A Primer on Ipv4 Scarcity
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Deploying Ipv6 for an African ISP
Deploying IPv6 for an African ISP By: Mathieu Paonessa How did this all started? • AfriNIC 15 meeEng held in Yaoundé, Cameroon in November 2011 • Presentaons of IPv6 deployments in Egypt, South Africa and Sudan during the African IPv6 iniEaves session. Who is Jaguar Network? • Jaguar Network is a French & Swiss network operator founded in 2001 in Marseille (France). Our main target is providing small & medium business xDSL connecEvity, IP transit, point to point transport, IP/MPLS VPN, colocaon & housing services in more than 30 faciliEes across Europe. • Jaguar Network is building a powerful and resilient opEcal fiber network in Europe to provide high speed and redundant access for all the services provided. Developing it's own label known as "THD" (Très Haute Disponibilité), Jaguar Network focus on quality and proximity with its customers in order to bring valued services to our customers. Who is Creolink? • CREOLINK is an enterprise that specialized in the provision of Telecommunicaons services. • It offers and proposes opEmal and innovave communicaons soluEons for all audiences, including access to high-speed Internet, telephony, connecon of mulple remote sites and much more… • Established in January 2001, CREOLINK has revoluEonized the management of daily business work in Cameroon with its perfect knowledge of the implementaon of new technologies of informaon and communicaon. First step: get an IPv6 allocaon • Started the discussion during the IPv6 session of Tuesday November 22nd. • Creolink was already a member of AfriNIC. • Went -

The Internet in Transition: the State of the Transition to Ipv6 in Today's
Please cite this paper as: OECD (2014-04-03), “The Internet in Transition: The State of the Transition to IPv6 in Today's Internet and Measures to Support the Continued Use of IPv4”, OECD Digital Economy Papers, No. 234, OECD Publishing, Paris. http://dx.doi.org/10.1787/5jz5sq5d7cq2-en OECD Digital Economy Papers No. 234 The Internet in Transition: The State of the Transition to IPv6 in Today's Internet and Measures to Support the Continued Use of IPv4 OECD FOREWORD This report was presented to the OECD Working Party on Communication, Infrastructures and Services Policy (CISP) in June 2013. The Committee for Information, Computer and Communications Policy (ICCP) approved this report in December 2013 and recommended that it be made available to the general public. It was prepared by Geoff Huston, Chief Scientist at the Asia Pacific Network Information Centre (APNIC). The report is published on the responsibility of the Secretary-General of the OECD. Note to Delegations: This document is also available on OLIS under reference code: DSTI/ICCP/CISP(2012)8/FINAL © OECD 2014 THE INTERNET IN TRANSITION: THE STATE OF THE TRANSITION TO IPV6 IN TODAY'S INTERNET AND MEASURES TO SUPPORT THE CONTINUED USE OF IPV4 TABLE OF CONTENTS FOREWORD ................................................................................................................................................... 2 THE INTERNET IN TRANSITION: THE STATE OF THE TRANSITION TO IPV6 IN TODAY'S INTERNET AND MEASURES TO SUPPORT THE CONTINUED USE OF IPV4 .......................... 4 -

Ipv6-Ipsec And
IPSec and SSL Virtual Private Networks ITU/APNIC/MICT IPv6 Security Workshop 23rd – 27th May 2016 Bangkok Last updated 29 June 2014 1 Acknowledgment p Content sourced from n Merike Kaeo of Double Shot Security n Contact: [email protected] Virtual Private Networks p Creates a secure tunnel over a public network p Any VPN is not automagically secure n You need to add security functionality to create secure VPNs n That means using firewalls for access control n And probably IPsec or SSL/TLS for confidentiality and data origin authentication 3 VPN Protocols p IPsec (Internet Protocol Security) n Open standard for VPN implementation n Operates on the network layer Other VPN Implementations p MPLS VPN n Used for large and small enterprises n Pseudowire, VPLS, VPRN p GRE Tunnel n Packet encapsulation protocol developed by Cisco n Not encrypted n Implemented with IPsec p L2TP IPsec n Uses L2TP protocol n Usually implemented along with IPsec n IPsec provides the secure channel, while L2TP provides the tunnel What is IPSec? Internet IPSec p IETF standard that enables encrypted communication between peers: n Consists of open standards for securing private communications n Network layer encryption ensuring data confidentiality, integrity, and authentication n Scales from small to very large networks What Does IPsec Provide ? p Confidentiality….many algorithms to choose from p Data integrity and source authentication n Data “signed” by sender and “signature” verified by the recipient n Modification of data can be detected by signature “verification” -

