Red Hat Openstack Platform 12 Networking Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Extreme Networks EXOS V12.3.6.2 EAL3+ ST
Extreme Networks, Inc. ExtremeXOS Network Operating System v12.3.6.2 Security Target Evaluation Assurance Level: EAL3+ Document Version: 0.9 Prepared for: Prepared by: Extreme Networks, Inc. Corsec Security, Inc. 3585 Monroe Street 13135 Lee Jackson Memorial Hwy., Suite 220 Santa Clara, CA 95051 Fairfax, VA 22033 Phone: +1 408 579 2800 Phone: +1 703 267 6050 http://www.extremenetworks.com http://www.corsec.c om Security Target , Version 0.9 March 12, 2012 Table of Contents 1 INTRODUCTION ................................................................................................................... 4 1.1 PURPOSE ................................................................................................................................................................ 4 1.2 SECURITY TARGET AND TOE REFERENCES ...................................................................................................... 4 1.3 TOE OVERVIEW ................................................................................................................................................... 5 1.3.1 TOE Environment ................................................................................................................................................... 5 1.4 TOE DESCRIPTION .............................................................................................................................................. 6 1.4.1 Architecture ............................................................................................................................................................. -

Network Devices Configuration Guide for Packetfence Version 6.5.0 Network Devices Configuration Guide by Inverse Inc
Network Devices Configuration Guide for PacketFence version 6.5.0 Network Devices Configuration Guide by Inverse Inc. Version 6.5.0 - Jan 2017 Copyright © 2017 Inverse inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License". The fonts used in this guide are licensed under the SIL Open Font License, Version 1.1. This license is available with a FAQ at: http:// scripts.sil.org/OFL Copyright © Łukasz Dziedzic, http://www.latofonts.com, with Reserved Font Name: "Lato". Copyright © Raph Levien, http://levien.com/, with Reserved Font Name: "Inconsolata". Table of Contents About this Guide ............................................................................................................... 1 Other sources of information ..................................................................................... 1 Note on Inline enforcement support ................................................................................... 2 List of supported Network Devices ..................................................................................... 3 Switch configuration .......................................................................................................... 4 Assumptions ............................................................................................................ -

Glossaire Des Protocoles Réseau
Glossaire des protocoles réseau - EDITION LIVRES POUR TOUS - http://www.livrespourtous.com/ Mai 2009 A ALOHAnet ALOHAnet, également connu sous le nom ALOHA, est le premier réseau de transmission de données faisant appel à un média unique. Il a été développé par l'université d'Hawaii. Il a été mis en service en 1970 pour permettre les transmissions de données par radio entre les îles. Bien que ce réseau ne soit plus utilisé, ses concepts ont été repris par l'Ethernet. Histoire C'est Norman Abramson qui est à l'origine du projet. L'un des buts était de créer un réseau à faible coût d'exploitation pour permettre la réservation des chambres d'hôtels dispersés dans l'archipel d'Hawaï. Pour pallier l'absence de lignes de transmissions, l'idée fut d'utiliser les ondes radiofréquences. Au lieu d'attribuer une fréquence à chaque transmission comme on le faisait avec les technologies de l'époque, tout le monde utiliserait la même fréquence. Un seul support (l'éther) et une seule fréquence allaient donner des collisions entre paquets de données. Le but était de mettre au point des protocoles permettant de résoudre les collisions qui se comportent comme des perturbations analogues à des parasites. Les techniques de réémission permettent ainsi d'obtenir un réseau fiable sur un support qui ne l'est pas. APIPA APIPA (Automatic Private Internet Protocol Addressing) ou IPv4LL est un processus qui permet à un système d'exploitation de s'attribuer automatiquement une adresse IP, lorsque le serveur DHCP est hors service. APIPA utilise la plage d'adresses IP 169.254.0.0/16 (qu'on peut également noter 169.254.0.0/255.255.0.0), c'est-à-dire la plage dont les adresses vont de 169.254.0.0 à 169.254.255.255. -

