Ez8 CPU User Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Automatic Extraction of X86 Formal Semantics from Its Natural Language Description
Automatic extraction of x86 formal semantics from its natural language description NGUYEN, Lam Hoang Yen Graduate School of Advanced Science and Technology Japan Advanced Institute of Science and Technology March, 2018 Master's Thesis Automatic extraction of x86 formal semantics from its natural language description 1610062 NGUYEN, Lam Hoang Yen Supervisor : Professor Mizuhito Ogawa Main Examiner : Professor Mizuhito Ogawa Examiners : Associate Professor Nguyen Minh Le Professor Kazuhiro Ogata Associate Professor Nao Hirokawa Graduate School of Advanced Science and Technology Japan Advanced Institute of Science and Technology [Information Science] February, 2018 Abstract Nowadays, computers have become an essential device of almost every activity for every- body at any age. From personal demands to industrial and business sectors, they are used to improve human life as well as the efficiency and the productivity. The more important they are, the more attractive target they become for being attacked and serving malicious purposes. There are various threats to a computer system. One of the most common manners that penetrates or damages a system with bad impacts to most of the computer users is malware. Malware detection and malware classification are two of the most at- tractive problems in not only industry area but also academic research. The bits-based fingerprint also known as the signature-based pattern recognition is applied popularly in commercial anti-virus software due to its light-weight and fast features. However, it is easily cheated by advanced polymorphic techniques in malware. Therefore, malware analyses based on control flow graph (CFG) have been attracting a lot of attention, e.g., VxClass at Google. -

Lecture Notes in Assembly Language
Lecture Notes in Assembly Language Short introduction to low-level programming Piotr Fulmański Łódź, 12 czerwca 2015 Spis treści Spis treści iii 1 Before we begin1 1.1 Simple assembler.................................... 1 1.1.1 Excercise 1 ................................... 2 1.1.2 Excercise 2 ................................... 3 1.1.3 Excercise 3 ................................... 3 1.1.4 Excercise 4 ................................... 5 1.1.5 Excercise 5 ................................... 6 1.2 Improvements, part I: addressing........................... 8 1.2.1 Excercise 6 ................................... 11 1.3 Improvements, part II: indirect addressing...................... 11 1.4 Improvements, part III: labels............................. 18 1.4.1 Excercise 7: find substring in a string .................... 19 1.4.2 Excercise 8: improved polynomial....................... 21 1.5 Improvements, part IV: flag register ......................... 23 1.6 Improvements, part V: the stack ........................... 24 1.6.1 Excercise 12................................... 26 1.7 Improvements, part VI – function stack frame.................... 29 1.8 Finall excercises..................................... 34 1.8.1 Excercise 13................................... 34 1.8.2 Excercise 14................................... 34 1.8.3 Excercise 15................................... 34 1.8.4 Excercise 16................................... 34 iii iv SPIS TREŚCI 1.8.5 Excercise 17................................... 34 2 First program 37 2.1 Compiling, -

Microprocessor's Registers
IT Basics The microprocessor and ASM Prof. Răzvan Daniel Zota, Ph.D. Bucharest University of Economic Studies Faculty of Cybernetics, Statistics and Economic Informatics [email protected] http://zota.ase.ro/itb Contents • Basic microprocessor architecture • Intel microprocessor registers • Instructions – their components and format • Addressing modes (with examples) 2 Basic microprocessor architecture • CPU registers – Special memory locations on the microprocessor chip – Examples: accumulator, counter, FLAGS register • Arithmetic-Logic Unit (ALU) – The place where most of the operations are being made inside the CPU • Bus Interface Unit (BIU) – It controls data and address buses when the main memory is accessed (or data from the cache memory) • Control Unit and instruction set – The CPU has a fixed instruction set for working with (examples: MOV, CMP, JMP) 3 Instruction’s processing • Processing an instruction requires 3 basic steps: 1. Fetching the instruction from memory (fetch) 2. Instruction’s decoding (decode) 3. Instruction’s execution (execute) – implies memory access for the operands and storing the result • Operation mode of an “antique” Intel 8086 Fetch Decode Execute Fetch Decode Execute …... Microprocessor 1 1 1 2 2 2 Busy Idle Busy Busy Idle Busy …... Bus 4 Instruction’s processing • Modern microprocessors may process more instructions simultaneously (pipelining) • Operation of a pipeline microprocessor (from Intel 80486 to our days) Fetch Fetch Fetch Fetch Store Fetch Fetch Read Fetch 1 2 3 4 1 5 6 2 7 Bus Unit Decode Decode -

