpful. -

Uni Koblenz-Landau Environmental Studies
M.SC. ENVIRONMENTAL SCIENCES M.SC. ECOTOXICOLOGY Innovative programs for highly motivated students LANDAU – A SMALL BUT VIVID STUDENT CITY! City of Landau Surrounding areas Vineyards; Source: Stadtverwaltung Landau in der Pfalz 2 Hamburg Berlin London Frankfurt Paris Munich Vienna Milan 3 THE IES IN LANDAU The Institute of Environmental Sciences has evolved very dynamically since its founding in 2004 and is now the leading university institute in Germany 4 H. Jungkunst GEOECOLOGY LANDSCAPE R.B. Schäfer GEOGRAPHY ECOLOGY M. Entling ECOSYSTEM ECOTOXICOLOGY ANALYSIS AND ENVIRONMENT R. Schulz (Founder) ENVIRONMENTAL ENVIRONMENTAL PHYSICS ECONOMICS A. Lorke O. Frör ENVIRONMENAL AND ORGANIC AND SOIL CHEMISTRY ECOLOGICAL CHEMISTRY MOLECULAR ECOLOGY K. Schuhen G.E. Schaumann K. Schwenk 5 STUDY PROGRAMS • M.Sc. Environmental Sciences • M.Sc. Ecotoxicology There are two ways of studying in the international master programs at the University of Koblenz-Landau: 1. Resident study program: Alll courses are studied and completed at the university location in Germany 2 M.SC. ENVIRONMENTAL SCIENCES STUDY PROGRAMS There are two ways of studying in the international master programs at the University of Koblenz-Landau: 1. Resident study program (1+2): All coureses are studied and completed at the university location in Germany • M.Sc. Environmental Science • M.Sc. Ecotoxicology 2 FEES AND LIVING COSTS COSTS FOR RESIDENT STUDY PROGRAM Ø No tuition fees for first bachelor or master‘s program Expenditures for living in Germany Costs in Euro/month Health insurance 90 Rent (student dormitory) 300 Semester registration fee 20 Food and living 350 Total (student dormitory) 760 8 STUDY PROGRAMS There are two ways of studying in the international master programs at the University of Koblenz-Landau: 1. -

