SOCKS Protocol Version 6
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Secure Shell Encrypt and Authenticate Remote Connections to Secure Applications and Data Across Open Networks
Product overview OpenText Secure Shell Encrypt and authenticate remote connections to secure applications and data across open networks Comprehensive Data security is an ongoing concern for organizations. Sensitive, security across proprietary information must always be protected—at rest and networks in motion. The challenge for organizations that provide access to applications and data on host systems is keeping the data Support for Secure Shell (SSH) secure while enabling access from remote computers and devices, whether in a local or wide-area network. ™ Strong SSL/TLS OpenText Secure Shell is a comprehensive security solution that safeguards network ® encryption traffic, including internet communication, between host systems (mainframes, UNIX ™ servers and X Window System applications) and remote PCs and web browsers. When ™ ™ ™ ™ Powerful Kerberos included with OpenText Exceed or OpenText HostExplorer , it provides Secure Shell 2 (SSH-2), Secure Sockets Layer (SSL), LIPKEY and Kerberos security mechanisms to ensure authentication security for communication types, such as X11, NFS, terminal emulation (Telnet), FTP support and any TCP/IP protocol. Secure Shell encrypts data to meet the toughest standards and requirements, such as FIPS 140-2. ™ Secure Shell is an add-on product in the OpenText Connectivity suite, which encrypts application traffic across networks. It helps organizations achieve security compliance by providing Secure Shell (SSH) capabilities. Moreover, seamless integration with other products in the Connectivity suite means zero disruption to the users who remotely access data and applications from web browsers and desktop computers. Secure Shell provides support for the following standards-based security protocols: Secure Shell (SSH)—A transport protocol that allows users to log on to other computers over a network, execute commands on remote machines and securely move files from one machine to another. -

Ipv6-Ipsec And
IPSec and SSL Virtual Private Networks ITU/APNIC/MICT IPv6 Security Workshop 23rd – 27th May 2016 Bangkok Last updated 29 June 2014 1 Acknowledgment p Content sourced from n Merike Kaeo of Double Shot Security n Contact: [email protected] Virtual Private Networks p Creates a secure tunnel over a public network p Any VPN is not automagically secure n You need to add security functionality to create secure VPNs n That means using firewalls for access control n And probably IPsec or SSL/TLS for confidentiality and data origin authentication 3 VPN Protocols p IPsec (Internet Protocol Security) n Open standard for VPN implementation n Operates on the network layer Other VPN Implementations p MPLS VPN n Used for large and small enterprises n Pseudowire, VPLS, VPRN p GRE Tunnel n Packet encapsulation protocol developed by Cisco n Not encrypted n Implemented with IPsec p L2TP IPsec n Uses L2TP protocol n Usually implemented along with IPsec n IPsec provides the secure channel, while L2TP provides the tunnel What is IPSec? Internet IPSec p IETF standard that enables encrypted communication between peers: n Consists of open standards for securing private communications n Network layer encryption ensuring data confidentiality, integrity, and authentication n Scales from small to very large networks What Does IPsec Provide ? p Confidentiality….many algorithms to choose from p Data integrity and source authentication n Data “signed” by sender and “signature” verified by the recipient n Modification of data can be detected by signature “verification” -

