Guidelines on Firewalls and Firewall Policy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ipsec, SSL, Firewall, Wireless Security
IPSec 1 Outline • Internet Protocol – IPv6 • IPSec – Security Association (SA) – IPSec Base Protocol (AH, ESP) – Encapsulation Mode (transport, tunnel) 2 IPv6 Header • Initial motivation: – 32-bit address space soon to be completely allocated. – Expands addresses to 128 bits • 430,000,000,000,000,000,000 for every square inch of earth’s surface! • Solves IPv4 problem of insufficient address space • Additional motivation: – header format helps speedy processing/forwarding – header changes to facilitate QoS IPv6 datagram format: – fixed-length 40 byte header – no fragmentation allowed 3 IPv6 Header (Cont) Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data 4 Other Changes from IPv4 • Checksum: removed entirely to reduce processing time at each hop • Options: allowed, but outside of header, indicated by “Next Header” field • ICMPv6: new version of ICMP – additional message types, e.g. “Packet Too Big” – multicast group management functions 5 IPv6 Security – IPsec mandated • IPsec is mandated in IPv6 – This means that all implementations (i.e. hosts, routers, etc) must have IPsec capability to be considered as IPv6-conformant • When (If?) IPv6 is in widespread use, this means that IPsec will be installed everywhere – At the moment, IPsec is more common in network devices (routers, etc) than user hosts, but this would change with IPsec • All hosts having IPsec => real end-to-end security possible 6 IPv6 Security • Enough IP addrs for every imaginable device + Real end-to-end security = Ability to securely communicate from anything to anything 7 IPv6 Security – harder to scan networks • With IPv4, it is easy to scan a network – With tools like nmap, can scan a typical subnet in a few minutes see: http://www.insecure.org/nmap/ – Returning list of active hosts and open ports – Many worms also operate by scanning • e.g. -

Poster: Introducing Massbrowser: a Censorship Circumvention System Run by the Masses
Poster: Introducing MassBrowser: A Censorship Circumvention System Run by the Masses Milad Nasr∗, Anonymous∗, and Amir Houmansadr University of Massachusetts Amherst fmilad,[email protected] ∗Equal contribution Abstract—We will present a new censorship circumvention sys- side the censorship regions, which relay the Internet traffic tem, currently being developed in our group. The new system of the censored users. This includes systems like Tor, VPNs, is called MassBrowser, and combines several techniques from Psiphon, etc. Unfortunately, such circumvention systems are state-of-the-art censorship studies to design a hard-to-block, easily blocked by the censors by enumerating their limited practical censorship circumvention system. MassBrowser is a set of proxy server IP addresses [14]. (2) Costly to operate: one-hop proxy system where the proxies are volunteer Internet To resist proxy blocking by the censors, recent circumven- users in the free world. The power of MassBrowser comes from tion systems have started to deploy the proxies on shared-IP the large number of volunteer proxies who frequently change platforms such as CDNs, App Engines, and Cloud Storage, their IP addresses as the volunteer users move to different a technique broadly referred to as domain fronting [3]. networks. To get a large number of volunteer proxies, we This mechanism, however, is prohibitively expensive [11] provide the volunteers the control over how their computers to operate for large scales of users. (3) Poor QoS: Proxy- are used by the censored users. Particularly, the volunteer based circumvention systems like Tor and it’s variants suffer users can decide what websites they will proxy for censored from low quality of service (e.g., high latencies and low users, and how much bandwidth they will allocate. -

Best Practices: Use of Web Application Firewalls
OWASP Papers Program Best Practice: Use of Web Application Firewalls Best Practices: Use of Web Application Firewalls Version 1.0.4, March 2008, English translation 25. May 2008 Author: OWASP German Chapter with collaboration from: Maximilian Dermann Mirko Dziadzka Boris Hemkemeier Achim Hoffmann Alexander Meisel Matthias Rohr Thomas Schreiber OWASP Papers Program Best Practice: Use of Web Application Firewalls Abstract Web applications of all kinds, whether online shops or partner portals, have in recent years increasingly become the target of hacker attacks. The attackers are using methods which are specifically aimed at exploiting potential weak spots in the web application software itself – and this is why they are not detected, or are not detected with sufficient accuracy, by traditional IT security systems such as network firewalls or IDS/IPS systems. OWASP develops tools and best practices to support developers, project managers and security testers in the development and operation of secure web applications. Additional protection against attacks, in particular for already productive web applications, is offered by what is still a emerging category of IT security systems, known as Web Application Firewalls (hereinafter referred to simply as WAF), often also called Web Application Shields or Web Application Security Filters. One of the criteria for meeting the security standard of the credit card industry currently in force (PCI DSS - Payment Card Industry Data Security Standard v.1.1) for example, is either a regular source code review or the use of a WAF. The document is aimed primarily at technical decision-makers, especially those responsible for operations and security as well as application owners (specialist department, technical application managers) evaluating the use of a WAF. -

