Network Monitoring Using Extreme Visualization Performance and Fault Manager Plus
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Gigabit Ethernet - CH 3 - Ethernet, Fast Ethernet, and Gigabit Ethern
Switched, Fast, and Gigabit Ethernet - CH 3 - Ethernet, Fast Ethernet, and Gigabit Ethern.. Page 1 of 36 [Figures are not included in this sample chapter] Switched, Fast, and Gigabit Ethernet - 3 - Ethernet, Fast Ethernet, and Gigabit Ethernet Standards This chapter discusses the theory and standards of the three versions of Ethernet around today: regular 10Mbps Ethernet, 100Mbps Fast Ethernet, and 1000Mbps Gigabit Ethernet. The goal of this chapter is to educate you as a LAN manager or IT professional about essential differences between shared 10Mbps Ethernet and these newer technologies. This chapter focuses on aspects of Fast Ethernet and Gigabit Ethernet that are relevant to you and doesn’t get into too much technical detail. Read this chapter and the following two (Chapter 4, "Layer 2 Ethernet Switching," and Chapter 5, "VLANs and Layer 3 Switching") together. This chapter focuses on the different Ethernet MAC and PHY standards, as well as repeaters, also known as hubs. Chapter 4 examines Ethernet bridging, also known as Layer 2 switching. Chapter 5 discusses VLANs, some basics of routing, and Layer 3 switching. These three chapters serve as a precursor to the second half of this book, namely the hands-on implementation in Chapters 8 through 12. After you understand the key differences between yesterday’s shared Ethernet and today’s Switched, Fast, and Gigabit Ethernet, evaluating products and building a network with these products should be relatively straightforward. The chapter is split into seven sections: l "Ethernet and the OSI Reference Model" discusses the OSI Reference Model and how Ethernet relates to the physical (PHY) and Media Access Control (MAC) layers of the OSI model. -

Extreme Networks EXOS V12.3.6.2 EAL3+ ST
Extreme Networks, Inc. ExtremeXOS Network Operating System v12.3.6.2 Security Target Evaluation Assurance Level: EAL3+ Document Version: 0.9 Prepared for: Prepared by: Extreme Networks, Inc. Corsec Security, Inc. 3585 Monroe Street 13135 Lee Jackson Memorial Hwy., Suite 220 Santa Clara, CA 95051 Fairfax, VA 22033 Phone: +1 408 579 2800 Phone: +1 703 267 6050 http://www.extremenetworks.com http://www.corsec.c om Security Target , Version 0.9 March 12, 2012 Table of Contents 1 INTRODUCTION ................................................................................................................... 4 1.1 PURPOSE ................................................................................................................................................................ 4 1.2 SECURITY TARGET AND TOE REFERENCES ...................................................................................................... 4 1.3 TOE OVERVIEW ................................................................................................................................................... 5 1.3.1 TOE Environment ................................................................................................................................................... 5 1.4 TOE DESCRIPTION .............................................................................................................................................. 6 1.4.1 Architecture ............................................................................................................................................................. -

Network Devices Configuration Guide for Packetfence Version 6.5.0 Network Devices Configuration Guide by Inverse Inc
Network Devices Configuration Guide for PacketFence version 6.5.0 Network Devices Configuration Guide by Inverse Inc. Version 6.5.0 - Jan 2017 Copyright © 2017 Inverse inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License". The fonts used in this guide are licensed under the SIL Open Font License, Version 1.1. This license is available with a FAQ at: http:// scripts.sil.org/OFL Copyright © Łukasz Dziedzic, http://www.latofonts.com, with Reserved Font Name: "Lato". Copyright © Raph Levien, http://levien.com/, with Reserved Font Name: "Inconsolata". Table of Contents About this Guide ............................................................................................................... 1 Other sources of information ..................................................................................... 1 Note on Inline enforcement support ................................................................................... 2 List of supported Network Devices ..................................................................................... 3 Switch configuration .......................................................................................................... 4 Assumptions ............................................................................................................ -

