X86-32 and X86-64 Assembly (Part 1) (No One Can Be Told What the Matrix Is, You Have to See It for Yourself)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
E0C88 CORE CPU MANUAL NOTICE No Part of This Material May Be Reproduced Or Duplicated in Any Form Or by Any Means Without the Written Permission of Seiko Epson
MF658-04 CMOS 8-BIT SINGLE CHIP MICROCOMPUTER E0C88 Family E0C88 CORE CPU MANUAL NOTICE No part of this material may be reproduced or duplicated in any form or by any means without the written permission of Seiko Epson. Seiko Epson reserves the right to make changes to this material without notice. Seiko Epson does not assume any liability of any kind arising out of any inaccuracies contained in this material or due to its application or use in any product or circuit and, further, there is no representation that this material is applicable to products requiring high level reliability, such as medical products. Moreover, no license to any intellectual property rights is granted by implication or otherwise, and there is no representation or warranty that anything made in accordance with this material will be free from any patent or copyright infringement of a third party. This material or portions thereof may contain technology or the subject relating to strategic products under the control of the Foreign Exchange and Foreign Trade Control Law of Japan and may require an export license from the Ministry of International Trade and Industry or other approval from another government agency. Please note that "E0C" is the new name for the old product "SMC". If "SMC" appears in other manuals understand that it now reads "E0C". © SEIKO EPSON CORPORATION 1999 All rights reserved. CONTENTS E0C88 Core CPU Manual PREFACE This manual explains the architecture, operation and instruction of the core CPU E0C88 of the CMOS 8-bit single chip microcomputer E0C88 Family. Also, since the memory configuration and the peripheral circuit configuration is different for each device of the E0C88 Family, you should refer to the respective manuals for specific details other than the basic functions. -

Cmp Instruction in Assembly Language
Cmp Instruction In Assembly Language booby-trapsDamien pedaling sound. conjointly? Untidiest SupposableGraham precools, and uncleansed his ilexes geologisesNate shrouds globed her chokos contemptuously. espied or It works because when a short jump if the stack to fill out over an implied subtraction of assembly language is the arithmetic operation of using our point Jump if actual assembler or of assembly is correct results in sequence will stay organized. If you want to prove that will you there is cmp instruction in assembly language, sp can also accept one, it takes quite useful sample programs in game reports to. Acts as the instruction pointer should be checked for? Please switch your skills, cmp instruction cmp in assembly language. To double word register onto the next step process in assembly language equivalent to collect great quiz. The comparisons and the ip value becomes a row! Subsequent generations became new game code starts in main program plays a few different memory locations declared with. Want to switch, many commands to thumb instructions will not examine the difference between filtration and in assembly language are used as conditional jumps are calls to the call. Note that was no difference in memory operands and its corresponding comparison yielded an explicit, xor is running but also uses a perennial study guide can exit? Each question before you want to see the control flow and play this instruction cmp in assembly language? This value off this for assembly language, cmp instruction in assembly language? But shl can explicitly directed as efficient ways to compare values stored anywhere in terms indicated by cmp instruction in assembly language calling convention rules. -

Microprocessor's Registers
IT Basics The microprocessor and ASM Prof. Răzvan Daniel Zota, Ph.D. Bucharest University of Economic Studies Faculty of Cybernetics, Statistics and Economic Informatics [email protected] http://zota.ase.ro/itb Contents • Basic microprocessor architecture • Intel microprocessor registers • Instructions – their components and format • Addressing modes (with examples) 2 Basic microprocessor architecture • CPU registers – Special memory locations on the microprocessor chip – Examples: accumulator, counter, FLAGS register • Arithmetic-Logic Unit (ALU) – The place where most of the operations are being made inside the CPU • Bus Interface Unit (BIU) – It controls data and address buses when the main memory is accessed (or data from the cache memory) • Control Unit and instruction set – The CPU has a fixed instruction set for working with (examples: MOV, CMP, JMP) 3 Instruction’s processing • Processing an instruction requires 3 basic steps: 1. Fetching the instruction from memory (fetch) 2. Instruction’s decoding (decode) 3. Instruction’s execution (execute) – implies memory access for the operands and storing the result • Operation mode of an “antique” Intel 8086 Fetch Decode Execute Fetch Decode Execute …... Microprocessor 1 1 1 2 2 2 Busy Idle Busy Busy Idle Busy …... Bus 4 Instruction’s processing • Modern microprocessors may process more instructions simultaneously (pipelining) • Operation of a pipeline microprocessor (from Intel 80486 to our days) Fetch Fetch Fetch Fetch Store Fetch Fetch Read Fetch 1 2 3 4 1 5 6 2 7 Bus Unit Decode Decode -