Telnet Client 5.11 Ssh Support
TELNET CLIENT 5.11 SSH SUPPORT This document provides This document describes how to install and configure SSH support in Wavelink Telnet Client 5.11. information on the SSH support available in Telnet Client 5.11 OVERVIEW OF SSH SUPPORT Secure Shell (SSH) is a protocol developed for transmitting private information over the Internet. SSH OVERVIEW encrypts data that is transferred over the Telnet session. • Overview of SSH The Telnet Client supports SSH version 1 and 2 and will automatically select the most secure protocol Support that the SSH server supports. • Installing Windows SSH Support This document describes the following: • Configuring the host • Installing Windows SSH support utility profile for SSH • Configuring the host profile for SSH support support • Deploying Windows • Deploying Windows SSH support to the device through Avalanche or ActiveSync SSH Support • Revision History INSTALLING WINDOWS SSH SUPPORT Installing SSH support is a two-step process. First, install SSH support on the PC from which you will deploy Telnet. Once you install SSH support on the PC, use Avalanche or ActiveSync to deploy the utility to the device. To install SSH support on your PC: 1. Obtain the installation executable for SSH support. NOTE: To obtain the Wavelink SSH support utility install, go to http://www.wavelink.com/downloads/ files/sshagreement.aspx. 2. Install SSH support on the PC from which you will deploy the Telnet Client. CONFIGURING THE HOST PROFILE FOR SSH SUPPORT SSH support is configured from the Host Profiles window of the configuration utility. NOTE: SSH is only an active option if SSH support has been installed on the PC running the Telnet Client configuration utility. -
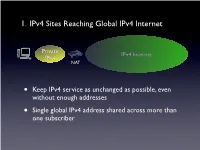
1. Ipv4 Sites Reaching Global Ipv4 Internet
1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber SP IPv6 Network Private Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet IPv4 • Scenario #2 - Service Providers Running out of Private IPv4 space • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup by DHCP, Routing, etc. between a GW and Router • Wherever the NAT lands, it is important that the user keeps control of it • Provides a path to delivering IPv6 SP IPv6 Network Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet • Scenario #3a “Wireless Greenfield” • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup between a host and a Router • IPv4 binding for host applications, transport over IPv6 • Wherever the NAT lands, it is important that the user keeps control of it 3 - 5 Translation Options IPv6 Internet IPv4 Internet IPv6 IPv4 My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #3” • NAT64/DNS64.... - Stateful, DNSSEC Challenges, DNS64 location, etc. My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #5” • IVI - NAT-PT..... Expose only certain IPv6 servers, etc. MY IPv4 Network IPv6 Internet IPv4 Internet • “Scenario #4” • NAT64 - 1:1, Stateless, DNSSEC OK, no DNS64 MY IPv4 Network IPv6 Internet IPv4 Internet • Already solved by existing transition mechanisms?? (teredo, etc). Scenarios 1 - 5 1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber 2. Service Providers Running out of Private IPv4 space ISP Private IPv4 Private Network IPv4 IPv4 Internet • Service Providers with large, privately addressed, IPv4 networks • Organic growth plus pressure to free global addresses for customer use contribute to the problem • The SP Private networks in question generally do not need to reach the Internet at large 3. -

Networking Telnet
IBM i Version 7.2 Networking Telnet IBM Note Before using this information and the product it supports, read the information in “Notices” on page 99. This edition applies to IBM i 7.2 (product number 5770-SS1) and to all subsequent releases and modifications until otherwise indicated in new editions. This version does not run on all reduced instruction set computer (RISC) models nor does it run on CISC models. This document may contain references to Licensed Internal Code. Licensed Internal Code is Machine Code and is licensed to you under the terms of the IBM License Agreement for Machine Code. © Copyright International Business Machines Corporation 1998, 2013. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Telnet................................................................................................................... 1 What's new for IBM i 7.2..............................................................................................................................1 PDF file for Telnet........................................................................................................................................ 1 Telnet scenarios...........................................................................................................................................2 Telnet scenario: Telnet server configuration.........................................................................................2 Telnet scenario: Cascaded Telnet -

Internet Protocol Suite
InternetInternet ProtocolProtocol SuiteSuite Srinidhi Varadarajan InternetInternet ProtocolProtocol Suite:Suite: TransportTransport • TCP: Transmission Control Protocol • Byte stream transfer • Reliable, connection-oriented service • Point-to-point (one-to-one) service only • UDP: User Datagram Protocol • Unreliable (“best effort”) datagram service • Point-to-point, multicast (one-to-many), and • broadcast (one-to-all) InternetInternet ProtocolProtocol Suite:Suite: NetworkNetwork z IP: Internet Protocol – Unreliable service – Performs routing – Supported by routing protocols, • e.g. RIP, IS-IS, • OSPF, IGP, and BGP z ICMP: Internet Control Message Protocol – Used by IP (primarily) to exchange error and control messages with other nodes z IGMP: Internet Group Management Protocol – Used for controlling multicast (one-to-many transmission) for UDP datagrams InternetInternet ProtocolProtocol Suite:Suite: DataData LinkLink z ARP: Address Resolution Protocol – Translates from an IP (network) address to a network interface (hardware) address, e.g. IP address-to-Ethernet address or IP address-to- FDDI address z RARP: Reverse Address Resolution Protocol – Translates from a network interface (hardware) address to an IP (network) address AddressAddress ResolutionResolution ProtocolProtocol (ARP)(ARP) ARP Query What is the Ethernet Address of 130.245.20.2 Ethernet ARP Response IP Source 0A:03:23:65:09:FB IP Destination IP: 130.245.20.1 IP: 130.245.20.2 Ethernet: 0A:03:21:60:09:FA Ethernet: 0A:03:23:65:09:FB z Maps IP addresses to Ethernet Addresses -

