The Internet in Transition: the State of the Transition to Ipv6 in Today's
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Remote Collaborative Real-Time Multimedia Experience Over The
Remote C ollaborative Real-Time Multimedia Experience over the Future Internet ROMEO Grant Agreement Number: 287896 D4.2 Report on streaming/broadcast techniques for 3D multi-view video and spatial audio ROMEO WP4 Page 1/50 Document description Name of document Report on streaming/broadcast techniques for 3D multi-view video and spatial audio Abstract This document provides a detailed description of the packetization schemes in ROMEO and specifies high level syntax elements of the media formats in order to perform efficient transport and synchronization of the 3D audio and multiview video streams. Adaptation mechanisms and error concealment methods are also proposed in the context of degraded network conditions. Document identifier D4.2 Document class Deliverable Version 1.0 Author(s) N.Tizon, D. Nicholson (VITEC) H. Weigold, H. Ibl, J. Lauterjung (R&S) K. Birkos, A. Kordelas, A. Lykourgiotis, I. Politis (UPAT) Xiyu Shi (MulSys) M.Laabs (IRT) E. Ekmekcioglu (UNIS) A. Akman, S. O. Pelvan, S. Çiftçi, E. Çimen Öztürk (TTA) QAT team D. Doyen (TEC) F. Pascual Blanco (TID) H. Marques (IT) Date of creation 24-Jul-2012 Date of last modification 21-Dec-2012 Status Final Destination European Commission WP number WP4 Dissemination Level Public Deliverable Nature Report ROMEO WP4 Page 2/50 TABLE OF CONTENTS TABLE OF CONTENTS ............................................................................................................. 3 LIST OF FIGURES..................................................................................................................... -

Army Packet Radio Network Protocol Study
FTD-RL29 742 ARMY PACKET RAHDIO NETWORK PROTOCOL STUDY(U) SRI / I INTERNATIONAL MENLO PARK CA D E RUBIN NOY 77 I SRI-TR-2325-i43-i DRHCi5-73-C-8i87 p UCLASSIFIED F/G 07/2. 1 L '44 .25I MICROCOPY RESOLUTION TFST CHART NAT ONAL BUREAU Cf STINDRES 1% l A I " S2 5 0 0 S _S S S ARMY PACKET RADIO NETWORK PROTOCOL STUDY CA Technical Report 2325-143-1 e November1977 By: Darryl E. Rubin Prepared for: U,S. Army Electronics Command Fort Monmouth, New Jersey 07703 Attn: Mi. Charles Graff, DRDCO-COM-RF-4 Contract DAHC 1 5-73-C-01 87 SRI Project 2325 * 0. The views and conclusions contained in this document are those of author and should not be Interpreted as necessarily representing th Cofficial policies, either expressed or implied, of the U.S. Army or the .LJ United States Government. -. *m 333 Ravenswood Ave. * Menlo Park, California 94025 0 (415) 326-6200 eCable: STANRES, Menlo Park * TWX: 910-373-1246 83 06 '03 . 4qUNCLASSIFIED SECURITY CLASSIFICATION OF THIS PAGE (When Data Entered) READ INSTRUCTIONS REPORT DOCUMENTATION PAGE BEFORE COMPLETING FORM 1 REPORT NUMBER 2. GOVT ACCESSION NO 3 RECIPIENT'S CATALOG NUMBER [" 2~~1325-143-1 / )r -. : i'/ - 4. TITLE Subtitle) 5-.and TYPE OF REPORT & PERIOD COVERED Army Packet Radio Network Protocol Study Technical Report 6. PERFORMING ORG. REPORT NUMBER 7 AUTHOR(s) A 8 CONTRACT OR GRANT NUMBER(s) Darrvl E. Rubin DAHCI5-73C-0187 9. PERFORMING ORGANIZATION NAME AND ADDRESS 10. PROGRAM ELEMENT, PROJECT. TASK AREA & WORK UNIT NUMBERS SRI International Program Code N. -