(PSW). Seven Bits Remain Unused While the Rest Nine Are Used
8086/8088MP INSTRUCTOR: ABDULMUTTALIB A. H. ALDOURI The Flags Register It is a 16-bit register, also called Program Status Word (PSW). Seven bits remain unused while the rest nine are used. Six are status flags and three are control flags. The control flags can be set/reset by the programmer. 1. DF (Direction Flag) : controls the direction of operation of string instructions. (DF=0 Ascending order DF=1 Descending order) 2. IF (Interrupt Flag): controls the interrupt operation in 8086µP. (IF=0 Disable interrupt IF=1 Enable interrupt) 3. TF (Trap Flag): controls the operation of the microprocessor. (TF=0 Normal operation TF=1 Single Step operation) The status flags are set/reset depending on the results of some arithmetic or logical operations during program execution. 1. CF (Carry Flag) is set (CF=1) if there is a carry out of the MSB position resulting from an addition operation or subtraction. 2. AF (Auxiliary Carry Flag) AF is set if there is a carry out of bit 3 resulting from an addition operation. 3. SF (Sign Flag) set to 1 when result is negative. When result is positive it is set to 0. 4. ZF (Zero Flag) is set (ZF=1) when result of an arithmetic or logical operation is zero. For non-zero result this flag is reset (ZF=0). 5. PF (Parity Flag) this flag is set to 1 when there is even number of one bits in result, and to 0 when there is odd number of one bits. 6. OF (Overflow Flag) set to 1 when there is a signed overflow. -
Assembly Language: IA-X86
Assembly Language for x86 Processors X86 Processor Architecture CS 271 Computer Architecture Purdue University Fort Wayne 1 Outline Basic IA Computer Organization IA-32 Registers Instruction Execution Cycle Basic IA Computer Organization Since the 1940's, the Von Neumann computers contains three key components: Processor, called also the CPU (Central Processing Unit) Memory and Storage Devices I/O Devices Interconnected with one or more buses Data Bus Address Bus data bus Control Bus registers Processor I/O I/O IA: Intel Architecture Memory Device Device (CPU) #1 #2 32-bit (or i386) ALU CU clock control bus address bus Processor The processor consists of Datapath ALU Registers Control unit ALU (Arithmetic logic unit) Performs arithmetic and logic operations Control unit (CU) Generates the control signals required to execute instructions Memory Address Space Address Space is the set of memory locations (bytes) that are addressable Next ... Basic Computer Organization IA-32 Registers Instruction Execution Cycle Registers Registers are high speed memory inside the CPU Eight 32-bit general-purpose registers Six 16-bit segment registers Processor Status Flags (EFLAGS) and Instruction Pointer (EIP) 32-bit General-Purpose Registers EAX EBP EBX ESP ECX ESI EDX EDI 16-bit Segment Registers EFLAGS CS ES SS FS EIP DS GS General-Purpose Registers Used primarily for arithmetic and data movement mov eax 10 ;move constant integer 10 into register eax Specialized uses of Registers eax – Accumulator register Automatically -

17Computerarchitectu
Computer Architecture and Assembly Language Prof. David August COS 217 1 Goals of Today’s Lecture • Computer architecture o Central processing unit (CPU) o Fetch-decode-execute cycle o Memory hierarchy, and other optimization • Assembly language o Machine vs. assembly vs. high-level languages o Motivation for learning assembly language o Intel Architecture (IA32) assembly language 2 Levels of Languages • Machine language o What the computer sees and deals with o Every command is a sequence of one or more numbers • Assembly language o Command numbers replaced by letter sequences that are easier to read o Still have to work with the specifics of the machine itself • High-level language o Make programming easier by describing operations in a natural language o A single command replaces a group of low-level assembly language commands 3 Why Learn Assembly Language? • Understand how things work underneath o Learn the basic organization of the underlying machine o Learn how the computer actually runs a program o Design better computers in the future • Write faster code (even in high-level language) o By understanding which high-level constructs are better o … in terms of how efficient they are at the machine level • Some software is still written in assembly language o Code that really needs to run quickly o Code for embedded systems, network processors, etc. 4 A Typical Computer CPU . CPU Memory Chipset I/O bus ROM Network 5 Von Neumann Architecture • Central Processing Unit CPU o Control unit Control – Fetch, decode, and execute Unit o Arithmetic -

