Leeds Thesis Template
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

In This Issue Monthly Meeting
Monthly Meeting January 28, 2004 The Apple Store Westfarms Mall Panther demo, hands-on G5 trials, great deals, etc. NEWSLETTER OF CONNECTICUT MACINTOSH CONNECTION, INC.JANUARY, 2004 Danger! iPod Could instead of making her surface was clear. Inspection of the wait to Christmas for it. car revealed the side walls on both Be Hazardous To After all, if I didn’t, I passenger tires were torn, and one rim Your Health! would have to burn 25 was badly chewed up. She had Mouse Tales CDs so she could lis- obviously tangled both right wheels By Don Dickey, president ten to the new book! with the curb, but why? Answer: iPod There was a single distraction. Whenever a good deal condition to my gift, appears, I often call Joe Arcuri however. Before shelling out $640 for a new and ask him to “talk me out of chrome plated alloy rim and half that it” if he can. He sometimes does the same with me. The iPod I ordered for a pair of new tires, I realized just Simultaneous failures arrived a couple of how lucky we were. This was a lesson led us to both purchase Umax days before Joe’s, so she walked away from. Had it clones and scanners, Wallstreet one morning I met him and his daugh- happened on Interstate 91 at 65 miles PowerBook G3s, Toshiba M4 digital ter Savannah for breakfast and per hour, things could have been cameras, PowerBook G4s, PowerBoy brought along the iPod to show him. much more tragic, to say the least. -

Web Browser a C-Class Article from Wikipedia, the Free Encyclopedia
Web browser A C-class article from Wikipedia, the free encyclopedia A web browser or Internet browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier (URI) and may be a web page, image, video, or other piece of content.[1] Hyperlinks present in resources enable users to easily navigate their browsers to related resources. Although browsers are primarily intended to access the World Wide Web, they can also be used to access information provided by Web servers in private networks or files in file systems. Some browsers can also be used to save information resources to file systems. Contents 1 History 2 Function 3 Features 3.1 User interface 3.2 Privacy and security 3.3 Standards support 4 See also 5 References 6 External links History Main article: History of the web browser The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. That browser brought together a variety of existing and new software and hardware technologies. Ted Nelson and Douglas Engelbart developed the concept of hypertext long before Berners-Lee and CERN. It became the core of the World Wide Web. Berners-Lee does acknowledge Engelbart's contribution. The introduction of the NCSA Mosaic Web browser in 1993 – one of the first graphical Web browsers – led to an explosion in Web use. Marc Andreessen, the leader of the Mosaic team at NCSA, soon started his own company, named Netscape, and released the Mosaic-influenced Netscape Navigator in 1994, which quickly became the world's most popular browser, accounting for 90% of all Web use at its peak (see usage share of web browsers). -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -

Advanced CSS
www.allitebooks.com AdvancED CSS Joseph R. Lewis and Meitar Moscovitz www.allitebooks.com AdvancED CSS Copyright © 2009 by Joseph R. Lewis and Meitar Moscovitz All rights reserved. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage or retrieval system, without the prior written permission of the copyright owner and the publisher. ISBN-13 (pbk): 978-1-4302-1932-3 ISBN-13 (electronic): 978-1-4302-1933-0 Printed and bound in the United States of America 9 8 7 6 5 4 3 2 1 Trademarked names may appear in this book. Rather than use a trademark symbol with every occurrence of a trademarked name, we use the names only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. Distributed to the book trade worldwide by Springer-Verlag New York, Inc., 233 Spring Street, 6th Floor, New York, NY 10013. Phone 1-800-SPRINGER, fax 201-348-4505, e-mail kn`ano)ju<olnejcan)o^i*_om, or visit sss*olnejcankjheja*_ki. For information on translations, please contact Apress directly at 2855 Telegraph Avenue, Suite 600, Berkeley, CA 94705. Phone 510-549-5930, fax 510-549-5939, e-mail ejbk<]lnaoo*_ki, or visit sss*]lnaoo*_ki. Apress and friends of ED books may be purchased in bulk for academic, corporate, or promotional use. eBook versions and licenses are also available for most titles. For more information, reference our Special Bulk Sales–eBook Licensing web page at dppl6++sss*]lnaoo*_ki+ejbk+^qhgo]hao. -

