Volume XIV, Issue 1 February 2020 PERSPECTIVES on TERRORISM Volume 14, Issue 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
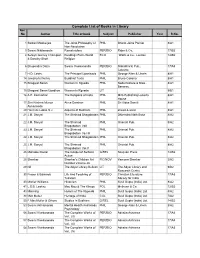
Complete List of Books in Library Acc No Author Title of Book Subject Publisher Year R.No
Complete List of Books in Library Acc No Author Title of book Subject Publisher Year R.No. 1 Satkari Mookerjee The Jaina Philosophy of PHIL Bharat Jaina Parisat 8/A1 Non-Absolutism 3 Swami Nikilananda Ramakrishna PER/BIO Rider & Co. 17/B2 4 Selwyn Gurney Champion Readings From World ECO `Watts & Co., London 14/B2 & Dorothy Short Religion 6 Bhupendra Datta Swami Vivekananda PER/BIO Nababharat Pub., 17/A3 Calcutta 7 H.D. Lewis The Principal Upanisads PHIL George Allen & Unwin 8/A1 14 Jawaherlal Nehru Buddhist Texts PHIL Bruno Cassirer 8/A1 15 Bhagwat Saran Women In Rgveda PHIL Nada Kishore & Bros., 8/A1 Benares. 15 Bhagwat Saran Upadhya Women in Rgveda LIT 9/B1 16 A.P. Karmarkar The Religions of India PHIL Mira Publishing Lonavla 8/A1 House 17 Shri Krishna Menon Atma-Darshan PHIL Sri Vidya Samiti 8/A1 Atmananda 20 Henri de Lubac S.J. Aspects of Budhism PHIL sheed & ward 8/A1 21 J.M. Sanyal The Shrimad Bhagabatam PHIL Dhirendra Nath Bose 8/A2 22 J.M. Sanyal The Shrimad PHIL Oriental Pub. 8/A2 Bhagabatam VolI 23 J.M. Sanyal The Shrimad PHIL Oriental Pub. 8/A2 Bhagabatam Vo.l III 24 J.M. Sanyal The Shrimad Bhagabatam PHIL Oriental Pub. 8/A2 25 J.M. Sanyal The Shrimad PHIL Oriental Pub. 8/A2 Bhagabatam Vol.V 26 Mahadev Desai The Gospel of Selfless G/REL Navijvan Press 14/B2 Action 28 Shankar Shankar's Children Art FIC/NOV Yamuna Shankar 2/A2 Number Volume 28 29 Nil The Adyar Library Bulletin LIT The Adyar Library and 9/B2 Research Centre 30 Fraser & Edwards Life And Teaching of PER/BIO Christian Literature 17/A3 Tukaram Society for India 40 Monier Williams Hinduism PHIL Susil Gupta (India) Ltd. -

Faith and Conflict in the Holy Land: Peacemaking Among Jews, Christians, and Muslims
ANNUAL FALL McGINLEY LECTURE Faith and Conflict in the Holy Land: Peacemaking Among Jews, Christians, and Muslims The Reverend Patrick J. Ryan, S.J. Laurence J. McGinley Professor of Religion and Society RESPONDENTS Abraham Unger, Ph.D. Associate Professor Department of Government and Politics Wagner College Ebru Turan, Ph.D. Assistant Professor of History Fordham University Tuesday, November 12, 2019 | Lincoln Center Campus Wednesday, November 13, 2019 | Rose Hill Campus 3 Faith and Conflict in the Holy Land: Peacemaking Among Jews, Christians, and Muslims The Reverend Patrick J. Ryan, S.J. Laurence J. McGinley Professor of Religion and Society Let me begin on holy ground, Ireland. In 1931 William Butler Yeats concluded his short poem, “Remorse for Intemperate Speech,” with a stanza that speaks to me as the person I am, for better or for worse: Out of Ireland have we come. Great hatred, little room, Maimed us at the start. I carry from my mother’s womb A fanatic heart. Ireland is, indeed, a small place, and it has seen great fanaticism and hatred, although the temperature of Ireland as a whole has subsided dramatically since the Good Friday Agreement of 1998, despite Boris Johnson. The whole island of Ireland today occupies 32,599 square miles. British-administered Northern Ireland includes 5,340 of those square miles. Combined Northern Ireland and the Republic of Ireland approximate the size of Indiana. The total population of the island of Ireland is 6.7 million people, about a half a million more than the population of Indiana. There is another place of “great hatred, little room” that I wish to discuss this evening: the Holy Land, made up today of the State of Israel and the Palestinian autonomous regions of the West Bank and the Gaza Strip. -

