Extreme Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Annual Report 2011
Table of Contents 004 (I)Important Notes 005 (II)Company Profile 007 (III)Financial and Operating Highlights 010 (IV)Changes in Equity and Shareholders 017 (V)Directors, Supervisors and Senior Management 026 (VI)Corporate Governance 034 (VII)Shareholders’Meeting 035 (VIII)Reports of the Board of Directors 061 (IX)Reports of the Board of Supervisors 063 (X)Important issues 075 (XI)Financial Report 203 (XII)Documents Available For Inspection Neusoft Corporation Annual Report 2011 The year 2011 saw the 20th anniversary of Neusoft, a milestone year for us. Focusing on business model innovation, global strategy and operational excellence, we have mapped out future development strategies to build up necessary power and capacities for a sustainable growth. In the aspect of business model innovation, we have been devoted to building a company driven by innovation and service through leveraging our competitiveness and com- petence. In the aspect of global strategy, we have combined all business lines in and outside China, making all products and services available in both local and international markets. In the aspect of operational excellence, we have made some reforms covering organization, technology, culture, leadership and human resources to ensure that Neusoft operates at in- creasingly high efficiency levels. However, the past years were merely a start for our future adventure at Neusoft. We need more entrepreneurial employees to stand out and continue our growth with passion and wisdom. In the coming years, Neusoft will strive to maintain -

Extreme Networks EXOS V12.3.6.2 EAL3+ ST
Extreme Networks, Inc. ExtremeXOS Network Operating System v12.3.6.2 Security Target Evaluation Assurance Level: EAL3+ Document Version: 0.9 Prepared for: Prepared by: Extreme Networks, Inc. Corsec Security, Inc. 3585 Monroe Street 13135 Lee Jackson Memorial Hwy., Suite 220 Santa Clara, CA 95051 Fairfax, VA 22033 Phone: +1 408 579 2800 Phone: +1 703 267 6050 http://www.extremenetworks.com http://www.corsec.c om Security Target , Version 0.9 March 12, 2012 Table of Contents 1 INTRODUCTION ................................................................................................................... 4 1.1 PURPOSE ................................................................................................................................................................ 4 1.2 SECURITY TARGET AND TOE REFERENCES ...................................................................................................... 4 1.3 TOE OVERVIEW ................................................................................................................................................... 5 1.3.1 TOE Environment ................................................................................................................................................... 5 1.4 TOE DESCRIPTION .............................................................................................................................................. 6 1.4.1 Architecture ............................................................................................................................................................. -

Deliverable No. 5.3 Techniques to Build the Cloud Infrastructure Available to the Community
Deliverable No. 5.3 Techniques to build the cloud infrastructure available to the community Grant Agreement No.: 600841 Deliverable No.: D5.3 Deliverable Name: Techniques to build the cloud infrastructure available to the community Contractual Submission Date: 31/03/2015 Actual Submission Date: 31/03/2015 Dissemination Level PU Public X PP Restricted to other programme participants (including the Commission Services) RE Restricted to a group specified by the consortium (including the Commission Services) CO Confidential, only for members of the consortium (including the Commission Services) Grant Agreement no. 600841 D5.3 – Techniques to build the cloud infrastructure available to the community COVER AND CONTROL PAGE OF DOCUMENT Project Acronym: CHIC Project Full Name: Computational Horizons In Cancer (CHIC): Developing Meta- and Hyper-Multiscale Models and Repositories for In Silico Oncology Deliverable No.: D5.3 Document name: Techniques to build the cloud infrastructure available to the community Nature (R, P, D, O)1 R Dissemination Level (PU, PP, PU RE, CO)2 Version: 1.0 Actual Submission Date: 31/03/2015 Editor: Manolis Tsiknakis Institution: FORTH E-Mail: [email protected] ABSTRACT: This deliverable reports on the technologies, techniques and configuration needed to install, configure, maintain and run a private cloud infrastructure for productive usage. KEYWORD LIST: Cloud infrastructure, OpenStack, Eucalyptus, CloudStack, VMware vSphere, virtualization, computation, storage, security, architecture. The research leading to these results has received funding from the European Community's Seventh Framework Programme (FP7/2007-2013) under grant agreement no 600841. The author is solely responsible for its content, it does not represent the opinion of the European Community and the Community is not responsible for any use that might be made of data appearing therein. -

