By Vladan Djeric a Thesis Submitted in Conformity with the Requirements For
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Cross Site Scripting Attacks Xss Exploits and Defense.Pdf
436_XSS_FM.qxd 4/20/07 1:18 PM Page ii 436_XSS_FM.qxd 4/20/07 1:18 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and deliv- ering those books in media and formats that fit the demands of our customers. We are also committed to extending the utility of the book you purchase via additional mate- rials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value- added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of expertise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in downloadable Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -
Design Decisions for a Structured Front End to LATEX Documents
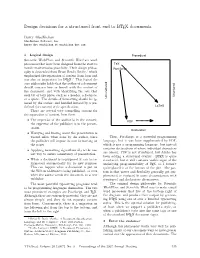
Design decisions for a structured front end to LATEX documents Barry MacKichan MacKichan Software, Inc. barry dot mackichan at mackichan dot com 1 Logical design Procedural Scientific WorkPlace and Scientific Word are word processors that have been designed from the start to TeX handle mathematics gracefully. Their design philos- PostScript ophy is descended from Brian Reid’s Scribe,1 which emphasized the separation of content from form and 2 was also an inspiration for LATEX. This logical de- sign philosophy holds that the author of a document should concern him- or herself with the content of the document, and with identifying the role that each bit of text plays, such as a header, a footnote, Structured or a quote. The details of formatting should be ig- Unstructured nored by the author, and handled instead by a pre- defined (or custom) style specification. LaTeX There are several very compelling reasons for the separation of content from form. • The expertise of the author is in the content; PDF the expertise of the publisher is in the presen- tation. Declarative • Worrying and fussing about the presentation is wasted effort when done by the author, since Thus, PostScript is a powerful programming the publisher will impose its own formatting on language, but it was later supplemented by PDF, the paper. which is not a programming language, but instead contains declarations of where individual characters • Applying formatting algorithmically is the eas- are placed. PDF is not structured, but Adobe has iest way to assure consistency of presentation. been adding a structural overlay. LATEX is quite • When a document is re-purposed it can be re- structured, but it still contains visible signs of the formatted automatically for its new purpose. -

Firefox Hacks Is Ideal for Power Users Who Want to Maximize The
Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader Firefox Hacks is ideal for power users who want to maximize the • Reviews effectiveness of Firefox, the next-generation web browser that is quickly • Errata gaining in popularity. This highly-focused book offers all the valuable tips • Academic and tools you need to enjoy a superior and safer browsing experience. Learn how to customize its deployment, appearance, features, and functionality. Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader • Reviews • Errata • Academic Copyright Credits About the Author Contributors Acknowledgments Preface Why Firefox Hacks? How to Use This Book How This Book Is Organized Conventions Used in This Book Using Code Examples Safari® Enabled How to Contact Us Got a Hack? Chapter 1. Firefox Basics Section 1.1. Hacks 1-10 Section 1.2. Get Oriented Hack 1. Ten Ways to Display a Web Page Hack 2. Ten Ways to Navigate to a Web Page Hack 3. Find Stuff Hack 4. Identify and Use Toolbar Icons Hack 5. Use Keyboard Shortcuts Hack 6. Make Firefox Look Different Hack 7. Stop Once-Only Dialogs Safely Hack 8. Flush and Clear Absolutely Everything Hack 9. Make Firefox Go Fast Hack 10. Start Up from the Command Line Chapter 2. Security Section 2.1. Hacks 11-21 Hack 11. Drop Miscellaneous Security Blocks Hack 12. Raise Security to Protect Dummies Hack 13. Stop All Secret Network Activity Hack 14. -

Here.Is.Only.Xul
Who am I? Alex Olszewski Elucidar Software Co-founder Lead Developer What this presentation is about? I was personally assigned to see how XUL and the Mozilla way measured up to RIA application development standards. This presentation will share my journey and ideas and hopefully open your minds to using these concepts for application development. RIA and what it means Different to many “Web Applications” that have features and functions of “Desktop” applications Easy install (generally requires only application install) or one-time extra(plug in) Updates automatically through network connections Keeps UI state on desktop and application state on server Runs in a browser or known “Sandbox” environment but has ability to access native OS calls to mimic desktop applications Designers can use asynchronous communication to make applications more responsive RIA and what it means(continued) Success of RIA application will ultimately be measured by how will it can match user’s needs, their way of thinking, and their behaviour. To review RIA applications take advantage of the “best” of both web and desktop apps. Sources: http://www.keynote.com/docs/whitepapers/RichInternet_5.pdf http://en.wikipedia.org/wiki/Rich_Internet_application My First Steps • Find working examples Known Mozilla Applications Firefox Thunderbird Standalone Applications Songbird Joost Komodo FindthatFont Prism (formerly webrunner) http://labs.mozilla.com/featured- projects/#prism XulMine-demo app http://benjamin.smedbergs.us/XULRunner/ Mozilla -