Pahalgam Hotels
www.cityinfoyellowpages.com Cityinfo Yellow Pages,J&K 2020-21 HOTELS - HOTELS 281 BOUILEVARD RD SGR....................2473672 HOTEL PANDIT PALACE HOTEL SILVER STAR ORION HOTEL HOTEL MAMTA KHAYAM RD., SGR.........................2450001 LASJAN, BYE PASS RD., SGR........2145586 LAL CHK., SGR.............................2472431 DAL GATE, SGR...............................2473388 HOTEL PARADISE HOTEL SILVER STAR PARAMOUNT GUEST HOUSE HOTEL MANAGER PARIMAHAL DAL GATE BOULEVARD, SGR.......2500663 LASJAN, BYE PASS RD., SGR........2146219 BAR BAR SHAH CHK, SGR..............2482528 BOULEVARD ROAD, SGR..............2479169 HOTEL PARIMAHAL HOTEL SILVER STAR PAKEEZA GUEST HOUSE HOTEL MANORA PALACE BOULEVARD ROAD, SGR..............2500369 LASJAN, BYE PASS RD., SGR........2465586 RAJ BAGH, SGR..............................2451282 NEHRU PARK, SGR........................2473479 HOTEL PEACE HOTEL SILVER STAR PEAK VIEW HOTEL & RESTAURANT HOTEL MANURANJAN LAL CHK., SGR...........................9906708485 LASJAN, BYE PASS RD., SGR........2466214 LAL CHK., SGR................................2477038 SONWAR, SGR................................2466966 HOTEL PEAK VIEW HOTEL SNOWLAND PERFECT HOLIDAYS HOTEL MARHABA RESTURANT LAL CHK. SGR..................................2477038 MUNAWARABAD, SGR...................2472591 BOULEVARD RD., SGR..............9419090011 JEHANGIR RD. SGR.......................2454909 HOTEL PEARL HOTEL STANDARD PINCER FOODS HOTEL MEHTAB IN SONAWAR, SGR..............................2466098 LAL CHOWK, SGR...........................2455285 -

Afzal Guru's Execution
Contents ARTICLES - India’s Compass On Terror Is Faulty What Does The Chinese Take Over - Kanwal Sibal 3 Of Gwadar Imply? 46 Stop Appeasing Pakistan - Radhakrishna Rao 6 - Satish Chandra Reforming The Criminal Justice 103 Slandering The Indian Army System 51 10 - PP Shukla - Dr. N Manoharan 107 Hydro Power Projects Race To Tap The ‘Indophobia’ And Its Expressions Potential Of Brahmaputra River 15 - Dr. Anirban Ganguly 62 - Brig (retd) Vinod Anand Pakistan Looks To Increase Its Defence Acquisition: Urgent Need For Defence Footprint In Afghanistan Structural Reforms 21 - Monish Gulati 69 - Brig (retd) Gurmeet Kanwal Political Impasse Over The The Governor , The Constitution And The Caretaker Government In 76 Courts 25 Bangladesh - Dr M N Buch - Neha Mehta Indian Budget Plays With Fiscal Fire 34 - Ananth Nageswaran EVENTS Afzal Guru’s Execution: Propaganda, Politics And Portents 41 Vimarsha: Security Implications Of - Sushant Sareen Contemporary Political 80 Environment In India VIVEK : Issues and Options March – 2013 Issue: II No: III 2 India’s Compass On Terror Is Faulty - Kanwal Sibal fzal Guru’s hanging shows state actors outside any law. The the ineptness with which numbers involved are small and A our political system deals the targets are unsuspecting and with the grave problem of unprepared individuals in the terrorism. The biggest challenge to street, in public transport, hotels our security, and indeed that of or restaurants or peaceful public countries all over the world that spaces. Suicide bombers and car are caught in the cross currents of bombs can cause substantial religious extremism, is terrorism. casualties indiscriminately. Shadowy groups with leaders in Traditional military threats can be hiding orchestrate these attacks. -