Empirical Analysis of the Effects and the Mitigation of Ipv4 Address Exhaustion
TECHNISCHE UNIVERSITÄT BERLIN FAKULTÄT FÜR ELEKTROTECHNIK UND INFORMATIK LEHRSTUHL FÜR INTELLIGENTE NETZE UND MANAGEMENT VERTEILTER SYSTEME Empirical Analysis of the Effects and the Mitigation of IPv4 Address Exhaustion vorgelegt von M.Sc. Philipp Richter geboren in Berlin von der Fakultät IV – Elektrotechnik und Informatik der Technischen Universität Berlin zur Erlangung des akademischen Grades DOKTOR DER NATURWISSENSCHAFTEN -DR. RER. NAT.- genehmigte Dissertation Promotionsausschuss: Vorsitzender: Prof. Dr.-Ing. Sebastian Möller, Technische Universität Berlin Gutachterin: Prof. Anja Feldmann, Ph.D., Technische Universität Berlin Gutachter: Prof. Vern Paxson, Ph.D., University of California, Berkeley Gutachter: Prof. Steve Uhlig, Ph.D., Queen Mary University of London Tag der wissenschaftlichen Aussprache: 2. August 2017 Berlin 2017 Abstract IP addresses are essential resources for communication over the Internet. In IP version 4, an address is represented by 32 bits in the IPv4 header; hence there is a finite pool of roughly 4B addresses available. The Internet now faces a fundamental resource scarcity problem: The exhaustion of the available IPv4 address space. In 2011, the Internet Assigned Numbers Authority (IANA) depleted its pool of available IPv4 addresses. IPv4 scarcity is now reality. In the subsequent years, IPv4 address scarcity has started to put substantial economic pressure on the networks that form the Internet. The pools of available IPv4 addresses are mostly depleted and today network operators have to find new ways to satisfy their ongoing demand for IPv4 addresses. Mitigating IPv4 scarcity is not optional, but mandatory: Networks facing address shortage have to take action in order to be able to accommodate additional subscribers and customers. Thus, if not confronted, IPv4 scarcity has the potential to hinder further growth of the Internet. -

Fireware Configuration Example
Configuration Example Use a Branch Office VPN for Failover From a Private Network Link Example configuration files created with — WSM v11.10.1 Revised — 7/22/2015 Use Case In this configuration example, an organization has networks at two sites and uses a private network link to send traffic between the two networks. To make their network configuration more fault-tolerant, they want to set up a secondary route between the networks to use as a backup if the private network link fails, but they do not want to spend money on a second private network connection. To solve this problem, they can use a branch office VPN with dynamic routing. This configuration example provides a model of how you could set up your network to automatically fail over to a branch office VPN if a primary private network connection between two sites becomes unavailable. To use the branch office VPN connection for automatic failover, you must enable dynamic routing on the Firebox at each site. You can use any supported dynamic routing protocol (RIP v1, RIP v2, OSPF, or BGP v4). This configuration example is provided as a guide. Additional configuration settings could be necessary, or more appropriate, for your network environment. Solution Overview A routing protocol is the method routers use to communicate with each other and share information about the status of network routing tables. On the Firebox, static routes are persistent and do not change, even if the link to the next hop goes down. When you enable dynamic routing, the Firebox automatically updates the routing table based on the status of the connection. -