Mozilla Development Roadmap
mozilla development roadmap Brendan Eich, David Hyatt table of contents • introduction • milestone schedule • about ownership... • a new • current release • what all this does not roadmap status mean • discussion • how you can help • application architecture • summary • project • to-do list rationale management introduction Welcome to the Mozilla development roadmap. This is the third major roadmap revision, with a notable recent change to the status of the integrated Mozilla application suite, since the original roadmap that set Mozilla on a new course for standards compliance, modularity, and portability in 1998. The previous roadmap documented milestones and rules of development through Mozilla 1.3, and contains links to older roadmaps. Most of this document reflects the new application architecture proposal made last year. The effort resulting from that proposal has finally borne fruit, or to mix metaphors, hatched new application creatures: Firefox and Thunderbird. The new, significant roadmap update hoped for early in 2004 has been postponed. See Brendan's roadmap blog for thoughts that may feed into it. An interim roadmap update focused on the "aviary 1.0" 1 From www.mozilla.org/roadmap.html 4 August 2004 releases of Firefox 1.0 and Thunderbird 1.0, and the 1.8 milestone that will follow, is coming soon. We have come a long way. We have achieved a Mozilla 1.0 milestone that satisfies the criteria put forth in the Mozilla 1.0 manifesto, giving the community and the wider world a high-quality release, and a stable branch for conservative development and derivative product releases. See the Mozilla Hall of Fame for a list of Mozilla-based projects and products that benefited from 1.0. -

Extending Your Browser
Extending your browser •Philip Roche – Karova •[email protected] •http://www.philroche.net/downloads Introduction – Today I’d like to discuss Mozilla as an application development framework, discussing the technologies used in that framework. I’d also like to discuss the Firefox web browser and some of it’s features. I will be talking about three Firefox extensions in particular. I will then attempt to put all that together by showing you the code of an extension I have been developing If you have any questions – don’t hesitate to ask. 1 Introduction Who are Mozilla? What is Firefox? What is Mozilla Application Framework? What is Gecko? 06/02/2007 Extending your browser 2 Mozilla The Mozilla Foundation is a free software/open source project that was founded in order to create the next-generation Internet suite for Netscape. In 2005, the Mozilla Foundation announced the creation of Mozilla Corporation, a wholly owned for-profit taxable subsidiary of Mozilla Foundation, that will focus on delivering Firefox and Thunderbird to end users. It is because of the Mozilla Corporation’s work that we have seen the increase in Firefox’s user base to 31% (w3schools.com jan 2007 stats). Firefox Firefox is a freely available cross-platform browser. Mozilla application framework Also known as XPFE or XPToolkit. A collection of cross-platform software components, One of which is the Gecko Layout engine. Gecko Gecko is a standard-based layout engine designed for performance and portability. The terms Gecko and Mozilla Application Framework tend to interchanged but Gecko is the layout engine that is part of the Mozilla Application Framework collection. -

SLES Security Guide-EAL3
SLES Security Guide Klaus Weidner <[email protected]> December 4, 2003; v2.33 atsec is a trademark of atsec GmbH IBM, IBM logo, BladeCenter, eServer, iSeries, OS/400, PowerPC, POWER3, POWER4, POWER4+, pSeries, S390, xSeries, zSeries, zArchitecture, and z/VM are trademarks or registered trademarks of International Business Machines Corporation in the United States, other countries, or both. Intel and Pentium are trademarks of Intel Corporation in the United States, other countries, or both. Java and all Java-based products are trademarks of Sun Microsystems, Inc., in the United States, other countries, or both. Linux is a registered trademark of Linus Torvalds. UNIX is a registered trademark of The Open Group in the United States and other countries. This document is provided AS IS with no express or implied warranties. Use the information in this document at your own risk. This document may be reproduced or distributed in any form without prior permission provided the copyright notice is retained on all copies. Modified versions of this document may be freely distributed provided that they are clearly identified as such, and this copyright is included intact. Copyright (c) 2003 by atsec GmbH, and IBM Corporation or its wholly owned subsidiaries. 2 Contents 1 Introduction 6 1.1 Purpose of this document . 6 1.2 How to use this document . 6 1.3 What is a CC compliant System? . 6 1.3.1 Hardware requirements . 7 1.3.2 Software requirements . 7 1.3.3 Environmental requirements . 7 1.3.4 Operational requirements . 7 1.4 Requirements for the system’s environment . -