A Strategy for Success in Libya
A Strategy for Success in Libya Emily Estelle NOVEMBER 2017 A Strategy for Success in Libya Emily Estelle NOVEMBER 2017 AMERICAN ENTERPRISE INSTITUTE © 2017 by the American Enterprise Institute. All rights reserved. The American Enterprise Institute (AEI) is a nonpartisan, nonprofit, 501(c)(3) educational organization and does not take institutional positions on any issues. The views expressed here are those of the author(s). Contents Executive Summary ......................................................................................................................1 Why the US Must Act in Libya Now ............................................................................................................................1 Wrong Problem, Wrong Strategy ............................................................................................................................... 2 What to Do ........................................................................................................................................................................ 2 Reframing US Policy in Libya .................................................................................................. 5 America’s Opportunity in Libya ................................................................................................................................. 6 The US Approach in Libya ............................................................................................................................................ 6 The Current Situation -

COI QUERY Disclaimer
COI QUERY Country of Origin Pakistan Main subject Situation in Pakistan-administered Kashmir Question(s) 1. General information Historical background Population and ethnic groups Returnees in Kashmir and Punjab Religious demography 2. Political situation 3. Human rights situation General overview Ethnic conflict Sectarian conflict 4. Security situation Conflict-related violence Line of control violations Cross-border attacks Examples of cross-border violence in 2020 Armed groups Hizb-ul-Mujahideen (HM) Jaish-e Muhammad (JeM) Lashkar-e Taiba (LeT) Harakat ul-Mujahidin (HuM) Date of completion 6 October 2020 Query Code Q27-2020 Contributing EU+ COI -- units (if applicable) Disclaimer This response to a COI query has been elaborated according to the EASO COI Report Methodology and EASO Writing and Referencing Guide. The information provided in this response has been researched, evaluated and processed with utmost care within a limited time frame. All sources used are referenced. A quality review has been performed in line with the above mentioned methodology. This document does not claim to be exhaustive neither conclusive as to the merit of any particular claim to international protection. If a certain event, person or organisation is not mentioned in the report, this does not mean that the event has not taken place or that the person or organisation does not exist. Terminology used should not be regarded as indicative of a particular legal position. 1 The information in the response does not necessarily reflect the opinion of EASO and makes no political statement whatsoever. The target audience is caseworkers, COI researchers, policy makers, and decision making authorities. The answer was finalised on 6 October 2020. -

Union Calendar No. 499
Union Calendar No. 499 107TH CONGRESS REPORT " ! 2d Session HOUSE OF REPRESENTATIVES 107–798 REPORT ON THE ACTIVITY OF THE COMMITTEE ON FINANCIAL SERVICES FOR THE 107TH CONGRESS JANUARY 2, 2003.—Committed to the Committee of the Whole House on the State of the Union and ordered to be printed Mr. OXLEY, from the Committee on Financial Services, submitted the following REPORT Clause 1(d) of rule XI of the Rules of the House of Representa- tives requires each standing Committee, not later than January 2 of each odd-numbered year, submit to the House a report on the activities of that committee, including separate sections summa- rizing the legislative and oversight activities of that committee dur- ing that Congress. CONTENTS Page Letter of Transmittal ............................................................................................... 2 Jurisdiction ............................................................................................................... 3 Rules of the Committee ........................................................................................... 7 Membership and Organization ............................................................................... 19 Legislative and Oversight Activities ...................................................................... 27 Full Committee ..................................................................................................... 29 Subcommittee on Capital Markets, Insurance, and Government Sponsored Enterprises ....................................................................................................... -