Glossaire Des Protocoles Réseau
Glossaire des protocoles réseau - EDITION LIVRES POUR TOUS - http://www.livrespourtous.com/ Mai 2009 A ALOHAnet ALOHAnet, également connu sous le nom ALOHA, est le premier réseau de transmission de données faisant appel à un média unique. Il a été développé par l'université d'Hawaii. Il a été mis en service en 1970 pour permettre les transmissions de données par radio entre les îles. Bien que ce réseau ne soit plus utilisé, ses concepts ont été repris par l'Ethernet. Histoire C'est Norman Abramson qui est à l'origine du projet. L'un des buts était de créer un réseau à faible coût d'exploitation pour permettre la réservation des chambres d'hôtels dispersés dans l'archipel d'Hawaï. Pour pallier l'absence de lignes de transmissions, l'idée fut d'utiliser les ondes radiofréquences. Au lieu d'attribuer une fréquence à chaque transmission comme on le faisait avec les technologies de l'époque, tout le monde utiliserait la même fréquence. Un seul support (l'éther) et une seule fréquence allaient donner des collisions entre paquets de données. Le but était de mettre au point des protocoles permettant de résoudre les collisions qui se comportent comme des perturbations analogues à des parasites. Les techniques de réémission permettent ainsi d'obtenir un réseau fiable sur un support qui ne l'est pas. APIPA APIPA (Automatic Private Internet Protocol Addressing) ou IPv4LL est un processus qui permet à un système d'exploitation de s'attribuer automatiquement une adresse IP, lorsque le serveur DHCP est hors service. APIPA utilise la plage d'adresses IP 169.254.0.0/16 (qu'on peut également noter 169.254.0.0/255.255.0.0), c'est-à-dire la plage dont les adresses vont de 169.254.0.0 à 169.254.255.255. -

IN the UNITED STATES BANKRUPTCY COURT for the DISTRICT of DELAWARE in Re: ) Chapter 11 ) NORTEL NETWORKS INC., Et Al. ) Case No
IN THE UNITED STATES BANKRUPTCY COURT FOR THE DISTRICT OF DELAWARE In re: ) Chapter 11 ) NORTEL NETWORKS INC., et al. ) Case No. 09-10138(KG) ) (Jointly Administered) Debtors. ) Re Dkt. No. 18210 SNMP Research International, Inc. and ) SNMP Research, Inc., ) ) Plaintiffs, ) ) v. ) Adv. Proc. No. 11-53454(KG) ) Nortel Networks Inc., et al., ) ) Defendants. ) Re Dkt. No. 585 OPINION MORRIS, NICHOLS, ARSHT & TUNNELL LLP CLEARY GOTTLIEB STEEN & HAMILTON LLP Derek C. Abbott, Esquire Lisa M. Schweitzer, Esquire Andrew R. Remming, Esquire David H. Herrington, Esquire Tamara K. Minott, Esquire One Liberty Plaza Andrew J. Roth-Moore, Esquire New York, New York 10006 1201 North Market Street P.O. Box 1347 Wilmington, Delaware 19801 - Counsel for Debtors and Debtors in Possession – COLE SCHOTZ P.C. KING & BALLOW LAW OFFICES Norman L. Pernick, Esquire Richard S. Busch, Esquire Nicholas J. Brannick, Esquire 315 Union Street, Suite 1100 500 Delaware Avenue, Suite 1410 Nashville, TN 37201 Wilmington, DE 19801 COLE SCHOTZ P.C. EGERTON, MCAFEE, ARMISTEAD G. David Dean, Esquire & DAVIS, P.C. 300 E. Lombard Street, Suite 1450 John L. Wood, Esq. Baltimore, MD 21202 900 S. Gay Street Knoxville, TN 37902 - Counsel for SNMP Research, Inc. and SNMP Research International, Inc. - I. INTRODUCTION1 The litigants in the adversary proceeding are plaintiffs SNMP Research International, Inc. (“SNMPRI”) and SNMP Research, Inc. (“SNMPR”) (collectively, “SNMP”) and the defendants, Nortel Networks Inc. and affiliated entities (“Nortel”). The Court held a two-day trial on May 11 and 12, 2017 (the “Trial”) to determine whether certain software was licensed for use or distribution by Nortel with respect to products after June 20, 2003. -