How to Find Us
How to find us Miltenyi Biotec B.V. & Co. KG Krefeld DÜSSELDORF Oberhausen Dortmund Germany | Bergisch Gladbach A 46 Headquarters By car: A 1 • Take highway A4 in the direction of Olpe. A 3 A 57 • Stay on the A4. • Leave highway at exit 20, Berg. Gladbach - Bensberg. • Stay on the right lane and follow the road BERGISCH Venlo GLADBACH Miltenyi Biotec to the traffic lights. KÖLN • Go straight ahead up the hill (on your right is A 61 the “Technologiepark Bergisch Gladbach”). A 4 • Turn left at the third traffic light. A 4 Olpe • Keep left and drive straight ahead through the gate. Aachen • On your right is the visitor parking lot A 1 A 59 A 3 (Besucherparkplatz). A 555 • From the visitor parking lot turn half left and go straight forward until you passed house 1. Turn right and take the steps on the right-hand A 61 side to the patio. Cross the patio until you reach BONN Saarbrücken Koblenz Frankfurt the entrance on the right-hand side. By train / bus: • From Cologne Central Station (HBF) take Herkenrath underground no. 16 or 18 to Neumarkt. • Leave the metro station, go upstairs and take Bensberg L 298 Lindlar tram (“Stadtbahn“) no. 1 to Bensberg. MOITZFELD L 195 • Alight at Bensberg and go upstairs to the bus station. Take bus no. 421 or 454 to Technologiepark. P • Cross the street at the traffic light and follow the street uphill for about 200 m, then turn left. P P • Now follow the road straight ahead toward Miltenyi Biotec Miltenyi Biotec. -
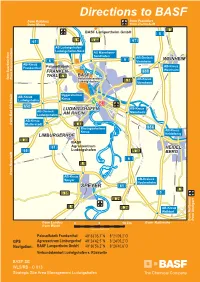
GPS Directions to BASF
WORMS B 47 Directions to BASF B 47from Koblenz from Frankfurt from MainzAS Worms from Darmstadt B 3 BASF Lampertheim GmbH R 5 h e i 61 B 9 n B 44 67 AS Ludwigshafen/ Ludwigshafen-Nord AS Mannheim- Sandhofen 6 AB-Dreieck WEINHEIM 6 Viernheim AB-Kreuz AB-Kreuz Frankenthal Palusolfabrik FRANKEN- 659 Weinheim THAL B 9 BASF fom Saarbrücken from Kaiserslautern Verbundstandort B 38 AB-Kreuz Ludwigshafen Viernheim Oggersheimer AB-Kreuz Kreuz Ludwigshafen 650 LUDWIGSHAFEN AB-Kreuz N AB-Dreieck e Mannheim c AM RHEIN k Bad Dürkheim Ludwigshafen a r AB-Kreuz from Mutterstadt B 44 Rheingönheimer 656 Kreuz AB-Kreuz LIMBURGERHOF Heidelberg B 38 BASF 61 Agrarzentrum HEIDEL- 65 Ludwigshafen B 36 BERG 6 B 9 Neustadt n i e from h AB-Kreuz R Speyer AB-Dreieck Hockenheim SPEYER 61 B 3 B 39 5 B 39 B 9 B 36 AB-Kreuz Walldorf from Stuttgart from Heilbronn from Landau 0 5 10 km from Karlsruhe from Wörth Copyright: BASF SE Palusolfabrik Frankenthal 49°33’05,7’’N 8°21’09,2’’O GPS Agrarzentrum Limburgerhof 49°24’42,5’’N 8°24’05,2’’O Navigation: BASF Lampertheim GmbH 49°36’56,2’’N 8°26’40,6’’O Verbundstandort Ludwigshafen s. Rückseite BASF SE WLS/RB - C 013 Strategic Site Area Management Ludwigshafen from AB-Kreuz from Worms Legend: Frankenthal B 9 N P parking P AS Ludwigshafen/ N T P parking Ludwigshafen-Nord Langgartenstraße Logistic Transfer Center, A6 North Harbour,SewageTechnical Treatment Engineering, T 5 gate T 49°33’08,5’’N Logistic CenterCenter, 8°24’03,8’’O IT-Service Q 920 Sewage from AB-Kreuz Treatment Viernheim BASF- Kleingartenbauverein Plant 7 - 8 Pfingst- 6 weide P H Nacht- Ammoniak- 11 weide H str. -

Case Study: Koblenz, Germany
Job Report Fresh water main for energy supply Mittelrhein GmbH in Koblenz Client: Energieversorgung Mittelrhein GmbH in Koblenz Year of manufacture: 2012 Type of construction: Restoration of two parallel running fresh water mains DN 400 in the Balduin bridge in Koblenz / Rhein Our services: • Delivery of flexible high pressure main Primus Line® and Primus Line connector • Installation of Systems Primus Line® Situation: The mains to be renewed, DN 400, are laid in the superstructure of the heavily used Balduin bridge over the river Mosel near the Deutsches Eck in Koblenz. The mains sections to be restored were determined by the client with l= 2 x 52 m und 2 x 195 m (DN 400). Access to the mains sections was only possible via chambers in the abutments of the bridge and via bays and chambers at the pillars of the bridge. The road over the bridge „An der Moselbrücke“ was not to be blocked for traffic at any of the construction phases. Due to the confined and thus difficult to manage local situation, the Energieversorgung Mittelrhein GmbH de- cided on a fast, space-saving and bend-capable pipe restoration with the System Primus Line®. It was agreed to place the hose drums on the bays of the pillars and the winches at the abutments of the bridge. According to the requirements of the principle, the utilised restoration system was supposed to be capable to allow for an insertion length of 195 m also through the arcs. While sections l= 52 m exhibit a continuously straight progression, respectively two arcs at 45 degrees exists in the sectors l = 195 m at the end of the line in the abutment bridge, on the side of the city swimming pool.