The Regional Internet Registry System Leslie Nobile
“How It Works” The Regional Internet Registry System Leslie Nobile v Overview • The Regional Internet Registry System • Internet Number Resource Primer: IPv4, IPv6 and ASNs • Significant happenings at the RIR • IPv4 Depletion and IPv6 Transition • IPv4 transfer market • Increase in fraudulent activity • RIR Tools, technologies, etc. 2 The Regional Internet Registry System 3 Brief History Internet Number Resource Administration • 1980s to 1990s • Administration of names, numbers, and protocols contracted by US DoD to ISI/Jon Postel (eventually called IANA) • Registration/support of this function contracted to SRI International and then to Network Solutions • Regionalization begins - Regional Internet Registry system Jon Postel forms • IP number resource administration split off from domain name administration • US Govt separates administration of commercial Internet (InterNIC) from the military Internet (DDN NIC) 4 What is an RIR? A Regional Internet Registry (RIR) manages the allocation and registration of Internet number resources in a particular region of the world and maintains a unique registry of all IP numbers issued. *Number resources include IP addresses (IPv4 and IPv6) and autonomous system (AS) numbers 5 Who Are the RIRs? 6 Core Functions of an RIR Manage, distribute -Maintain directory -Support Internet and register Internet services including infrastructure through Number Resources Whois and routing technical coordination (IPv4 & IPv6 registries addresses and Autonomous System -Facilitate community numbers (ASNs) -Provide -
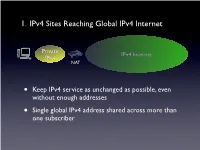
1. Ipv4 Sites Reaching Global Ipv4 Internet
1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber SP IPv6 Network Private Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet IPv4 • Scenario #2 - Service Providers Running out of Private IPv4 space • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup by DHCP, Routing, etc. between a GW and Router • Wherever the NAT lands, it is important that the user keeps control of it • Provides a path to delivering IPv6 SP IPv6 Network Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet • Scenario #3a “Wireless Greenfield” • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup between a host and a Router • IPv4 binding for host applications, transport over IPv6 • Wherever the NAT lands, it is important that the user keeps control of it 3 - 5 Translation Options IPv6 Internet IPv4 Internet IPv6 IPv4 My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #3” • NAT64/DNS64.... - Stateful, DNSSEC Challenges, DNS64 location, etc. My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #5” • IVI - NAT-PT..... Expose only certain IPv6 servers, etc. MY IPv4 Network IPv6 Internet IPv4 Internet • “Scenario #4” • NAT64 - 1:1, Stateless, DNSSEC OK, no DNS64 MY IPv4 Network IPv6 Internet IPv4 Internet • Already solved by existing transition mechanisms?? (teredo, etc). Scenarios 1 - 5 1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber 2. Service Providers Running out of Private IPv4 space ISP Private IPv4 Private Network IPv4 IPv4 Internet • Service Providers with large, privately addressed, IPv4 networks • Organic growth plus pressure to free global addresses for customer use contribute to the problem • The SP Private networks in question generally do not need to reach the Internet at large 3. -