Usability and Security of Personal Firewalls
Usability and Security of Personal Firewalls Almut Herzog^ and Nahid Shahmehri^ Dept. of Computer and Information Science, Linkopings universitet,Sweden {almhe, nahsh}@ida.liu.se Abstract. Effective security of a personal firewall depends on (1) the rule granularity and the implementation of the rule enforcement and (2) the correctness and granularity of user decisions at the time of an alert. A misconfigured or loosely configured firewall may be more dangerous than no firewall at all because of the user's false sense of security. This study assesses effective security of 13 personal firewalls by comparing possible granularity of rules as well as the usability of rule set-up and its influence on security. In order to evaluate usability, we have submitted each firewall to use cases that require user decisions and cause rule creation. In order to evaluate the firewalls' security, we analysed the created rules. In ad dition, we ran a port scan and replaced a legitimate, network-enabled application with another program to etssess the firewalls' behaviour in misuse cases. We have conducted a cognitive walkthrough paying special attention to user guidance and user decision support. We conclude that a stronger emphasis on user guidance, on conveying the design of the personal firewall application, on the principle of least privilege and on implications of default settings would greatly enhance both usability and security of personal firewalls. 1 Introduction In times where roaming users connect their laptops to a variety of public, pri vate and corporate wireless or wired networks and in times where more and more computers are always online, host-based firewalls implemented in soft ware, called personal firewalls, have become an important part of the security armour of a personal computer. -

SILC-A SECURED INTERNET CHAT PROTOCOL Anindita Sinha1, Saugata Sinha2 Asst
ISSN (Print) : 2320 – 3765 ISSN (Online): 2278 – 8875 International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering Vol. 2, Issue 5, May 2013 SILC-A SECURED INTERNET CHAT PROTOCOL Anindita Sinha1, Saugata Sinha2 Asst. Prof, Dept. of ECE, Siliguri Institute of Technology, Sukna, Siliguri, West Bengal, India 1 Network Engineer, Network Dept, Ericsson Global India Ltd, India2 Abstract:-. The Secure Internet Live Conferencing (SILC) protocol, a new generation chat protocol provides full featured conferencing services, compared to any other chat protocol. Its main interesting point is security which has been described all through the paper. We have studied how encryption and authentication of the messages in the network achieves security. The security has been the primary goal of the SILC protocol and the protocol has been designed from the day one security in mind. In this paper we have studied about different keys which have been used to achieve security in the SILC protocol. The main function of SILC is to achieve SECURITY which is most important in any chat protocol. We also have studied different command for communication in chat protocols. Keywords: SILC protocol, IM, MIME, security I.INTRODUCTION SILC stands for “SECURE INTERNET LIVE CONFERENCING”. SILC is a secure communication platform, looks similar to IRC, first protocol & quickly gained the status of being the most popular chat on the net. The security is important feature in applications & protocols in contemporary network environment. It is not anymore enough to just provide services; they need to be secure services. The SILC protocol is a new generation chat protocol which provides full featured conferencing services; additionally it provides security by encrypting & authenticating the messages in the network. -

The Internet in Transition: the State of the Transition to Ipv6 in Today's
Please cite this paper as: OECD (2014-04-03), “The Internet in Transition: The State of the Transition to IPv6 in Today's Internet and Measures to Support the Continued Use of IPv4”, OECD Digital Economy Papers, No. 234, OECD Publishing, Paris. http://dx.doi.org/10.1787/5jz5sq5d7cq2-en OECD Digital Economy Papers No. 234 The Internet in Transition: The State of the Transition to IPv6 in Today's Internet and Measures to Support the Continued Use of IPv4 OECD FOREWORD This report was presented to the OECD Working Party on Communication, Infrastructures and Services Policy (CISP) in June 2013. The Committee for Information, Computer and Communications Policy (ICCP) approved this report in December 2013 and recommended that it be made available to the general public. It was prepared by Geoff Huston, Chief Scientist at the Asia Pacific Network Information Centre (APNIC). The report is published on the responsibility of the Secretary-General of the OECD. Note to Delegations: This document is also available on OLIS under reference code: DSTI/ICCP/CISP(2012)8/FINAL © OECD 2014 THE INTERNET IN TRANSITION: THE STATE OF THE TRANSITION TO IPV6 IN TODAY'S INTERNET AND MEASURES TO SUPPORT THE CONTINUED USE OF IPV4 TABLE OF CONTENTS FOREWORD ................................................................................................................................................... 2 THE INTERNET IN TRANSITION: THE STATE OF THE TRANSITION TO IPV6 IN TODAY'S INTERNET AND MEASURES TO SUPPORT THE CONTINUED USE OF IPV4 .......................... 4 -