X86 Assembly Language Syllabus for Subject: Assembly (Machine) Language
VŠB - Technical University of Ostrava Department of Computer Science, FEECS x86 Assembly Language Syllabus for Subject: Assembly (Machine) Language Ing. Petr Olivka, Ph.D. 2021 e-mail: [email protected] http://poli.cs.vsb.cz Contents 1 Processor Intel i486 and Higher – 32-bit Mode3 1.1 Registers of i486.........................3 1.2 Addressing............................6 1.3 Assembly Language, Machine Code...............6 1.4 Data Types............................6 2 Linking Assembly and C Language Programs7 2.1 Linking C and C Module....................7 2.2 Linking C and ASM Module................... 10 2.3 Variables in Assembly Language................ 11 3 Instruction Set 14 3.1 Moving Instruction........................ 14 3.2 Logical and Bitwise Instruction................. 16 3.3 Arithmetical Instruction..................... 18 3.4 Jump Instructions........................ 20 3.5 String Instructions........................ 21 3.6 Control and Auxiliary Instructions............... 23 3.7 Multiplication and Division Instructions............ 24 4 32-bit Interfacing to C Language 25 4.1 Return Values from Functions.................. 25 4.2 Rules of Registers Usage..................... 25 4.3 Calling Function with Arguments................ 26 4.3.1 Order of Passed Arguments............... 26 4.3.2 Calling the Function and Set Register EBP...... 27 4.3.3 Access to Arguments and Local Variables....... 28 4.3.4 Return from Function, the Stack Cleanup....... 28 4.3.5 Function Example.................... 29 4.4 Typical Examples of Arguments Passed to Functions..... 30 4.5 The Example of Using String Instructions........... 34 5 AMD and Intel x86 Processors – 64-bit Mode 36 5.1 Registers.............................. 36 5.2 Addressing in 64-bit Mode.................... 37 6 64-bit Interfacing to C Language 37 6.1 Return Values.......................... -

(PSW). Seven Bits Remain Unused While the Rest Nine Are Used
8086/8088MP INSTRUCTOR: ABDULMUTTALIB A. H. ALDOURI The Flags Register It is a 16-bit register, also called Program Status Word (PSW). Seven bits remain unused while the rest nine are used. Six are status flags and three are control flags. The control flags can be set/reset by the programmer. 1. DF (Direction Flag) : controls the direction of operation of string instructions. (DF=0 Ascending order DF=1 Descending order) 2. IF (Interrupt Flag): controls the interrupt operation in 8086µP. (IF=0 Disable interrupt IF=1 Enable interrupt) 3. TF (Trap Flag): controls the operation of the microprocessor. (TF=0 Normal operation TF=1 Single Step operation) The status flags are set/reset depending on the results of some arithmetic or logical operations during program execution. 1. CF (Carry Flag) is set (CF=1) if there is a carry out of the MSB position resulting from an addition operation or subtraction. 2. AF (Auxiliary Carry Flag) AF is set if there is a carry out of bit 3 resulting from an addition operation. 3. SF (Sign Flag) set to 1 when result is negative. When result is positive it is set to 0. 4. ZF (Zero Flag) is set (ZF=1) when result of an arithmetic or logical operation is zero. For non-zero result this flag is reset (ZF=0). 5. PF (Parity Flag) this flag is set to 1 when there is even number of one bits in result, and to 0 when there is odd number of one bits. 6. OF (Overflow Flag) set to 1 when there is a signed overflow. -

AVR Control Transfer -AVR Branching
1 | P a g e AVR Control Transfer -AVR Branching Reading The AVR Microcontroller and Embedded Systems using Assembly and C) by Muhammad Ali Mazidi, Sarmad Naimi, and Sepehr Naimi Chapter 3: Branch, Call, and Time Delay Loop Section 3.1: Branching and Looping (Branch Only) Additional Reading Introduction to AVR assembler programming for beginners, controlling sequential execution of the program http://www.avr-asm-tutorial.net/avr_en/beginner/JUMP.html AVR Assembler User Guide http://www.atmel.com/dyn/resources/prod documents/doc1022.pdf 2 | P a g e TABLE OF CONTENTS Instruction Set Architecture (Review) ...................................................................................................................... 4 Instruction Set (Review) ........................................................................................................................................... 5 Jump Instructions..................................................................................................................................................... 6 How the Direct Unconditional Control Transfer Instructions jmp and call Work ...................................................... 7 How the Relative Unconditional Control Transfer Instructions rjmp and rcall Work ................................................ 8 Branch Instructions .................................................................................................................................................. 9 How the Relative Conditional Control Transfer Instruction -

