UNIT: 4 8086 INTERRUPTS: 8086 Interrupts and Interrupt Responses
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Microprocessor's Registers
IT Basics The microprocessor and ASM Prof. Răzvan Daniel Zota, Ph.D. Bucharest University of Economic Studies Faculty of Cybernetics, Statistics and Economic Informatics [email protected] http://zota.ase.ro/itb Contents • Basic microprocessor architecture • Intel microprocessor registers • Instructions – their components and format • Addressing modes (with examples) 2 Basic microprocessor architecture • CPU registers – Special memory locations on the microprocessor chip – Examples: accumulator, counter, FLAGS register • Arithmetic-Logic Unit (ALU) – The place where most of the operations are being made inside the CPU • Bus Interface Unit (BIU) – It controls data and address buses when the main memory is accessed (or data from the cache memory) • Control Unit and instruction set – The CPU has a fixed instruction set for working with (examples: MOV, CMP, JMP) 3 Instruction’s processing • Processing an instruction requires 3 basic steps: 1. Fetching the instruction from memory (fetch) 2. Instruction’s decoding (decode) 3. Instruction’s execution (execute) – implies memory access for the operands and storing the result • Operation mode of an “antique” Intel 8086 Fetch Decode Execute Fetch Decode Execute …... Microprocessor 1 1 1 2 2 2 Busy Idle Busy Busy Idle Busy …... Bus 4 Instruction’s processing • Modern microprocessors may process more instructions simultaneously (pipelining) • Operation of a pipeline microprocessor (from Intel 80486 to our days) Fetch Fetch Fetch Fetch Store Fetch Fetch Read Fetch 1 2 3 4 1 5 6 2 7 Bus Unit Decode Decode -

(PSW). Seven Bits Remain Unused While the Rest Nine Are Used
8086/8088MP INSTRUCTOR: ABDULMUTTALIB A. H. ALDOURI The Flags Register It is a 16-bit register, also called Program Status Word (PSW). Seven bits remain unused while the rest nine are used. Six are status flags and three are control flags. The control flags can be set/reset by the programmer. 1. DF (Direction Flag) : controls the direction of operation of string instructions. (DF=0 Ascending order DF=1 Descending order) 2. IF (Interrupt Flag): controls the interrupt operation in 8086µP. (IF=0 Disable interrupt IF=1 Enable interrupt) 3. TF (Trap Flag): controls the operation of the microprocessor. (TF=0 Normal operation TF=1 Single Step operation) The status flags are set/reset depending on the results of some arithmetic or logical operations during program execution. 1. CF (Carry Flag) is set (CF=1) if there is a carry out of the MSB position resulting from an addition operation or subtraction. 2. AF (Auxiliary Carry Flag) AF is set if there is a carry out of bit 3 resulting from an addition operation. 3. SF (Sign Flag) set to 1 when result is negative. When result is positive it is set to 0. 4. ZF (Zero Flag) is set (ZF=1) when result of an arithmetic or logical operation is zero. For non-zero result this flag is reset (ZF=0). 5. PF (Parity Flag) this flag is set to 1 when there is even number of one bits in result, and to 0 when there is odd number of one bits. 6. OF (Overflow Flag) set to 1 when there is a signed overflow. -
Assembly Language: IA-X86
Assembly Language for x86 Processors X86 Processor Architecture CS 271 Computer Architecture Purdue University Fort Wayne 1 Outline Basic IA Computer Organization IA-32 Registers Instruction Execution Cycle Basic IA Computer Organization Since the 1940's, the Von Neumann computers contains three key components: Processor, called also the CPU (Central Processing Unit) Memory and Storage Devices I/O Devices Interconnected with one or more buses Data Bus Address Bus data bus Control Bus registers Processor I/O I/O IA: Intel Architecture Memory Device Device (CPU) #1 #2 32-bit (or i386) ALU CU clock control bus address bus Processor The processor consists of Datapath ALU Registers Control unit ALU (Arithmetic logic unit) Performs arithmetic and logic operations Control unit (CU) Generates the control signals required to execute instructions Memory Address Space Address Space is the set of memory locations (bytes) that are addressable Next ... Basic Computer Organization IA-32 Registers Instruction Execution Cycle Registers Registers are high speed memory inside the CPU Eight 32-bit general-purpose registers Six 16-bit segment registers Processor Status Flags (EFLAGS) and Instruction Pointer (EIP) 32-bit General-Purpose Registers EAX EBP EBX ESP ECX ESI EDX EDI 16-bit Segment Registers EFLAGS CS ES SS FS EIP DS GS General-Purpose Registers Used primarily for arithmetic and data movement mov eax 10 ;move constant integer 10 into register eax Specialized uses of Registers eax – Accumulator register Automatically -