CGI Developer's Guide by Eugene Eric Kim
CGI Developer's Guide By Eugene Eric Kim Introduction Chapter 1 Common Gateway Interface (CGI) What Is CGI? Caveats Why CGI? Summary Choosing Your Language Chapter 2 The Basics Hello, World! The <form> Tag Dissecting hello.cgi The <input> Tag Hello, World! in C Submitting the Form Outputting CGI Accepting Input from the Browser Installing and Running Your CGI Program Environment Variables Configuring Your Server for CGI GET Versus POST Installing CGI on UNIX Servers Encoded Input Installing CGI on Windows Parsing the Input Installing CGI on the Macintosh A Simple CGI Program Running Your CGI General Programming Strategies A Quick Tutorial on HTML Forms Summary Chapter 3 HTML and Forms A Quick Review of HTML Some Examples HTML Basic Font Tags Comments Form The <head> Tag Ordering Food Forms Voting Booth/Poll The <FORM> Tag Shopping Cart The <INPUT> Tag Map The <SELECT> Tag Summary The <TEXTAREA> Tag Chapter 4 OutPut Revised January 20, 2009 Page 1 of 428 CGI Developer's Guide By Eugene Eric Kim Header and Body: Anatomy of Server Displaying the Current Date Response Server-Side Includes HTTP Headers On-the-Fly Graphics Formatting Output in CGI A "Counter" Example MIME Counting the Number of Accesses Location Text Counter Using Server-Side Includes Status Graphical Counter Other Headers No-Parse Header Dynamic Pages Summary Using Programming Libraries to Code CGI Output Chapter 5 Input Background cgi-lib.pl How CGI Input Works cgihtml Environment Variables Strategies Encoding -

Giant List of Web Browsers
Giant List of Web Browsers The majority of the world uses a default or big tech browsers but there are many alternatives out there which may be a better choice. Take a look through our list & see if there is something you like the look of. All links open in new windows. Caveat emptor old friend & happy surfing. 1. 32bit https://www.electrasoft.com/32bw.htm 2. 360 Security https://browser.360.cn/se/en.html 3. Avant http://www.avantbrowser.com 4. Avast/SafeZone https://www.avast.com/en-us/secure-browser 5. Basilisk https://www.basilisk-browser.org 6. Bento https://bentobrowser.com 7. Bitty http://www.bitty.com 8. Blisk https://blisk.io 9. Brave https://brave.com 10. BriskBard https://www.briskbard.com 11. Chrome https://www.google.com/chrome 12. Chromium https://www.chromium.org/Home 13. Citrio http://citrio.com 14. Cliqz https://cliqz.com 15. C?c C?c https://coccoc.com 16. Comodo IceDragon https://www.comodo.com/home/browsers-toolbars/icedragon-browser.php 17. Comodo Dragon https://www.comodo.com/home/browsers-toolbars/browser.php 18. Coowon http://coowon.com 19. Crusta https://sourceforge.net/projects/crustabrowser 20. Dillo https://www.dillo.org 21. Dolphin http://dolphin.com 22. Dooble https://textbrowser.github.io/dooble 23. Edge https://www.microsoft.com/en-us/windows/microsoft-edge 24. ELinks http://elinks.or.cz 25. Epic https://www.epicbrowser.com 26. Epiphany https://projects-old.gnome.org/epiphany 27. Falkon https://www.falkon.org 28. Firefox https://www.mozilla.org/en-US/firefox/new 29. -