Sintesi Catalogo Competenze 2
Internet of Things Competenze Campi di applicazione • Progettazione e sviluppo di firmware su micro • Monitoraggio ambientale meteorologico di para- controllori a basso e bassissimo consumo quali ad metri climatici e parametri della qualità dell’aria, esempio Arduino, Microchip, NXP, Texas Instru- anche in mobilità ments e Freescale • Monitoraggio ambientale distribuito per l’agricol- • Sviluppo su PC embedded basati su processori tura di precisione ARM e sistema operativo Linux quali ad esempio • Monitoraggio della qualità dell’acqua e dei parame- Portux, Odroid, RaspberryPI ed Nvidia Jetson tri di rischio ambientale (alluvioni, frane, ecc.) • Progettazione e sviluppo di Wired e Wireless Sen- • Monitoraggio di ambienti indoor (scuole, bibliote- sor Networks basate su standard quali ZigBee, che, uffici pubblici, ecc) SimpliciTI, 6LoWPAN, 802.15.4 e Modbus • Smart building: efficienza energetica, comfort am- • Progettazione e sviluppo di sistemi ad alimentazio- bientale e sicurezza ne autonoma e soluzioni di Energy harvesting • Utilizzo di piattaforme microUAV per misure distri- • Ottimizzazione di software e protocolli wireless buite, per applicazioni di fotogrammetria, teleme- per l’uso efficiente dell’energia all’interno di nodi tria e cartografia, per sistemi di navigazione auto- ad alimentazione autonoma matica basata su sensoristica e image processing, • Design e prototipazione (con strumenti CAD, pianificazione e gestione delle missioni stampante 3D, ecc) di circuiti elettronici per l’inte- • Smart Grid locale per l’ottimizzazione -

Network Devices Configuration Guide
Network Devices Configuration Guide PacketFence v11.0.0 Version 11.0.0 - September 2021 Table of Contents 1. About this Guide . 2 1.1. Other sources of information . 2 2. Note on Inline enforcement support. 3 3. Note on RADIUS accounting . 4 4. List of supported Network Devices. 5 5. Switch configuration . 6 5.1. Assumptions . 6 5.2. 3COM . 6 5.3. Alcatel . 12 5.4. AlliedTelesis . 16 5.5. Amer . 21 5.6. Aruba. 22 5.7. Avaya. 24 5.8. Brocade. 25 5.9. Cisco . 28 5.10. Cisco Small Business (SMB) . 61 5.11. D-Link. 63 5.12. Dell . 65 5.13. Edge core . 70 5.14. Enterasys . 71 5.15. Extreme Networks. 74 5.16. Foundry . 78 5.17. H3C . 80 5.18. HP . 83 5.19. HP ProCurve . 84 5.20. Huawei . 94 5.21. IBM . 97 5.22. Intel. 98 5.23. Juniper . 98 5.24. LG-Ericsson . 104 5.25. Linksys . 105 5.26. Netgear . 106 5.27. Nortel . 108 5.28. Pica8. 110 5.29. SMC . 111 5.30. Ubiquiti. 112 6. Wireless Controllers and Access Point Configuration . 116 6.1. Assumptions. 116 6.2. Unsupported Equipment . 116 6.3. Aerohive Networks . 117 6.4. Anyfi Networks . 135 6.5. Avaya . 138 6.6. Aruba . 138 6.7. Belair Networks (now Ericsson) . 158 6.8. Bluesocket . 158 6.9. Brocade . 159 6.10. Cambium . 159 6.11. Cisco. 163 6.12. CoovaChilli. 204 6.13. D-Link. 206 6.14. Extricom . 206 6.15. Fortinet FortiGate . 207 6.16. Hostapd . -
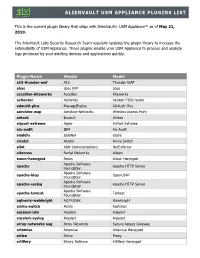
Alienvault Usm Appliance Plugins List
ALIENVAULT USM APPLIANCE PLUGINS LIST This is the current plugin library that ships with AlienVault USM Appliance as of May 21, 2019. The AlienVault Labs Security Research Team regularly updates the plugin library to increase the extensibility of USM Appliance. These plugins enable your USM Appliance to process and analyze logs produced by your existing devices and applications quickly. Plugin Name Vendor Model a10-thunder-waf A10 Thunder WAF abas abas ERP abas accellion-kiteworks Accellion Kiteworks actiontec Actiontec Verizon FIOS router adaudit-plus ManageEngine ADAudit Plus aerohive-wap Aerohive Networks Wireless Access Point airlock Envault Airlock airport-extreme Apple AirPort Extreme aix-audit IBM Aix Audit aladdin SafeNet eSafe alcatel Alcatel Arista Switch allot Allot Communications NetEnforcer alteonos Nortel Networks Alteon amun-honeypot Amun Amun Honeypot Apache Software apache Apache HTTP Server Foundation Apache Software apache-ldap OpenLDAP Foundation Apache Software apache-syslog Apache HTTP Server Foundation Apache Software apache-tomcat Tomcat Foundation aqtronix-webknight AQTRONiX WebKnight arista-switch Arista Switches arpalert-idm Arpalert Arpalert arpalert-syslog Arpalert Arpalert array-networks-sag Array Networks Secure Access Gateway artemisa Artemisa Artemisa Honeypot artica Artica Proxy artillery Binary Defense Artillery Honeypot ALIENVAULT USM APPLIANCE PLUGINS LIST aruba Aruba Networks Mobility Access Switches aruba-6 Aruba Networks Wireless aruba-airwave Aruba Networks Airwave aruba-clearpass Aruba Networks -