Sintesi Catalogo Competenze 2
Internet of Things Competenze Campi di applicazione • Progettazione e sviluppo di firmware su micro • Monitoraggio ambientale meteorologico di para- controllori a basso e bassissimo consumo quali ad metri climatici e parametri della qualità dell’aria, esempio Arduino, Microchip, NXP, Texas Instru- anche in mobilità ments e Freescale • Monitoraggio ambientale distribuito per l’agricol- • Sviluppo su PC embedded basati su processori tura di precisione ARM e sistema operativo Linux quali ad esempio • Monitoraggio della qualità dell’acqua e dei parame- Portux, Odroid, RaspberryPI ed Nvidia Jetson tri di rischio ambientale (alluvioni, frane, ecc.) • Progettazione e sviluppo di Wired e Wireless Sen- • Monitoraggio di ambienti indoor (scuole, bibliote- sor Networks basate su standard quali ZigBee, che, uffici pubblici, ecc) SimpliciTI, 6LoWPAN, 802.15.4 e Modbus • Smart building: efficienza energetica, comfort am- • Progettazione e sviluppo di sistemi ad alimentazio- bientale e sicurezza ne autonoma e soluzioni di Energy harvesting • Utilizzo di piattaforme microUAV per misure distri- • Ottimizzazione di software e protocolli wireless buite, per applicazioni di fotogrammetria, teleme- per l’uso efficiente dell’energia all’interno di nodi tria e cartografia, per sistemi di navigazione auto- ad alimentazione autonoma matica basata su sensoristica e image processing, • Design e prototipazione (con strumenti CAD, pianificazione e gestione delle missioni stampante 3D, ecc) di circuiti elettronici per l’inte- • Smart Grid locale per l’ottimizzazione -

CV, Curriculum Vitae, Rhys Haden
Curriculum Vitae Last Updated 2nd February 2016 Rhys Bradley Haden Personal Information Address Telephone E-mail Website Available on Available on [email protected] http://rhyshaden.com enquiry enquiry Date of Birth Nationality Status Driver 30th July 1963 British Married with two children Full clean UK license Key Skills Structured Cabling Design and installation. Integration of building services on to a common data infrastructure. Intelligent Patching Systems design and installation. PC construction. HTML authoring and web site design. Good grounding in Windows network design and installation. Thorough knowledge of TCP/IP addressing, subnetting and summarisation. Solid understanding of IP protocols including HTTP, FTP, Telnet etc. Ethernet, Token Ring and FDDI design and troubleshooting within both shared and switched LAN environments. Thorough knowledge of bridging in both Ethernet and Token Ring environments. Experience in the use of network analysis tools in troubleshooting LANs. ISDN, SMDS, Frame Relay and ATM knowledge and experience, including some LANE. Good routing protocol experience including RIP (1 and 2), OSPF, EIGRP and HSRP/VRRP. Some BGP experience. Good Novell IPX protocol experience. Some DECnet protocol experience. Thorough Nortel Networks equipment experience particularly on the router side. Good experience of designing using, and working with, Extreme Network switches. Thorough knowledge of most of Cisco Systems network equipment range routers, switches and security. Cisco firewall configuration and management. Some experience in IPsec VPN set up. Substantial experience in Content Delivery networks, layer 4-7 switching and HTTP cache engines. Some Experience in IP Telephony and Voice over IP, within the Cisco environment. Wireless LAN design skills. Good teaching skills, including some presentation ability and positive customer- facing attitude. -