MCP Q4`18 Release Notes Version Q4-18 Mirantis Cloud Platform Release Notes Version Q4`18
MCP Q4`18 Release Notes version q4-18 Mirantis Cloud Platform Release Notes version Q4`18 Copyright notice 2021 Mirantis, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. No part of this publication may be reproduced in any written, electronic, recording, or photocopying form without written permission of Mirantis, Inc. Mirantis, Inc. reserves the right to modify the content of this document at any time without prior notice. Functionality described in the document may not be available at the moment. The document contains the latest information at the time of publication. Mirantis, Inc. and the Mirantis Logo are trademarks of Mirantis, Inc. and/or its affiliates in the United States an other countries. Third party trademarks, service marks, and names mentioned in this document are the properties of their respective owners. ©2021, Mirantis Inc. Page 2 Mirantis Cloud Platform Release Notes version Q4`18 What’s new This section provides the details about the features and enhancements introduced with the latest MCP release version. Note The MCP integration of the community software projects, such as OpenStack, Kubernetes, OpenContrail, and Ceph, includes the integration of the features which the MCP consumers can benefit from. Refer to the MCP Q4`18 Deployment Guide for the software features that can be deployed and managed by MCP DriveTrain. MCP DriveTrain • Encryption of sensitive data in the Reclass model • Galera verification and restoration pipeline • Jenkins version upgrade • Partitioning table for the VCP images Encryption of sensitive data in the Reclass model SECURITY Implemented the GPG encryption to protect sensitive data in the Git repositories of the Reclass model as well as the key management mechanism for secrets encryption and decryption. -

Examining Factors of the NFV-I Impacting Performance and Portability
WHITE PAPER Examining Factors of the NFV-I Impacting Performance and Portability www.ixiacom.com 915-0953-01 Rev. A, May 2015 2 Table of Contents Introduction ................................................................................................. 4 Compute Platform ........................................................................................ 7 CPU/Motherboard and Storage .............................................................. 8 CPU Pinning ........................................................................................... 9 Logical Processor Support ................................................................... 11 QuickPath Interconnect (QPI) ...............................................................12 Packet Processing Enhancements and Acceleration ............................13 Storage .................................................................................................16 Network Interface Cards (NICs) .................................................................17 PCI Passthrough ...................................................................................18 Single Root I/O Virtualization (SR-IOV) ...............................................18 Host OS and Hypervisor ............................................................................21 Open Source NFV-I Platforms ............................................................. 23 Know the Performance Curve ............................................................. 24 Virtual Networking ................................................................................... -

Exploring Platform Ecosystems: a Comparison of Complementor Networks and Their Characteristics
Exploring Platform Ecosystems: A Comparison of Complementor Networks and their Characteristics Joey van Angeren [email protected] Utrecht University Department of Information and Computing Sciences Master in Business Informatics MSc. thesis submitted under supervision of: First supervisor: Dr. Slinger Jansen (Utrecht University) Second supervisor: Prof. dr. Sjaak Brinkkemper (Utrecht University) November 2013 Abstract Owners of software platforms are increasingly dependent on developers of complemen- tarities. As the proprietary platform itself exhibits elementary or generic functionality, platform owners depend on a complementor ecosystem populated by third-parties. As such, the ecosystem became a pivotal determinant for the success or failure of a software platform in platform-based competition. At present, little is known about mechanisms at play in proprietary platform ecosystems, and it remains unclear how these ecosystems differ from each other across firms and platform types. Addressing this deficiency, this thesis investigates and contrasts four proprietary platform ecosystems through statistical and network analysis. The research compares the ecosystems that exist around Google Apps, Google Chrome, Office365 and Internet Explorer, with data obtained by means of automated app store data extraction and interfirm relationships obtained from company websites and Crunch- Base. Results show similarities among the four proprietary platform ecosystems. The ecosystems are sparsely connected and highly centralized, since 3.18% to 29.82% of com- plementors initiated interfirm relationships. Furthermore, the ecosystems are predomi- nantly populated by complementors that limitedly commit to application development, the average number of applications developed per complementor ranges from 1.34 to 2.18. This is especially apparent in the Google Apps and Office365 ecosystems, that display strong characteristics of power law scaling in the distribution of the number of applications developed per complementor. -