Network Monitoring Using Extreme Visualization Performance and Fault Manager Plus
Network Monitoring using Extreme Visualization Performance and Fault Manager Plus Release 1.1 NN48100-500 Issue 02.02 December 2017 © 2017, Extreme Networks, Inc. REPRESENT THAT YOU HAVE THE AUTHORITY TO BIND SUCH All Rights Reserved. ENTITY TO THESE TERMS OF USE. IF YOU DO NOT HAVE SUCH AUTHORITY, OR IF YOU DO NOT WISH TO ACCEPT THESE Notice TERMS OF USE, YOU MUST NOT ACCESS OR USE THE While reasonable efforts have been made to ensure that the HOSTED SERVICE OR AUTHORIZE ANYONE TO ACCESS OR information in this document is complete and accurate at the time of USE THE HOSTED SERVICE. printing, Extreme Networks, Inc. assumes no liability for any errors. Licenses Extreme Networks, Inc. reserves the right to make changes and corrections to the information in this document without the obligation THE SOFTWARE LICENSE TERMS AVAILABLE ON THE to notify any person or organization of such changes. EXTREME NETWORKS WEBSITE, https://extremeportal.force.com OR SUCH SUCCESSOR SITE AS DESIGNATED BY EXTREME Documentation disclaimer NETWORKS, ARE APPLICABLE TO ANYONE WHO “Documentation” means information published in varying mediums DOWNLOADS, USES AND/OR INSTALLS EXTREME NETWORKS which may include product information, operating instructions and SOFTWARE, PURCHASED FROM EXTREME NETWORKS INC., performance specifications that are generally made available to users ANY EXTREME NETWORKS AFFILIATE, OR AN EXTREME of products. Documentation does not include marketing materials. NETWORKS CHANNEL PARTNER (AS APPLICABLE) UNDER A Extreme Networks shall not be responsible for any modifications, COMMERCIAL AGREEMENT WITH EXTREME NETWORKS OR additions, or deletions to the original published version of AN EXTREME NETWORKS CHANNEL PARTNER. -

5–3–06 Vol. 71 No. 85 Wednesday May 3, 2006 Pages 25919–26188
5–3–06 Wednesday Vol. 71 No. 85 May 3, 2006 Pages 25919–26188 VerDate Aug 31 2005 20:07 May 02, 2006 Jkt 208001 PO 00000 Frm 00001 Fmt 4710 Sfmt 4710 E:\FR\FM\03MYWS.LOC 03MYWS jlentini on PROD1PC65 with FRWS II Federal Register / Vol. 71, No. 85 / Wednesday, May 3, 2006 The FEDERAL REGISTER (ISSN 0097–6326) is published daily, SUBSCRIPTIONS AND COPIES Monday through Friday, except official holidays, by the Office PUBLIC of the Federal Register, National Archives and Records Administration, Washington, DC 20408, under the Federal Register Subscriptions: Act (44 U.S.C. Ch. 15) and the regulations of the Administrative Paper or fiche 202–512–1800 Committee of the Federal Register (1 CFR Ch. I). The Assistance with public subscriptions 202–512–1806 Superintendent of Documents, U.S. Government Printing Office, Washington, DC 20402 is the exclusive distributor of the official General online information 202–512–1530; 1–888–293–6498 edition. Periodicals postage is paid at Washington, DC. Single copies/back copies: The FEDERAL REGISTER provides a uniform system for making Paper or fiche 202–512–1800 available to the public regulations and legal notices issued by Assistance with public single copies 1–866–512–1800 Federal agencies. These include Presidential proclamations and (Toll-Free) Executive Orders, Federal agency documents having general FEDERAL AGENCIES applicability and legal effect, documents required to be published Subscriptions: by act of Congress, and other Federal agency documents of public interest. Paper or fiche 202–741–6005 Documents are on file for public inspection in the Office of the Assistance with Federal agency subscriptions 202–741–6005 Federal Register the day before they are published, unless the issuing agency requests earlier filing. -