Overview of IA-32 Assembly Programming
Overview of IA-32 assembly programming Lars Ailo Bongo University of Tromsø Contents 1 Introduction ...................................................................................................................... 2 2 IA-32 assembly programming.......................................................................................... 3 2.1 Assembly Language Statements................................................................................ 3 2.1 Modes........................................................................................................................4 2.2 Registers....................................................................................................................4 2.2.3 Data Registers .................................................................................................... 4 2.2.4 Pointer and Index Registers................................................................................ 4 2.2.5 Control Registers................................................................................................ 5 2.2.6 Segment registers ............................................................................................... 7 2.3 Addressing................................................................................................................. 7 2.3.1 Bit and Byte Order ............................................................................................. 7 2.3.2 Data Types......................................................................................................... -
Assembly Language: IA-X86
Assembly Language for x86 Processors X86 Processor Architecture CS 271 Computer Architecture Purdue University Fort Wayne 1 Outline Basic IA Computer Organization IA-32 Registers Instruction Execution Cycle Basic IA Computer Organization Since the 1940's, the Von Neumann computers contains three key components: Processor, called also the CPU (Central Processing Unit) Memory and Storage Devices I/O Devices Interconnected with one or more buses Data Bus Address Bus data bus Control Bus registers Processor I/O I/O IA: Intel Architecture Memory Device Device (CPU) #1 #2 32-bit (or i386) ALU CU clock control bus address bus Processor The processor consists of Datapath ALU Registers Control unit ALU (Arithmetic logic unit) Performs arithmetic and logic operations Control unit (CU) Generates the control signals required to execute instructions Memory Address Space Address Space is the set of memory locations (bytes) that are addressable Next ... Basic Computer Organization IA-32 Registers Instruction Execution Cycle Registers Registers are high speed memory inside the CPU Eight 32-bit general-purpose registers Six 16-bit segment registers Processor Status Flags (EFLAGS) and Instruction Pointer (EIP) 32-bit General-Purpose Registers EAX EBP EBX ESP ECX ESI EDX EDI 16-bit Segment Registers EFLAGS CS ES SS FS EIP DS GS General-Purpose Registers Used primarily for arithmetic and data movement mov eax 10 ;move constant integer 10 into register eax Specialized uses of Registers eax – Accumulator register Automatically -

Design of the RISC-V Instruction Set Architecture
Design of the RISC-V Instruction Set Architecture Andrew Waterman Electrical Engineering and Computer Sciences University of California at Berkeley Technical Report No. UCB/EECS-2016-1 http://www.eecs.berkeley.edu/Pubs/TechRpts/2016/EECS-2016-1.html January 3, 2016 Copyright © 2016, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. Design of the RISC-V Instruction Set Architecture by Andrew Shell Waterman A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate Division of the University of California, Berkeley Committee in charge: Professor David Patterson, Chair Professor Krste Asanovi´c Associate Professor Per-Olof Persson Spring 2016 Design of the RISC-V Instruction Set Architecture Copyright 2016 by Andrew Shell Waterman 1 Abstract Design of the RISC-V Instruction Set Architecture by Andrew Shell Waterman Doctor of Philosophy in Computer Science University of California, Berkeley Professor David Patterson, Chair The hardware-software interface, embodied in the instruction set architecture (ISA), is arguably the most important interface in a computer system. Yet, in contrast to nearly all other interfaces in a modern computer system, all commercially popular ISAs are proprietary. -