Ipv6 Allocation Policy
Internet Number Resource Status Report As of 31 March 2005 Prepared by Regional Internet Registries AFRINIC, APNIC, ARIN, LACNIC and RIPE NCC Presented by Axel Pawlik Chair, NRO Managing Director, RIPE NCC IPv4 /8 Address Space Status Allocated 94 Available IANA 73 Reserved 16 20 16 1 2 Not Available ARIN Experimental 16 APNIC LACNIC Multicast 16 RIPE NCC 1 (*) AFRINIC Private Use Public Use 1 Central Registry (*) AFRINIC block was allocated on April 11th by IANA March 2005 Internet Number Resource Report IPv4 Allocations from RIRs to LIRs/ISPs Yearly Comparison 3.0 2.5 AFRINIC APNIC 2.0 ARIN LACNIC 1.5 RIPE NCC /8s 1.0 0.5 0.0 1999 2000 2001 2002 2003 2004 2005 March 2005 Internet Number Resource Report IPv4 Allocations RIRs to LIRs/ISPs Cumulative Total (Jan 1999 – March 2005) AFRINIC RIPE NCC 0.3 10.2 0.1% 31% APNIC 11.1 33% ARIN 10.9 33% LACNIC 0.6 2% March 2005 Internet Number Resource Report ASN Assignments RIRs to LIRs/ISPs Yearly Comparison 3000 2500 AFRINIC APNIC ARIN 2000 LACNIC RIPE NCC 1500 1000 500 0 1999 2000 2001 2002 2003 2004 2005 March 2005 Internet Number Resource Report ASN Assignments RIRs to LIRs/ISPs Cumulative Total (Jan 1999 – March 2005) AFRINIC 114 1% RIPE NCC 8369 34% APNIC ARIN 2789 12331 11% 51% LACNIC 645 3% March 2005 Internet Number Resource Report IANA IPv6 Allocations to RIRs (no of /23s) 70 66 APNIC 60 ARIN 50 LACNIC RIPE NCC 40 28 30 20 10 4 1 0 APNIC ARIN LACNIC RIPE NCC March 2005 Internet Number Resource Report IPv6 Allocations RIRs to LIRs/ISPs Yearly Comparison 160 140 AFRINIC APNIC 120 ARIN 100 -

AFRINIC Internet Routing Registry
AFRINIC Internet Routing Registry Alan Barrett CEO AFRINIC AFPIF 2018 | August 2018 Introduction ● AFRINIC IRR ● How AFRINIC IRR functions ● Comparison between AFRINIC and RIPE NCC IRR ● RIPE NCC Announcement ● Analysis of impact on AFRINIC membership ● Communication to Membership ● Proposal for future IRR enhancements AFRINIC IRR Features • Open to AFRINIC Resource members and Legacy Resource Holders in AFRINIC service region. The AFRINIC IRR is a free service • AFRINIC IRR is mirrored by the other IRRs such as APNIC, RIPE NCC, NTTCOM, AMS-IX, Work Online(SA), Moscow IXP and RADB. • Stable and secure source of routing information. No downtimes recorded since the go-live of the AFRINIC IRR • Easy to Use, AFRINIC IRR is a one-stop-shop as it is part of the AFRINIC WHOIS service. • AFRINIC is the single point of contact for both Internet Resource Management and Routing Registry AFRINIC IRR Roadmap June 2013 - June 2018 June 2013: Deployment of AFRINIC IRR 2013 to 2018: Various AFRINIC initiatives to increase IRR adoption and member education on how to to use the AFRINIC IRR (bootcamps, documentation on website, tutorials during outreach, assistance during face to face consultations, migration tool) Enhancements to Business Rules in May 2016, to address some issues experienced by the AFRINIC membership Adoption of the AFRINIC IRR 23% of AFRINIC members (277) adopted the IRR @30 June 2018 We target adoption by at least 50% of AFRINIC members in the next 12 months Majority of AFRINIC members are still using RIPE NCC IRR (free service) Some members use paid IRR services. Adoption of the AFRINIC IRR AFRINIC encourages adoption of the IRR through: 1. -

Internet Protocol Suite
InternetInternet ProtocolProtocol SuiteSuite Srinidhi Varadarajan InternetInternet ProtocolProtocol Suite:Suite: TransportTransport • TCP: Transmission Control Protocol • Byte stream transfer • Reliable, connection-oriented service • Point-to-point (one-to-one) service only • UDP: User Datagram Protocol • Unreliable (“best effort”) datagram service • Point-to-point, multicast (one-to-many), and • broadcast (one-to-all) InternetInternet ProtocolProtocol Suite:Suite: NetworkNetwork z IP: Internet Protocol – Unreliable service – Performs routing – Supported by routing protocols, • e.g. RIP, IS-IS, • OSPF, IGP, and BGP z ICMP: Internet Control Message Protocol – Used by IP (primarily) to exchange error and control messages with other nodes z IGMP: Internet Group Management Protocol – Used for controlling multicast (one-to-many transmission) for UDP datagrams InternetInternet ProtocolProtocol Suite:Suite: DataData LinkLink z ARP: Address Resolution Protocol – Translates from an IP (network) address to a network interface (hardware) address, e.g. IP address-to-Ethernet address or IP address-to- FDDI address z RARP: Reverse Address Resolution Protocol – Translates from a network interface (hardware) address to an IP (network) address AddressAddress ResolutionResolution ProtocolProtocol (ARP)(ARP) ARP Query What is the Ethernet Address of 130.245.20.2 Ethernet ARP Response IP Source 0A:03:23:65:09:FB IP Destination IP: 130.245.20.1 IP: 130.245.20.2 Ethernet: 0A:03:21:60:09:FA Ethernet: 0A:03:23:65:09:FB z Maps IP addresses to Ethernet Addresses -