New Techniques to Enhance the Capabilities of the Socks Network Security Protocol
NEW TECHNIQUES TO ENHANCE THE CAPABILITIES OF THE SOCKS NETWORK SECURITY PROTOCOL Mukund Sundararajan and Mohammad S. Obaidat Computer Science Department, Monmouth University, West Long Branch, NJ, U.S.A. Keywords: Security protocols for computer networks, SOCKS, telecommunications, multicast, UDP tunneling. Abstract: SOCKS is an industry standard network security protocol used in private networks to allow secure traversal of application layer traffic through the boundaries of the network. Standardized by IETF in Request for Comments (RFC) 1928 (Leech et al., 1996) as SOCKS Version 5, this protocol has found widespread use in various security frameworks to allow a variety of application layer protocols to securely traverse a firewall. This paper is the result of research performed on the usability of the protocol in application domains such as multicast. We discuss some of the shortcomings of the SOCKS protocol and provide a framework and the methods for enhancing the capabilities of the protocol in areas such as multicast and advanced TCP and UDP capabilities not addressed by the current standard of the protocol. The methods proposed are being implemented in a reference implementation by the authors. 1 INTRODUCTION Operating in a client server mode, application nodes or computers within a SOCKS protected In today’s global and geographically dispersed network are ‘socksified’ by a socks client library that organizational world, network security is a key provides a transparent abstraction layer between the concern to organizations and individuals. With application and the kernel socket library and hides advances in technology, most of today’s the implementation details of the socks protocol from organizations have their key resources and data the application. -

Ipv6-Only Deployment in Broadband and Cellular Networks Ipv4 As-A-Service
IPv6-only Deployment in Broadband and Cellular Networks IPv4 as-a-Service LACNIC31 May, 2019 Punta Cana, DO @JordiPalet ([email protected]) - 1 Transition / Co-Existence Techniques • IPv6 has been designed for easing the transition and coexistence with IPv4 • Several strategies have been designed and implemented for coexisting with IPv4 hosts, grouped in three categories: – Dual stack: Simultaneous support for both IPv4 and IPv6 stacks – Tunnels: IPv6 packets encapsulated in IPv4 ones • This has been the commonest choice • Today expect IPv4 packets in IPv6 ones! – Translation: Communication of IPv4-only and IPv6- only. Initially discouraged and only “last resort” (imperfect). Today no other choice! • Expect to use them in combination! - 2 Dual-Stack Approach • When adding IPv6 to a system, do not delete IPv4 – This multi-protocol approach is familiar and well-understood (e.g., for AppleTalk, IPX, etc.) – In the majority of the cases, IPv6 is be bundled with all the OS release, not an extra-cost add-on • Applications (or libraries) choose IP version to use – when initiating, based on DNS response: • if (dest has AAAA record) use IPv6, else use IPv4 – when responding, based on version of initiating packet • This allows indefinite co-existence of IPv4 and IPv6, and gradual app-by-app upgrades to IPv6 usage • A6 record is experimental - 3 Dual-Stack Approach IPv6 IPv6 IPv4 IPv4 Application Application Application Application TCP/UDP TCP/UDP TCP/UDP IPv6 IPv6 IPv4 IPv4 IPv6-only stack Dual-stack (IPv4 & IPv6) IPv4-only stack IPv6 -

Data Communications & Networks Session 1
Data Communications & Networks Session 1 – Main Theme Introduction and Overview Dr. Jean-Claude Franchitti New York University Computer Science Department Courant Institute of Mathematical Sciences Adapted from course textbook resources Computer Networking: A Top-Down Approach, 5/E Copyright 1996-2009 J.F. Kurose and K.W. Ross, All Rights Reserved 1 Agenda 11 InstructorInstructor andand CourseCourse IntroductionIntroduction 22 IntroductionIntroduction andand OverviewOverview 33 SummarySummary andand ConclusionConclusion 2 Who am I? - Profile - 27 years of experience in the Information Technology Industry, including twelve years of experience working for leading IT consulting firms such as Computer Sciences Corporation PhD in Computer Science from University of Colorado at Boulder Past CEO and CTO Held senior management and technical leadership roles in many large IT Strategy and Modernization projects for fortune 500 corporations in the insurance, banking, investment banking, pharmaceutical, retail, and information management industries Contributed to several high-profile ARPA and NSF research projects Played an active role as a member of the OMG, ODMG, and X3H2 standards committees and as a Professor of Computer Science at Columbia initially and New York University since 1997 Proven record of delivering business solutions on time and on budget Original designer and developer of jcrew.com and the suite of products now known as IBM InfoSphere DataStage Creator of the Enterprise Architecture Management Framework (EAMF) and main -