World Wide Web
Informationsdienste im Internet World Wide Web Diese Reisen durch's Internet sollen jetzt auch viel Wissenschaftler, die an gemeinsamen Projekten ar- komfortabler geworden sein - und teurer. Man reist beiten, sind oft über die ganze Welt verstreut. Mitar- jetzt mit Mosaic. Gopher kennt kaum noch einer (?). beiter, Studenten, Gast-Wissenschaftler wechseln Was mein Nachbar bei seiner letzten Reise so alles zwischen den Forschungszentren, bleiben aber Mit- gesehen hat ... glieder dieser verteilten Arbeitsgruppen. Dazu kommt Anstelle einer Vorrede hier ein Auszug aus den Noti- die Vielfalt der Hard- und Software. Wer den Ar- zen jenes ,Datenreisenden’: beitsort wechselte, mußte mit neuen Rechnernamen, Paßworten, Terminalemulationen, Kommandos usw. W3 Search Engines zurechtkommen (Sie kennen das?). Für eine effekti- World Wide Web FAQ vere Zusammenarbeit wurde deshalb dringend ein The Best of WWW Contest System benötigt, das orts- und rechnerunabhängig Oldenburg Archie Gateway den Zugang zu Informationen und deren Austausch HypArt - The Project vereinfacht. Linux Software Map Dieses System heißt heute World Wide Web, hat sich Studienberatung für das Lehramt sehr schnell über das gesamte Internet verbreitet und Lernen und Lehren im WWW ist inzwischen einer der wichtigsten Informations- Yoga für alle dienste. Esperanto HyperCourse Dieser Artikel sollen allen „Newbies“ (Lektion1: Shoemaker-Levy 9/Jupiter Collision Internet-Sprachgebrauch) einen Überblick verschaf- Libraries via Internet fen und mit einer kurzen Beschreibung des Mosaic- German -

The Internet Companion, 2Nd Edition
The Internet Companion, 2nd edition The Internet Companion A Beginner's Guide to Global Networking (2nd edition) by Tracy LaQuey The OBS is pleased to present our free, "distributive" full-text HTML version of the second edition of this bestselling title, linked to resources around the world. As with all our distributive publications, we invite you to browse, comment, and send in your link suggestions. We are also pleased to offer paths to a sibling version of the Internet Companion, produced as a class project at the University of North Carolina. This use of online files points the way to a new form of reading and publishing on the Net: true interactivity where the students or readers can affect a book's content by finding, choosing, and implementing links for it. About the Internet Companion What World Media is Saying About the Internet Companion About Tracy LaQuey Copyright The Internet Companion at the University of North Carolina Buy this Book http://www.obs-us.com/obs/english/books/editinc/top.htm (1 of 3) [5/1/1999 11:46:04 PM] The Internet Companion, 2nd edition Contents Front Matter Foreword Preface Chapter 1 What Is the Internet and Why Should You Know About It? Whence It Came It Keeps Going and Going . The Equalizer Peeling Back the Layers: Differences between Networks Convergence: A Traffic Circle on the Information Highway Mrs. Smith Connects to Washington Business Use Backing Out of the Driveway The Future Chapter 2 Internet: The Lowdown A Network of Networks In the Beginning How Computers Talk Who Runs the Internet? Acceptable -

Web Browser a C-Class Article from Wikipedia, the Free Encyclopedia
Web browser A C-class article from Wikipedia, the free encyclopedia A web browser or Internet browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier (URI) and may be a web page, image, video, or other piece of content. Hyperlinks present in resources enable users to easily navigate their browsers to related resources. Although browsers are primarily intended to access the World Wide Web, they can also be used to access information provided by Web servers in private networks or files in file systems. Some browsers can also be used to save information resources to file systems. Contents 1 History 2 Function 3 Features 3.1 User interface 3.2 Privacy and security 3.3 Standards support 4 See also 5 References 6 External links History Main article: History of the web browser The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. That browser brought together a variety of existing and new software and hardware technologies. Ted Nelson and Douglas Engelbart developed the concept of hypertext long before Berners-Lee and CERN. It became the core of the World Wide Web. Berners-Lee does acknowledge Engelbart's contribution. The introduction of the NCSA Mosaic Web browser in 1993 – WorldWideWeb for NeXT, released in one of the first graphical Web browsers – led to an explosion in 1991, was the first Web browser. -