Microsoft Dynamics CRM Online Small and Medium Business – Frequently Asked Questions
Microsoft Dynamics CRM Online Small and medium business – frequently asked questions Answers to frequently asked questions by prospects Use this document to get answers to frequently asked questions about Microsoft Dynamics CRM Online for small and medium businesses. For help determining the right technology solution for your business, including the license requirements and pricing information, consult with a Microsoft Dynamics Certified Partner. This document does not supersede or replace any of the legal documentation covering use rights. Microsoft Corporation reserves the right to revise the existing version without prior notice. 1. Product capabilities................................................................................................................................................. 2 1.1 What is Microsoft Dynamics CRM Online? ............................................................................................................................ 2 1.2 What can Dynamics CRM Online help us do? ...................................................................................................................... 2 1.3 How does Dynamics CRM Online work with Office 365? ................................................................................................. 2 1.4 How can my organization learn more about Dynamics CRM Online? ........................................................................ 2 1.5 Are there industry-specific Dynamics CRM Online solutions? ...................................................................................... -
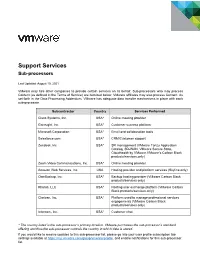
Support Services Sub-Processors
Support Services Sub-processors Last Updated: August 10, 2021 VMware may hire other companies to provide certain services on its behalf. Sub-processors who may process Content (as defined in the Terms of Service) are itemized below. VMware affiliates may also process Content. As set forth in the Data Processing Addendum, VMware has adequate data transfer mechanisms in place with each sub-processor. Subcontractor Country Services Performed Cisco Systems, Inc. USA* Online meeting provider Gainsight, Inc. USA* Customer success platform Microsoft Corporation USA* Email and collaboration tools Salesforce.com USA* CRM/Customer support Zendesk, Inc USA* SR management (VMware Tanzu Application Catalog, SD-WAN, VMware Secure State, Cloudhealth by VMware,VMware’s Carbon Black products/services, only) Zoom Video Communications, Inc. USA* Online meeting provider Amazon Web Services, Inc. USA Hosting provider and platform services (Skyline only) OwnBackup, Inc. USA* Backup hosting provider (VMware Carbon Black products/services only) Khoros, LLC USA* Hosting user exchange platform (VMware Carbon Black products/services only) Clarizen, Inc. USA* Platform used to manage professional services engagements (VMware Carbon Black products/services only) Intercom, Inc. USA* Customer chat * The country listed is the sub-processor’s primary location. VMware purchases the sub-processor’s standard offering and thus the sub-processor controls the country in which data is stored. If you would like to receive updates to this sub-processor list, please go into your user profile subscription tab settings available at https://my.vmware.com/group/vmware/profile, and enable notifications for this sub-processor list. Sub-processors who provide contract staff The following sub-processors provide contract staff that work in close coordination with VMware staff to help provide the support services to VMware customers and in the course of doing so may be exposed to Your Content/Support Request Content (including personal data contained therein). -
China Computer Software Industry Report, 2014-2017
China Computer Software Industry Report, 2014-2017 Apr. 2014 STUDY GOAL AND OBJECTIVES METHODOLOGY This report provides the industry executives with strategically significant Both primary and secondary research methodologies were used competitor information, analysis, insight and projection on the in preparing this study. Initially, a comprehensive and exhaustive competitive pattern and key companies in the industry, crucial to the search of the literature on this industry was conducted. These development and implementation of effective business, marketing and sources included related books and journals, trade literature, R&D programs. marketing literature, other product/promotional literature, annual reports, security analyst reports, and other publications. REPORT OBJECTIVES Subsequently, telephone interviews or email correspondence To establish a comprehensive, factual, annually updated and cost- was conducted with marketing executives etc. Other sources effective information base on market size, competition patterns, included related magazines, academics, and consulting market segments, goals and strategies of the leading players in the companies. market, reviews and forecasts. To assist potential market entrants in evaluating prospective INFORMATION SOURCES acquisition and joint venture candidates. The primary information sources include Company Reports, To complement the organizations’ internal competitor information and National Bureau of Statistics of China etc. gathering efforts with strategic analysis, data interpretation -