Design of the RISC-V Instruction Set Architecture
Design of the RISC-V Instruction Set Architecture Andrew Waterman Electrical Engineering and Computer Sciences University of California at Berkeley Technical Report No. UCB/EECS-2016-1 http://www.eecs.berkeley.edu/Pubs/TechRpts/2016/EECS-2016-1.html January 3, 2016 Copyright © 2016, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. Design of the RISC-V Instruction Set Architecture by Andrew Shell Waterman A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate Division of the University of California, Berkeley Committee in charge: Professor David Patterson, Chair Professor Krste Asanovi´c Associate Professor Per-Olof Persson Spring 2016 Design of the RISC-V Instruction Set Architecture Copyright 2016 by Andrew Shell Waterman 1 Abstract Design of the RISC-V Instruction Set Architecture by Andrew Shell Waterman Doctor of Philosophy in Computer Science University of California, Berkeley Professor David Patterson, Chair The hardware-software interface, embodied in the instruction set architecture (ISA), is arguably the most important interface in a computer system. Yet, in contrast to nearly all other interfaces in a modern computer system, all commercially popular ISAs are proprietary. -
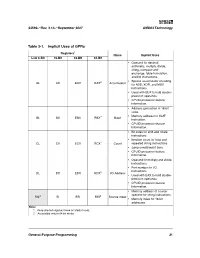
Implicitly Modified Registers
24592—Rev. 3.14—September 2007 AMD64 Technology Table 3-1. Implicit Uses of GPRs Registers 1 Name Implicit Uses Low 8-Bit 16-Bit 32-Bit 64-Bit • Operand for decimal arithmetic, multiply, divide, string, compare-and- exchange, table-translation, and I/O instructions. 2 • Special accumulator encoding AL AX EAX RAX Accumulator for ADD, XOR, and MOV instructions. • Used with EDX to hold double- precision operands. • CPUID processor-feature information. • Address generation in 16-bit code. • Memory address for XLAT BL BX EBX RBX 2 Base instruction. • CPUID processor-feature information. • Bit index for shift and rotate instructions. • Iteration count for loop and CL CX ECX RCX 2 Count repeated string instructions. • Jump conditional if zero. • CPUID processor-feature information. • Operand for multiply and divide instructions. • Port number for I/O instructions. DL DX EDX RDX 2 I/O Address • Used with EAX to hold double- precision operands. • CPUID processor-feature information. • Memory address of source operand for string instructions. SIL 2 SI ESI RSI 2 Source Index • Memory index for 16-bit addresses. Note: 1. Gray-shaded registers have no implicit uses. 2. Accessible only in 64-bit mode. General-Purpose Programming 31 AMD64 Technology 24592—Rev. 3.14—September 2007 Table 3-1. Implicit Uses of GPRs (continued) Registers 1 Name Implicit Uses Low 8-Bit 16-Bit 32-Bit 64-Bit • Memory address of destination Destination operand for string instructions. DIL 2 DI EDI RDI 2 Index • Memory index for 16-bit addresses. • Memory address of stack- BPL 2 BP EBP RBP 2 Base Pointer frame base pointer. -

Assembly Language Tutorial
Assembly Language Tutorial ASSEMBLY LANGUAGE TUTORIAL Simply Easy Learning by tutorialspoint.com tutorialspoint.com i ABOUT THE TUTORIAL Assembly Programming Tutorial Assembly language is a low-level programming language for a computer, or other programmable device specific to a particular computer architecture in contrast to most high- level programming languages, which are generally portable across multiple systems. Assembly language is converted into executable machine code by a utility program referred to as an assembler like NASM, MASM etc. Audience This tutorial has been designed for software programmers with a need to understand the Assembly programming language starting from scratch. This tutorial will give you enough understanding on Assembly programming language from where you can take yourself at higher level of expertise. Prerequisites Before proceeding with this tutorial you should have a basic understanding of Computer Programming terminologies. A basic understanding of any of the programming languages will help you in understanding the Assembly programming concepts and move fast on the learning track. TUTORIALS POINT Simply Easy Learning Copyright & Disclaimer Notice All the content and graphics on this tutorial are the property of tutorialspoint.com. Any content from tutorialspoint.com or this tutorial may not be redistributed or reproduced in any way, shape, or form without the written permission of tutorialspoint.com. Failure to do so is a violation of copyright laws. This tutorial may contain inaccuracies or errors and tutorialspoint provides no guarantee regarding the accuracy of the site or its contents including this tutorial. If you discover that the tutorialspoint.com site or this tutorial content contains some errors, please contact us at [email protected] TUTORIALS POINT Simply Easy Learning Table of Content Assembly Programming Tutorial ............................................. -