Empirical Analysis of the Effects and the Mitigation of Ipv4 Address Exhaustion
TECHNISCHE UNIVERSITÄT BERLIN FAKULTÄT FÜR ELEKTROTECHNIK UND INFORMATIK LEHRSTUHL FÜR INTELLIGENTE NETZE UND MANAGEMENT VERTEILTER SYSTEME Empirical Analysis of the Effects and the Mitigation of IPv4 Address Exhaustion vorgelegt von M.Sc. Philipp Richter geboren in Berlin von der Fakultät IV – Elektrotechnik und Informatik der Technischen Universität Berlin zur Erlangung des akademischen Grades DOKTOR DER NATURWISSENSCHAFTEN -DR. RER. NAT.- genehmigte Dissertation Promotionsausschuss: Vorsitzender: Prof. Dr.-Ing. Sebastian Möller, Technische Universität Berlin Gutachterin: Prof. Anja Feldmann, Ph.D., Technische Universität Berlin Gutachter: Prof. Vern Paxson, Ph.D., University of California, Berkeley Gutachter: Prof. Steve Uhlig, Ph.D., Queen Mary University of London Tag der wissenschaftlichen Aussprache: 2. August 2017 Berlin 2017 Abstract IP addresses are essential resources for communication over the Internet. In IP version 4, an address is represented by 32 bits in the IPv4 header; hence there is a finite pool of roughly 4B addresses available. The Internet now faces a fundamental resource scarcity problem: The exhaustion of the available IPv4 address space. In 2011, the Internet Assigned Numbers Authority (IANA) depleted its pool of available IPv4 addresses. IPv4 scarcity is now reality. In the subsequent years, IPv4 address scarcity has started to put substantial economic pressure on the networks that form the Internet. The pools of available IPv4 addresses are mostly depleted and today network operators have to find new ways to satisfy their ongoing demand for IPv4 addresses. Mitigating IPv4 scarcity is not optional, but mandatory: Networks facing address shortage have to take action in order to be able to accommodate additional subscribers and customers. Thus, if not confronted, IPv4 scarcity has the potential to hinder further growth of the Internet. -

The Internet Protocol, Version 4 (Ipv4)
Today’s Lecture I. IPv4 Overview The Internet Protocol, II. IP Fragmentation and Reassembly Version 4 (IPv4) III. IP and Routing IV. IPv4 Options Internet Protocols CSC / ECE 573 Fall, 2005 N.C. State University copyright 2005 Douglas S. Reeves 1 copyright 2005 Douglas S. Reeves 2 Internet Protocol v4 (RFC791) Functions • A universal intermediate layer • Routing IPv4 Overview • Fragmentation and reassembly copyright 2005 Douglas S. Reeves 3 copyright 2005 Douglas S. Reeves 4 “IP over Everything, Everything Over IP” IP = Basic Delivery Service • Everything over IP • IP over everything • Connectionless delivery simplifies router design – TCP, UDP – Dialup and operation – Appletalk – ISDN – Netbios • Unreliable, best-effort delivery. Packets may be… – SCSI – X.25 – ATM – Ethernet – lost (discarded) – X.25 – Wi-Fi – duplicated – SNA – FDDI – reordered – Sonet – ATM – Fibre Channel – Sonet – and/or corrupted – Frame Relay… – … – Remote Direct Memory Access – Ethernet • Even IP over IP! copyright 2005 Douglas S. Reeves 5 copyright 2005 Douglas S. Reeves 6 1 IPv4 Datagram Format IPv4 Header Contents 0 4 8 16 31 •Version (4 bits) header type of service • Functions version total length (in bytes) length (x4) prec | D T R C 0 •Header Length x4 (4) flags identification fragment offset (x8) 1. universal 0 DF MF s •Type of Service (8) e time-to-live (next) protocol t intermediate layer header checksum y b (hop count) identifier •Total Length (16) 0 2 2. routing source IP address •Identification (16) 3. fragmentation and destination IP address reassembly •Flags (3) s •Fragment Offset ×8 (13) e t 4. Options y IP options (if any) b •Time-to-Live (8) 0 4 ≤ •Protocol Identifier (8) s e t •Header Checksum (16) y b payload 5 •Source IP Address (32) 1 5 5 6 •Destination IP Address (32) ≤ •IP Options (≤ 320) copyright 2005 Douglas S. -