Guidelines for the Secure Deployment of Ipv6
Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks NIST Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 December 2010 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Dr. Patrick D. Gallagher, Director GUIDELINES FOR THE SECURE DEPLOYMENT OF IPV6 Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-119 Natl. Inst. Stand. Technol. Spec. Publ. 800-119, 188 pages (Dec. 2010) Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. -
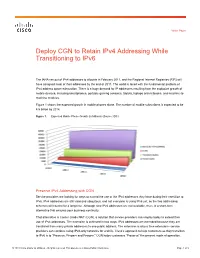
Deploy CGN to Retain Ipv4 Addressing While Transitioning to Ipv6
White Paper Deploy CGN to Retain IPv4 Addressing While Transitioning to IPv6 The IANA ran out of IPv4 addresses to allocate in February 2011, and the Regional Internet Registries (RIR) will have assigned most of their addresses by the end of 2011. The world is faced with the fundamental problem of IPv4 address space exhaustion. There is a huge demand for IP addresses resulting from the explosive growth of mobile devices, including smartphones, portable gaming consoles, tablets, laptops and netbooks, and machine-to- machine modules. Figure 1 shows the expected growth in mobile phones alone. The number of mobile subscribers is expected to be 4.5 billion by 2014. Figure 1. Expected Mobile Phone Growth (in Millions) (Source: IDC) Preserve IPv4 Addressing with CGN Service providers are looking for ways to extend the use of the IPv4 addresses they have during their transition to IPv6. IPv4 addresses are still valid and ubiquitous, and not everyone is using IPv6 yet, so the two addressing schemes will coexist for a long time. Although new IPv4 addresses are not available, there is a short-term alternative that ensures your business continuity. That alternative is Carrier Grade NAT (CGN), a solution that service providers can employ today to extend their use of IPv4 addresses. The extension is achieved in two ways: IPv4 addresses are extended because they are translated from many private addresses to one public address. The extension is also a time extension–-service providers can continue using IPv4-only networks for a while. Cisco’s approach to help customers as they transition to IPv6 is to “Preserve, Prepare and Prosper.” CGN helps customers “Preserve” the present mode of operation. -

Implications of Large Scale Network Address Translation (NAT)
Implications of Large Scale Network Address Translation (NAT) A BROADBAND INTERNET TECHNICAL ADVISORY GROUP TECHNICAL WORKING GROUP REPORT A Near-Uniform Agreement Report (100% Consensus Achieved) Issued: March 2012 Copyright / Legal Notice Copyright © Broadband Internet Technical Advisory Group, Inc. 2012. All rights reserved. This document may be reproduced and distributed to others so long as such reproduction or distribution complies with Broadband Internet Technical Advisory Group, Inc.’s Intellectual Property Rights Policy, available at www.bitag.org, and any such reproduction contains the above copyright notice and the other notices contained in this section. This document may not be modified in any way without the express written consent of the Broadband Internet Technical Advisory Group, Inc. This document and the information contained herein is provided on an “AS IS” basis and BITAG AND THE CONTRIBUTORS TO THIS REPORT MAKE NO (AND HEREBY EXPRESSLY DISCLAIM ANY) WARRANTIES (EXPRESS, IMPLIED OR OTHERWISE), INCLUDING IMPLIED WARRANTIES OF MERCHANTABILITY, NON-INFRINGEMENT, FITNESS FOR A PARTICULAR PURPOSE, OR TITLE, RELATED TO THIS REPORT, AND THE ENTIRE RISK OF RELYING UPON THIS REPORT OR IMPLEMENTING OR USING THE TECHNOLOGY DESCRIBED IN THIS REPORT IS ASSUMED BY THE USER OR IMPLEMENTER. The information contained in this Report was made available from contributions from various sources, including members of Broadband Internet Technical Advisory Group, Inc.’s Technical Working Group and others. Broadband Internet Technical Advisory Group, Inc. takes no position regarding the validity or scope of any intellectual property rights or other rights that might be claimed to pertain to the implementation or use of the technology described in this Report or the extent to which any license under such rights might or might not be available; nor does it represent that it has made any independent effort to identify any such rights. -