Google Cloud Platform (GCP): Возможности И Преимущества
Google Cloud Platform (GCP): возможности и преимущества Дмитрий Новаковский, Олег Ивонин Январь 2017 Кто мы? Дмитрий Новаковский / [email protected] ● Customer Engineer @ Google Netherlands B.V. ● Поддержка продаж и разработка решений на основе GCE, GKE, GAE ● В прошлом: ○ IaaS/PaaS (OpenStack @ Mirantis) ○ SaaS (ETAdirect @ TOA Technologies/Oracle) Олег Ивонин / [email protected] ● Cloud Web Solutions Engineer @ Google Netherlands B.V. ● Разработка инструментов для анализа стоимости конфигураций и планирования архитектуры облачных решений на основе GCP ○ Google Cloud Platform Pricing Calculator и другие О чем мы расскажем? ● Часть 1: Google Cloud Platform 101 ○ Наборы облачных сервисов и их назначение ○ Преимущества на рынке ● Часть 2: Инфраструктурные сервисы GCP (IaaS/PaaS) ○ GCE - Виртуальные машины ○ GKE - Оркестрация Docker контейнеров ○ GAE - NoOps/PaaS окружения ● Часть 3: Big Data и Machine Learning инструменты GCP ● Часть 4: Примеры, итоги и вопросы/ответы Disclaimer Google Cloud Platform 4 Часть 1: Google Cloud Platform 101 Google Cloud Platform 5 Путь IT-инфраструктуры в “облако” Storage Processing Memory Network Storage Processing Memory Network Physical / Self-Service / Serverless / Colo / VPS Elastic / IaaS NoOps / PaaS Google Cloud Platform 6 Что такое Google Cloud Platform? GCP - это набор коммерческих облачных сервисов, основанных на разработках и опыте Google в для собственных продуктов: ● Google Search ● YouTube ● Google Maps ● и др. Google’s Data Research Flume MapReduce Dremel Millwheel TensorFlow GFS Megastore -
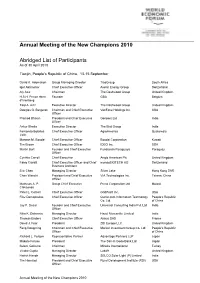
Annual Meeting of the New Champions 2010 Abridged List Of
Annual Meeting of the New Champions 2010 Abridged List of Participants As of 30 April 2010 Tianjin, People's Republic of China, 13-15 September David K. Adomakoh Group Managing Director TisoGroup South Africa Igor Akhmerov Chief Executive Officer Avelar Energy Group Switzerland Aly Aziz Chairman The Dashwood Group United Kingdom H.S.H. Prince Henri Founder GBA Belgium d'Arenberg Taqi A. Aziz Executive Director The Dashwood Group United Kingdom Douglas G. Bergeron Chairman and Chief Executive VeriFone Holdings Inc. USA Officer Pramod Bhasin President and Chief Executive Genpact Ltd India Officer Ankur Bhatia Executive Director The Bird Group India Fernando Bolaños Chief Executive Officer AgroAmerica Guatemala Valle Marwan M. Boodai Chief Executive Officer Boodai Corporation Kuwait Tim Brown Chief Executive Officer IDEO Inc. USA Martin Burt Founder and Chief Executive Fundación Paraguaya Paraguay Officer Cynthia Carroll Chief Executive Anglo American Plc United Kingdom Fabio Cavalli Chief Executive Officer and Chief mondoBIOTECH AG Switzerland Business Architect Eric Chen Managing Director Silver Lake Hong Kong SAR Chen Wenchi President and Chief Executive VIA Technologies Inc. Taiwan, China Officer Mathews A. P. Group Chief Executive Press Corporation Ltd Malawi Chikaonda Peter L. Corsell Chief Executive Officer GridPoint Inc. USA Fritz Demopoulos Chief Executive Officer Qunar.com Information Technology People's Republic Co. Ltd. of China Jay P. Desai Founder and Chief Executive Universal Consulting India Pvt. Ltd India Officer Nitin K. Didwania Managing Director Hazel Mercantile Limited India Thomas Enders Chief Executive Officer Airbus SAS France David J. Fear President ZBI Europe LLC United Kingdom Feng Dongming Chairman and Chief Executive Markor Investment Group Co. -

Network Devices Configuration Guide for Packetfence Version 6.5.0 Network Devices Configuration Guide by Inverse Inc
Network Devices Configuration Guide for PacketFence version 6.5.0 Network Devices Configuration Guide by Inverse Inc. Version 6.5.0 - Jan 2017 Copyright © 2017 Inverse inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License". The fonts used in this guide are licensed under the SIL Open Font License, Version 1.1. This license is available with a FAQ at: http:// scripts.sil.org/OFL Copyright © Łukasz Dziedzic, http://www.latofonts.com, with Reserved Font Name: "Lato". Copyright © Raph Levien, http://levien.com/, with Reserved Font Name: "Inconsolata". Table of Contents About this Guide ............................................................................................................... 1 Other sources of information ..................................................................................... 1 Note on Inline enforcement support ................................................................................... 2 List of supported Network Devices ..................................................................................... 3 Switch configuration .......................................................................................................... 4 Assumptions ............................................................................................................