Lecture Notes in Assembly Language Piotr Fulmański
Uniwersytet Łódzki Wydział Matematyki i Informatyki Informatyka Lecture Notes in Assembly Language Short introduction to low-level programming Piotr Fulmański Łódź, 2013 Spis treści Spis treści iii 1 Before we begin1 1.1 Simple assembler.................................... 1 1.1.1 Excercise 1 ................................... 2 1.1.2 Excercise 2 ................................... 2 1.1.3 Excercise 3 ................................... 3 1.1.4 Excercise 4 ................................... 5 1.2 Improvements, part I.................................. 6 1.2.1 Excercise 5 ................................... 9 1.3 Improvements, part II ................................. 9 1.3.1 Solution 5.2.2 – bad second approach..................... 14 1.4 Improvements, part III................................. 16 1.4.1 Excercise 6 ................................... 17 1.5 Improvements, part IV................................. 19 1.5.1 Excercise 6 – second approach ........................ 19 1.5.2 Excercise 7 ................................... 19 1.5.3 Excercise 8 ................................... 20 1.6 Improvements, part V ................................. 20 1.6.1 Excercise 9 ................................... 20 1.6.2 Excercise 10................................... 21 1.7 Other excercises .................................... 21 1.7.1 Excercise 11................................... 21 1.7.2 Excercise x ................................... 22 iii iv SPIS TREŚCI 1.7.3 Excercise x ................................... 22 1.7.4 Excercise x .................................. -

Term 2 Lecture 6
Assembly Language J. Vaughan Lecture Notes on Assembly Language - J. Vaughan 13. Instructions and data (ctd) From the NASM Manual: AND: Bitwise AND AND r/m8,reg8 ; 20 /r [8086] AND r/m16,reg16 ; o16 21 /r [8086] AND r/m32,reg32 ; o32 21 /r [386] AND reg8,r/m8 ; 22 /r [8086] AND reg16,r/m16 ; o16 23 /r [8086] AND reg32,r/m32 ; o32 23 /r [386] AND r/m8,imm8 ; 80 /4 ib [8086] AND r/m16,imm16 ; o16 81 /4 iw [8086] AND r/m32,imm32 ; o32 81 /4 id [386] AND r/m16,imm8 ; o16 83 /4 ib [8086] AND r/m32,imm8 ; o32 83 /4 ib [386] AND AL,imm8 ; 24 ib [8086] AND AX,imm16 ; o16 25 iw [8086] AND EAX,imm32 ; o32 25 id [386] AND performs a bitwise AND operation between its two operands (i.e. each bit of the result is 1 if and only if the corresponding bits of the two inputs were both 1), and stores the result in the destination (first) operand. The destination operand can be a register or a memory location. The source operand can be a register, a memory location or an immediate value. In the forms with an 8−bit immediate second operand and a longer first operand, the second operand is considered to be signed, and is sign−extended to the length of the first operand. In these cases, the BYTE qualifier is necessary to force NASM to generate this form of the instruction. CALL: Call Subroutine CALL imm ; E8 rw/rd [8086] CALL imm:imm16 ; o16 9A iw iw [8086] CALL imm:imm32 ; o32 9A id iw [386] CALL FAR mem16 ; o16 FF /3 [8086] CALL FAR mem32 ; o32 FF /3 [386] CALL r/m16 ; o16 FF /2 [8086] CALL r/m32 ; o32 FF /2 [386] CALL calls a subroutine, by means of pushing the current instruction pointer (IP) and optionally CS as well on the stack, and then jumping to a given address. -

X86 Assembly Language Reference Manual
x86 Assembly Language Reference Manual Sun Microsystems, Inc. 901 N. San Antonio Road Palo Alto, CA 94303-4900 U.S.A. Part No: 805-4693-10 October 1998 Copyright 1998 Sun Microsystems, Inc. 901 San Antonio Road, Palo Alto, California 94303-4900 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, SunDocs, Java, the Java Coffee Cup logo, and Solaris are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. The OPEN LOOK and SunTM Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user interfaces for the computer industry. Sun holds a non-exclusive license from Xerox to the Xerox Graphical User Interface, which license also covers Sun’s licensees who implement OPEN LOOK GUIs and otherwise comply with Sun’s written license agreements. -