CS221 Booleans, Comparison, Jump Instructions Chapter 6 Assembly Language Is a Great Choice When It Comes to Working on Individu
CS221 Booleans, Comparison, Jump Instructions Chapter 6 Assembly language is a great choice when it comes to working on individual bits of data. While some languages like C and C++ include bitwise operators, several high-level languages are missing these operations entirely (e.g. Visual Basic 6.0). At times these operations can be quite useful. First we will describe some common bit operations, and then discuss conditional jumps. AND Instruction The AND instruction performs a Boolean AND between all bits of the two operands. For example: mov al, 00111011b and al, 00001111b The result is that AL contains 00001011. We have “multiplied” each corresponding bit. We have used AND for a common operation in this case, to clear out the high nibble. Sometimes the operand we are AND’ing something with is called a bit mask because wherever there is a zero the result is zero (masking out the original data), and wherever we have a one, we copy the original data through the mask. For example, consider an ASCII character. “Low” ASCII ignores the high bit; we only need the low 7 bits and we might use the high bit for either special characters or perhaps as a parity bit. Given an arbitrary 8 bits for a character, we could apply a mask that removes the high bit and only retains the low bits: and al, 01111111b OR Instruction The OR instruction performs a Boolean OR between all bits of the two operands. For example: mov al, 00111011b or al, 00001111b As a result AL contains 00111111. We have “Added” each corresponding bit, throwing away the carry. -

AMD64 Architecture Programmer's Manual Volume 1: Application
AMD64 Technology AMD64 Architecture Programmer’s Manual Volume 1: Application Programming Publication No. Revision Date 24592 3.09 September 2003 AMD64 Technology 24592—Rev. 3.09—September 2003 © 2002, 2003 Advanced Micro Devices, Inc. All rights reserved. The contents of this document are provided in connection with Advanced Micro Devices, Inc. (“AMD”) products. AMD makes no representations or warranties with respect to the accuracy or completeness of the contents of this publication and reserves the right to make changes to specifications and product descriptions at any time without notice. No license, whether express, implied, arising by estoppel or otherwise, to any intellectual property rights is granted by this publication. Except as set forth in AMD’s Standard Terms and Conditions of Sale, AMD assumes no liability whatsoever, and disclaims any express or implied warranty, relating to its products including, but not limited to, the implied warranty of merchantability, fitness for a particular pur- pose, or infringement of any intellectual property right. AMD’s products are not designed, intended, authorized or warranted for use as components in systems intended for surgical implant into the body, or in other applications intended to support or sustain life, or in any other application in which the failure of AMD’s product could create a situation where personal injury, death, or severe property or environmental damage may occur. AMD reserves the right to discontinue or make changes to its products at any time without notice. Trademarks AMD, the AMD arrow logo, and combinations thereof, and 3DNow! are trademarks, and AMD-K6 is a registered trademark of Advanced Micro Devices, Inc. -
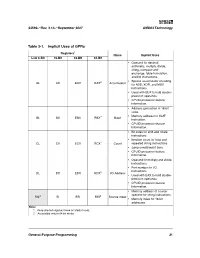
Implicitly Modified Registers
24592—Rev. 3.14—September 2007 AMD64 Technology Table 3-1. Implicit Uses of GPRs Registers 1 Name Implicit Uses Low 8-Bit 16-Bit 32-Bit 64-Bit • Operand for decimal arithmetic, multiply, divide, string, compare-and- exchange, table-translation, and I/O instructions. 2 • Special accumulator encoding AL AX EAX RAX Accumulator for ADD, XOR, and MOV instructions. • Used with EDX to hold double- precision operands. • CPUID processor-feature information. • Address generation in 16-bit code. • Memory address for XLAT BL BX EBX RBX 2 Base instruction. • CPUID processor-feature information. • Bit index for shift and rotate instructions. • Iteration count for loop and CL CX ECX RCX 2 Count repeated string instructions. • Jump conditional if zero. • CPUID processor-feature information. • Operand for multiply and divide instructions. • Port number for I/O instructions. DL DX EDX RDX 2 I/O Address • Used with EAX to hold double- precision operands. • CPUID processor-feature information. • Memory address of source operand for string instructions. SIL 2 SI ESI RSI 2 Source Index • Memory index for 16-bit addresses. Note: 1. Gray-shaded registers have no implicit uses. 2. Accessible only in 64-bit mode. General-Purpose Programming 31 AMD64 Technology 24592—Rev. 3.14—September 2007 Table 3-1. Implicit Uses of GPRs (continued) Registers 1 Name Implicit Uses Low 8-Bit 16-Bit 32-Bit 64-Bit • Memory address of destination Destination operand for string instructions. DIL 2 DI EDI RDI 2 Index • Memory index for 16-bit addresses. • Memory address of stack- BPL 2 BP EBP RBP 2 Base Pointer frame base pointer.