Ipv6-Ipsec And
IPSec and SSL Virtual Private Networks ITU/APNIC/MICT IPv6 Security Workshop 23rd – 27th May 2016 Bangkok Last updated 29 June 2014 1 Acknowledgment p Content sourced from n Merike Kaeo of Double Shot Security n Contact: [email protected] Virtual Private Networks p Creates a secure tunnel over a public network p Any VPN is not automagically secure n You need to add security functionality to create secure VPNs n That means using firewalls for access control n And probably IPsec or SSL/TLS for confidentiality and data origin authentication 3 VPN Protocols p IPsec (Internet Protocol Security) n Open standard for VPN implementation n Operates on the network layer Other VPN Implementations p MPLS VPN n Used for large and small enterprises n Pseudowire, VPLS, VPRN p GRE Tunnel n Packet encapsulation protocol developed by Cisco n Not encrypted n Implemented with IPsec p L2TP IPsec n Uses L2TP protocol n Usually implemented along with IPsec n IPsec provides the secure channel, while L2TP provides the tunnel What is IPSec? Internet IPSec p IETF standard that enables encrypted communication between peers: n Consists of open standards for securing private communications n Network layer encryption ensuring data confidentiality, integrity, and authentication n Scales from small to very large networks What Does IPsec Provide ? p Confidentiality….many algorithms to choose from p Data integrity and source authentication n Data “signed” by sender and “signature” verified by the recipient n Modification of data can be detected by signature “verification” -

Brocade Vyatta Network OS ALG Configuration Guide, 5.2R1
CONFIGURATION GUIDE Brocade Vyatta Network OS ALG Configuration Guide, 5.2R1 Supporting Brocade 5600 vRouter, VNF Platform, and Distributed Services Platform 53-1004711-01 24 October 2016 © 2016, Brocade Communications Systems, Inc. All Rights Reserved. Brocade, the B-wing symbol, and MyBrocade are registered trademarks of Brocade Communications Systems, Inc., in the United States and in other countries. Other brands, product names, or service names mentioned of Brocade Communications Systems, Inc. are listed at www.brocade.com/en/legal/ brocade-Legal-intellectual-property/brocade-legal-trademarks.html. Other marks may belong to third parties. Notice: This document is for informational purposes only and does not set forth any warranty, expressed or implied, concerning any equipment, equipment feature, or service offered or to be offered by Brocade. Brocade reserves the right to make changes to this document at any time, without notice, and assumes no responsibility for its use. This informational document describes features that may not be currently available. Contact a Brocade sales office for information on feature and product availability. Export of technical data contained in this document may require an export license from the United States government. The authors and Brocade Communications Systems, Inc. assume no liability or responsibility to any person or entity with respect to the accuracy of this document or any loss, cost, liability, or damages arising from the information contained herein or the computer programs that accompany it. The product described by this document may contain open source software covered by the GNU General Public License or other open source license agreements. To find out which open source software is included in Brocade products, view the licensing terms applicable to the open source software, and obtain a copy of the programming source code, please visit http://www.brocade.com/support/oscd. -

EC-Council Network Security Administrator (Exam 312-38)
Product Information Sheet Exam 312-38 EC-Council Network Security Administrator (Exam 312-38) Page | 1 ENSAv4 Copyright © by EC-Council All Rights Reserved. Reproduction is Strictly Prohibited. Product Information Sheet Exam 312-38 EC-Council NSA is CNSS 4011 Certified The Committee on National Security Systems (CNSS)/National Security Agency (NSA) of the United States of America certified EC-Council’s Network Security Administrator (ENSA) course as having met 100% of the requirements as set out by the Committee on National Security Systems (CNSS) National Standards 4011. This certification is managed by the Information Assurance Courseware Evaluation (IACE) Program, National INFOSEC (Information Security) Education and Training Program and is administered by the U.S. National Security Agency (NSA). The Committee on National Security Systems (CNSS) and National Security Agency (NSA) has developed a nationally recognized certification program based on NSTISSI standards. The CNSS/NSA Certification is a government class certification that is recognized as the National Training Standard for Information Security Professionals Students who have obtained these certifications would have demonstrated a solid grasp of the principles as outlined in the 4011 standard. With this, EC-Council has joined the ranks of the organizations United States Air Force Academy, United States Military Academy, Air Force Institute of Technology and Carnegie Mellon University; all of whom have attained the National Training Standard for Information Security Professionals - the CNSS 4011. Introduction The EC-Council's Network Security Administrator certification looks at the network security in defensive view while the CEH certification program looks at the security in offensive mode. The ENSA program is designed to provide fundamental skills needed to analyze the internal and external security threats against a network, and to develop security policies that will protect an organization’s information. -