Network Devices Configuration Guide
Network Devices Configuration Guide PacketFence v11.0.0 Version 11.0.0 - September 2021 Table of Contents 1. About this Guide . 2 1.1. Other sources of information . 2 2. Note on Inline enforcement support. 3 3. Note on RADIUS accounting . 4 4. List of supported Network Devices. 5 5. Switch configuration . 6 5.1. Assumptions . 6 5.2. 3COM . 6 5.3. Alcatel . 12 5.4. AlliedTelesis . 16 5.5. Amer . 21 5.6. Aruba. 22 5.7. Avaya. 24 5.8. Brocade. 25 5.9. Cisco . 28 5.10. Cisco Small Business (SMB) . 61 5.11. D-Link. 63 5.12. Dell . 65 5.13. Edge core . 70 5.14. Enterasys . 71 5.15. Extreme Networks. 74 5.16. Foundry . 78 5.17. H3C . 80 5.18. HP . 83 5.19. HP ProCurve . 84 5.20. Huawei . 94 5.21. IBM . 97 5.22. Intel. 98 5.23. Juniper . 98 5.24. LG-Ericsson . 104 5.25. Linksys . 105 5.26. Netgear . 106 5.27. Nortel . 108 5.28. Pica8. 110 5.29. SMC . 111 5.30. Ubiquiti. 112 6. Wireless Controllers and Access Point Configuration . 116 6.1. Assumptions. 116 6.2. Unsupported Equipment . 116 6.3. Aerohive Networks . 117 6.4. Anyfi Networks . 135 6.5. Avaya . 138 6.6. Aruba . 138 6.7. Belair Networks (now Ericsson) . 158 6.8. Bluesocket . 158 6.9. Brocade . 159 6.10. Cambium . 159 6.11. Cisco. 163 6.12. CoovaChilli. 204 6.13. D-Link. 206 6.14. Extricom . 206 6.15. Fortinet FortiGate . 207 6.16. Hostapd . -

Red Hat Openstack Platform 12 Networking Guide
Red Hat OpenStack Platform 12 Networking Guide An Advanced Guide to OpenStack Networking Last Updated: 2019-12-04 Red Hat OpenStack Platform 12 Networking Guide An Advanced Guide to OpenStack Networking OpenStack Team [email protected] Legal Notice Copyright © 2019 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Test Results of Nortel and Lucent Units
802.3af Plug Fest Results IEEE November 2000 Plenary Michael McCormack Tampa Units Tested: 1. Nortel unit with two D-Cell power supply 2. Lucent unit with AC power supply Test Method: 1. Verify operation of unit with provided “dummy load” and 1M CAT5 patch cord 2. Plug unit under test into legacy port with 1M CAT5 patch cord 3. Repeat step 2 with all legacy equipment within reach 4. Plug unit under test into legacy port with 1M “Twisted” CAT5 patch cord 5. Repeat step 4 with all legacy equipment within reach 6. Verify operation of unit with provided “dummy load” and 1M CAT5 patch cord Switches / Hubs / Routers MFG Model Problem Liteon LiteSpeed 100 Level One LXD 980 Digital Etherworks 2TTX Edge Access (Canoga Perkins) 9135 Switch Samsung SS6224S Fore ForeRunnere ES-3810 Intel 16 Port 10/100 Hub SynOptics (Bay Networks) 28115 SMC EZ Hub 100 5208TX Intel 6000 Series Intel Express 410F Nortel Networks Falcon 24T Nortel Networks BayStack 450-24T Anritsu Multiflow 5024 Bay Networks Model 5000 (5625 Blade) Intel 330T Stackable Hub Intel Express 550 (4Port Uplink Mod) Intel EtherExpress 10/100 Stackable Hub 802.3af Plug Fest Results IEEE November 2000 Plenary Michael McCormack Tampa Switches / Hubs / Routers MFG Model Problem Intel Express 100Base-TX Stackable Hub Intel Express 100Base-TX Switching Hub Intel Express 510T Intel Express 220T Intel Express 520T SMC Tiger Stack 3312TC SMC TigerStack 100 5324TX SMC TigerStack 100 5300-NMU SMC TigerStack 100 5312TX SMC TigerHub 100 SMC (Cabletron) Tiger Switch (Fast Net 10) Extreme Summit 48-I SMC -
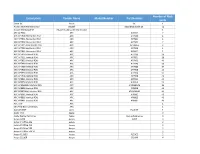
Smartzone 7.1 Device Catalog
Number of Rack Description Vendor Name Model Number Part Number Units 3com 8C 3com 8C 1 Alcatel 3600 Mainstreet 23 Alcatel 3600 Mainstreet 23_ 11 Alcatel Omnistack-24 Alcatel Sistemas de Informacion 1 APC ACF002 APC ACF002 2 APC AP7900 Horizontal PDU APC AP7900 1 APC AP7901 Horizontal PDU APC AP7901 1 APC AP7902 Horizontal PDU APC AP7902 2 APC AP7911A Horizontal PDU APC AP7911A 2 APC AP7920 Horizontal PDU APC AP7920 1 APC AP7921 Horizontal PDU APC AP8921 1 APC AP7930 Vertical PDU APC AP7930 36 APC AP7931 Vertical PDU APC AP7931 28 APC AP7932 Vertical PDU APC AP7932 40 APC AP7940 Vertical PDU APC AP7940 36 APC AP7960 Vertical PDU APC AP7960 37 APC AP7968 Vertical PDU APC AP7968 40 APC AP7990 Vertical PDU APC AP7990 37 APC AP7998 Vertical PDU APC AP7998 40 APC AP8941 Vertical PDU APC AP8941 42 APC AP8958 Vertical PDU APC AP8958 23 APC AP8958NA3 Vertical PDU APC AP8958NA3 23 APC AP8959 Vertical PDU APC AP8959 40 APC AP8959NA3 Vertical PDU APC AP8959NA3 40 APC AP8961 Vertical PDU APC AP8961 40 APC AP8965 Vertical PDU APC AP8965 40 APC AP8981 Vertical PDU APC AP8981 41 APC PDU APC 1 APC PDU Environmentals APC 1 Apex El 40DT Apex El_40DT 1 Apple iPad Apple 0 Apple Xserve Raid array Apple Xserve Raid array 3 Avaya G350 Avaya G350 3 Avaya IP Office 406 Avaya 2 Avaya IP Office 412 Avaya 2 Avaya IP Office 500 Avaya 2 Avaya IP Office 500 V2 Avaya 2 Avaya P133G2 Avaya P133G2 2 Avaya S3210R Avaya S3210R 4 Number of Rack Description Vendor Name Model Number Part Number Units Avaya S8500C Avaya S8500C 1 Avaya S8720 Avaya S8720 2 Nortel 8610 Avaya (Rapid -