Standoff Markup Peter L
Enhancing composite Digital Documents Using XML-based Standoff Markup Peter L. Thomas David F. Brailsford Document Engineering Laboratory Document Engineering Laboratory School of Computer Science School of Computer Science University of Nottingham University of Nottingham Nottingham, NG8 1BB, UK Nottingham, NG8 1BB, UK [email protected] [email protected] ABSTRACT 1. INTRODUCTION Document representations can rapidly become unwieldy if they In two previous papers [1, 2] we have set out techniques for try to encapsulate all possible document properties, ranging using XML templates as a guide for embedding customised from abstract structure to detailed rendering and layout. structure into PDF files. A Structured PDF file usually marks up its PDF content with the Adobe Standard Structured Tagset We present a composite document approach wherein an XML- (SST). The SST Tags (see [3]) are roughly equivalent to those based document representation is linked via a ‘shadow tree’ of in HTML in that they denote document components such as bi-directional pointers to a PDF representation of the same paragraphs, titles, headings etc. Unlike XML, it is not possible document. Using a two-window viewer any material selected to directly intermix SST tags and PDF content. Instead, the in the PDF can be related back to the corresponding material in tags comprise the nodes of a separate structure tree and each of the XML, and vice versa. In this way the treatment of specialist these nodes contains a pointer to a linked list of marked material such as mathematics, music or chemistry (e.g. via ‘read content within the PDF itself. -

O'reilly Programming Firefox.Pdf
Programming Firefox Kenneth C. Feldt Beijing • Cambridge • Farnham • Köln • Paris • Sebastopol • Taipei • Tokyo Programming Firefox by Kenneth C. Feldt Copyright © 2007 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Simon St.Laurent Indexer: Reg Aubry Production Editor: Rachel Monaghan Cover Designer: Karen Montgomery Copyeditor: Audrey Doyle Interior Designer: David Futato Proofreader: Rachel Monaghan Illustrators: Robert Romano and Jessamyn Read Printing History: April 2007: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. Programming Firefox, the image of a red fox, and related trade dress are trademarks of O’Reilly Media, Inc. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. This book uses RepKover™, a durable and flexible lay-flat binding. ISBN-10: 0-596-10243-7 ISBN-13: 978-0-596-10243-2 [M] Table of Contents Preface . -

Proceedings of the 4Th Annual Linux Showcase & Conference, Atlanta
USENIX Association Proceedings of the 4th Annual Linux Showcase & Conference, Atlanta Atlanta, Georgia, USA October 10 –14, 2000 THE ADVANCED COMPUTING SYSTEMS ASSOCIATION © 2000 by The USENIX Association All Rights Reserved For more information about the USENIX Association: Phone: 1 510 528 8649 FAX: 1 510 548 5738 Email: [email protected] WWW: http://www.usenix.org Rights to individual papers remain with the author or the author's employer. Permission is granted for noncommercial reproduction of the work for educational or research purposes. This copyright notice must be included in the reproduced paper. USENIX acknowledges all trademarks herein. Mozilla as a cross-platform application development framework David Ascher, Eric Promislow, Dick Hardt ActiveState Tool Corporation 1 Outline • Overview of Mozilla as an application development framework • Building portable user interfaces with XUL, XBL and JavaScript • XPCOM: Mozilla's component strategy • Architecture of the Komodo IDE, a large non- browser Mozilla application • Lessons learned in working with Mozilla Mozilla Overview • XML & JS define the UI • Components (think of them as classes) define the implementation/backend • NSPR is a portable runtime library • Necko is network library • Oh yeah, there’s a layout engine too… (Gecko) • Emphasis on standards compliance 2 UI TLAs • XUL: XML dialect for layout of widgets • XBL: XML dialect for association of behaviors with widgets • JavaScript: What to do on events • Skins: switchable themes XUL Example <?xml version="1.0"?> <?xml-stylesheet