The Historical Development of Irish Euroscepticism to 2001
The Historical Development of Irish Euroscepticism to 2001 Troy James Piechnick Thesis submitted as part of the Doctor of Philosophy (PhD) program at Flinders University on the 1st of September 2016 Social and Behavioural Sciences School of History and International Relations Flinders University 2016 Supervisors Professor Peter Monteath (PhD) Dr Evan Smith (PhD) Associate Professor Matt Fitzpatrick (PhD) Contents GLOSSARY III ABSTRACT IV ACKNOWLEDGEMENTS V CHAPTER 1 INTRODUCTION 1 DEFINITIONS 2 PARAMETERS 13 LITERATURE REVIEW 14 MORE RECENT DEVELOPMENTS 20 THESIS AND METHODOLOGY 24 STRUCTURE 28 CHAPTER 2 EARLY ANTECEDENTS OF IRISH EUROSCEPTICISM: 1886–1949 30 IRISH REPUBLICANISM, 1780–1886 34 FIRST HOME RULE BILL (1886) AND SECOND HOME RULE BILL (1893) 36 THE BOER WAR, 1899–1902 39 SINN FÉIN 40 WORLD WAR I AND EASTER RISING 42 IRISH DECLARATION OF INDEPENDENCE 46 IRISH WAR OF INDEPENDENCE 1919 AND CIVIL WAR 1921 47 BALFOUR DECLARATION OF 1926 AND THE STATUTE OF WESTMINSTER IN 1931 52 EAMON DE VALERA AND WORLD WAR II 54 REPUBLIC OF IRELAND ACT 1948 AND OTHER IMPLICATIONS 61 CONCLUSION 62 CHAPTER 3 THE TREATY OF ROME AND FAILED APPLICATIONS FOR MEMBERSHIP IN 1961 AND 1967 64 THE TREATY OF ROME 67 IRELAND IN THE 1950S 67 DEVELOPING IRISH EUROSCEPTICISM IN THE 1950S 68 FAILED APPLICATIONS FOR MEMBERSHIP IN 1961 AND 1967 71 IDEOLOGICAL MAKINGS: FURTHER DEVELOPMENTS OF A EUROSCEPTIC NATURE (1960S) 75 Communist forms of Irish euroscepticism 75 Irish eurosceptics and republicanism 78 Irish euroscepticism accommodating democratic socialism 85 -

Directory Establishment
DIRECTORY ESTABLISHMENT SECTOR :URBAN STATE : JAMMU & KASHMIR DISTRICT : Anantnag Year of start of Employment Sl No Name of Establishment Address / Telephone / Fax / E-mail Operation Class (1) (2) (3) (4) (5) NIC 2004 : 0121-Farming of cattle, sheep, goats, horses, asses, mules and hinnies; dairy farming [includes stud farming and the provision of feed lot services for such animals] 1 DEPARTMENT OF ANIMAL HUSBANDRY NAZ BASTI ANTNTNAG OPPOSITE TO SADDAR POLICE STATION ANANTNAG PIN CODE: 2000 10 - 50 192102, STD CODE: NA , TEL NO: NA , FAX NO: NA, E-MAIL : N.A. NIC 2004 : 0122-Other animal farming; production of animal products n.e.c. 2 ASSTSTANT SERICULTURE OFFICER NAGDANDY , PIN CODE: 192201, STD CODE: NA , TEL NO: NA , FAX NO: NA, E-MAIL : N.A. 1985 10 - 50 3 INTENSIVE POULTRY PROJECT MATTAN DTSTT. ANANTNAG , PIN CODE: 192125, STD CODE: NA , TEL NO: NA , FAX NO: 1988 10 - 50 NA, E-MAIL : N.A. NIC 2004 : 0140-Agricultural and animal husbandry service activities, except veterinary activities. 4 DEPTT, OF HORTICULTURE KULGAM TEH KULGAM DISTT. ANANTNAG KASHMIR , PIN CODE: 192231, STD CODE: NA , 1969 10 - 50 TEL NO: NA , FAX NO: NA, E-MAIL : N.A. 5 DEPTT, OF AGRICULTURE KULGAM ANANTNAG NEAR AND BUS STAND KULGAM , PIN CODE: 192231, STD CODE: NA , 1970 10 - 50 TEL NO: NA , FAX NO: NA, E-MAIL : N.A. NIC 2004 : 0200-Forestry, logging and related service activities 6 SADU NAGDANDI PIJNAN , PIN CODE: 192201, STD CODE: NA , TEL NO: NA , FAX NO: NA, E-MAIL : 1960 10 - 50 N.A. 7 CONSERVATOR LIDDER FOREST CONSERVATOR LIDDER FOREST DIVISION GORIWAN BIJEHARA PIN CODE: 192124, STD CODE: 1970 10 - 50 DIVISION NA , TEL NO: NA , FAX NO: NA, E-MAIL : N.A. -