SOCKS Protocol Version 6
SOCKS Protocol Version 6 draft-olteanu-intarea-socks-6-08 Vladimir Olteanu IETF 106 What’s new ● DNS provided by SOCKS ● Options for Happy Eyeballs at the proxy Clients need DNS-like features ● A and AAAA – LD_PRELOAD for non-SOCKS-aware apps: gedaddrinfo() separate from connect() – Happy Eyeballs: need to do queries separately ● TXT – ESNI ● MX, Service Binding, etc. – <Insert future use case here> Providing DNS-like features ● Individual SOCKS options (removed in -08) – Have to keep up with use cases – Duplicate DNS functionality – Until -07: A, AAAA, PTR ● Having the client use DNS – Hard to convey policies: resolver IPs, plaintext / over TLS / over HTTPS etc., maybe credentials, etc. – Provide a DNS proxy Why not separate DNS from SOCKS? Client Proxy Server HTTP/SOCKS :1080 HTTP :80 DNS :53 Why not separate DNS from SOCKS? Client Proxy Server HTTP/SOCKS :1080 HTTP :80 DNS :53 WHICH TOR CIRCUIT? ● Need context for DNS query – Otherwise: privacy leaks, suboptimal CDN use DNS provided by SOCKS ● Clients make CONNECT request to 0.0.0.0:53 – Proxy needn’t provide a valid bind address ● Plaintext DNS over SOCKS (opt. over TLS) – TCP by default: SOCKS + UDP more cumbersome to use ● Implementation in Sixtysocks – Run separate DNS proxy locally – Translate 0.0.0.0:53 to 127.0.0.1:53 Happy Eyeballs ● RFC 8305: resolve and connect to a server using both IPv4 and IPv6, keep only one connection – Failover from IPv6 to IPv4 – Better responsiveness if one is faster ● Clients can implement Happy Eyeballs locally – Have DNS + CONNECT Happy Eyeballs: -

Ipv6-Only Deployment in Broadband and Cellular Networks Ipv4 As-A-Service
IPv6-only Deployment in Broadband and Cellular Networks IPv4 as-a-Service LACNIC31 May, 2019 Punta Cana, DO @JordiPalet ([email protected]) - 1 Transition / Co-Existence Techniques • IPv6 has been designed for easing the transition and coexistence with IPv4 • Several strategies have been designed and implemented for coexisting with IPv4 hosts, grouped in three categories: – Dual stack: Simultaneous support for both IPv4 and IPv6 stacks – Tunnels: IPv6 packets encapsulated in IPv4 ones • This has been the commonest choice • Today expect IPv4 packets in IPv6 ones! – Translation: Communication of IPv4-only and IPv6- only. Initially discouraged and only “last resort” (imperfect). Today no other choice! • Expect to use them in combination! - 2 Dual-Stack Approach • When adding IPv6 to a system, do not delete IPv4 – This multi-protocol approach is familiar and well-understood (e.g., for AppleTalk, IPX, etc.) – In the majority of the cases, IPv6 is be bundled with all the OS release, not an extra-cost add-on • Applications (or libraries) choose IP version to use – when initiating, based on DNS response: • if (dest has AAAA record) use IPv6, else use IPv4 – when responding, based on version of initiating packet • This allows indefinite co-existence of IPv4 and IPv6, and gradual app-by-app upgrades to IPv6 usage • A6 record is experimental - 3 Dual-Stack Approach IPv6 IPv6 IPv4 IPv4 Application Application Application Application TCP/UDP TCP/UDP TCP/UDP IPv6 IPv6 IPv4 IPv4 IPv6-only stack Dual-stack (IPv4 & IPv6) IPv4-only stack IPv6