Ipv6 DMZ Web Service Technology Design Guide
IPv6 DMZ Web Service Technology Design Guide August 2014 Series Table of Contents Preface ........................................................................................................................................1 CVD Navigator .............................................................................................................................2 Use Cases .................................................................................................................................. 2 Scope ......................................................................................................................................... 2 Proficiency .................................................................................................................................. 2 Introduction .................................................................................................................................3 Technology Use Cases ............................................................................................................... 3 Use Case: Enable Native IPv6 Access for Network Traffic Between the Internet and a Web Server DMZ Network.............................................................................................................. 3 Use Case: Enable IPv6 Access for Network Traffic Between the Internet and an IPv4-only Web Server DMZ Network ..................................................................................................... 3 Design Overview ........................................................................................................................ -

Iptables with Shorewall!
Iptables with shorewall! Table of Contents 1. Install swarmlab-sec (Home PC) . 1 2. shorewall . 1 2.1. Installation . 2 3. Basic Two-Interface Firewall. 2 4. Shorewall Concepts . 3 4.1. zones — Shorewall zone declaration file . 3 4.2. interfaces — Shorewall interfaces file. 4 4.3. policy — Shorewall policy file . 4 4.4. rules — Shorewall rules file . 4 4.5. Compile then Execute . 4 5. Three-Interface Firewall. 5 5.1. zones . 6 5.2. interfaces . 6 5.3. policy . 7 5.4. rules . 7 5.5. masq - Shorewall Masquerade/SNAT definition file . 7 5.6. snat — Shorewall SNAT/Masquerade definition file . 8 5.7. Compile and Execute . 8 1. Install swarmlab-sec (Home PC) HowTo: See http://docs.swarmlab.io/lab/sec/sec.adoc.html NOTE Assuming you’re already logged in 2. shorewall Shorewall is an open source firewall tool for Linux that builds upon the Netfilter (iptables/ipchains) system built into the Linux kernel, making it easier to manage more complex configuration schemes by providing a higher level of abstraction for describing rules using text files. More: wikipedia 1 NOTE Our docker instances have only one nic to add more nic’s: create netowrk frist docker network create --driver=bridge --subnet=192.168.0.0/16 net1 docker network create --driver=bridge --subnet=192.168.0.0/16 net2 docker network create --driver=bridge --subnet=192.168.0.0/16 net3 then connect network to container connect network created to container docker network connect net1 master docker network connect net1 worker1 docker network connect net2 master docker network connect net2 worker2 now let’s look at the following image 2.1. -
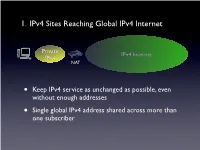
1. Ipv4 Sites Reaching Global Ipv4 Internet
1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber SP IPv6 Network Private Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet IPv4 • Scenario #2 - Service Providers Running out of Private IPv4 space • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup by DHCP, Routing, etc. between a GW and Router • Wherever the NAT lands, it is important that the user keeps control of it • Provides a path to delivering IPv6 SP IPv6 Network Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet • Scenario #3a “Wireless Greenfield” • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup between a host and a Router • IPv4 binding for host applications, transport over IPv6 • Wherever the NAT lands, it is important that the user keeps control of it 3 - 5 Translation Options IPv6 Internet IPv4 Internet IPv6 IPv4 My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #3” • NAT64/DNS64.... - Stateful, DNSSEC Challenges, DNS64 location, etc. My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #5” • IVI - NAT-PT..... Expose only certain IPv6 servers, etc. MY IPv4 Network IPv6 Internet IPv4 Internet • “Scenario #4” • NAT64 - 1:1, Stateless, DNSSEC OK, no DNS64 MY IPv4 Network IPv6 Internet IPv4 Internet • Already solved by existing transition mechanisms?? (teredo, etc). Scenarios 1 - 5 1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber 2. Service Providers Running out of Private IPv4 space ISP Private IPv4 Private Network IPv4 IPv4 Internet • Service Providers with large, privately addressed, IPv4 networks • Organic growth plus pressure to free global addresses for customer use contribute to the problem • The SP Private networks in question generally do not need to reach the Internet at large 3.