Packetfence Network Devices Configuration Guide for Version 4.2.1 Packetfence Network Devices Configuration Guide by Inverse Inc
PacketFence Network Devices Configuration Guide for version 4.2.1 PacketFence Network Devices Configuration Guide by Inverse Inc. Version 4.2.1 - May 2014 Copyright © 2010-2014 Inverse inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License". The fonts used in this guide are licensed under the SIL Open Font License, Version 1.1. This license is available with a FAQ at: http://scripts.sil.org/OFL Copyright © Barry Schwartz, http://www.crudfactory.com, with Reserved Font Name: "Sorts Mill Goudy". Copyright © Raph Levien, http://levien.com/, with Reserved Font Name: "Inconsolata". Table of Contents About this Guide ................................................................................................................ 1 Other sources of information ........................................................................................ 1 Note on Inline enforcement support ...................................................................................... 2 List of supported Network Devices ........................................................................................ 3 Switch configuration ............................................................................................................ 4 Assumptions -
Extremexos Quick Guide
ExtremeXOS Quick Guide 121131-00 Published November 2015 Copyright © 2011–2015 All rights reserved. Legal Notice Extreme Networks, Inc. reserves the right to make changes in specifications and other information contained in this document and its website without prior notice. The reader should in all cases consult representatives of Extreme Networks to determine whether any such changes have been made. The hardware, firmware, software or any specifications described or referred to in this document are subject to change without notice. Trademarks Extreme Networks and the Extreme Networks logo are trademarks or registered trademarks of Extreme Networks, Inc. in the United States and/or other countries. All other names (including any product names) mentioned in this document are the property of their respective owners and may be trademarks or registered trademarks of their respective companies/owners. For additional information on Extreme Networks trademarks, please see: www.extremenetworks.com/company/legal/trademarks/ Support For product support, including documentation, visit: www.extremenetworks.com/ documentation/ For information, contact: Extreme Networks, Inc. 145 Rio Robles San Jose, California 95134 USA Table of Contents Preface......................................................................................................................................... 5 Text Conventions................................................................................................................................................................. -

Networking Market Primer
Networking Market Primer Focus Research Networking Group May 2009 Focus Research © 2009 All Rights Reserved Introduction Not sure where to start with networking? Building a local area network is a serious endeavor, and it can be difficult to know where to begin. Our Networking Market Primer is intended to provide CEOs, IT administrators and anyone else involved in making a first-time networking purchase with a fundamental understanding of network storage hardware and software. In this Market Primer, you’ll find: Table of Contents 1 Networking Basics: Market definition and the top 10 things to know about local area networks . p. 3 2 Market Summary: Market trends and vendor landscape . p. 6 3 Product In-Depth: Requirements, support and cost . p. 9 4 Tools: Glossary, checklists and vendor list . p. 16 Networking Market Primer Focus Research ©2009 2 1 Networking Basics Networking Defined The largest network in the world is the Web, which creates a grid of thousands of PCs and servers all over the world. But a network can be as simple as just two or three computers connected so that users can share data and compute resources. Most modern business networks are built in the client/server model — PCs are the clients that make application requests to the server — and include routers and switches to connect PCs, laptops, printers and other peripherals. A network is made more useful by software, which includes performance and monitoring tools to keep network traffic moving smoothly and efficiently, NOSes (network operating systems) to get computers online, and security applications to protect it from the outside world. -

Technology Integration Guide
TECHNOLOGY INTEGRATION GUIDE INTRODUCTION RedSeal’s cyber terrain analytics platform unifies public cloud, private cloud and physical network environments into one, interactive model. Customers see how (or if) data can move within and between environments. RedSeal overlays host and endpoint information along with identified vulnerabilities. Risk and compliance managers can see if their network is set up as intended and get alerts if anything changes. Vulnerability managers can identify areas their scanners are missing and improve their prioritization with RedSeal’s vulnerability risk calculations. Incident responders can speed their investigation and containment with the network situational awareness RedSeal supplies, and network security personnel can validate and manage their segmentation and test changes to see if they’ll violate any policies. RedSeal continues to license its standard software based on the number of layer 3 (L3) devices, layer 2(L2) devices, CIS/STIG checks and Cloud/SDN technologies. Any integration without † is not standard and requires an additional license. REDSEAL SDN/CLOUD INTEGRATIONS Amazon AWS† Amazon C2S† Cisco ACI up to version 4.2.x† Google Cloud Platform† Microsoft Azure† Oracle Cloud Infrastructure† VMware NSX Manager up to version 6.4.x† † Included with your standard RedSeal license SERVICE CHAINS Amazon AWS with VMware NSX ALB (AVI LB) Amazon AWS with Palo Alto NGFW Cisco ACI with Cisco ASAv firewalls Cisco ACI with HAProxy load balancer Cisco ACI with Palo Alto NGFW Microsoft Azure with Fortinet NGFW