The Internet Protocol, Version 4 (Ipv4)
Today’s Lecture I. IPv4 Overview The Internet Protocol, II. IP Fragmentation and Reassembly Version 4 (IPv4) III. IP and Routing IV. IPv4 Options Internet Protocols CSC / ECE 573 Fall, 2005 N.C. State University copyright 2005 Douglas S. Reeves 1 copyright 2005 Douglas S. Reeves 2 Internet Protocol v4 (RFC791) Functions • A universal intermediate layer • Routing IPv4 Overview • Fragmentation and reassembly copyright 2005 Douglas S. Reeves 3 copyright 2005 Douglas S. Reeves 4 “IP over Everything, Everything Over IP” IP = Basic Delivery Service • Everything over IP • IP over everything • Connectionless delivery simplifies router design – TCP, UDP – Dialup and operation – Appletalk – ISDN – Netbios • Unreliable, best-effort delivery. Packets may be… – SCSI – X.25 – ATM – Ethernet – lost (discarded) – X.25 – Wi-Fi – duplicated – SNA – FDDI – reordered – Sonet – ATM – Fibre Channel – Sonet – and/or corrupted – Frame Relay… – … – Remote Direct Memory Access – Ethernet • Even IP over IP! copyright 2005 Douglas S. Reeves 5 copyright 2005 Douglas S. Reeves 6 1 IPv4 Datagram Format IPv4 Header Contents 0 4 8 16 31 •Version (4 bits) header type of service • Functions version total length (in bytes) length (x4) prec | D T R C 0 •Header Length x4 (4) flags identification fragment offset (x8) 1. universal 0 DF MF s •Type of Service (8) e time-to-live (next) protocol t intermediate layer header checksum y b (hop count) identifier •Total Length (16) 0 2 2. routing source IP address •Identification (16) 3. fragmentation and destination IP address reassembly •Flags (3) s •Fragment Offset ×8 (13) e t 4. Options y IP options (if any) b •Time-to-Live (8) 0 4 ≤ •Protocol Identifier (8) s e t •Header Checksum (16) y b payload 5 •Source IP Address (32) 1 5 5 6 •Destination IP Address (32) ≤ •IP Options (≤ 320) copyright 2005 Douglas S. -

61A Lecture 35 Distributed Computing Internet Protocol Transmission
Announcements • Homework 9 (6 pts) due Wednesday 11/26 @ 11:59pm ! Homework Party Monday 6pm-8pm in 2050 VLSB • Guest in live lecture, TA Soumya Basu, on Monday 11/24 • Optional Scheme recursive art contest due Monday 12/1 @ 11:59pm 61A Lecture 35 • No lecture on Wednesday 11/26 (turkey) • No lab on Tuesday 11/25 & Wednesday 11/26 • The week of 12/1: Homework 10 due Wednesday 12/3 & Quiz 3 due Thursday 12/4 on SQL Monday, November 24 ! The lab on SQL (12/2 & 12/3) will be an excellent place to get homework help 2 Distributed Computing A distributed computing application consists of multiple programs running on multiple computers that together coordinate to perform some task. • Computation is performed in parallel by many computers. • Information can be restricted to certain computers. • Redundancy and geographic diversity improve reliability. Distributed Computing Characteristics of distributed computing: • Computers are independent — they do not share memory. • Coordination is enabled by messages passed across a network. • Individual programs have differentiating roles. Distributed computing for large-scale data processing: • Databases respond to queries over a network. • Data sets can be partitioned across multiple machines (next lecture). 4 Network Messages Computers communicate via messages: sequences of bytes transmitted over a network. Messages can serve many purposes: • Send data to another computer • Request data from another computer • Instruct a program to call a function on some arguments. Internet Protocol • Transfer a program to be executed by another computer. Messages conform to a message protocol adopted by both the sender (to encode the message) & receiver (to interpret the message). -

New Techniques to Enhance the Capabilities of the Socks Network Security Protocol
NEW TECHNIQUES TO ENHANCE THE CAPABILITIES OF THE SOCKS NETWORK SECURITY PROTOCOL Mukund Sundararajan and Mohammad S. Obaidat Computer Science Department, Monmouth University, West Long Branch, NJ, U.S.A. Keywords: Security protocols for computer networks, SOCKS, telecommunications, multicast, UDP tunneling. Abstract: SOCKS is an industry standard network security protocol used in private networks to allow secure traversal of application layer traffic through the boundaries of the network. Standardized by IETF in Request for Comments (RFC) 1928 (Leech et al., 1996) as SOCKS Version 5, this protocol has found widespread use in various security frameworks to allow a variety of application layer protocols to securely traverse a firewall. This paper is the result of research performed on the usability of the protocol in application domains such as multicast. We discuss some of the shortcomings of the SOCKS protocol and provide a framework and the methods for enhancing the capabilities of the protocol in areas such as multicast and advanced TCP and UDP capabilities not addressed by the current standard of the protocol. The methods proposed are being implemented in a reference implementation by the authors. 1 INTRODUCTION Operating in a client server mode, application nodes or computers within a SOCKS protected In today’s global and geographically dispersed network are ‘socksified’ by a socks client library that organizational world, network security is a key provides a transparent abstraction layer between the concern to organizations and individuals. With application and the kernel socket library and hides advances in technology, most of today’s the implementation details of the socks protocol from organizations have their key resources and data the application. -