Espionage Against the United States by American Citizens 1947-2001
Technical Report 02-5 July 2002 Espionage Against the United States by American Citizens 1947-2001 Katherine L. Herbig Martin F. Wiskoff TRW Systems Released by James A. Riedel Director Defense Personnel Security Research Center 99 Pacific Street, Building 455-E Monterey, CA 93940-2497 REPORT DOCUMENTATION PAGE Form Approved OMB No. 0704-0188 The public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instructions, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing the burden, to Department of Defense, Washington Headquarters Services, Directorate for Information Operations and Reports (0704- 0188), 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302. Respondents should be aware that notwithstanding any other provision of law, no person shall be subject to any penalty for failing to comply with a collection of information if it does not display a currently valid OMB control number. PLEASE DO NOT RETURN YOUR FORM TO THE ABOVE ADDRESS. 1. REPORT DATE (DDMMYYYY) 2. REPORT TYPE 3. DATES COVERED (From – To) July 2002 Technical 1947 - 2001 4. TITLE AND SUBTITLE 5a. CONTRACT NUMBER 5b. GRANT NUMBER Espionage Against the United States by American Citizens 1947-2001 5c. PROGRAM ELEMENT NUMBER 6. AUTHOR(S) 5d. PROJECT NUMBER Katherine L. Herbig, Ph.D. Martin F. Wiskoff, Ph.D. 5e. TASK NUMBER 5f. WORK UNIT NUMBER 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. -

Organized Crime Drug Enforcement Task Force (OCDETF) Cases
I. Making America Safe Goal: To guarantee the incarceration of violent and repeat offenders and concentrate law enforcement resources where they can be most effective. As this Nation’s chief law enforcement organization, the Department of Justice is charged with providing leadership to ensure that the citizens of the United States are protected from vio- lence and criminal activities. In 1996, the Department worked aggressively toward this goal by advancing a number of anti-crime proposals that resulted in legislation to address gun violence, methamphetamine use, computer crime, child pornography, youth crime, and other priority areas. The Department also worked to ensure that key anti-crime initiatives, including the Brady Law, the assault weapons ban, and the Community Oriented Policing Services (COPS) Program, were not repealed or weakened. The Department continued to expand assistance to and interaction with State and local police forces, participate in task force operations, and improve its technological crime-fighting capabilities, thereby enhancing the safety of our communities. National Security/Anti-terrorism Responding to Acts of Terrorism The United States has a firm policy for dealing with acts of ter- rorism, focusing on deterrence, quick and decisive responses, and international cooperation. In July, the Attorney General played a leadership role on this issue at the ministerial-level meeting of the G-7/P-8 nations in Paris. The United States has reiterated publicly to both our allies and potential adversaries that it will never accede to terrorist demands, no matter what they might be, and that any effort to intimidate or coerce the United States will be futile. -

The 2016 U.S. Election
April 2017, Volume 28, Number 2 $14.00 The 2016 U.S. Election William Galston John Sides, Michael Tesler, and Lynn Vavreck James Ceaser Nathaniel Persily Charles Stewart III The Modernization Trap Jack Snyder The Freedom House Survey for 2016 Arch Puddington and Tyler Roylance Sheriff Kora and Momodou Darboe on the Gambia Thomas Pepinsky on Southeast Asia Nic Cheeseman, Gabrielle Lynch, and Justin Willis on Ghana’s Elections Kai M. Thaler on Nicaragua Sean Yom on Jordan and Morocco The End of the Postnational Illusion Ghia Nodia The 2016 U.S. Election Longtime readers will be aware that this is the first time the Journal of Democracy has ever devoted a set of articles to the situation of democracy in the United States. Our traditional focus has been on the problems and prospects of democracy in developing and postcommunist countries. In the introduction to the group of essays in our October 2016 issue entitled “The Specter Haunting Europe,” we explained why we felt we had to redirect some of our attention to the growing vulnerability of democracy in the West, and promised that we would not refrain from examining the United States as well. This is an especially delicate task for us because our parent organization, the National Endowment for Democracy, is a reso- lutely bipartisan institution that seeks to steer clear of the controversies of U.S. domestic politics. We hope we have succeeded in avoiding the pitfalls of partisanship; but in an era when the trends that are weakening liberal democracy are increasingly global, an editorial version of “Ameri- can isolationism” no longer seemed a defensible policy.