Internet Address Space: Economic Considerations in the Management of Ipv4”, OECD Digital Economy Papers, No
Please cite this paper as: OECD (2008-06-18), “Internet Address Space: Economic Considerations in the Management of IPv4”, OECD Digital Economy Papers, No. 145, OECD Publishing, Paris. http://dx.doi.org/10.1787/230461618475 OECD Digital Economy Papers No. 145 Internet Address Space ECONOMIC CONSIDERATIONS IN THE MANAGEMENT OF IPV4 OECD DSTI/ICCP(2007)20/FINAL FOREWORD The report provides an analysis of economic considerations associated with the transition from IPv4 to IPv6. It provides background analysis supporting the forthcoming ICCP-organised Ministerial-level meeting on ―The Future of the Internet Economy‖, to take place in Seoul, Korea on 17-18 June 2008. This report was prepared by Ms. Karine Perset of the OECD‘s Directorate for Science Technology and Industry. It was declassified by the ICCP Committee at its 54th Session on 5-7 March 2008. It is published under the responsibility of the Secretary-General of the OECD. This paper has greatly benefited from the expert input of Geoff Huston from APNIC, David Conrad from the IANA, Patrick Grossetête from CISCO Systems, Bill Woodcock from Packet Clearing House, Marcelo Bagnulo Braun from the University of Madrid, Alain Durand from Comcast, and Vincent Bataille from Mulot Déclic, although interpretations, unless otherwise stated, are those of the author. 2 DSTI/ICCP(2007)20/FINAL TABLE OF CONTENTS FOREWORD ................................................................................................................................................... 2 MAIN POINTS .............................................................................................................................................. -

Session 5: Data Link Control
Data Communications & Networks Session 4 – Main Theme Data Link Control Dr. Jean-Claude Franchitti New York University Computer Science Department Courant Institute of Mathematical Sciences Adapted from course textbook resources Computer Networking: A Top-Down Approach, 6/E Copyright 1996-2013 J.F. Kurose and K.W. Ross, All Rights Reserved 1 Agenda 1 Session Overview 2 Data Link Control 3 Summary and Conclusion 2 What is the class about? .Course description and syllabus: »http://www.nyu.edu/classes/jcf/csci-ga.2262-001/ »http://cs.nyu.edu/courses/Fall13/CSCI-GA.2262- 001/index.html .Textbooks: » Computer Networking: A Top-Down Approach (6th Edition) James F. Kurose, Keith W. Ross Addison Wesley ISBN-10: 0132856204, ISBN-13: 978-0132856201, 6th Edition (02/24/12) 3 Course Overview . Computer Networks and the Internet . Application Layer . Fundamental Data Structures: queues, ring buffers, finite state machines . Data Encoding and Transmission . Local Area Networks and Data Link Control . Wireless Communications . Packet Switching . OSI and Internet Protocol Architecture . Congestion Control and Flow Control Methods . Internet Protocols (IP, ARP, UDP, TCP) . Network (packet) Routing Algorithms (OSPF, Distance Vector) . IP Multicast . Sockets 4 Course Approach . Introduction to Basic Networking Concepts (Network Stack) . Origins of Naming, Addressing, and Routing (TCP, IP, DNS) . Physical Communication Layer . MAC Layer (Ethernet, Bridging) . Routing Protocols (Link State, Distance Vector) . Internet Routing (BGP, OSPF, Programmable Routers) . TCP Basics (Reliable/Unreliable) . Congestion Control . QoS, Fair Queuing, and Queuing Theory . Network Services – Multicast and Unicast . Extensions to Internet Architecture (NATs, IPv6, Proxies) . Network Hardware and Software (How to Build Networks, Routers) . Overlay Networks and Services (How to Implement Network Services) .