Embedded Intel486™ Processor Family Developer's Manual
Embedded Intel486™ Processor Family Developer’s Manual Release Date: October 1997 Order Number: 273021-001 The Intel486™ processors may contain design defects known as errata which may cause the products to deviate from published specifications. Currently characterized errata are avail- able on request. Information in this document is provided in connection with Intel products. No license, express or implied, by estoppel or oth- erwise, to any intellectual property rights is granted by this document. Except as provided in Intel’s Terms and Conditions of Sale for such products, Intel assumes no liability whatsoever, and Intel disclaims any express or implied warranty, relating to sale and/or use of Intel products including liability or warranties relating to fitness for a particular purpose, merchantability, or infringement of any patent, copyright or other intellectual property right. Intel products are not intended for use in medical, life saving, or life sustaining applications. Intel retains the right to make changes to specifications and product descriptions at any time, without notice. Contact your local Intel sales office or your distributor to obtain the latest specifications and before placing your product order. *Third-party brands and names are the property of their respective owners. Copies of documents which have an ordering number and are referenced in this document, or other Intel literature, may be obtained from: Intel Corporation P.O. Box 5937 Denver, CO 80217-9808 or call 1-800-548-4725 or visit Intel’s website at http:\\www.intel.com Copyright © INTEL CORPORATION, October 1997 CONTENTS CHAPTER 1 GUIDE TO THIS MANUAL 1.1 MANUAL CONTENTS ................................................................................................. -

Intel Processor Identification and the CPUID Instruction
E AP-485 APPLICATION NOTE Intel Processor Identification and the CPUID Instruction January 1999 Order Number : 241618-012 1/14/99 2:13 PM CPUID INTEL CONFIDENTIAL (until publication date) Information in this document is provided in connection with Intel products. No license, express or implied, by estoppel or otherwise, to any intellectual property rights is granted by this document. Except as provided in Intel’s Terms and Conditions of Sale for such products, Intel assumes no liability whatsoever, and Intel disclaims any express or implied warranty, relating to sale and/or use of Intel products including liability or warranties relating to fitness for a particular purpose, merchantability, or infringement of any patent, copyright or other intellectual property right. Intel products are not intended for use in medical, life saving, or life sustaining applications. Intel may make changes to specifications and product descriptions at any time, without notice. Designers must not rely on the absence or characteristics of any features or instructions marked “reserved” or “undefined.” Intel reserves these for future definition and shall have no responsibility whatsoever for conflicts or incompatibilities arising from future changes to them. Intel’s Intel Architecture processors (e.g., Pentium® processor, Pentium processor with MMX™ technology, Pentium Pro processor, Pentium II processor, Pentium II Xeon™ processor, Intel Celeron™ processor, Pentium III processor and Pentium III Xeon processor) may contain design defects or errors known as errata which may cause the product to deviate from published specifications. Current characterized errata are available on request. Contact your local Intel sales office or your distributor to obtain the latest specifications and before placing your product order. -

FLAGS Register (Computing) - Wikipedia, the Free Encyclopedia Page 1 of 3
FLAGS register (computing) - Wikipedia, the free encyclopedia Page 1 of 3 FLAGS register (computing) From Wikipedia, the free encyclopedia This article discusses the flag register specific to the x86 architecture. For a general discussion about flag registers, see status register. The FLAGS register is the status register in Intel x86 microprocessors that contains the current state of the processor. This register is 16 bits wide. Its successors, the EFLAGS and RFLAGS registers are 32 bits and 64 bits wide, respectively. The wider registers retain compatibility with their smaller predecessors. Intel x86 FLAGS Register Bit # Abbreviation Description Category [1] FLAGS 0 CF Carry flag S 1 1 Reserved 2 PF Parity flag S 3 0 Reserved 4 AF Adjust flag S 5 0 Reserved 6 ZF Zero flag S 7 SF Sign flag S 8 TF Trap flag (single step) X 9 IF Interrupt enable flag X 10 DF Direction flag C 11 OF Overflow flag S 12, 13 IOPL I/O privilege level (286+ only) X 14 NT Nested task flag (286+ only) X 15 0 Reserved EFLAGS 16 RF Resume flag (386+ only) X 17 VM Virtual 8086 mode flag (386+ only) X 18 AC Alignment check (486SX+ only) X 19 VIF Virtual interrupt flag (Pentium+) X 20 VIP Virtual interrupt pending (Pentium+) X 21 ID Identification (Pentium+) X 22 0 Reserved http://en.wikipedia.org/wiki/FLAGS_register_(computing) 9/22/2010 FLAGS register (computing) - Wikipedia, the free encyclopedia Page 2 of 3 23 0 Reserved 24 0 Reserved 25 0 Reserved 26 0 Reserved 27 0 Reserved 28 0 Reserved 29 0 Reserved 30 0 Reserved 31 0 Reserved RFLAGS 32-63 0 Reserved 1.