ETHERNET TECNOLOGIES 1º: O Que É Ethernet ?
ETHERNET TECNOLOGIES 1º: O Que é Ethernet ? Ethernet Origem: Wikipédia, a enciclopédia livre. Este artigo ou se(c)ção cita fontes fiáveis e independentes, mas que não cobrem todo o conteúdo (desde setembro de 2012). Por favor, adicione mais referências e insira-as no texto ou no rodapé, conforme o livro de estilo. Conteúdo sem fontes poderá serremovido. Encontre fontes: Google (notícias, livros, acadêmico) — Yahoo! — Bing. Protocolos Internet (TCP/IP) Cam Protocolo ada 5.Apl HTTP, SMTP, FTP, SSH,Telnet, SIP, RDP, I icaçã RC,SNMP, NNTP, POP3, IMAP,BitTorrent, o DNS, Ping ... 4.Tra nspo TCP, UDP, RTP, SCTP,DCCP ... rte 3.Re IP (IPv4, IPv6) , ARP, RARP,ICMP, IPsec ... de Ethernet, 802.11 (WiFi),802.1Q 2.Enl (VLAN), 802.1aq ace (SPB), 802.11g, HDLC,Token ring, FDDI,PPP,Switch ,Frame relay, 1.Físi Modem, RDIS, RS-232, EIA-422, RS-449, ca Bluetooth, USB, ... Ethernet é uma arquitetura de interconexão para redes locais - Rede de Área Local (LAN) - baseada no envio de pacotes. Ela define cabeamento e sinais elétricos para a camada física, e formato de pacotes e protocolos para a subcamada de controle de acesso ao meio (Media Access Control - MAC) do modelo OSI.1 A Ethernet foi padronizada pelo IEEE como 802.3. A partir dos anos 90, ela vem sendo a tecnologia de LAN mais amplamente utilizada e tem tomado grande parte do espaço de outros padrões de rede como Token Ring, FDDI e ARCNET.1 Índice [esconder] 1 História 2 Descrição geral 3 Ethernet com meio compartilhado CSMA/CD 4 Hubs Ethernet 5 Ethernet comutada (Switches Ethernet) 6 Tipos de