NBAR2 Standard Protocol Pack 1.0
NBAR2 Standard Protocol Pack 1.0 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 © 2013 Cisco Systems, Inc. All rights reserved. CONTENTS CHAPTER 1 Release Notes for NBAR2 Standard Protocol Pack 1.0 1 CHAPTER 2 BGP 3 BITTORRENT 6 CITRIX 7 DHCP 8 DIRECTCONNECT 9 DNS 10 EDONKEY 11 EGP 12 EIGRP 13 EXCHANGE 14 FASTTRACK 15 FINGER 16 FTP 17 GNUTELLA 18 GOPHER 19 GRE 20 H323 21 HTTP 22 ICMP 23 IMAP 24 IPINIP 25 IPV6-ICMP 26 IRC 27 KAZAA2 28 KERBEROS 29 L2TP 30 NBAR2 Standard Protocol Pack 1.0 iii Contents LDAP 31 MGCP 32 NETBIOS 33 NETSHOW 34 NFS 35 NNTP 36 NOTES 37 NTP 38 OSPF 39 POP3 40 PPTP 41 PRINTER 42 RIP 43 RTCP 44 RTP 45 RTSP 46 SAP 47 SECURE-FTP 48 SECURE-HTTP 49 SECURE-IMAP 50 SECURE-IRC 51 SECURE-LDAP 52 SECURE-NNTP 53 SECURE-POP3 54 SECURE-TELNET 55 SIP 56 SKINNY 57 SKYPE 58 SMTP 59 SNMP 60 SOCKS 61 SQLNET 62 SQLSERVER 63 SSH 64 STREAMWORK 65 NBAR2 Standard Protocol Pack 1.0 iv Contents SUNRPC 66 SYSLOG 67 TELNET 68 TFTP 69 VDOLIVE 70 WINMX 71 NBAR2 Standard Protocol Pack 1.0 v Contents NBAR2 Standard Protocol Pack 1.0 vi CHAPTER 1 Release Notes for NBAR2 Standard Protocol Pack 1.0 NBAR2 Standard Protocol Pack Overview The Network Based Application Recognition (NBAR2) Standard Protocol Pack 1.0 is provided as the base protocol pack with an unlicensed Cisco image on a device. -

Domain Name System 1 Domain Name System
Domain Name System 1 Domain Name System The Domain Name System (DNS) is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. A Domain Name Service translates queries for domain names (which are easier to understand and utilize when accessing the internet) into IP addresses for the purpose of locating computer services and devices worldwide. An often-used analogy to explain the Domain Name System is that it serves as the phone book for the Internet by translating human-friendly computer hostnames into IP addresses. For example, the domain name www.example.com translates to the addresses 192.0.43.10 (IPv4) and 2620:0:2d0:200::10 (IPv6). The Domain Name System makes it possible to assign domain names to groups of Internet resources and users in a meaningful way, independent of each entity's physical location. Because of this, World Wide Web (WWW) hyperlinks and Internet contact information can remain consistent and constant even if the current Internet routing arrangements change or the participant uses a mobile device. Internet domain names are easier to remember than IP addresses such as 208.77.188.166 (IPv4) or 2001:db8:1f70::999:de8:7648:6e8 (IPv6). Users take advantage of this when they recite meaningful Uniform Resource Locators (URLs) and e-mail addresses without having to know how the computer actually locates them. The Domain Name System distributes the responsibility of assigning domain names and mapping those names to IP addresses by designating authoritative name servers for each domain. -

Nist Sp 800-77 Rev. 1 Guide to Ipsec Vpns
NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel Karen Scarfone Paul Wouters This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 C O M P U T E R S E C U R I T Y NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel* Computer Security Division Information Technology Laboratory Karen Scarfone Scarfone Cybersecurity Clifton, VA Paul Wouters Red Hat Toronto, ON, Canada *Former employee; all work for this publication was done while at NIST This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 June 2020 U.S. Department of Commerce Wilbur L. Ross, Jr., Secretary National Institute of Standards and Technology Walter Copan, NIST Director and Under Secretary of Commerce for Standards and Technology Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3551 et seq., Public Law (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on federal agencies by the Secretary of Commerce under statutory authority.