Design of the RISC-V Instruction Set Architecture
Design of the RISC-V Instruction Set Architecture Andrew Waterman Electrical Engineering and Computer Sciences University of California at Berkeley Technical Report No. UCB/EECS-2016-1 http://www.eecs.berkeley.edu/Pubs/TechRpts/2016/EECS-2016-1.html January 3, 2016 Copyright © 2016, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. Design of the RISC-V Instruction Set Architecture by Andrew Shell Waterman A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate Division of the University of California, Berkeley Committee in charge: Professor David Patterson, Chair Professor Krste Asanovi´c Associate Professor Per-Olof Persson Spring 2016 Design of the RISC-V Instruction Set Architecture Copyright 2016 by Andrew Shell Waterman 1 Abstract Design of the RISC-V Instruction Set Architecture by Andrew Shell Waterman Doctor of Philosophy in Computer Science University of California, Berkeley Professor David Patterson, Chair The hardware-software interface, embodied in the instruction set architecture (ISA), is arguably the most important interface in a computer system. Yet, in contrast to nearly all other interfaces in a modern computer system, all commercially popular ISAs are proprietary. -

Intel Architecture Intel Architecture
CS499 Intel Architecture Intel Architecture References IA-32 Intel® Architecture Software Developer’s Manual, • Volume 1: Basic Architecture • Volume 2: Instruction Set Reference www.intel.com/design/pentiumii/manuals/ Number Systems Decimal-to-Hexadecimal: 420.62510 = 420.62510 = 42010 + .62510 Division Quotient Remainder 420 ÷ 16 26 4 LSB 26 ÷ 16 1 10 (or A) 1 ÷ 16 0 1 MSB Multiplication Product Carry-out .625 x 16 10.00 10 (or A) 420.62510 = 1A4.A16 413510 = 102716 625.62510 = 271.A16 Number Systems Binary-Coded Hexadecimal (BCH): 2AC = 0010 1010 1100 1000 0011 1101 . 1110 = 83D.E Complements Data are stored in complement form to represent negative numbers One’s complements of 01001100 1111 1111 -0100 1100 1011 0011 Two’s complements 1011 0011 +0000 0001 1011 0100 The 80x86 MICROPROCESSOR Some buzz words ...ha? CISC – Complex Instruction Set Computers • Refers to number and complexity of instructions • Improvements was: Multiply and Divide • The number of instruction increased from • 45 on 4004 to: • 246 on 8085 • 20,000 on 8086 and 8088 RISC – Reduced Instruction Set Computer • Executes one instruction per clock Newer RISC - Superscaler Technology • Execute more than one instruction per clock Inside The 8088/8086 Concepts important to the internal operation of 8088/8086 • Pipelining • Registers Inside The 8088/8086…pipelining • Pipelining – Two ways to make CPU process information faster: • Increase the working frequency – technology dependent • Change the internal architecture of the CPU – Pipelining is to allow CPU to fetch and -

(Mentos) Fundamental Concepts
Mentoring Operating System (MentOS) fundamental concepts Alessandro Danese University of Verona [email protected] Version 1.0.0 Mentoring Operating System (MentOS) fundamental concepts Version 1.0.0 1 / 23 Table of Contents 1 Mentoring Operating System 2 Fundamental concepts Central Processing Unit (CPU) Programmable Interrupt Controller (PIC) Memory organization 3 Kernel doubly-linked list Mentoring Operating System (MentOS) fundamental concepts Version 1.0.0 2 / 23 Mentoring Operating System Mentoring Operating System (MentOS) fundamental concepts Version 1.0.0 3 / 23 MentOS What... MentOS (Mentoring Operating system) is an open source educational operating system. MentOS can be freely downloaded from a public github repository: https://mentos-team.github.io/MentOS/ Goal... The goal of MentOS is to provide a project environment that is realistic enough to show how a real Operating System work, yet simple enough that students can understand and modify it in significant ways. Mentoring Operating System (MentOS) fundamental concepts Version 1.0.0 4 / 23 MentOS Why... There are so many operating systems, why did we write MentOs? It is true, there are a lot of education operating system, BUT how many of them follow the guideline defined by Linux? MentOs aims to have the same Linux's data structures and algorithms. It has a well-documented source code, and you can compile it on your laptop in a few seconds! If you are a beginner in Operating-System developing, perhaps MentOS is the right operating system to start with. Mentoring Operating System (MentOS) fundamental concepts Version 1.0.0 5 / 23 Fundamental concepts Mentoring Operating System (MentOS) fundamental concepts Version 1.0.0 6 / 23 The big picture Central Processing Unit Programmable Interrupt Controller Random Access Memory RAM PIC CPU BUS (Address, Data, Control) Mentoring Operating System (MentOS) fundamental concepts Version 1.0.0 7 / 23 CPU registers There are three types of registers: general-purpose data registers, segment registers, and status control registers. -
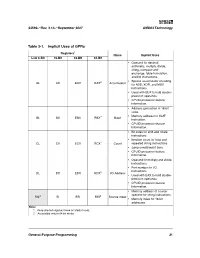
Implicitly Modified Registers
24592—Rev. 3.14—September 2007 AMD64 Technology Table 3-1. Implicit Uses of GPRs Registers 1 Name Implicit Uses Low 8-Bit 16-Bit 32-Bit 64-Bit • Operand for decimal arithmetic, multiply, divide, string, compare-and- exchange, table-translation, and I/O instructions. 2 • Special accumulator encoding AL AX EAX RAX Accumulator for ADD, XOR, and MOV instructions. • Used with EDX to hold double- precision operands. • CPUID processor-feature information. • Address generation in 16-bit code. • Memory address for XLAT BL BX EBX RBX 2 Base instruction. • CPUID processor-feature information. • Bit index for shift and rotate instructions. • Iteration count for loop and CL CX ECX RCX 2 Count repeated string instructions. • Jump conditional if zero. • CPUID processor-feature information. • Operand for multiply and divide instructions. • Port number for I/O instructions. DL DX EDX RDX 2 I/O Address • Used with EAX to hold double- precision operands. • CPUID processor-feature information. • Memory address of source operand for string instructions. SIL 2 SI ESI RSI 2 Source Index • Memory index for 16-bit addresses. Note: 1. Gray-shaded registers have no implicit uses. 2. Accessible only in 64-bit mode. General-Purpose Programming 31 AMD64 Technology 24592—Rev. 3.14—September 2007 Table 3-1. Implicit Uses of GPRs (continued) Registers 1 Name Implicit Uses Low 8-Bit 16-Bit 32-Bit 64-Bit • Memory address of destination Destination operand for string instructions. DIL 2 DI EDI RDI 2 Index • Memory index for 16-bit addresses. • Memory address of stack- BPL 2 BP EBP RBP 2 Base Pointer frame base pointer. -