Carte Care Se Vrea În Esență Despre Internet Și Despre Web Este Cel Puțin Ciudat Să Folosesc Un Astfel De Motto
Cuprins 1 Introducere ..................................................................5 1.1 Să ne lămurim… .................................................. 6 1.1.1 La început a fost WEB-ul: fals ........................ 6 1.1.2 WEB-ul era la sistemul de operare: fals ........ 6 1.1.3 Sistemul de operare era WEB-ul: fals ........... 6 1.2 Când a început WEB-ul? ..................................... 7 1.3 La început a fost Internetul: aproape corect ...... 9 2 HTML – HTML5 ....................................................... 14 2.1 WWW (World Wide Web)? ................................ 14 2.2 Pagini Web ......................................................... 15 2.3 Adresa unei pagini de Web ................................ 15 2.4 Cum aduce browserul paginile web? ................. 17 2.5 Cum afișează browser-ul paginile web? ............ 19 2.6 Ce este un fișier HTML? ................................... 20 2.7 Structura standard a unui document html5 ..... 21 2.7.1 Primul cod html ............................................ 21 2.7.2 Explicarea structurii standard: ................... 24 2.8 Tag-uri html ...................................................... 26 2.8.1 DOM – Document Object Model .................27 2.8.2 Observații generale ..................................... 29 1 2.9 Marcarea corectă a textului ............................... 31 2.9.1 Marcarea metadatelor ................................. 32 2.9.2 Delimitarea logică a conținutului ............... 34 2.9.3 Tag-uri pentru marcarea structurală a conținutul textului -
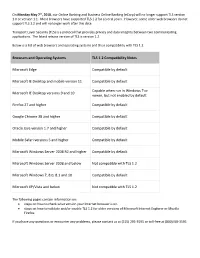
Browsers and Operating Systems TLS 1.2 Compatibility Notes Microsoft
On Monday May 7th, 2018, our Online Banking and Business Online Banking (eCorp) will no longer support TLS version 1.0 or version 1.1. Most browsers have supported TLS 1.2 for several years. However, some older web browsers do not support TLS 1.2 and will no longer work after this date. Transport Layer Security (TLS) is a protocol that provides privacy and data integrity between two communicating applications. The latest release version of TLS is version 1.2 Below is a list of web browsers and operating systems and their compatibility with TLS 1.2. Browsers and Operating Systems TLS 1.2 Compatibility Notes Microsoft Edge Compatible by default Microsoft IE Desktop and mobile version 11 Compatible by default Capable when run in Windows 7 or Microsoft IE Desktop versions 9 and 10 newer, but not enabled by default Firefox 27 and higher Compatible by default Google Chrome 38 and higher Compatible by default Oracle Java version 1.7 and higher Compatible by default Mobile Safari versions 5 and higher Compatible by default Microsoft Windows Server 2008 R2 and higher Compatible by default Microsoft Windows Server 2008 and below Not compatible with TLS 1.2 Microsoft Windows 7, 8.0, 8.1 and 10 Compatible by default Microsoft XP/Vista and below Not compatible with TLS 1.2 The following pages contain information on: steps on how to check what version your Internet browser is on. steps on how to validate and/or enable TLS 1.2 for older versions of Microsoft Internet Explorer or Mozilla Firefox. -

Introducción a La Informática
Introducción a la informática Introducción a la informática Introducción.................................................................................................... 5 Conceptos básicos .............................................................................. 5 Tratamiento de la información................................................... 5 Definición de informática. .......................................................... 5 El ordenador o computadora..................................................... 5 Evolución histórica de los ordenadores ............................................... 6 Componentes físicos del ordenador (Hardware) ................................. 7 La unidad central....................................................................... 7 Los periféricos........................................................................... 8 Componentes lógicos del ordenador (Software)................................ 13 Sistema operativo.................................................................... 13 Aplicaciones de usuario .......................................................... 14 Aplicaciones en los equipos corporativos................................ 15 Sistema operativo Windows XP ................................................................... 18 Login de usuario. ............................................................................... 18 El escritorio ........................................................................................ 19 Los iconos.........................................................................................