Assembly Language Tutorial
Assembly Language Tutorial ASSEMBLY LANGUAGE TUTORIAL Simply Easy Learning by tutorialspoint.com tutorialspoint.com i ABOUT THE TUTORIAL Assembly Programming Tutorial Assembly language is a low-level programming language for a computer, or other programmable device specific to a particular computer architecture in contrast to most high- level programming languages, which are generally portable across multiple systems. Assembly language is converted into executable machine code by a utility program referred to as an assembler like NASM, MASM etc. Audience This tutorial has been designed for software programmers with a need to understand the Assembly programming language starting from scratch. This tutorial will give you enough understanding on Assembly programming language from where you can take yourself at higher level of expertise. Prerequisites Before proceeding with this tutorial you should have a basic understanding of Computer Programming terminologies. A basic understanding of any of the programming languages will help you in understanding the Assembly programming concepts and move fast on the learning track. TUTORIALS POINT Simply Easy Learning Copyright & Disclaimer Notice All the content and graphics on this tutorial are the property of tutorialspoint.com. Any content from tutorialspoint.com or this tutorial may not be redistributed or reproduced in any way, shape, or form without the written permission of tutorialspoint.com. Failure to do so is a violation of copyright laws. This tutorial may contain inaccuracies or errors and tutorialspoint provides no guarantee regarding the accuracy of the site or its contents including this tutorial. If you discover that the tutorialspoint.com site or this tutorial content contains some errors, please contact us at [email protected] TUTORIALS POINT Simply Easy Learning Table of Content Assembly Programming Tutorial ............................................. -

Chapter 3 Basic Execution Environment
CHAPTER 3 BASIC EXECUTION ENVIRONMENT This chapter describes the basic execution environment of an Intel 64 or IA-32 processor as seen by assembly- language programmers. It describes how the processor executes instructions and how it stores and manipulates data. The execution environment described here includes memory (the address space), general-purpose data registers, segment registers, the flag register, and the instruction pointer register. 3.1 MODES OF OPERATION The IA-32 architecture supports three basic operating modes: protected mode, real-address mode, and system management mode. The operating mode determines which instructions and architectural features are accessible: • Protected mode — This mode is the native state of the processor. Among the capabilities of protected mode is the ability to directly execute “real-address mode” 8086 software in a protected, multi-tasking environment. This feature is called virtual-8086 mode, although it is not actually a processor mode. Virtual-8086 mode is actually a protected mode attribute that can be enabled for any task. • Real-address mode — This mode implements the programming environment of the Intel 8086 processor with extensions (such as the ability to switch to protected or system management mode). The processor is placed in real-address mode following power-up or a reset. • System management mode (SMM) — This mode provides an operating system or executive with a transparent mechanism for implementing platform-specific functions such as power management and system security. The processor enters SMM when the external SMM interrupt pin (SMI#) is activated or an SMI is received from the advanced programmable interrupt controller (API C). In SMM, the processor switches to a separate address space while saving the basic context of the currently running program or task.